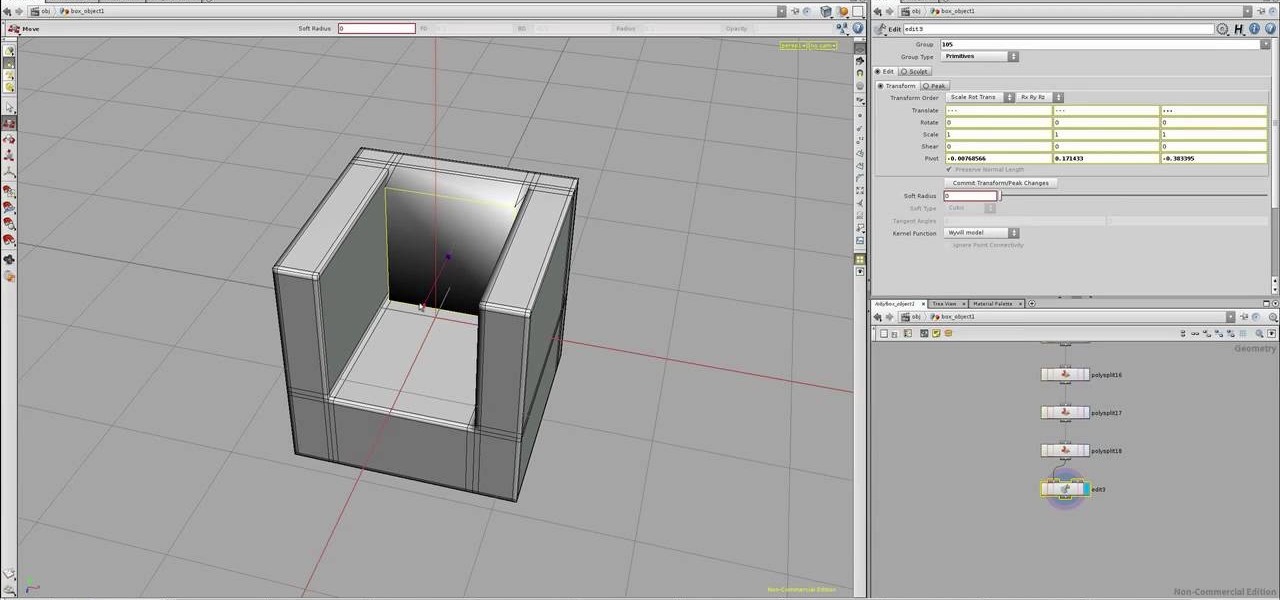
Interested in making a chair within Houdini? Pull one up and see how it's done. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look.
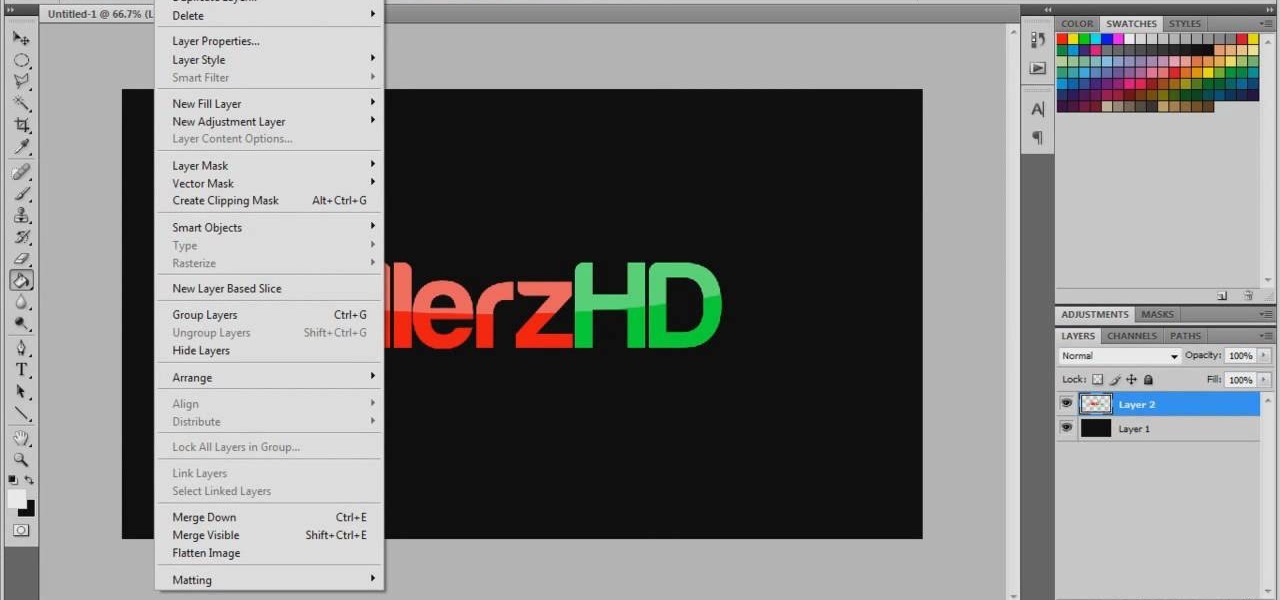
Want to create full 3D text but don't have fancy 3D modeling software? Never fear. With Adobe Photoshop CS5, it's easy to generate 3D, glossy header text. Whether you're new to Adobe's popular graphics editor or a seasoned design professional looking to get better acquainted with the industry-standard app, you're sure to benefit from this free software tutorial. For more information, watch this designer's guide.
You might have difficulty installing Windows XP on a computer that has Windows Vista because it will say it’s incompatible. You’ll have to make a cd with an extracting software. You’ll need several more programs and software. It’ll take some effort but if you follow along this video you should be able to achieve the goal.

This video gives a tour of the Motorola Droid software. The video begins with the user turning on the cell phone and guides you through navigating the gui (graphic user interface). The easy to use Youtube desktop widget is featured as well as the scrolling desktop that's moved by a flick of the finger tip in either a left to right or right to left direction.

At least with a stomach virus you may drop a few pounds; a virtual virus just screws up your computer. Take these precautions to avoid problems. You will need anti-virus software, spyware, a firewall, and a healthy dose of skepticism. You can find free safety software on the internet.

This software tutorial takes a look at some of the editing capabilities inside of the freeware image viewing application IrfanView. Learn how to use IrfanView to crop, resize and retouch images. If you can't get your hands on Photoshop or a professional image editing software, download and try IrfanView for your basic editing needs.

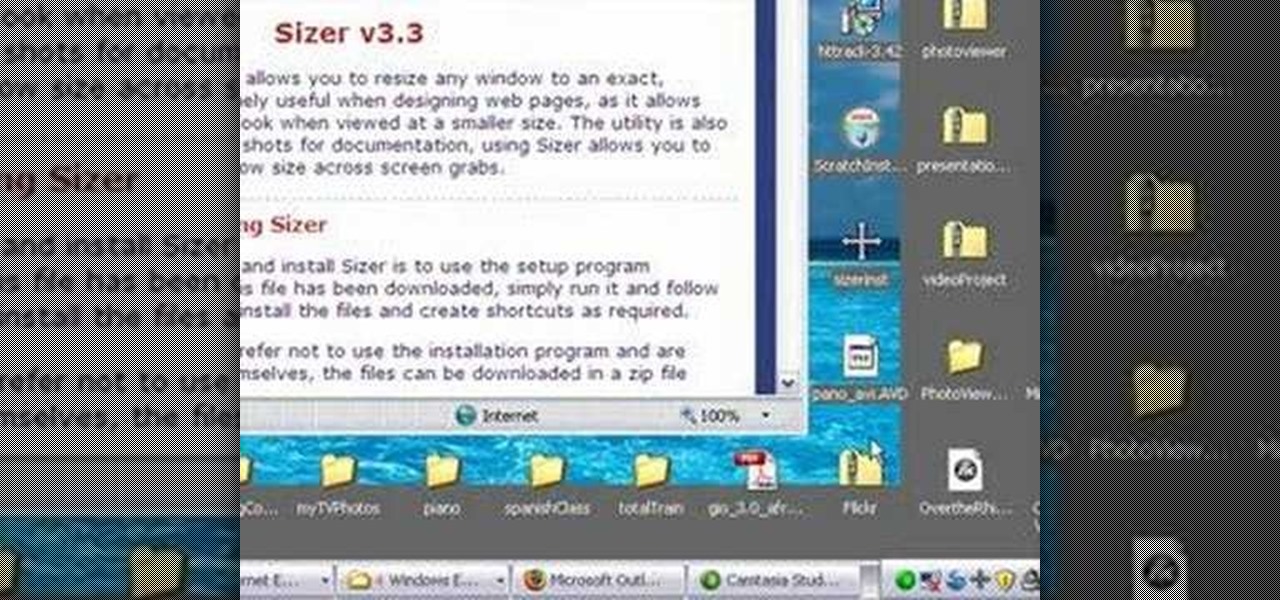
This software tutorial is on downloading and using Sizer to resize windows for exact screen grabs. Sizer is a free open source software that allows you to size a window to an exact numeric size instead of dragging the window around randomly. This is great for screen recordings with softwares like Camtasia, or for image screen grabs. See how to download and use Sizer in this tutorial.

In this video tutorial, you'll be taught a method for installing software packages within the Ubuntu Linux distribution in the simplest and most painless way available. There will be no web searching, downloading, or running, etc., of anything–just three clicks, and 2 minutes of your time! For a video walkthrough of the process, take a look!

Here is a demonstration of a custom designed brush for the TVPaint software. This pen is sensitive to a realistic method of gestural drawing. Watch this instructional video to use this software brush to make several types of digital drawing strokes.

Picasa 2 is a free image editing software from google. This software tutorial shows you how to use the basics of Picasa 2 for photo shorting, fixing and sharing. Learn how to navigate the interface and use the basic editing controls of Picasa 2.

This photo editing software tutorial shows you how to use this free software FastStone Photo Resizer 2.5 for Windows to batch rename and resize your images. Make life easier and resize and rename your photos all at once with the batch functions in FastStone Photo Resizer 2.5.

This photography software tutorial shows you how to use Kodak EasyShare free software from Kodak to organize your photos, make small fixes and access online services, from a UK perspective.

This software tutorial shows you how to use the video editing software Wax 2.0 to clone someone in a video. Learn to make multiple versions of yourself interact in one video in this Wax 2.0 cloning tutorial.

This software tutorial will show you how to track a laptop if it gets stolen using free tracking software Adeona. Of course, it's a good idea to figure out how to keep your laptop from getting stolen, but if you lose it, you can use Adeona to find the location of your laptop.

Everyone and their moms are into Guitar Hero nowadays. If you can't afford this great game, check out this tutorial and learn how to create your own Guitar Hero clone using free software and a controller that you can make using parts that total around $22. The free software used in this instructional video is called Frets on Fire.

In this software tutorial you will see how to create a polaroid picture and make it look like it is pinned up on a wall using Inkscape. All you need for this creative pinned-up polaroid is a picture and the open source software Inkscape.

If you do any amount of graphic design or layout design, then you know the importance of using kerning when working with typeface. This Inkscape software tutorial shows you how to manually kern text within Inkscape. This isn't the best graphic design software, but it is open source and if you are using it for layout you may need to use text kerning and will find this video helpful.

In this software tutorial you will learn how to make a simple paperclip from scratch using the curve tools in Inkscape. Inkscape is an open source freeware software so it's easy to get ahold of and start using for your graphic design needs.

This software tutorial shows you how to build a luma track matte in Cinema 4D 3D modeling software and then help speed-up your compositing of the track matte in After Effects. Creating a spinning logo with video footage inside the logo, as shown in this tutorial is a great way to learn to use Cinema 4D and After Effects together.

Check out this video tutorial for building a Bart PE CD with Part PE Builder made by Runtime Software. Make sure that you have Internet access, a blank CD, and a copy of your Windows XP compact disk with at least Service Pack 1 on it. This will help you creat a bootable CD-ROM for your computer.

This is a terrible prank to pull on a friend. Destroy their iPhone software with a couple of quick hacks.

This shows you how to use the free software to unlock the iPhone, to work with any GSM Carrier. It is a very detailed, and quirky tutorial, so pay attention.

Learn how to use Inkscape (an opensource software) to design a logo for your website. This tutorial gives an overview of the software by running you through an example logo.

Are you the go-to guy/girl whenever your friends and family need tech support? You might want to consider installng LogMeIn - remote desktop software. The Lab Rats, Andy Walker and Sean Carruthers, will show you the benefits of LogmeIn software.

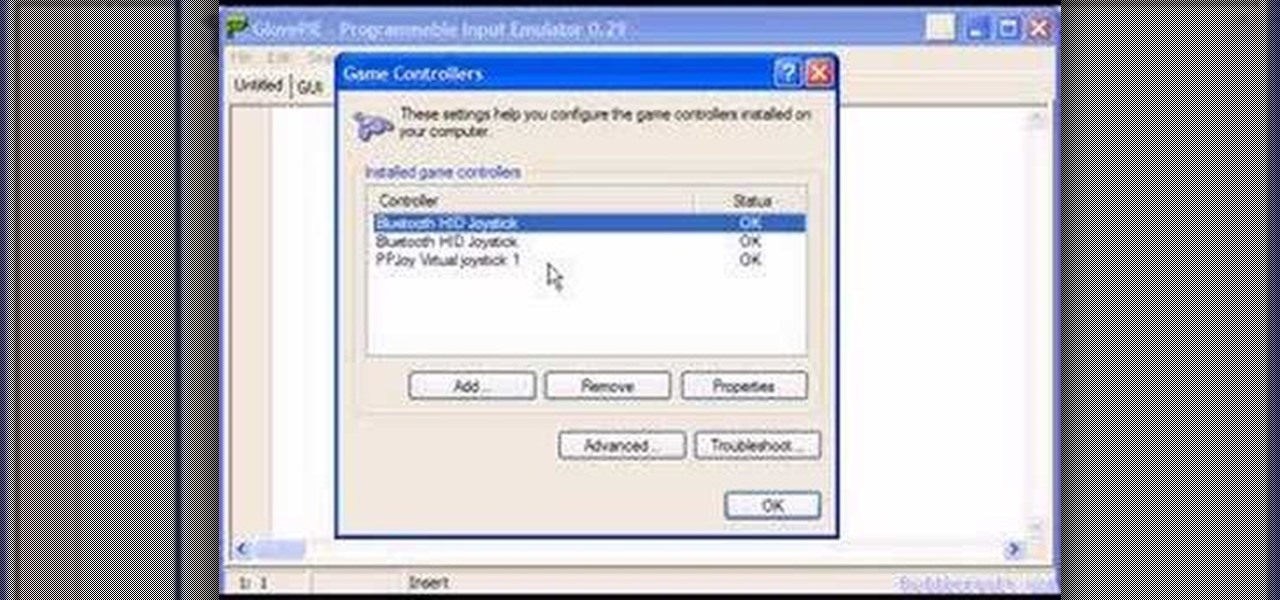
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to recognize analog input or joystick/joypad input from a Wiimote using GlovePie and another piece of software called PPJOY

The fourth room in the Color software that's part of the Final Cut Studio of Apple, is the ColorFX tab. This section of the software allows you to create different looks by combining different effects nodes.

Here is a supernatural how-to for all you spirit lovers. This is a step-by-step guide to create a fake ghost video with free software. The initial technique is simple, but with a few more tweaks, you can get video that can fake at least your grandmother. Use this as inspiration for one of your April Fools Day pranks!

This video tutorial shows how to download .cut files onto Cricut software to design cards. Learn how to use this card making software, and get instructions for how to make a strawberry greeting card.

Updating your Galaxy to the latest software version is optional, but you wouldn't know that from the persistent notification and status bar icon that are constantly reminding you to. Thankfully, you're just an app away from hiding these eyesores without the need to update your phone.

The automatic software update setting on your iPhone is nice, but you may not always want to install new iOS versions blindly. New updates could contain bugs and vulnerabilities, and your favorite features may even disappear. With the auto-update option turned off, you can manually download and install updates, but there are also hidden options to be more specific about how you want to do it.

Automotive augmented reality display maker WayRay is making a move to help developers get all those slick, futuristic AR functions we see in concept videos into the real cars of today.

New documents reveal that electric car company Tesla has filed a surprising new patent that has nothing to do with batteries or autonomous driving and everything to do with augmented reality.

The release of iOS 11 and ARKit is probably the biggest event for mobile developers since the advent of the App Store.

Smartglass maker ThirdEye Gen, Inc. has introduced an augmented reality solution for enterprises that includes their X1 Smartglass and a suite of software applications that enable completely hands-free computing.

Numerous examples exist of doctors and surgeons using HoloLens to plan surgeries. The device has even been used to view reference images during a procedure and stream it to a remote audience. Until recently, it has not been used to augment the surgeon's view of the patient during a live surgery.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

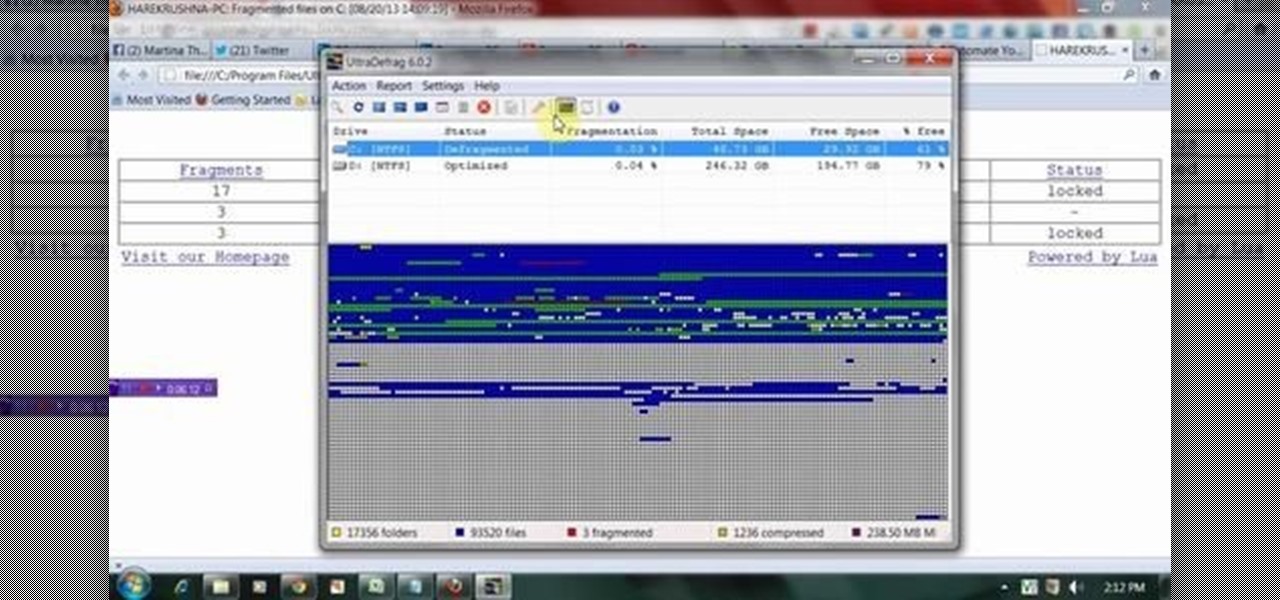
This Tutorial video will show you how to automate hard drive organization or defragmentation with ultradefrag software. UltraDefrag, PC utility software defrags your pc and speed up PC performance. So please watch the video and follow the steps to do it yourself.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

"We all want to escape our circumstances, don't we?" Benedict Cumberbatch may have been talking about acting, but the sentiment rings true for all of us at some point or another. Whether it's work, school, or just boredom at home—we all wish for an escape sometimes. If only.