The number of households in the US that go hungry because they lack money for food hit a high of almost 15% in 2011. While that number continues to decline, nearly 13% of American households still go hungry.

We continue to field stories underscoring the strong trends of Investment in augmented reality in various sectors. This week, one company strengthens their offerings to the enterprise sector, while two other companies capitalize on the promise presented by augmented reality to consumers – specifically, in gaming.

A few years ago, the Hilton hotel group unrolled the Digital Key, a feature of the Hilton Honors app that allows you to unlock your hotel room with your smartphone.

More platforms and more tools to make content for those platforms. It seems like the Dev Report —Next Reality's breakdown on the latest information on tools and processes to make augmented reality experiences — is going to be coming out on a much shorter cycle.

Meta Company filed suit today against a former employee and his startup DreamWorld USA, Inc. for the misappropriation of trade secrets and confidential information.

Magic Leap has always been intensely secretive about its work on its augmented reality headset, so it's interesting that they're now publicly recruiting developers to build software for the device before its launch.

The driverless competition is heating up as Detroit automakers attempt to woo tech talent away from some of Silicon Valley's biggest players.

Final Fantasy XV, the latest release in the long-running Final Fantasy franchise, has been a massive success, shipping around 6 million copies worldwide in less than two months. Final Fantasy XV: A New Empire is a mobile game based off this popular console iteration, and has surfaced in New Zealand for download.

As someone who grew up adamantly complaining every time my parents dared to turn on talk radio in the car, I can admit it's a bit weird that I have a love affair with podcasts. I can't help it! Even though podcasts are essentially the modern-day customizable talk radio, I choose to defend my all-out obsession with pointing out how popular they are (I mean, SNL even picked up on the trend).

Having a Clostridium difficile infection means stomach pains, diarrhea, fever, and loss of appetite, and if the symptoms weren't bad enough, the disease often reoccurs. Now, new research has found an increased risk of recurrence in people who take medication to treat their stomach acid, gastroesophageal reflux disease, peptic ulcer disease, or stomach discomfort.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

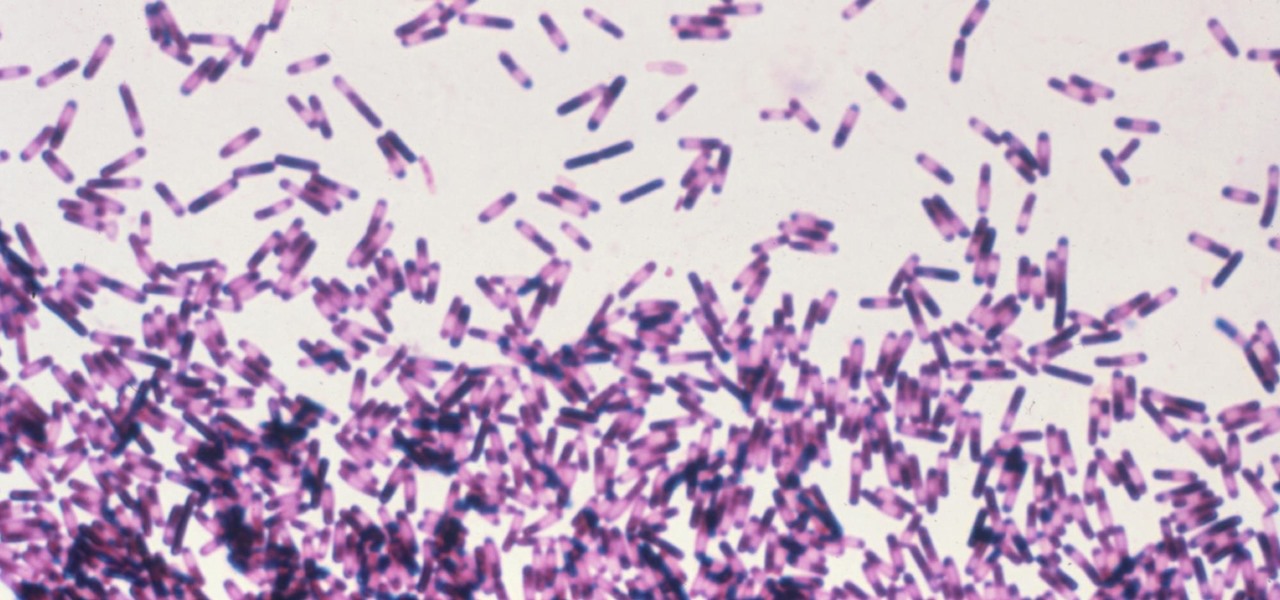
Some bacteria can already do it—generate electric current, that is—and those microbes are called "electrogenic." Now, thanks to the work of a research group from the University of California, Santa Barbara, we know how to easily turn non-electrogenic bacteria into electricity producers.

No one can dispute the evolutionary success of bugs. The oldest insect fossils were found encased in crystallized mineral silica in Scotland in 1926, and they're between 396 and 407 million years old.

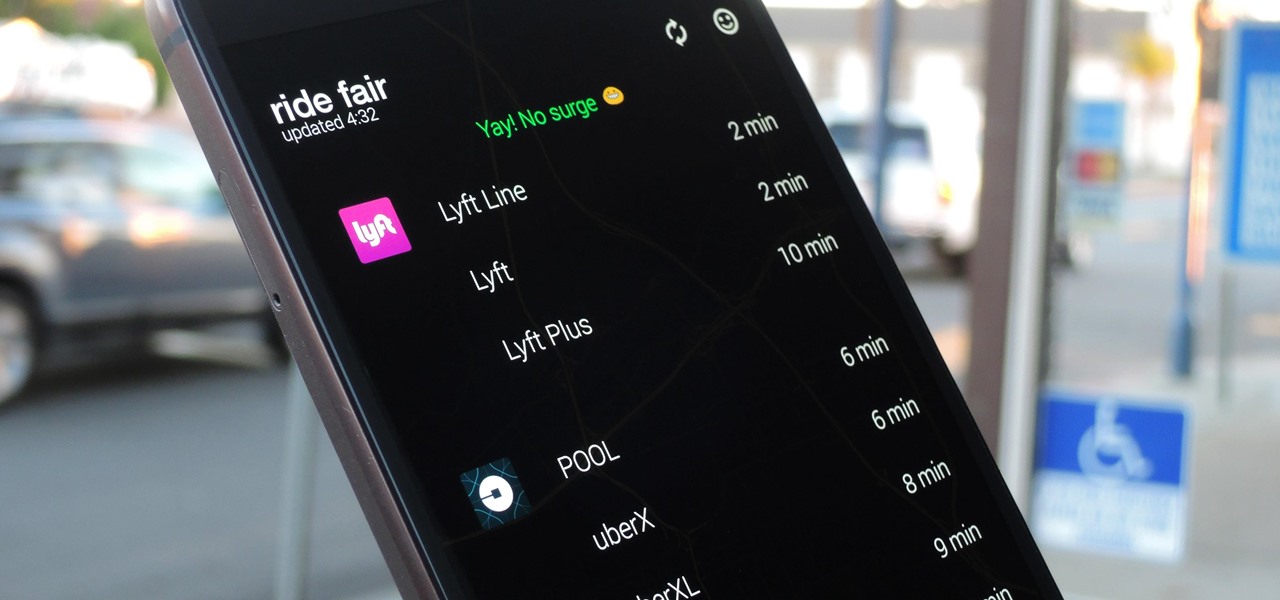
With the exception of New York, D.C., and maybe San Francisco, public transportation in the United States is downright abysmal. Like it or not, you need a car to get around. This is why Uber and Lyft have seen so much success in recent years. Both ride-sharing services get you from point A to point B in an efficient manner, and they do it without costing an arm and a leg. Well, in most cases.

Google's Pixel and Pixel XL flagship phones are a rousing success, with consumers praising the fluid user experience and overall performance as two of the devices' biggest strengths. But even though Google may have knocked it out of the park with a set of Apple-like smartphones that "just work," there's still room for improvement in a few areas.

The US Department of Education has put together a competition called the EdSim Challenge with a $680,000 purse to facilitate next-gen education. The event calls upon augmented and virtual reality, as well as video game developers, to bring immersive simulation concepts to prepare the workforce of the future.

The future for the Meta 2 augmented reality headset will have to wait. While shipments were supposedly on their way out back in June, Meta revealed today that they need a bit more time to provide the best possible experience—and that's really for the best.

Pokémon GO has become a cultural phenomenon. Finally, we can do what we always dreamed of back when we were kids—catch Pokémon in real life!

Our brains do a magnificent amount of work to process visual stimuli, but they aren't difficult to fool. Optical illusions can trick our minds into believing what we're seeing is real, even if it's not—and virtual and mixed reality technologies take advantage of this little loophole in our brain to help us accept the unreal.

Amazon has completely changed the way we purchase household items, to the point where many of us haven't visited a big box, brick-and-mortar store like Walmart or Best Buy in years. And when you think about it, all of this success comes down to two main factors—convenience and price.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...

As one of the most popular home screen apps on Android, the Google Now Launcher is used by millions of people across the world. The two main reasons behind this success are its integrated Google Now home page and an elegant, easy-to-use design.

Dried fruit makes a great snack or salad topping, but after a while, they tend to become fossilized, rock-hard versions of their former selves. At this point, most folks probably just toss them out, as they're unpleasant to chew on when eaten raw and even more unpleasant to eat in bread or cooked with other ingredients.

Welcome back, my hacker novitiates! In the previous part of this series, we looked at how to use Metasploit's web delivery exploit to create a script to connect to a UNIX, Linux, or OS X machine using Python. Many members of the Null Byte community have asked me, "Can we do the same for a Windows systems?" The answer is YES!

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

Nowadays, it feels like you can't talk about eating healthy without bringing up quinoa. Quinoa (KEEN-wah) has been the "superstar" of the health movement for a while; 2013 was declared the International Year of Quinoa by the United Nations, and has only continued to grow in popularity with both health nuts and culinary experts alike through the past few years. The true testament to quinoa's success has been its eventual integration into our everyday lives. Quinoa is now very accessible to fol...

The first written account of "stock" as a culinary staple goes back to 1653, when La Varenne's Cookery described boiling mushroom stems and table scraps with other ingredients (such as herbs and basic vegetables) in water to use for sauces. But really, the concept of stock has probably been around for as long as people have been using water to boil food.

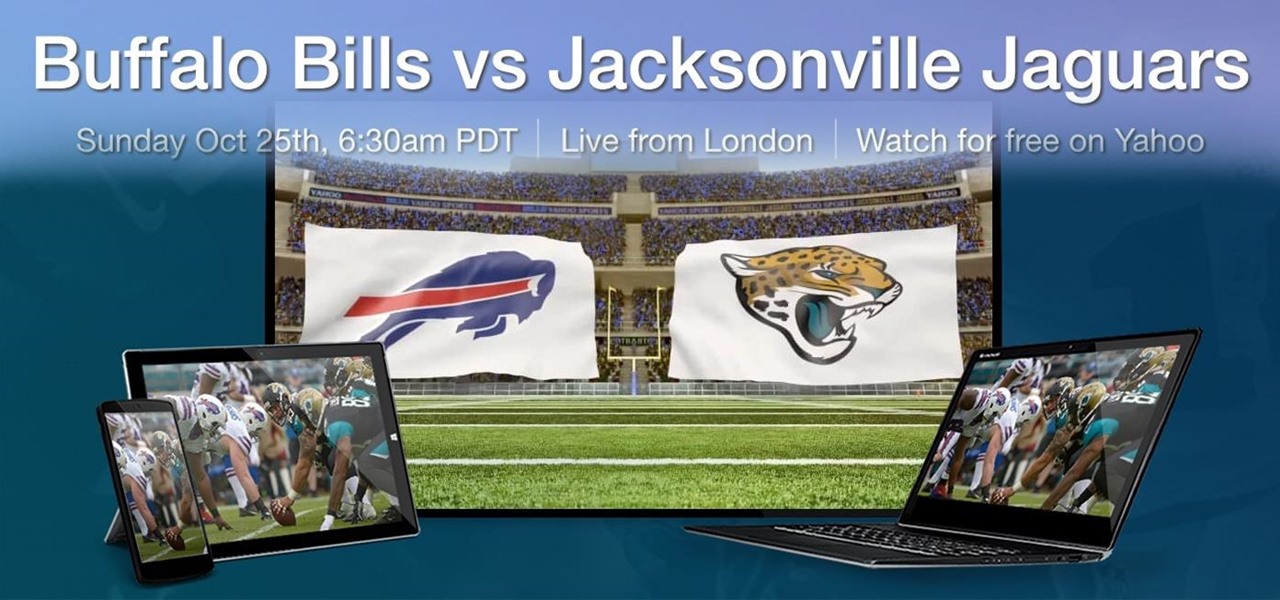
For a lot of would-be cord cutters, the lack of streaming local sports is the only hurdle that needs to be cleared before they can sever all ties with big cable. This is why it was a huge victory for us anti-cable folks when Yahoo announced that they would be hosting the first ever live-streaming NFL game this Sunday at 9:30 AM Eastern.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

Boxed brownie mixes advertise their convenience compared to homemade brownies—with only a few ingredients, they promise a moist, chocolatey crumb. However, these "instant" mixes still require fresh ingredients and a baking time that matches that of homemade brownies. When you're craving a chocolate fix but you're coming up short on eggs, oil, and time, don't despair: you can still make brownies using a can of soda. Two Different Methods, One Soda Required

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

Welcome back, my novice hackers! As most of you know by now, a notorious commercial, legal hacking group named "Hacking Team" was recently hacked. As part of the hack, thousands of emails and other material on their servers was divulged. Among the material released were three zero-day exploits. In this tutorial, we will walk through the steps to load one of them, which has become known as the CVE-2015-5119 exploit.

Welcome back, my hacker novitiates!

I grew up in a rural town, and that meant that we dehydrated a lot of food. Even with a hungry family of five, there was no way that we could eat all of the season's tomatoes before they molded, or all of the orchard's apples before they grew soft, or all of the wild mushrooms that we picked. And so our dehydrator was always getting a good workout.

My morning just doesn't start without a cup of coffee and an incredibly hot shower. There's nothing better than sloughing off sleep with a dose of warm, cleansing water. Except, as scientists are pointing out, our habit of showering daily isn't exactly the healthiest choice. Though it feels great, if you have a shower-a-day habit like I do, you're showering all wrong.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible when you think about all the trees that had to get cut down in order to produce them.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

When Google Play Music launched a few years ago, I ditched iTunes and began using the service as my one and only source for listening to my personal music library. While All Access is great, I still prefer the radio feature on Spotify, so I still use that to discover new music.

Are you a follower or a leader? No matter how you respond, we all know that leader is a more desirable position to hold. Great leaders typically share a few qualities—confidence, intelligence, and strength, to name a few—but one of the most intriguing is their appearance. With the right facial structure, and some well-rehearsed expressions, you can trick others into thinking you're leader material.