In this video they are showing how to use proportions to solve word problems. In the first example they used 2/3 is equal to x/6. To solve for x, you begin by cross multiplying setting up and equation 3x=12. Next, divide 12 by 3 which equals 4. So x equals 4. In the next example, she has given a situation where she is making a ranch dip using a ranch powder and sour cream. She want to use 80oz of sour cream and she wants to know how much powder ranch she will need. She know that for 16oz of s...
This is a presentation from WatchMojo detailing the operation of a manual/standard automobile. Explanation includes the placement of pedals listed from left to right as the clutch, the brake, and the gas. There is also an explanation on the gearshift which includes a diagram of where gears are located. Explanation for the beginning of driving includes instructions as follows; ensuring that the ground is flat, the application of the parking brake, the process of depressing the clutch, placing ...
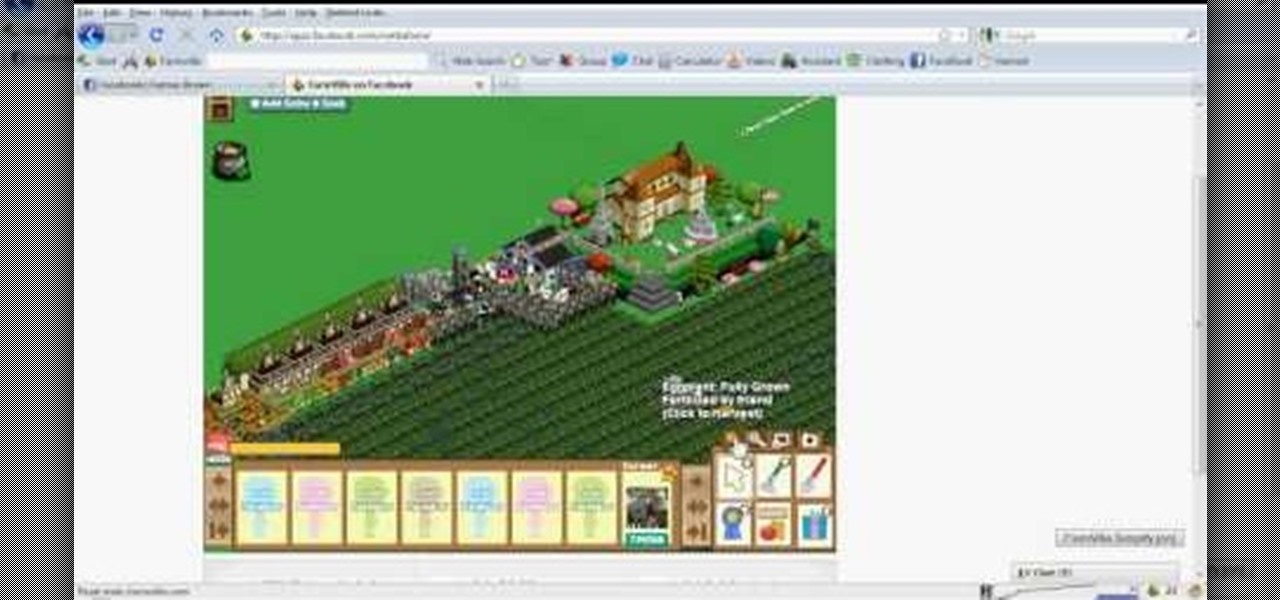
This is a recent glitch, similar to the chicken coop glitch, where you can make your horse stable completely ready. Just watch this brief video tip to see how to benefit from the Horse Stable glitch in FarmVille (03/09/10). It's a simple glitch in the game that allows you to use a horse that is unready to make a stable 100% ready and be able to collect from it. This is very helpful when you are trying to achieve the HorsePower ribbon on Farmville.
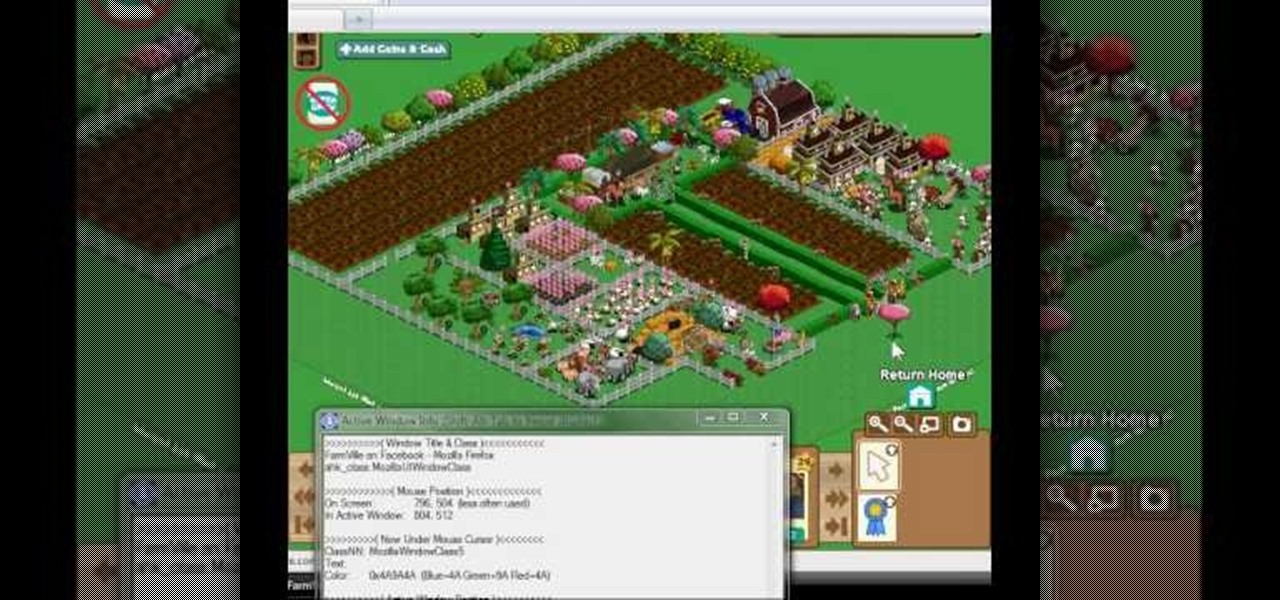
This is an easy glitch in FarmVille that's been around for a long time. Stacking crops. If you want to learn how to stack your crops in FarmVille, just watch this video tip on how to do it (02/16/10). This glitch allows you to grow many more crops than usual, using your limited space on your farm to maximize the most crops in the least amount of space. By doing this glitch, you can easily achieve mastery for all crops in a quicker time frame.
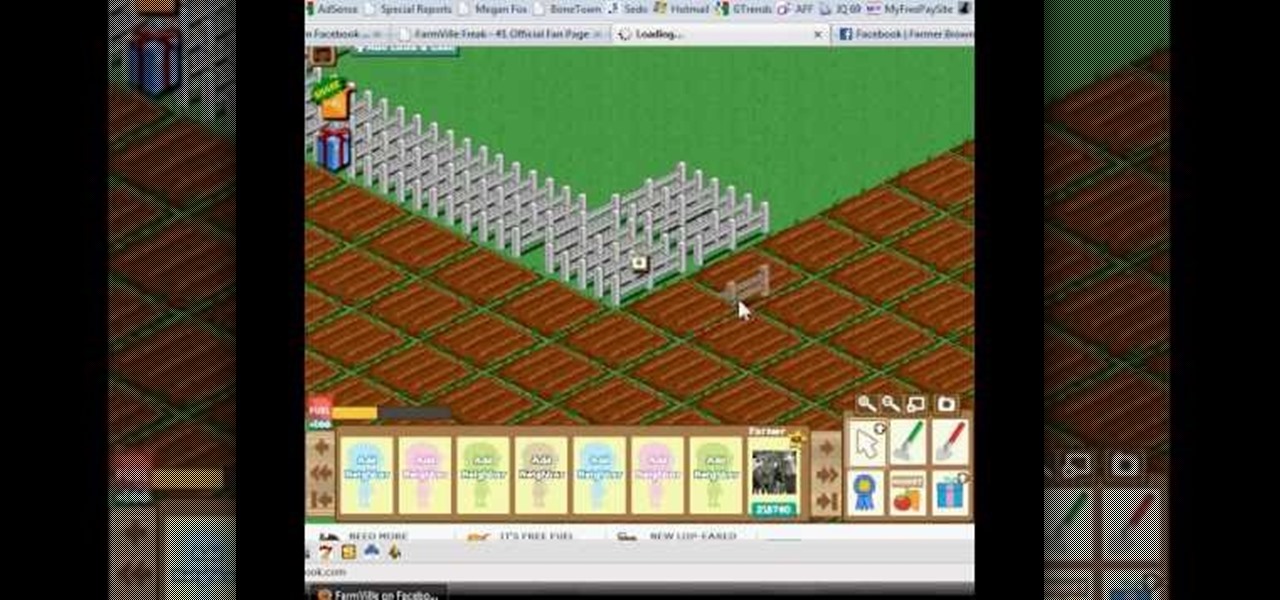
To quickly receive your blue ribbon with the fences in FarmVille, you're going to want to watch this video tip. It's a brief explanation of how you can easily get the Blue "Fenced In" ribbon in FarmVille (01/11/10). BEfore you start this, you will need 75,000 coins and 77 free plots of land to get the blue ribbon.
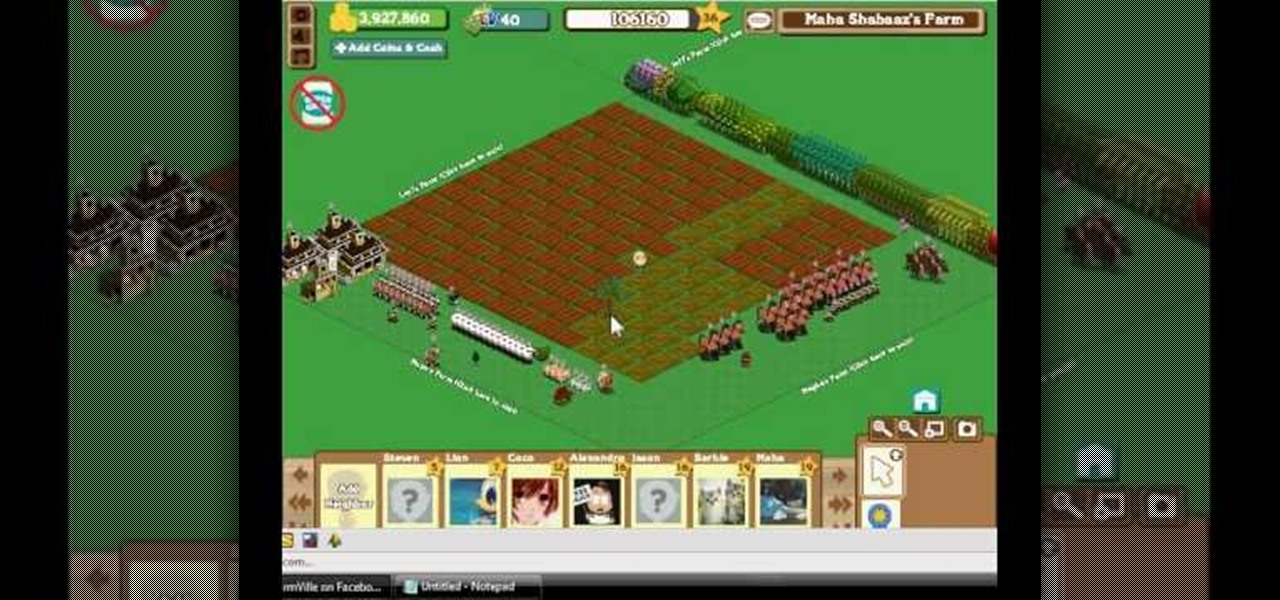
Everybody wants to find out the answer to "How do I put trees on my crops?", but it's a tricky one to figure out. But this video walkthrough will show you the steps necessary to finally Put trees on top of crops in FarmVille (12/13/09). Just watch and learn.

If you work with a computer, at some point in time your computer is going to freeze. Hopefully, you've been saving any important data or writing you've been doing because there are a few easy steps to take to get that computer running smoothly.

Is your farm looking a little bland in FarmVille? Using a basic optical illusion, you can make what appears to be hills!

Purple is a classic eyeshadow color that can effortlessly be worn as part of the smoky look, whether you're an expert or novice at applying makeup.

Check out this video if you are interested in learning how to Jailbreak AND Unlock the iPhone - Firmware 3.0.1 (August 2009).

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to take and share photos on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to shop the App Store on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to customize the Home Screen on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Watch this video tutorial from the Polish Guy to see how to polish and restore a brass lamp font with Simichrome Polish. In this demonstration tutorial we use Simichrome to polish a piece of brass. The tutorial includes a detailed work instructions and best practices.

Watch this video tutorial from the Polish Guy to see how to clean and polish a headlight using Autosol Polish. In this polishing tip we clean a headlight from a Ford F150 using Autosol metal polish. The video includes polishing instructions for cleaning a car or truck headlight by hand as well as using a drill with a buffing wheel.

Watch this video tutorial from the Polish Guy to see how to polish silverware using Cape Cod polishing cloths. In this polishing tip we polish silverware using Cap Cod Metal Polishing Cloths. The cloths are individually packaged in an attractive tin that includes a pair of reusable gloves and a buffing cloth.

Watch this video tutorial from the Polish Guy to see how to polish a stainless steel roller using Autosol. In this polishing tip we polish a stainless steel roller using Autosol Metal Polish. The tutorial includes detailed work instructions and best practices.

Watch this video tutorial from the Polish Guy to see how to polish a chrome car rim using Flitz Polish and a buff ball. In this polishing tip we polish a Jeep wheel using Flitz Metal Polish and a Flitz BuffBall. The tutorial includes detailed work instructions and best practices.

Watch this video tutorial from the Polish Guy to see how to polish an Andersen Door Handle using Simichrome. In this demonstration we use Simichrome to polish an Andersen Perma-Shield Frenchwood hinged patio door’s brass entrance handle. The tutorial includes a detailed work instructions and best practices.

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

Learn how to use Audacity, a free audio editing application that can be used to record music, podcasts, and more. You will learn how to install the LAME Encoder, set your preferences, save the project, record, preview your recordings, edit content, remove noise, adjust volume, time shift, and exporting. Each of these is an important part of the podcast creation process and you will learn to do it all in this Audacity video series.

Windows Movie Maker is the basic video application included with Windows XP. Learn how to use Windows Movie Maker to create a movie with transitions, effects, background music, and voice over narration. If you have never made a podcast or simple movie before, this series is a great way to get started without needing additional software if you have a Windows XP OS.

Since its release back in 1988, Microsoft Office has been the top client and server software suite for businesses around the world. Office's domination is thanks to both Microsoft's extraordinary foresight and their continual updates and innovations to ensure that companies always get what they need.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Just as Apple, Snapchat, and other tech giants are working on augmented reality wearables in the race to replace smartphones for the future of mobile computing, so is Samsung.

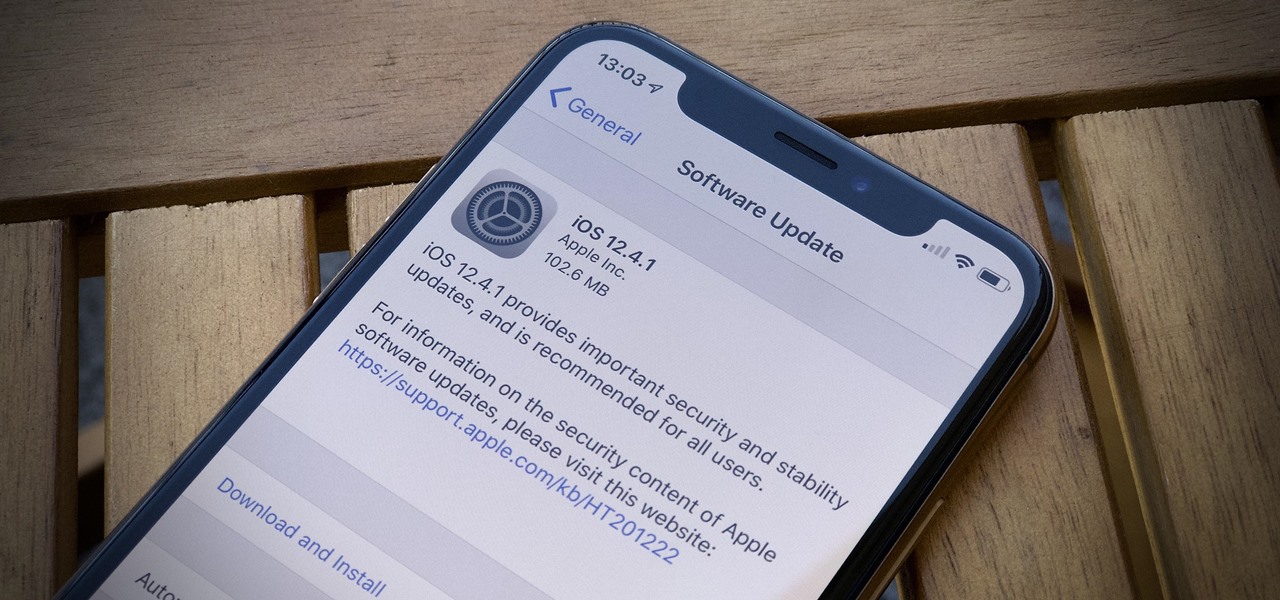
While all eyes might be on the next beta release for iOS 13, Apple is still pumping out updates for iOS 12. The company released iOS 12.4.1, the first update since iOS 12.4, on Aug. 26. The latest update includes a patch for the jailbreak vulnerability recently discovered in 12.4. One month later, on Sept. 26, iOS 12.4.2 came out for older iPhone models.

As Microsoft works toward fulfilling its $480 million contract to supply modified HoloLens 2 headsets to the US Army, Airbus is preparing to supply advanced augmented reality apps for the device.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Next to map data overlays, one of the most often discussed concepts for apps that could propel augmented reality smartglasses into the mainstream is a real-time language translation app.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

The last few months have delivered some great new Magic Leap releases, but that doesn't mean the development team is resting on its laurels when it comes to the platform itself.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Augmented reality productivity software maker Upskill has expanded the reach of its Skylight platform with support for Microsoft HoloLens.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

In recent years, medical professionals have demonstrated how the HoloLens can assist in surgeries, ranging from collarbone repairs to spinal surgeries to cosmetic procedures. Now, the largest children's hospital in the United Kingdom is also ready to deploy the technology.

Based on its continued research, it appears Microsoft recognizes that the next HoloLens needs a wider field of view (FoV). Based on a recently-revealed documentation, the company's research team has found another way to accomplish that objective.

New York-based startup CTRL-Labs has closed a $28 million Series A round of funding from Google parent Alphabet's GV and Amazon's Alexa Fund, among others, for its next-generation neural interface technology for AR/VR and robotics.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

After more than a year and a half of silence, the rumors have morphed into reality: Microsoft has finally released an update for the HoloLens. And with that update comes a collection of new features that hint at big plans for the HoloLens this year.

With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming.