My bathroom is like my own private arcade room. Whenever I'm seated comfortably on the toilet, no one is going to disturb me, so I can play anything I want on my smartphone. You probably do it, too — and your parents, kids, friends, colleagues, and boss — so don't be afraid to admit it.
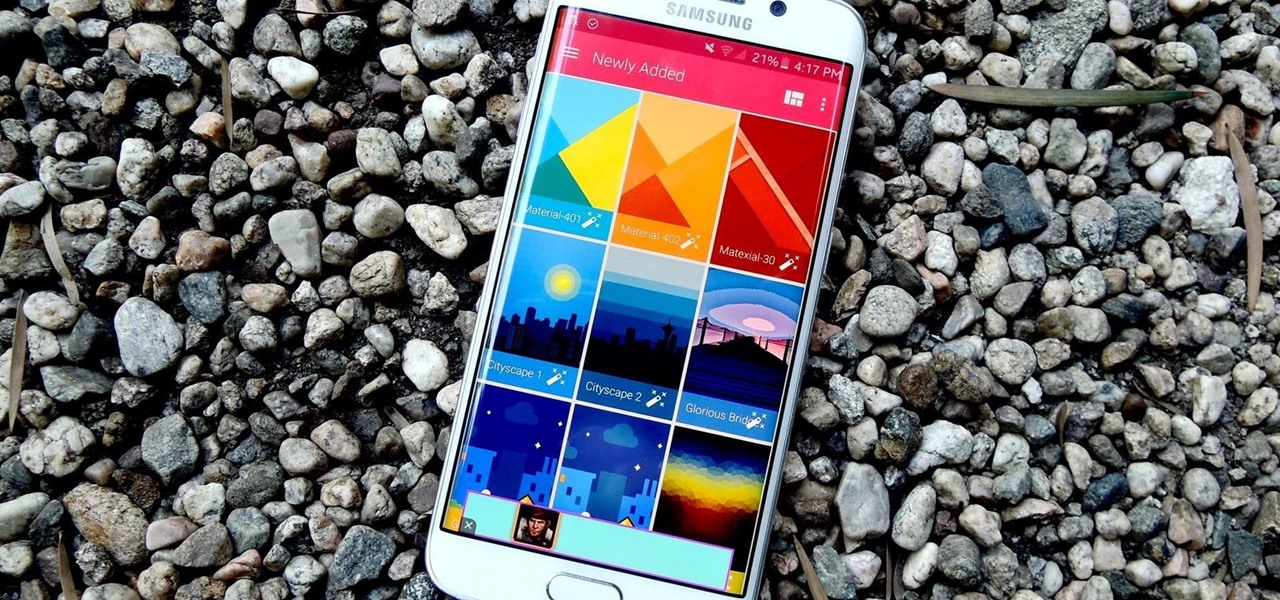
Out of all the questions that we receive from our readers and viewers here at Gadget Hacks, the most frequently asked one is "What wallpaper is that?" On occasion, our wallpapers may be personal or images from the web, but for the most part, they come from dedicated wallpaper apps.

A good, sharp knife is a cook's best friend, which is why there's so much passionate debate about what kind you should get. Most enthusiastic home cooks opt for a stainless steel knife, but it turns out there's a different option that the pros favor, and that's carbon steel.

Pizza. It's seen you through your best and worst times. It was there during your first relationship and the subsequent dumping. It got you through college, and maybe even your twenties. Domino's phone number is programmed in your speed dial, and though you won't admit it out loud, you love pizza, you really do.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

There are a lot of people out there who don't like vegetables, but I would contend that that's because they haven't eaten any really good vegetables. I thought I hated tomatoes (okay, technically a fruit, but used mostly as a vegetable) until I ate some fresh from a garden. One bite of a juicy, ripe heirloom tomato made me realize that I love tomatoes—it's those bland, mealy supermarket tomatoes that I hate.

Biting into a perfectly ripened piece of fruit is enough to convince you to give up baked goods and plant your own garden. The combination of flavor, juice, and sweetness in a ripe mango, apple, plum, or berry is the stuff of life itself.

It's nice to have a drink on an airplane, whether you're taking a flight somewhere fun or for work. However, what's not so nice is the high prices and relatively bad quality of the liquor that's available.

You know you've had a long day when you head home with a headache, back pain, and eyes so sore they feel like they might roll out of your head. Turns out your medicine cabinet isn't the only place you can find help—instead of popping painkillers, just open up your wallet for instant pain relief.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

How to easily build a raised garden bed out of wooden pallets for free! …Well almost free. Building a raised vegetable garden with pallets or reclaimed wood is a really rewarding experience. The garden bed idea out of pallets came about from the fact that l wanted to build a rustic looking raised garden bed. A vegetable garden bed that not only provides delicious food, but looks good at the same time. The recycled wood has come from hardwood timber pallets that have been sourced totally FREE ...

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

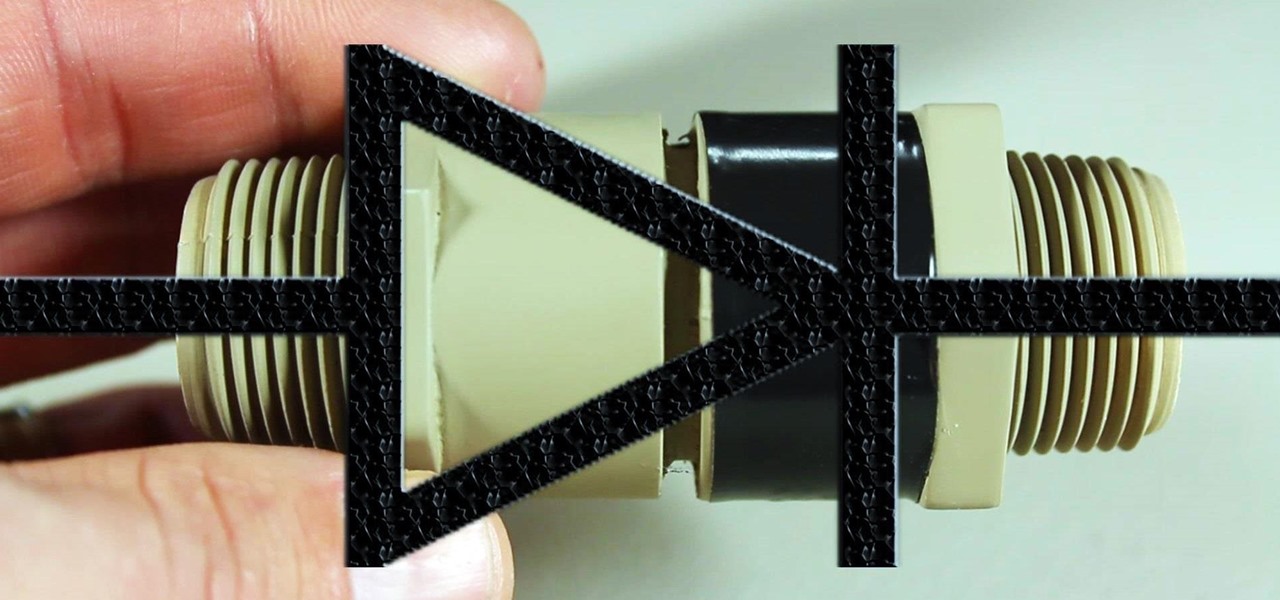
If you're going to build yourself a water gun to cool down this summer, or maybe just a useful water pump, you'll need some check valves. However, the most expensive parts of a water pump or DIY super soaker are usually the check valves. So, let's make some from scratch for as little as $0.35 each.

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Pronunciation is key to learning any new language. Before diving into the vocabulary and basic phrases, a good approach is to listen and try and get your aural perception honed in. A new word or phrase, like "je m'appelle" in French, is awesome to learn, but it's important to learn it correctly: that starts and ends with pronunciation.

The most recent premium flagship smartphones from Google — the Pixel 7 Pro and Pixel 6 Pro — are equipped with displays cable of 1440 QHD+ resolution. But they also come with a tool to downgrade to 1080p FHD+, which you may want to do in certain situations.

After years of testing and modifications, the US Army is moving forward with its customized version of HoloLens 2 from Microsoft.

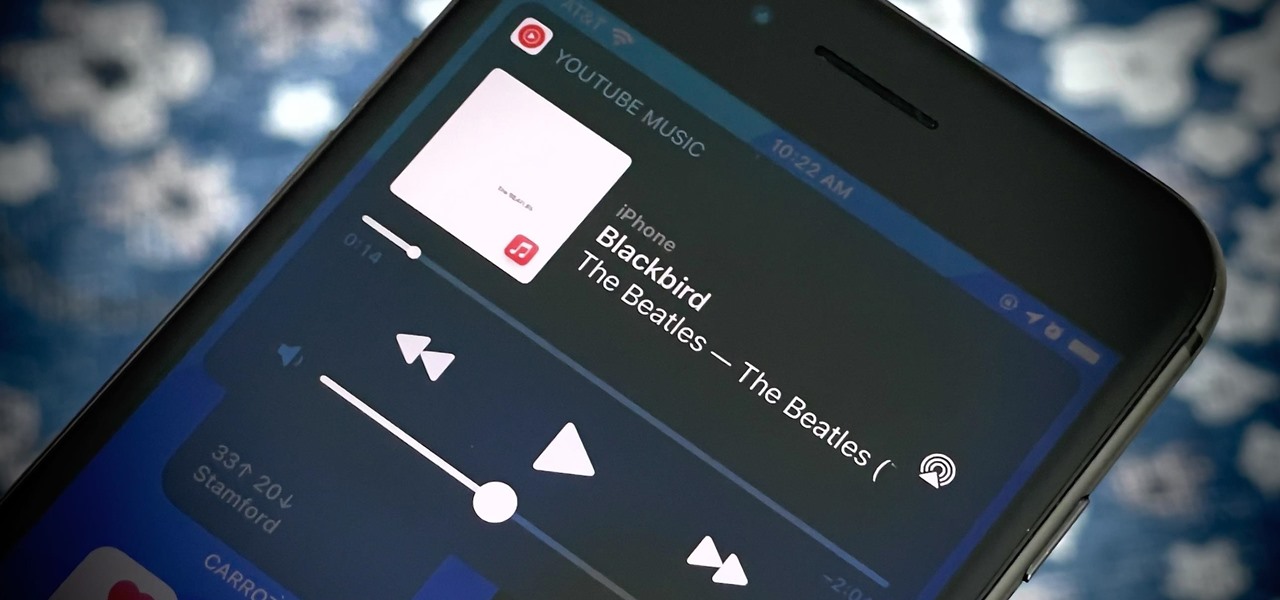
A new feature in iOS 14.5 lets you change your preferred music player for Siri requests. So if you primarily use YouTube Music over Apple Music and other services, Siri will learn so that you never have to tell the virtual assistant to play a song, artist, or album "on YouTube Music" again.

Up and coming Los Angeles-based rock group Palaye Royale has managed to grow a substantial social media following, and now the group is looking to grow its fan base through the power of augmented reality.

Niantic recently added a new Field Research task type called AR Mapping that challenges players to capture video footage of PokéStop landmarks and upload them. In return, players receive rewards in the form of in-game items.

This week, developer Niantic began rolling out a new feature called AR Mapping to Pokémon GO that has bigger implications on the realism of augmented reality in mobile gaming and beyond.

Apple just released the third developer beta for iOS 13.6 today, Tuesday, June 30. This update comes three weeks after the company released the second 13.6 developer and public betas, which changed the name of the software from 13.5.5. It also comes eight days after Apple released the first developer beta for iOS 14.

A modern iPhone is capable of running sophisticated, exquisitely-rendered games that rival titles on current-generation consoles. However, there is some value in classic video game titles, whether you grew up playing games on the Atari 2600, Nintendo Entertainment System, and Sega Genesis or not.

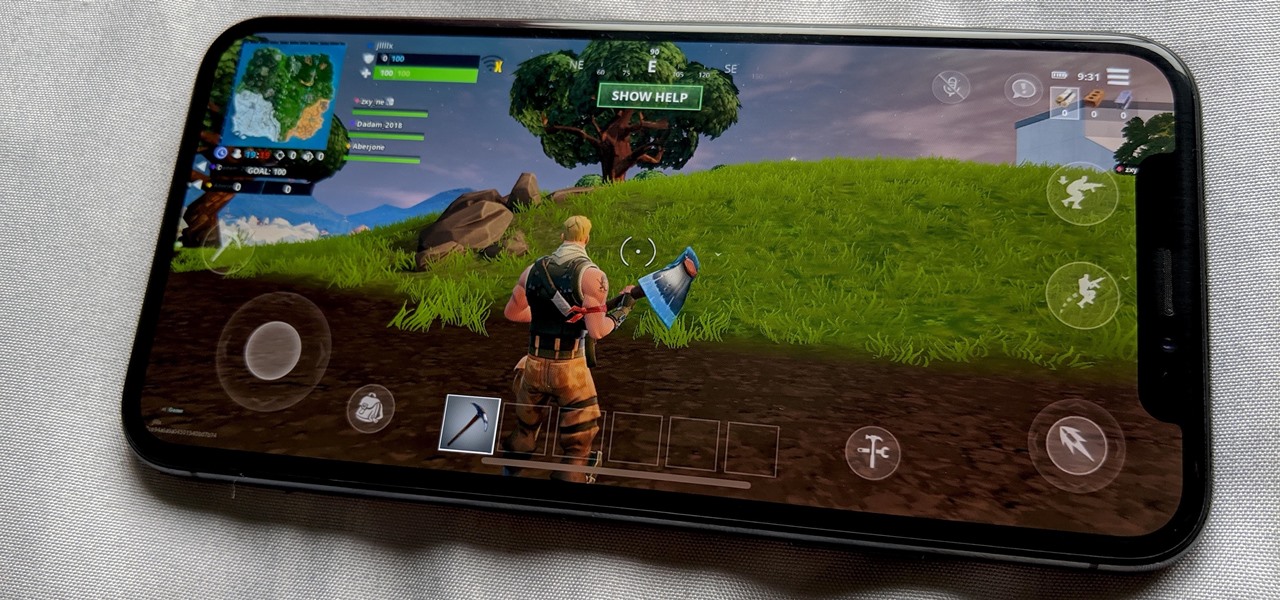
The COVID-19 pandemic has practically shut down all sports except for World Wrestling Entertainment, which has continued staging matches without an audience, leaving us sports fans with nothing much to cheer for. While they can't replace live games, smartphone games provide an alternate reality to live out our competitive entertainment in the absence of the real thing.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

Phone specs get better and better each year, and multiplayer mobile games are right there with them. Instead of playing solo, jump into some real-time gameplay with co-op and player vs. player modes, and battle friends, family, and strangers from around the world. But which multiplayer games are worth your time on Android or iOS?

Action games encompass a wide array of categories, ranging from racing games that pit you against players the world over for track domination, to endless runners that push you to set ever higher scores, and RPGs that let you embark on adventures in fantasy worlds. With such a huge selection of titles to look through, it's all too easy to overlook a game you might otherwise like.

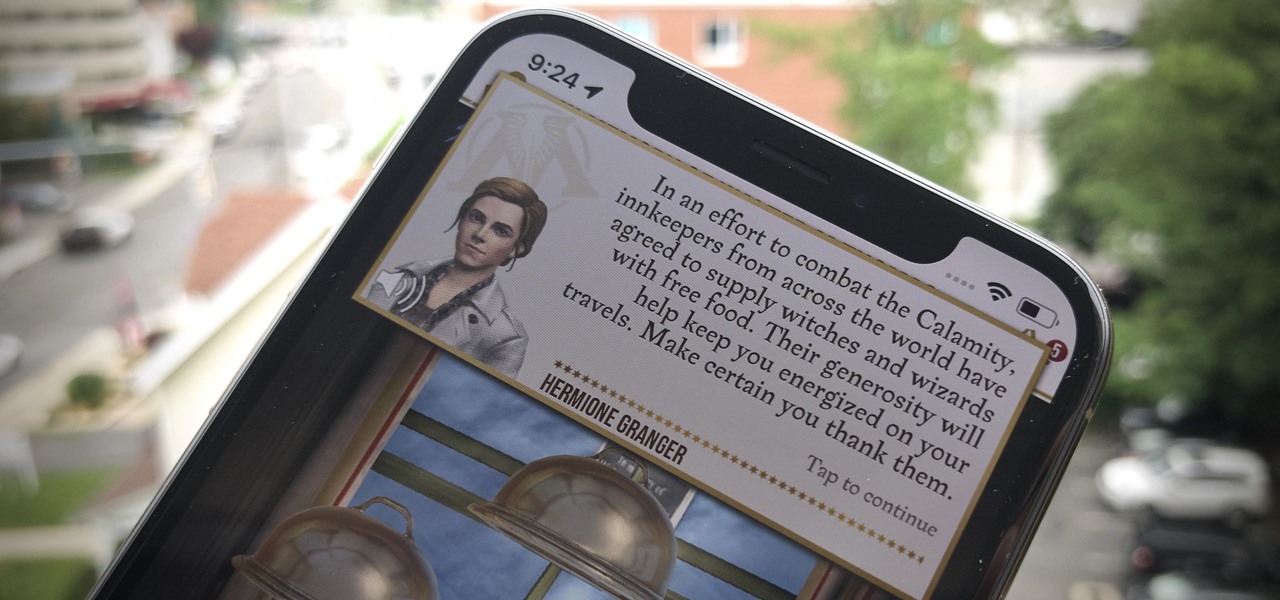
We Harry Potter fans all remember Hogwarts students pulling Mandrake Roots in the greenhouses in Chamber of Secrets. Well, in Harry Potter: Wizards Unite, we now have an opportunity to work in our own Greenhouses, as well as dine inside Inns scattered throughout the map. Let's take a look at how these two establishments help you along your magical AR journey.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

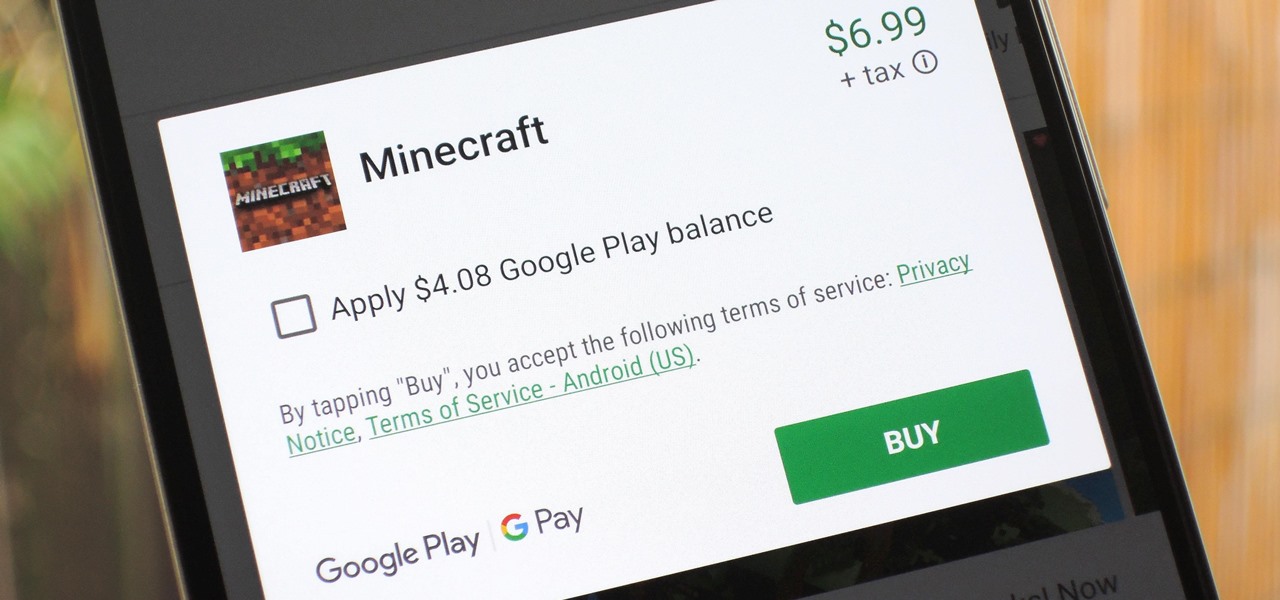
The iTunes App Store makes it easy to buy an app or game on someone else's behalf, and it's a great way to send an iPhone user a thoughtful gift. The Google Play Store doesn't have such functionality, but there are still a few workarounds to accomplish the same goal: gifting an app to an Android user.

Like many things associated with Magic Leap, the start of the company's first annual L.E.A.P. conference got off to a unique start. Taking the stage on Wednesday morning in Los Angeles, the company's CEO, Rony Abovitz, gave a brief introductory speech welcoming the crowd and outlining the mission of Magic Leap.

Reconnaissance is the phase of an attack where a red team or hacker designs a strategy based on the information they can learn about the target, as well as what the available attack surface looks like. These scans can take time to discover relationships, but Raccoon OSINT scanner coordinates multiple automated scans to produce invasively detailed reports on a target with a single command.

Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your child could do if they were able to harness this technical aptitude and put it to good use — and they can, with learning apps.

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

For all those times when an app either isn't available or simply won't cut it, your phone's internet browser provides access to your favorite websites and services. But some browsers are flat-out better than others, and chances are, the browser that came pre-installed on your phone isn't the best option out there.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.