Microsoft Visual Studio 2008 is an integrated development environment that lets you develop websites, web applications, and web services. It requires a bit of computer coding to run (C#, Visual Basic, ASP, C++) and will work on any web server that supports Microsoft.
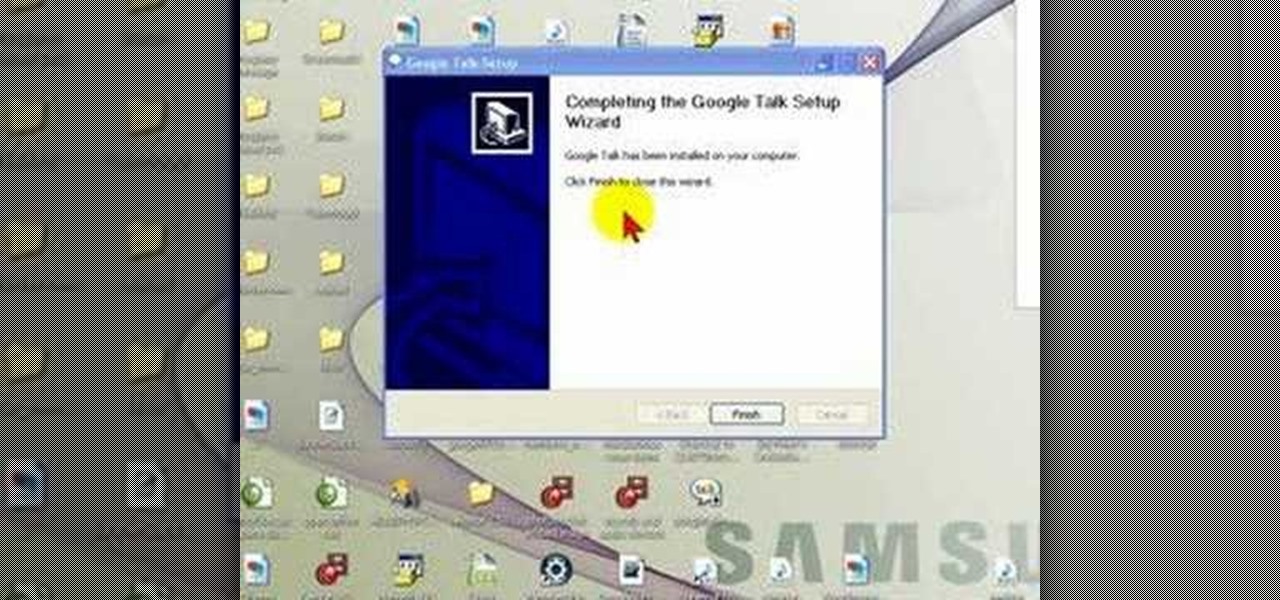
Google Talk is an application that allows you to chat to your Googlemail(Gmail) contacts without being signed into your online Googlemail inbox.

Let Deb Cross and John Hendron demonstrate how to paste text on a Macintosh without keeping the style information (font size, color) in your target application.

Watch this video and learn how to create a perfectly flawless look by properly applying foundation.

Short tutorial on how to run a wide selection of Windows native programs on Ubuntu Linux using Wine.

Learn how to install Apache and MySQL by using XAMPP. You will also write a small application in PHP.

This video shows you how to customize the dock on your Mac using Candy Bar application from Panic.com (http://panic.com/candybar), and icons from IconFactory (http://iconfactory.com).

Learn how to create a to-do list using the iCal application that comes standard on all Macs.

Gary Rosenzweig looks at various methods for printing lists of files in folders in Mac OS Leopard: downloadable applications, using the Terminal, and simple copy and paste methods.

Have you ever wanted to build a statue of the one you love to show them how much they mean to you? Well, I'm guessing your no stone sculptor so you'll have to resort to the powers of Photoshop. In this tutorial, learn how to turn any human or person in a photo into a statue in the application, Photoshop.

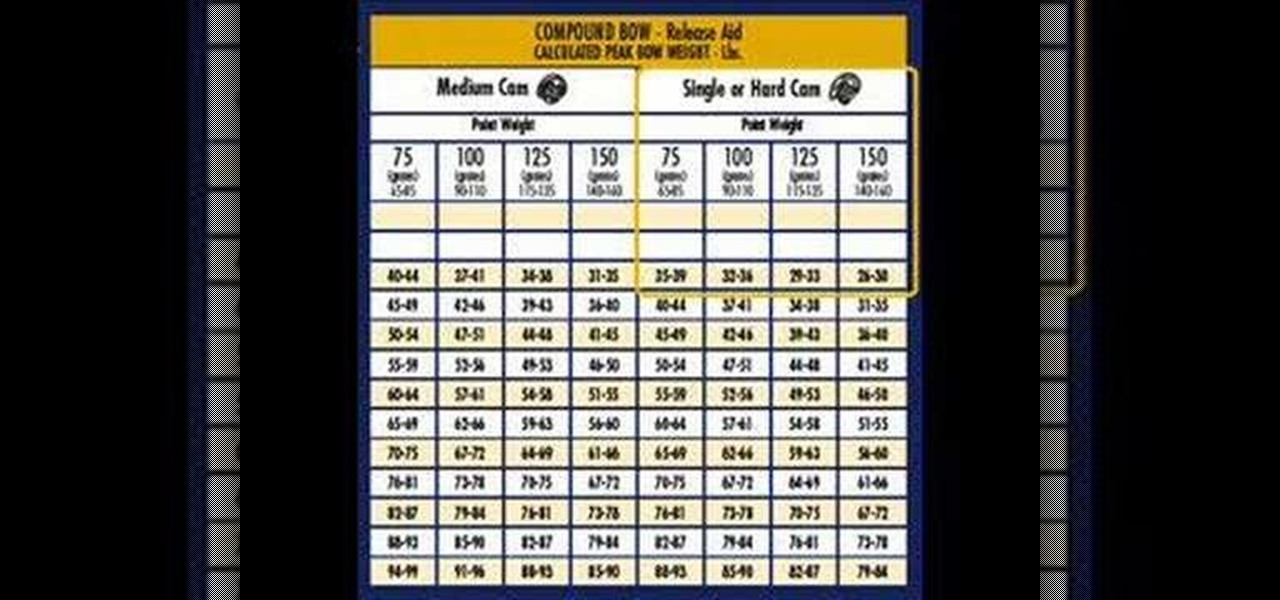
This is a short archery video that attempts to explain why arrow application charts are so complicated. The first three minutes or so present a model of a shaft to help visualize the independent factors that drive each section of the chart.

Learn how to install a ladder rack awning onto Thule's professional load bars as well as their other lines of load bars. One technical note here, this awning is specified for three load bars, instead of the two shown in this video. Chances are this will be used on a van as opposed to a pickup truck bed but everything still applies to that application.

The Red Cine Application is essential to learn if you plan on shooting with the RED ONE camera. This tutorial goes over the library interface.

The Red Cine Application is essential to learn if you plan on shooting with the RED ONE camera. This tutorial goes over output settings, including path, name, size and format.

The Red Cine Application is essential to learn if you plan on shooting with the RED ONE camera. This tutorial goes over color settings and grading.

This video goes over the entire process of a paraffin bath - from set up to application, for stress relief and muscle relaxation.

Learn how to burn a DVD or save a movie with the Adobe Premiere Elements application. Very simple and easy!

How to jailbreak an iPod Touch 1.1.2 on a PC. Jailbreaking allows you to download third-party applications.

A primer on how to install apps in Sabayon Linux 3.4.

Want to learn the easiest way to get music off an iPod and onto a Mac? A Webb from howdoimac.com recommends using iPodDisk, a great little application that mounts your iPod as a hard drive. Your simply drag your music off the drive onto your computer and into iTunes!

Installing custom firmware on your PSP allows you to run outside and homebrew applications, run games directly from your PSP, and burned games on your PSP. Note that you need to have PSP firmware version 1.5 to install this otherwise you will have to downgrade.

Libraries have been used in page layout applications for years. InDesign CS2 has one of the best implementations of Libraries, however, InDesign CS2 also introduces Snippets. In this episode Terry White will show you the ins and outs of both and let you decide which one is best

Version Cue is tightly integrated into the Adobe Bridge and the CS2 Applications. In this video you will see how to set up a Version Cue project and how to save multiple versions of a Photoshop document into your project. Then you'll see how to revert back to a previous version.

inDesign has some hidden special effects that will make your type on a path much more compelling. Granted Type on a Path is not a new concept and has been around in Illustrator for years. However, no other application out there can handle Type on a Path as well as InDesign CS2.

This video tutorial takes a look at how to create layers in Photoshop CS2 that build up to your signature. Then we'll pop over to Adobe ImageReady to put the finishing touches on animating that signature so that it can be used on the web or in your email application. Check out this Terry White's video now!

Starting an independent record label, like starting any other business, requires a well-conceived plan with clear goals. Check out this tutorial and learn how to take your love of music and turn a profit.

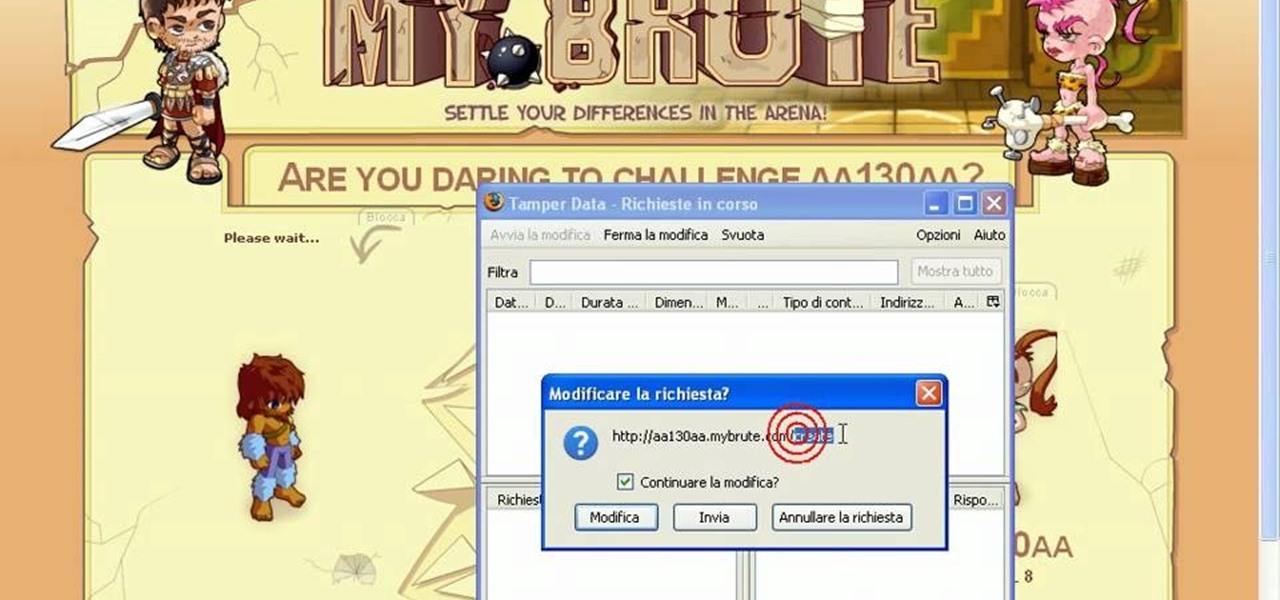
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to cheat MyBrute for a bear (05/08/09). This is the easiest way to get a bear!

In a stunning end-of-year twist to the Magic Leap versus Nreal legal saga, the China-based startup is now filing a motion against Magic Leap.

Now that we've had our hands on the Magic Leap One for almost a year and early adopter developers have had the opportunity to publish apps for the AR headset, it's time to see how it stands up against the rigors of a day at the office. We did just that, and we wrote about it!

While the 49th Annual Gay Pride Parade and Festival will take place on Santa Monica Boulevard and West Hollywood Park, revelers will also be able venture Northeast to the TCL Chinese Theater on Hollywood Boulevard to continue celebrating via Snapchat.

With the defending champion Golden State Warriors and Drake's favorite team, the Toronto Raptors, set to face off in the NBA Finals starting Thursday, Snapchat has gifted hoops fans with a pair of augmented reality experiences.

If you need some help expressing how you feel to your mom for Mother's Day, Snapchat and Facebook are here with some augmented reality help.

Just when we thought the AT&T partnership with Magic Leap wouldn't really take off until the latter launched a true consumer edition of the Magic Leap One, the dynamic duo jumped into action this week to offer the current generation headset to customers.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

Location-based gaming pioneer Niantic has been preparing its flavor of AR cloud, the Niantic Real World Platform, to bring more realistic and interactive augmented reality experiences to mobile apps. And now the company is looking for a few good developers to help execute its vision on the platform.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Just days after Bose did its best to frame a pair of glasses frames with spatial audio as "augmented reality," a patent application from Magic Leap, surfaced on Thursday, March 15, offers a similar idea, but with real AR included.

A Swedish digital artist has developed an app for the iPhone X that creates mind-bending 3D illusions that correlate to the user's point of view.

A new smartglasses powerhouse is rising in Europe, led by two of the region's leading brands, optical systems company Zeiss (also known as Carl Zeiss) and telecommunications giant Deutsche Telekom.