Gender standards are entirely pervasive. We raise our sons to be masculine and our daughters to be feminine, which perpetuates the gender role formula when they grow up to be parents and raise their own children. Part of this whole equation is that boys are supposed to remain stoic and project an air of strength, and girls are expected to be amiable while being held to unrealistic standards of outward beauty.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Let's take a minute and talk about something you're doing wrong — using the restroom. Many view the subject as improper or even taboo, but why? Thanks to your upbringing, you've assumed you know the basics... But you don't. Avoiding discussion on the subject has led many of us to unwittingly interact incorrectly during our private time with our old friend, Jon.

Is there a black or yellow mustache stripe? This is just one of the physical characteristics you will need to know to determine what kind of meadowlark you are looking at. Take a minute to enjoy the outdoors while identifying the distinct sound, look and location of meadowlarks.

You don’t need a camera to recreate a picture you see. Choose and object and with only a pen and pencil you can recreate that object as a sketch. Take your time, and choose somewhere quite where you can focus on your creation.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade EXT Premier Telescope to ogle the universe.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade EXT-80-TC Telescope to ogle the universe.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade AZ Series Telescope to ogle the universe.

Accents are not only fun but attractive too, when done properly, at least. Work on your Irish accent, practicing the inflection and sound of consonants and vowels. Impress your friends with your new accent.

In this video, viewers learn how to skip YouTube pre-roll ads. These ads last 15-20 seconds long and appear at the beginning of some YouTube videos. To skip these ads, users simply reload the page. Once they reloaded the page, the video will automatically start. This video contains voice narration for guidance and a visual demonstration for viewers to easily observe and follow along. This video will benefit those viewers who watch videos on YouTube and want to avoid this problem.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Exposed to hormones, pharmaceuticals, and other chemicals, the beautiful wild fish in Canada's Grand River have taken on some pretty odd characteristics—they're turning into females. A long-term study suggests using bacteria to manage polluted water could turn the tide for feminized fish.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

March is looking to be an eventful month for Apple. Even with coronavirus throwing the tech industry into uncertainty, we still expect Apple to release the iPhone SE 2, the long-awaited follow up to the iPhone SE. Is it possible we'll also see iOS 13.4 fully released this month? We wouldn't be surprised if we do, seeing as Apple just released its fourth developer beta.

In the late nineteenth century, the advent of the motion picture wowed audiences with a new storytelling medium. Nearly a century and a half later, augmented reality is establishing a new frontier in film.

While the automotive industry is moving towards adopting AR displays in future models, BMW is already shifting into the next gear with its vision of the technology.

Samsung, like other OEMs, partners with third-party companies to include their apps on Galaxy devices. For example, Microsoft pays Samsung millions to pre-install certain Office apps. But one of these partners might not be on the up and up.

Those going on crazy off-road adventures, taking their inspiration from various SUV commercials, are likely to encounter many unexpected, all-terrain dangers.

Thanks to improvements in technology, AR has become more prominent on our phones. With all the power of the Galaxy Note 10 and Note 10+, Samsung decided to add some pretty nifty AR features. One of these is the new AR Doodle mode, a feature that will make your videos pop.

Amid the opulent and historic confines of Paris, Microsoft is now hosting an exhibit at a local museum that brings a historic map of a Normandy tourist destination to life in augmented reality.

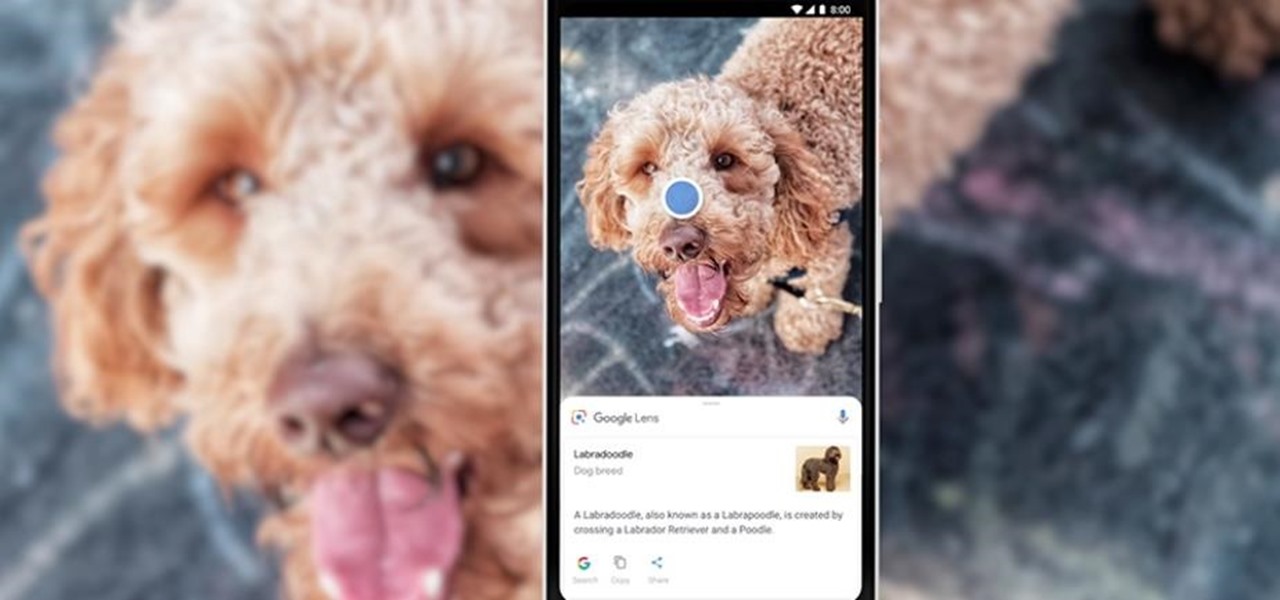
During Tuesday's keynote at the I/O developer conference, Google unveiled new capabilities for its Lens visual search engine and expanded the availability of the platform in smartphone camera apps.

A development duo has concocted an iPhone app that displays related tweets based on objects recognized by the device's camera.

We may not know what Magic Leap's product looks like. And we haven't received even a "save the date" for its launch. But we know that it will display mixed reality comics from Madefire when whatever it is arrives.

Directive Games received the enviable honor of unveiling their ARKit game, The Machines, on stage as part of Apple's iPhone launch presentation.

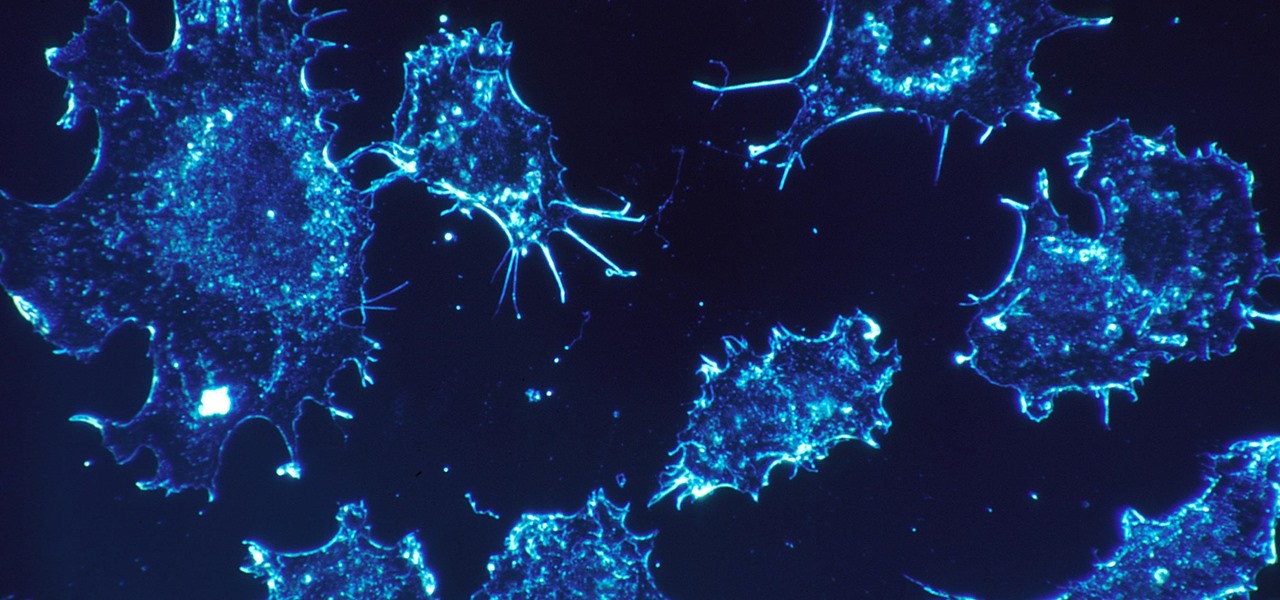
As our cells age, they eventually mature and die. As they die, they alert nearby cells to grow and multiply to replace them. Using a special imaging process that combines video and microscopy, scientists have observed the cellular communication between dying and neighboring cells for the first time, and think they may be able to use their new-found information against cancer cells, whose damaged genomes let them escape the normal dying process.

Wound infections don't usually enter the blood and become systemic, spreading the infection throughout our bodies, and there's a good reason for that: Our bodies actively work to prevent it, according to research that discovered a new use for a protein first discovered decades ago.

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.

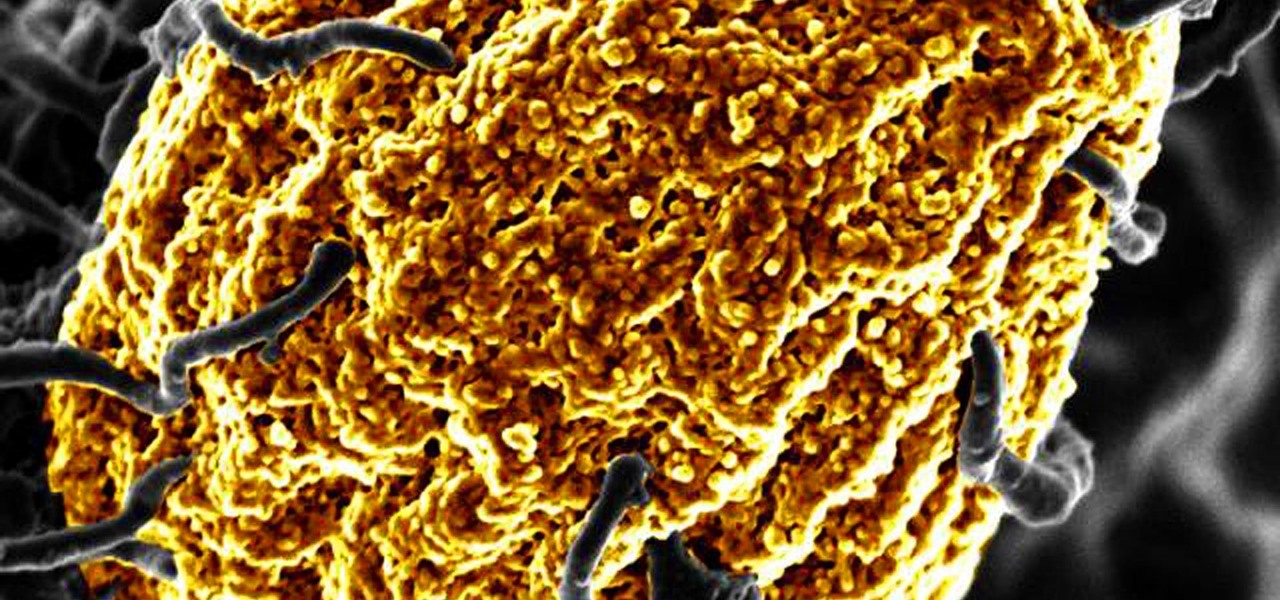
We usually associate Salmonella bacteria with a dangerous type of food poisoning, but they actually are pretty good at seeking out tumors. That trait made the bacteria a great candidate to deliver a protein that would help knock tumors out.

Sleep lets our body processes rest and restores us for the next day, so a bad night's sleep can ruin the following twenty-four hours and even make us feel sick. Now, new research published in the journal Sleep cements the idea that loss of sleep actually leaves us vulnerable to sickness.

For anyone who has spent an entire afternoon attempting to assemble a set of IKEA chairs, these wooden masterpieces probably seem pretty appealing.

Hello, this is my first post on Null-Byte. This is made for those who have an interest in writing into another processes memory. Why would you want to do this? Who knows, personally I just wanted to mess around with games on my computer(have unlimited health).

Last year, The New York Times wrote that certain restaurants in Manhattan and Brooklyn banned patrons from taking photos of their meals. That means no flash photography, no standing on chairs for a better angle, not even a quick pic for your Instagram followers before the first bite. Little do these restaurants know, this ban can actually make their customers' food taste worse, so to speak.

Someone does't really like you. I don't know who or where they are, but they exist. If you want to change that, simply ask them to do you a favor.

The Geminid meteor shower happens every December and has been observed for over 500 years. It's is also known as Winter's Fireworks because when viewed from the right location, there are enough meteors to light up the whole night sky, and some of them can even be different colors. The shower appears to come from the Gemini constellation, but is actually caused by Earth passing through the tail of dust and debris left behind by the comet 3200 Phaethon.

All you science and astronomy nuts out there, pay attention, this detailed video tutorial series will tell you everything you need to know about using the Meade ETX-AT Series Telescope to ogle the universe.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.