
How To: Get blocked video and websites
In order to access blocked videos and websites, you will need to set up a proxy service in the U.S., if you are trying to use Hulu. Go to a list site.


In order to access blocked videos and websites, you will need to set up a proxy service in the U.S., if you are trying to use Hulu. Go to a list site.

Multiplicity photography is a type of photography where you take multiple images of the same subject in different parts of the same frame, then combine them digitally to create a photo with multiple different images of the same person, animal, or object in the same setting. This is also called sequence photography when it's used in sports. This video will show you how to do it with a digital camera and Photoshop, creating amazingly cool-looking results.

The Contacts application on Android-powered cell phones provides a powerful way to manage your address books and keep in touch with friends and family. You can even add and manage multiple accounts from various sources. Watch these tips from Google to learn who to get the most of the Contacts Android app.
Motion tracking a movie scene in After Effects is a royal pain in the butt. It takes a long time, depends largely on the suitability of the footage you are working with, and is rather confusing. This video is here to shed some light on the subject, offering many tips and tricks for basic motion tracking in After Effects. If you're having trouble getting your own scum-sucking monster to wander the desert realistically, watch this video!
If there are words that you use often but Swype doesn't know them yet, you can easily add them to the database of your texting program. In this clip, learn all about adding uncommon or unique words to your Skype dictionary so that you can text even faster. You can even add web addresses, e-mails, nicknames and anything else you use often and don't want to tap out.

Head wounds are among the very worse types of wound, and as a results are very fun and popular subjects for representation in film. This video will teach you how to create an open gash wound on the head of your actor without taking a bottle to it. The wound looks very real, make sure you don't let your actor get near a hospital!
In this advanced level tutorial, learn how to tween with Actionscript 3.0 in Flash CS4. This video starts out slow with a simple fade-in animation and later gets more complex. Subjects covered in this tutorial include: Tween class, creating tweens, timers, timer events, tween events, using event listeners, functions, and more.

Getting into editorial art department work? They may have you switching the color of a model's clothes, eyes, and/or hair in a number of photographs... so better get schooled on the subject now! In the following video, learn how to transform a brunette to a full blown blonde with a technique that is sure to come in handy in the future.
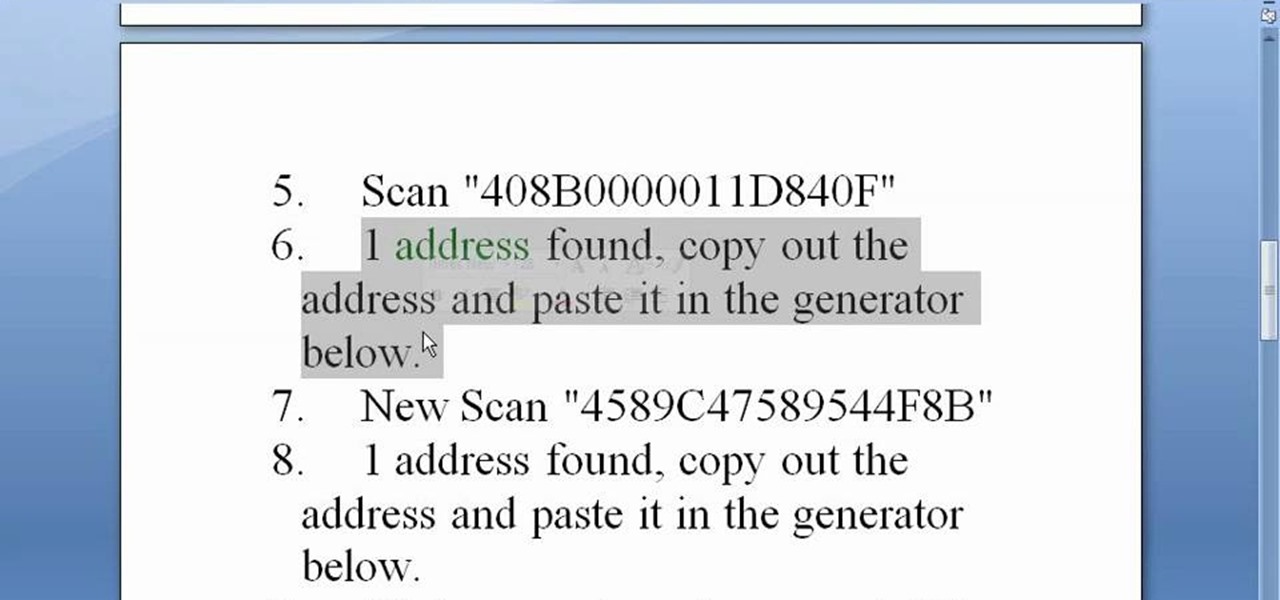
This is a jumprope hack for Pet Society. It's called the Auto Jump + Coin hack, and involves your jumprope, Cheat Engine, and a little code generator.
You can add keywords as metadata to your images to enable you to search images by common characteristics or subject matter and to keep your library organized.

Mark Wallace explains how to set up butterfly lighting (AKA Glamour Lighting; AKA Paramount Lighting)with three light sources. This video shows a nice soft lighting underneath the nose. Used if you want to create a strong powerful look, or if your subject has strong cheekbones or jawline. This type of lighting was used in the filming of "Sin City".

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.
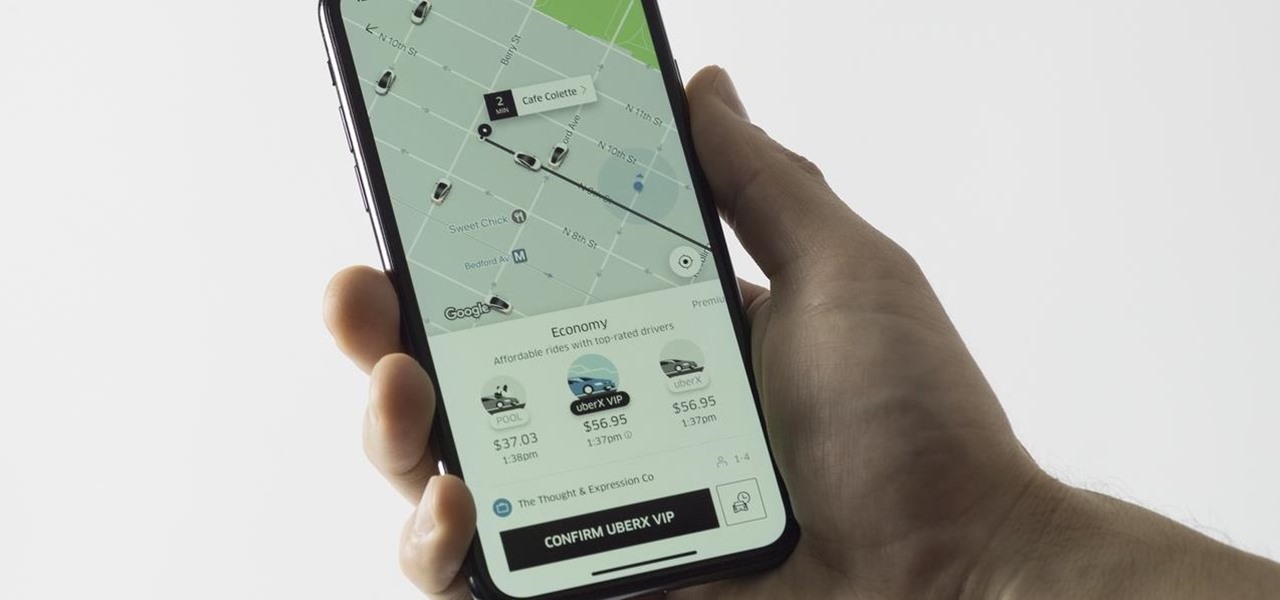
Uber is one of the best ride sharing services out there, allowing you to travel without needing to be tethered to a car of your own. Still, if you're a frequent flyer, you may get tired of entering the same few locations into your app every time you use it. Fortunately, Uber lets you streamline this process.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Hello there! This will probably be the final tutorial on functions where we will be looking over a method called pass by reference. This technique allows us to modify large amounts of data without the overhead and return multiple values. Let's go!

After a few unnecessary U-turns, I quickly realized that Apple Maps wasn't for me, which is why I hate that it opens as the default app any time I select a shared location or an address from Yelp. Copying and pasting the address to Google Maps isn't a huge deal, but it's certainly not as fluid of a process as I'd like.
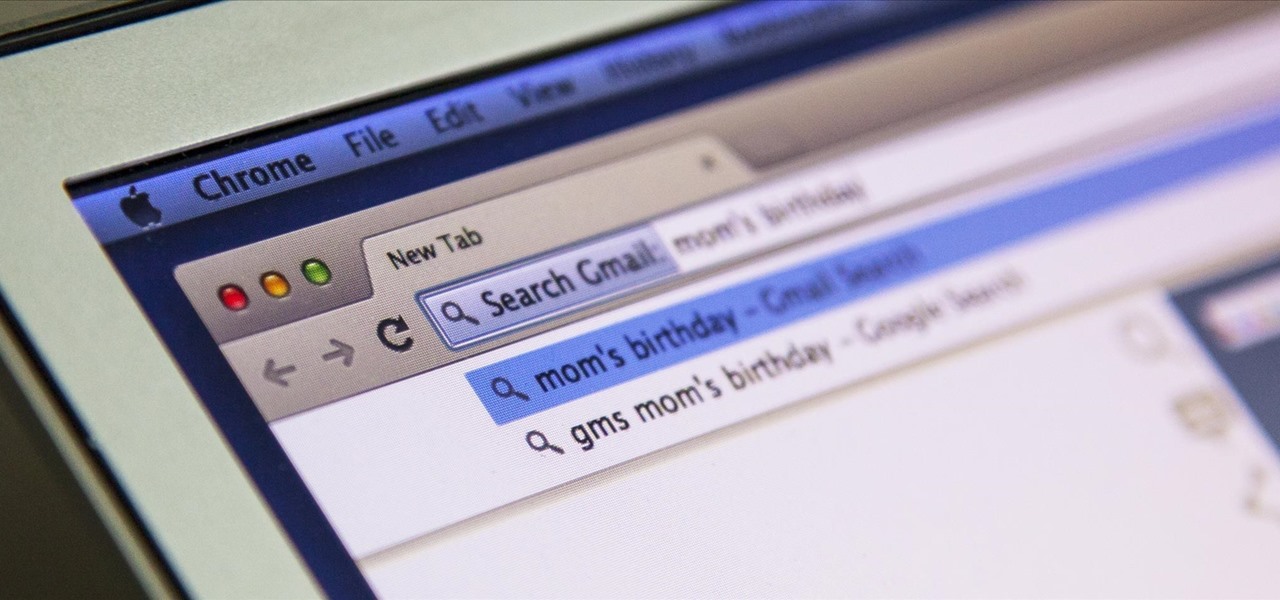
I'm all about saving time. If there's a quicker way to do something, I'm going to find it. For this reason, whenever I need to search through old emails or compose new ones in Gmail, I do it directly from Chrome's address bar, or as Google likes to call it, the omnibox—and you can, too.

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

"Enter your email address. Confirm your email address." I absolutely hate seeing those two sentences when I'm signing up for something online, especially on my Samsung Galaxy S3. The less keyboard work I have to do on my mobile the better. Luckily, there is a way to enter your email address without having to type it all out, and I'm going to show you how it's done.

Welcome back, my hacker novitiates! Many of you have probably heard of a man-in-the-middle attack and wondered how difficult an attack like that would be. For those of you who've never heard of one, it's simply where we, the hacker, place ourselves between the victim and the server and send and receive all the communication between the two.

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

One of the most frustrating things on the Internet are sites that make you register just to view content. I'm not talking about paywalls—I mean the sites that make you give them personal information to look at free articles or forum threads. Most people are uncomfortable with this because a lot of these sites either spam you themselves, or sell your information to someone else who will.

Remote Desktop gives you access to your Windows 8 PC or device from wherever you are to run your applications and access your files remotely.

In evolutionary times, we were far more likely to die from starvation than from diseases related to obesity. In those times, when food was available, it was best to stuff oneself.
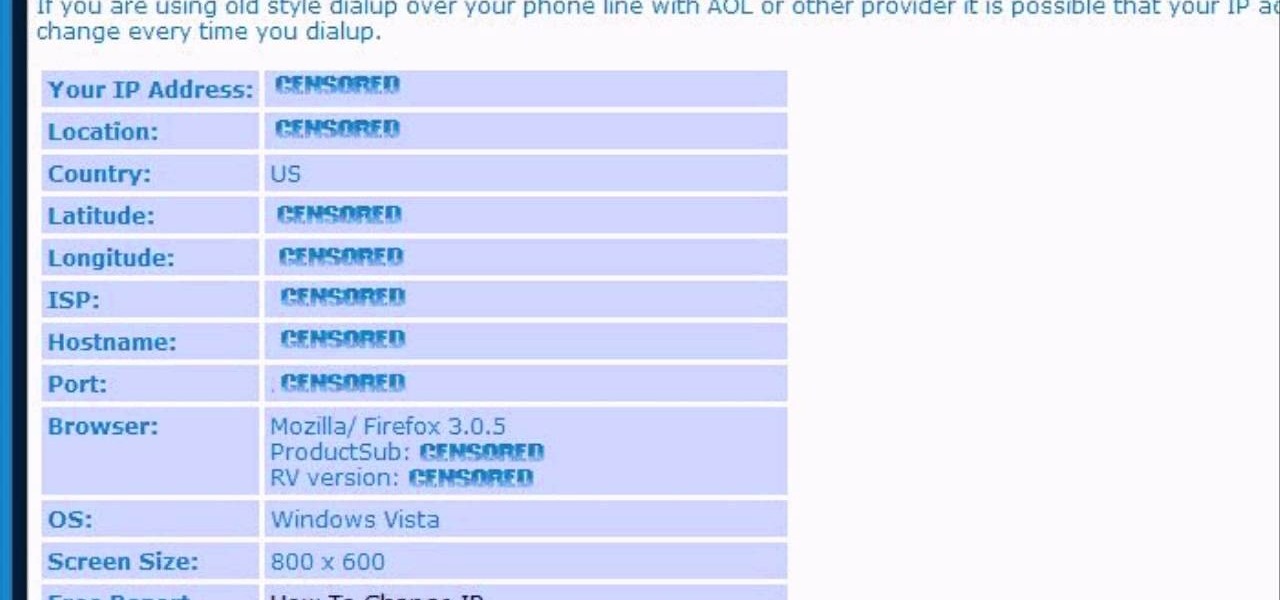
In this video, we learn how to find your IP address. First, start up your computer and open up your web browser. Next, you will type in the site: WhatIsMyIPAddress. Once you do this, you will be led to a new site which will load up your IP information at the top of the page. Once you have this information, make sure you don't share it with anyone else. If someone gets this information, they will be able to hack into your computer and ruin it. They could also access sensitive information and s...

In this tutorial, we learn how to use AV mode & High Speed Sync (flash). First, go to AV mode and change the settings to 2.8. When you do this, your shutter speed will blink at 250. To fix this, hit the lightning bolt with the "h" and change it to the high speed setting. Now, your camera will be able to use the high speed shutter with the flash as well. Now, take some shots of your subject in the sun and you should be able to see a huge difference. The background should come in crystal clear ...
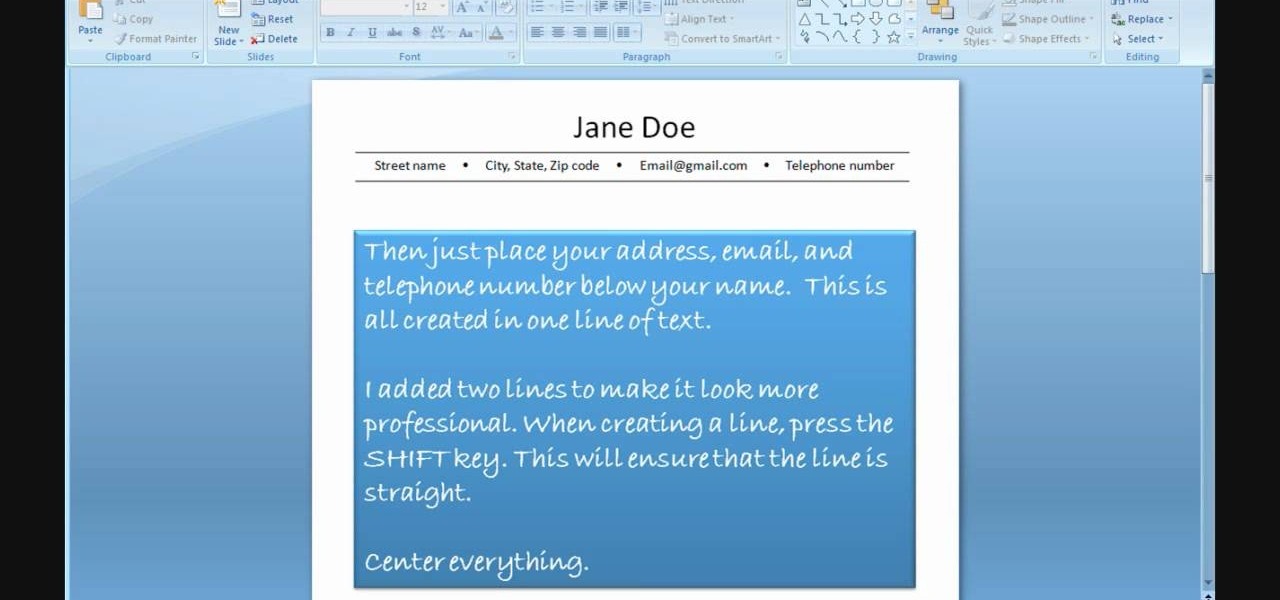
In order to use PowerPoint to create your resume, you will need to select "page setup", in order to change from landscape to portrait. Insert a text box in the center of the page and type your name in it. Next, click on the "format" tab. Next, select your alignment from the alignment center.
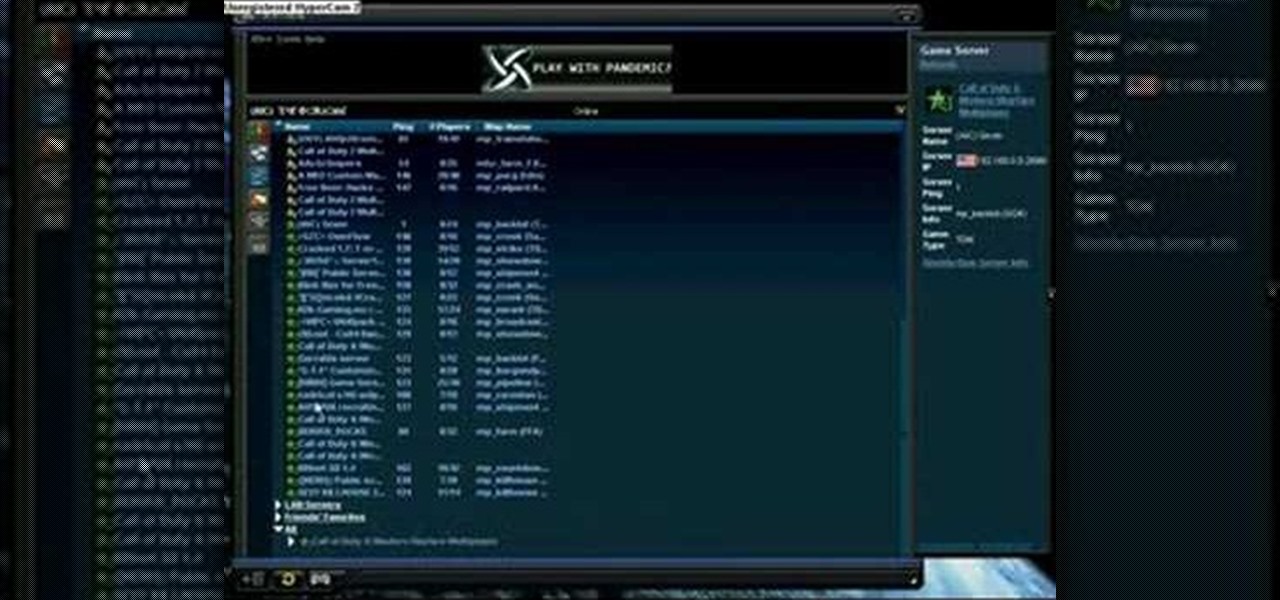
In this tutorial, we learn how to make a Call of Duty 4 working server. First, go into your game and go to "start new server". Next, name it whatever you want and put internet into the dedicated section. After this, save the information and a console will pop up. Don't close this, minimize it. Next, open up your game and go to "join game" and search for your server. When you find it, click on the information and write down the IP address it has inside of it. Now, go to XFire and type in the I...

In this tutorial, we learn how to paint a portrait. Start off by having a subject to draw, then hold your paint brush loosely. Start to outline the face of the subject, then paint in the facial features. Shade around the eyes and cheekbones, and add the ears to the face. Use the paintbrush to create different types of strokes to the painting that fit the face you are looking at. Use shading to your advantage, because this can make a person look older or younger, depending on where you place t...
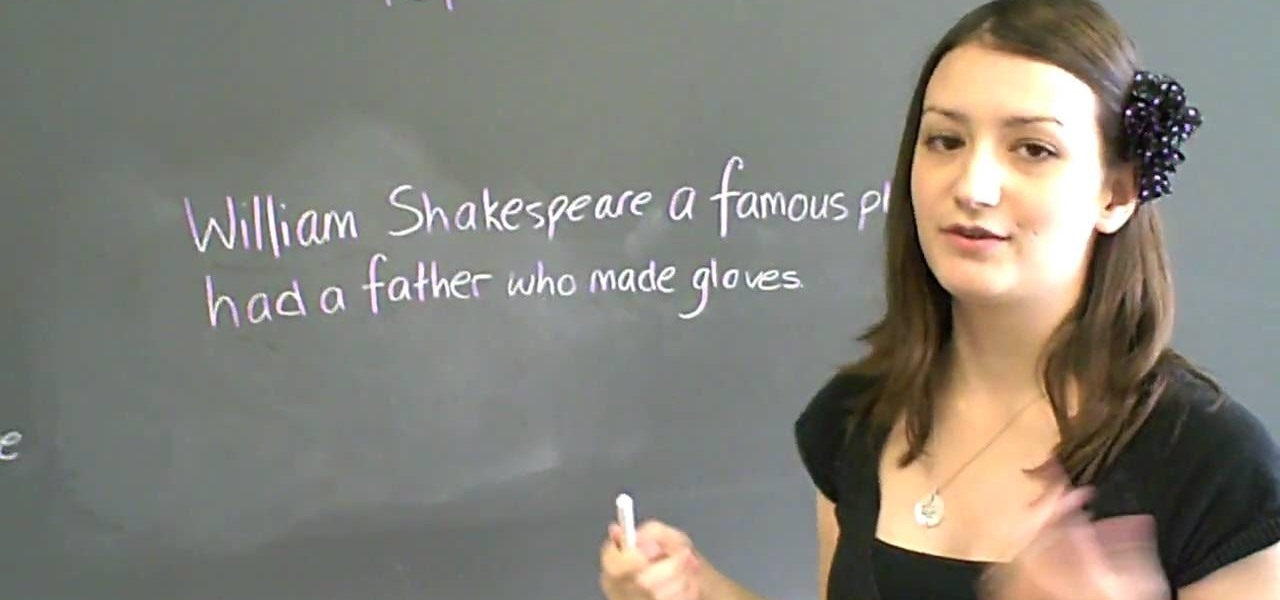
This video tutorial is in the Education category where you will learn how to use commas with restrictive and non-restrictive clauses. Restrictive and non-restrictive clauses are phrases or words that come between the subject and the verb. You don't use commas to separate restrictive clauses. For example, in the sentence "the students who did not wear uniforms were punished". Here "students" is the subject and "were punished" is the verb and the clause "who did not wear uniforms" is restrictiv...
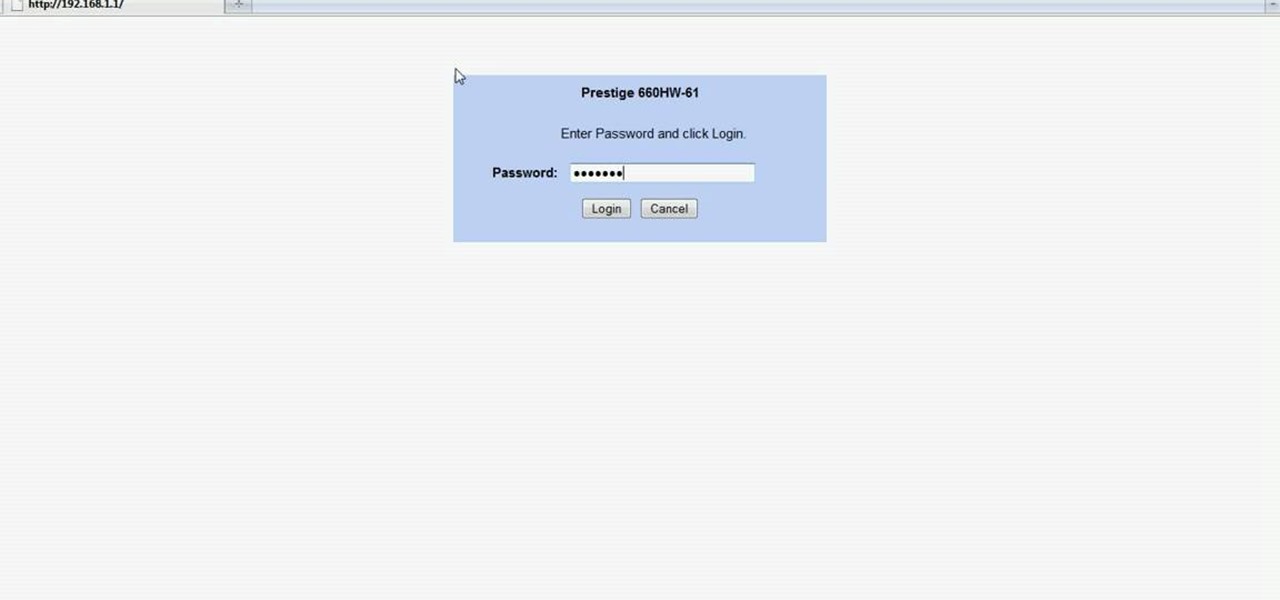
In this Computers & Programming video tutorial you will learn how to easily open your NAT on a ZyXel router. There are three steps involved in doing this. Open your web browser and type in the router IP address which is normally http://192.168.1.1. Then you will get the log in page. The password is either 1234 or admin. It will be written on the packaging of the router. On the next page click on UPNP, then check all three boxes and click 'apply'. Then you click on NAT and set the start and en...
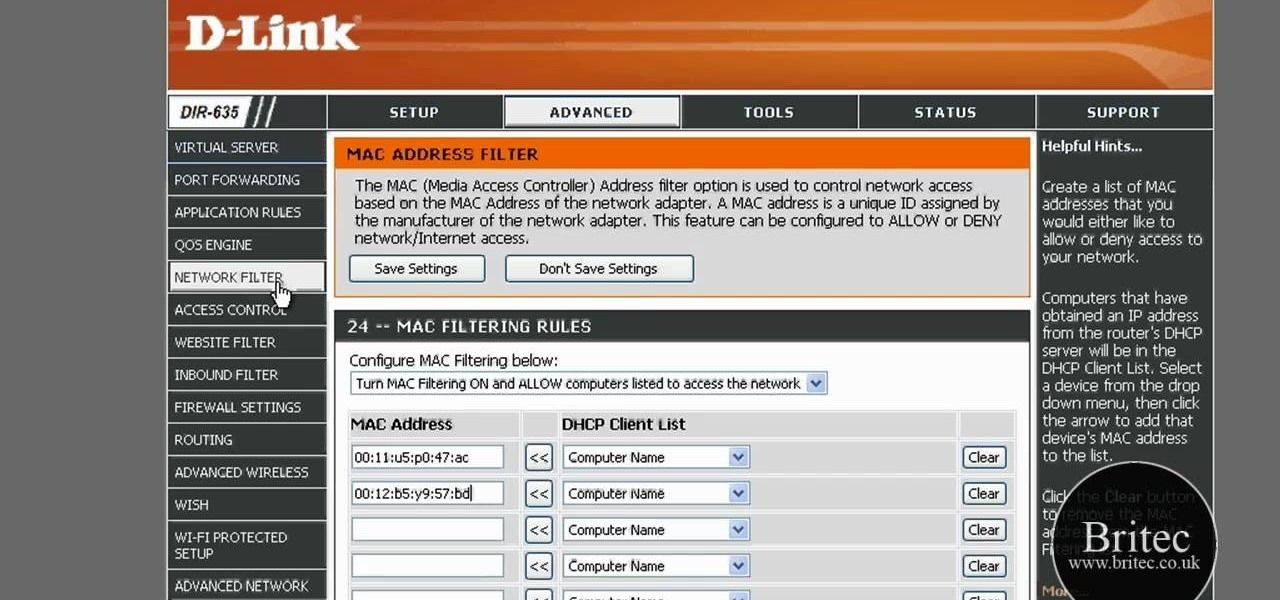
In this tutorial, we learn how to detect all computers connected to your Wi-Fi network. To begin, go to the website, http://msdn.microsoft.com/en-gb/netframework/aa569263.aspx. Once you are on this site, download and install the program. Once it's installed, open the program and then look for the MAC address. Once you find this, go back to the website and enter this into the MAC address line. After you do this, you will be able to see what computers are listed on your network. If you see any ...
In order to get add-ons and plug-ins for Google Chrome, you to go to Chrome Plugins. Type the address into your browser. Then, press Enter. Scroll down the list. Choose and add-on that you want: for example, Click & Clean. Click on the one that you would like to choose. Find "Download Latest Version" and click on it. Wait for it to download and click on it. There are lots of options. Click & Clean allows you to clean your browser with only one click. Session Save allows you to save the sessio...

In this tutorial, we learn how to write a research paper for school. To begin a research paper, start in the library. Grab books that all pertain to your subject, and research as much as you can. You can also search online to get background information on your subject. Make sure you cite your book on a note card in the correct format. Now, you can begin to write your research paper by starting out with an introduction paragraph that captures the attention of the reader and has good facts in i...

In this tutorial, we learn how to control an iPhone from a computer. First, go to Google and search for "real vnc". Then, download and install the program. Now, go to your iPhone and open the program "Cydia" up. Once opened, search for a program called "veency" and download and install it. After you reboot, click on "settings", then "wi-fi", then "select your connection", and find what your IP address is. Next open "VNC viewer" on your laptop, and type in the IP address you just got from your...
If the subject of your photo doesn't look as fresh as you'd like, check out this tutorial and learn how to soften skin with the surface blur tool in Photoshop. This tool is quite easy to do and in less than five minutes you could make a dramatic difference to your photos.
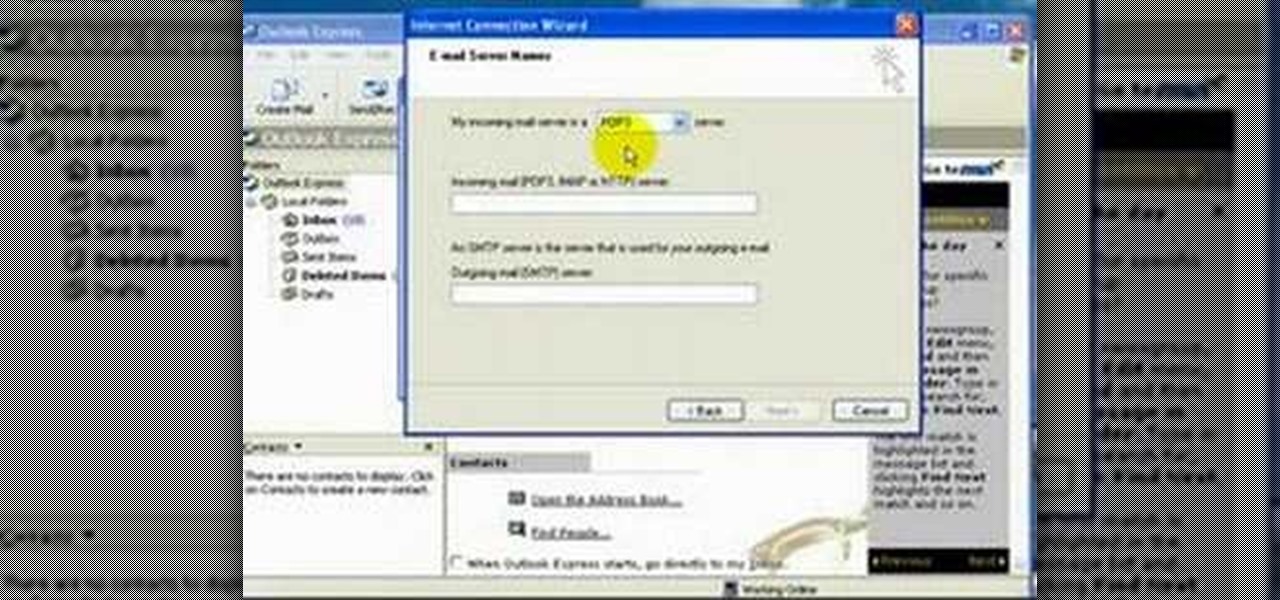
Carole Gallesie from Creative Media Web shows viewers how to set up a new account in Microsoft Outlook Express. Express is preferred because it is a scaled-down version of the popular email client and it is easier to navigate. From your Windows desktop, go to the start menu, all programs, and click on outlook express. When the program opens, look at the top of the page for the "tools" menu, select accounts, add, and mail. The new account wizard will then appear and will walk you through setup...