This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting that should make updating a bit less complicated, along with a few other benefits.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.

My bathroom is like my own private arcade room. Whenever I'm seated comfortably on the toilet, no one is going to disturb me, so I can play anything I want on my smartphone. You probably do it, too — and your parents, kids, friends, colleagues, and boss — so don't be afraid to admit it.
Organizing contacts is a bitch, especially on the iPhone. Some contacts will have multiple entries, you can only delete contacts one by one, and certain types of contacts can't be deleted at all. If that isn't enough to make you pull your hair out, then I don't know what will.

My years in the restaurant business have taught me many things. Some of those things are best left unsaid and other things require a PhD in vulgarity, but the one thing I learned that I keep coming back to night after night is that you do not have to spend a lot of money to drink excellent wine. This is especially true of champagne...I'm sorry, sparkling wines.

Fall is my favorite time of year, yet I cringe every time it begins. Why? Because it seems like every business is in a frenzy to start the Christmas shopping season the day after Halloween ends. For those of us who are fans of pumpkins, that's a buzzkill.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

If you've read any health news in the past year or so, you've probably been bombarded with headlines announcing that frequent sitters face certain death, even when you're just relaxing and watching TV at home.

Climbing into bed and shutting your eyes each night is heavenly—but waking up the next morning isn't. We all hate dragging ourselves out of the comfort of sleep and into the groggy, exhausting work day. Yet starting your day doesn't have to be awful if you know how to hack your sleep cycles and get the most out of your shut-eye.

Foodies and big-time chefs like Thomas Keller go crazy for fleur de sel. This finishing salt appears in fancy eateries and cookbooks the world over, and in the early 2000s, it was not uncommon to see diners in a high-end restaurant sprinkle a pinch of fleur de sel on their plates from their own personal stash.

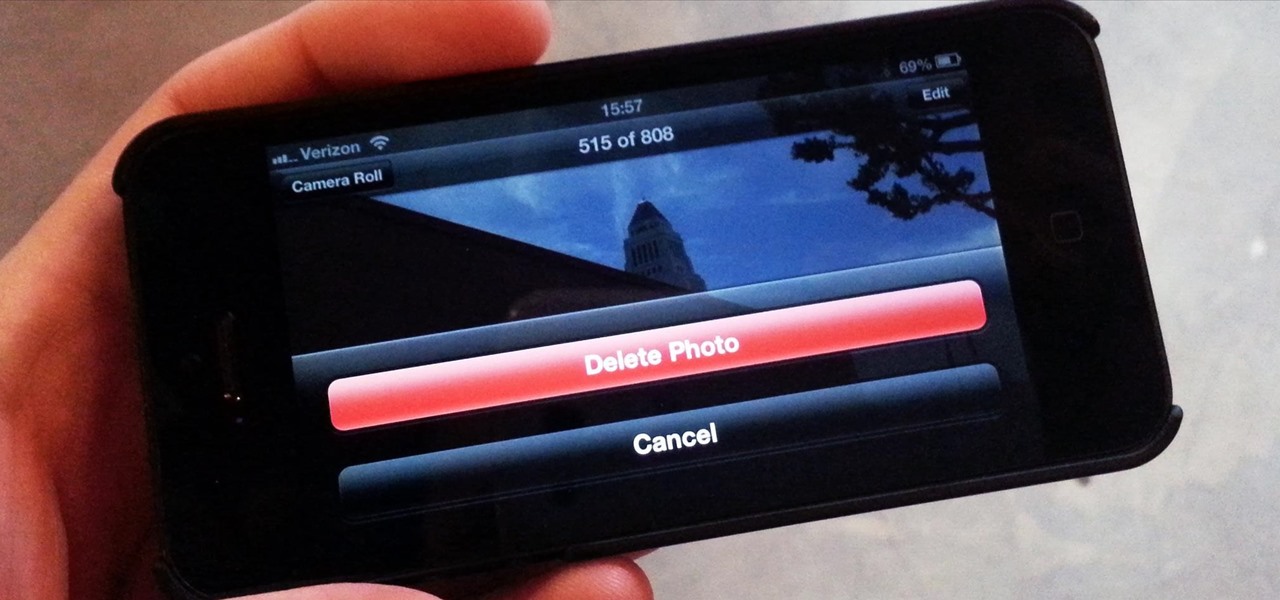
In one of Apple's newer ads, the company claims that "more photos are taken with the iPhone than any other camera." If this is in fact true, then it might also be appropriate to say that more photos are accidentally deleted on iPhones than any other camera.

Most of us have conducted an investigatory science project without even knowing it, or at least without knowing that's what it was called. Most science experiments performed, from elementary to high school students and all the way up to professional scientists, are investigatory projects.

Living in Los Angeles has given me the opportunity to attend a bunch of really cool events. I've been to Dodgers, Lakers, and Clippers games, a few concerts at the Staples Center, and a plethora of smaller joints.

A few weeks ago, Facebook published a blog post called "Proposed Updates to our Governing Documents," which outlines a few changes in their policies and user voting system. These changes would essentially take away users' right to vote on future changes to Facebook's data use policy while also taking away Facebook's responsibility to alert users of those changes. If the new policy is enacted, the vote will be replaced with "a system that leads to more meaningful feedback and engagement," what...

All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

Samsung and Google have done some amazing work together in the past, particularly with Android related projects. But after years of an inexplicable lack of interoperability, the primary smart home hardware divisions from both companies are finally on the same page — starting right now.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

Apple has introduced several new features to its native Messages app with iOS 14. When it comes to group chats, you can now pin those conversations, use inline replies, and receive notifications only when you're tagged. And if that wasn't good enough, you or anyone else in the group can assign a photo for the entire group.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

Recording phone calls has always been tricky due to legal, ethical, and technical considerations. With iOS 18.1, Apple brings your iPhone a native call recording feature that simplifies this process while addressing privacy concerns.

Apple Maps keeps getting better and better for all the hikers in the world. The latest update gives you access to thousands of detailed trail maps within U.S. national parks and topographic views, but it also lets you create your own walking and hiking routes.

Apple's upcoming iOS 17 is expected to include many new features first seen on Android, but there are also some exciting, unique features that Android needs to steal pronto.

There's more than one way to get free credits and discounts in the Google Play Store for apps, games, books, movies, in-app items, and other Play Store content. You may know a few of them — but some of these may surprise you.

There are two types of people in this world: those who recognize Wordle grids of yellow, green, and gray/black blocks and those who do not. No matter which category you fall in, there's a Wordle-inspired game that's perfect for you.

While hitting snooze won't help you much if you fall back asleep, it can help you wake up more gently. However, your iPhone's default nine-minute snooze may be too long or too short for your preferences. If you tend to fall back asleep quickly, you might be better with a two-minute snooze.

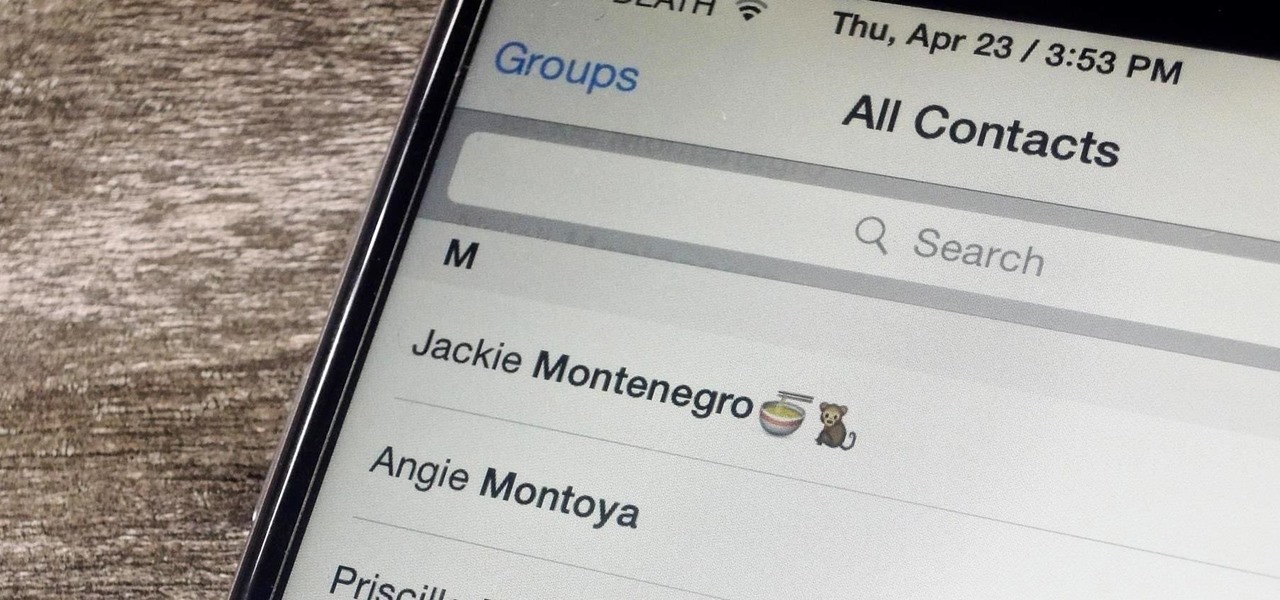
You can view and hide iCloud contact groups on your iPhone, but Apple won't let you create or delete groups or add or delete contacts from any groups unless you're on a tablet or computer. Why Apple refuses to add a group management tool to Contacts on iOS is anybody's guess, but there is a workaround you can use instead.

Downloading content from TikTok is relatively easy, even if the video is protected, but the same can't be said of Reels, Instagram's version of short-form videos. Instagram doesn't make it easy to download content unless it's your own, and that's especially true with Reels. However, there is a way to bypass Instagram's restrictions on your iPhone and save videos locally without ever leaving the app.

When it comes to the ever-shifting sands of the augmented reality space, you never know which week will end up being truly historic. Well, this one was one for the history books.

Amid a troubling resurgence in coronavirus cases, led by the new Delta variant, augmented reality is once again moving back into the spotlight as a solution, especially now that the move to return to offices has been stalled.

Over the past week, practically every major tech company working on augmented reality has held their quarterly earnings calls with investors, and each addressed or at least mentioned the role of AR during their prepared remarks. However, Facebook's earnings call had some of the spicier commentary on the technology.

Brands are increasingly adopting augmented reality to promote their products and services, and they have multiple paths for bringing AR experience to their audiences.

Ever since Facebook announced its partnership with Luxxotica brand Ray-Ban to produce smartglasses, the augmented reality space has been on high alert awaiting more details.

Magic Leap has had a rough couple of years, highlighted by high-profile executive departures, lawsuits, troublesome patent shuffles, and massive layoffs.

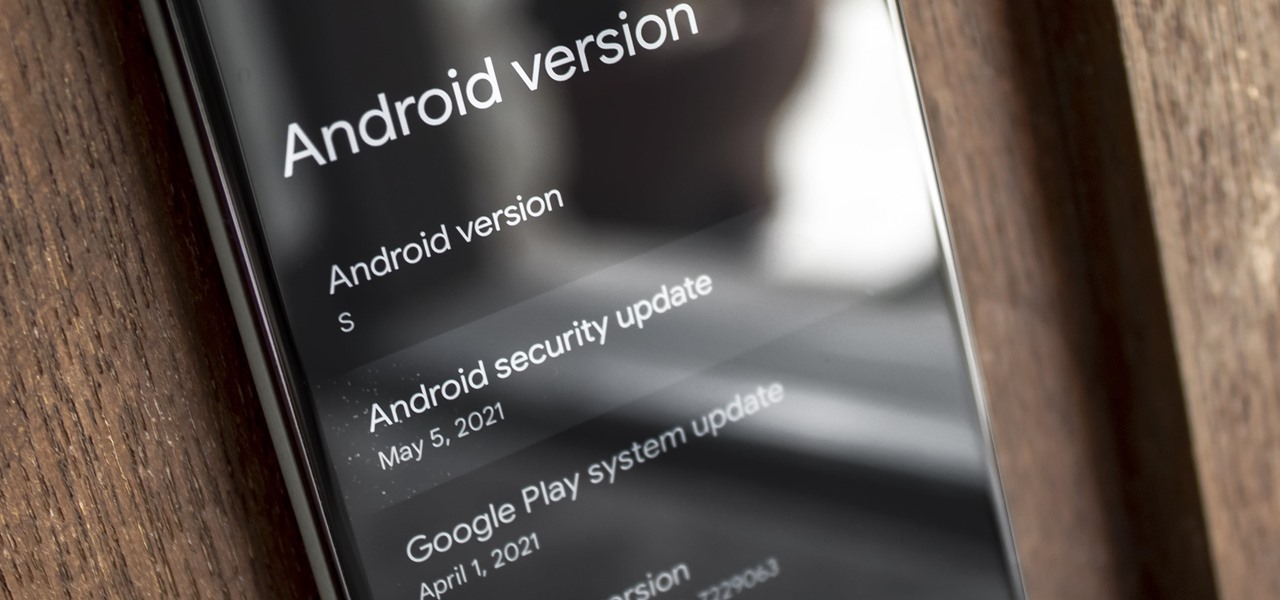
Numerous potential exploits are found for every operating system each month, and Android is no exception. Trouble is, lots of Android devices don't receive timely updates — but many are now getting regular monthly security patches to at least shore up these vulnerabilities.

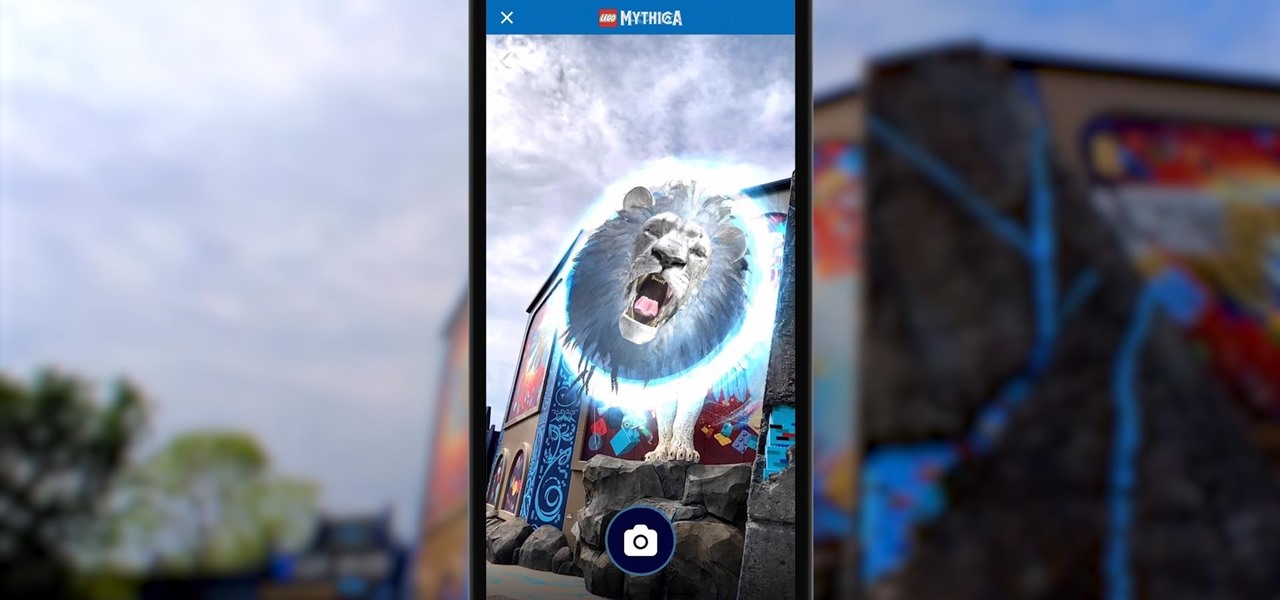
Few brands have been more enthusiastic about augmented reality than Lego, which has now expanded its AR experiences from toys to theme parks.

If you've recently built a Wi-Fi spy camera out of an ESP32-CAM, you can use it for a variety of things. A baby monitor at night, a security camera for catching package thieves, a hidden video streamer to catch someone going somewhere they shouldn't be — you could use it for pretty much anything. Best of all, this inexpensive camera module can perform facial detection and facial recognition!