Finding an instrumental or karaoke version of a song can be pretty easy unless you're dealing with a song that isn't popular. That leaves you with just the full version of the song, complete with vocals. So how do you convert it into an instrumental or karaoke track?

We often discuss the augmented reality efforts coming from the biggest players in Silicon Valley like Google, Facebook, Apple, and others, but one name that keeps coming up when you really begin to dig into the AR space is Vuzix. Since the late '90s, the company has quietly but deliberately worked to build itself into a viable competitor in the enterprise space via its wearable display technology.

Bloatware is a problem on Android, and it's not just a Samsung thing. Removing apps that have the Uninstall or Disable button grayed out in Settings has always involved sending ADB commands to your phone from a computer, which itself was always such a pain to set up. Thankfully, that has finally changed.

When approaching a target, having a precise and detailed plan of attack is absolutely necessary. One of the main goals is to increase the attack surface since the more opportunities there are for exploitation, the greater the chances of success. Subdomain enumeration is one method used to increase the attack surface, and we'll be using a tool called Subfinder to discover hidden subdomains.

The future of TikTok in the U.S. is all but certain. Microsoft, Walmart, or Oracle could save the day by buying the company, TikTok may win its lawsuit, or China's new restrictions could halt everything — but all could fail. Just like Vine before it, TikTok could be on its way out, only for opposite reasons. But will it matter if TikTok gets banned in the States? With the competition heating up, likely not.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

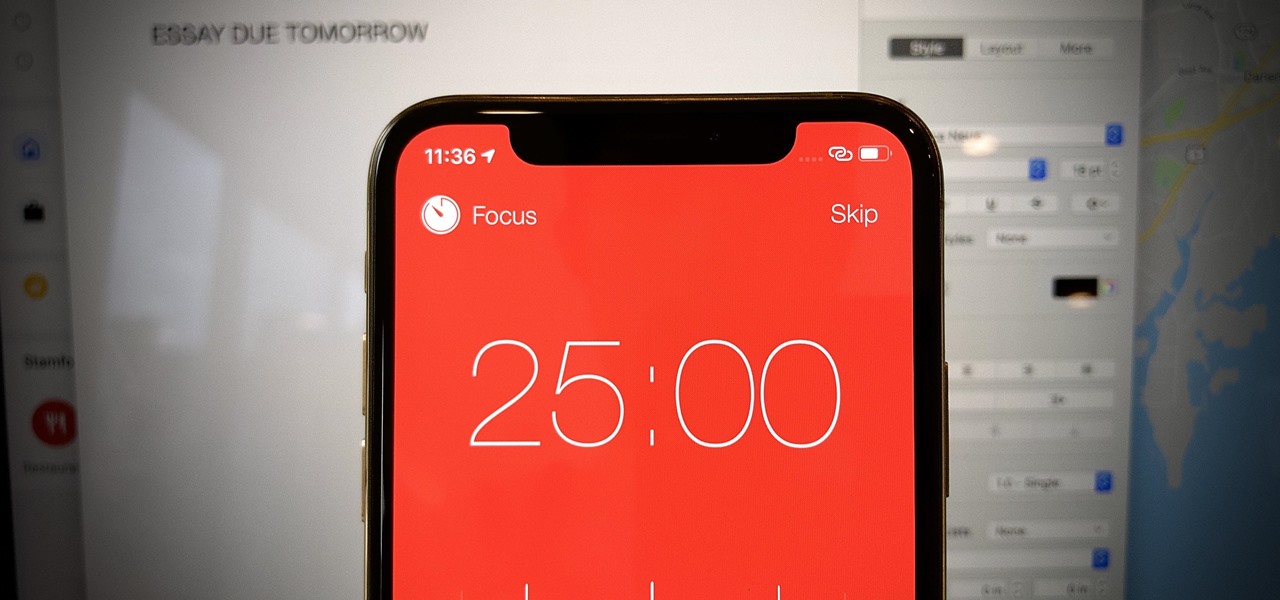
Procrastination is an ugly beast. At first, it seems so innocent to spend five minutes checking Reddit or Twitter. You'll get started on work right after. Next thing you know, it's 1 a.m. and that paper is due in seven hours. Before you start another YouTube video, know you don't have to be like Spongebob. You can be like me, taking control of your productivity with the right app.

Well before Magisk was in our lives, the Xposed framework was where all the mods and magic happened. Magisk was built on a similar concept with the ability to customize your system via modules. We can thank Xposed for where we are today in terms of root-related mods, but it's not done just yet — it's still very much alive and kicking after all these years.

When setting up a Raspberry Pi, it's easy to overlook changing the default password. Like many IoT devices, the Raspberry Pi's default Raspbian operating system installs with a widely-known default password, leaving the device vulnerable to remote access. Using a tool called rpi-hunter, hackers can discover, access, and drop custom payloads on any weak Pi connected to the same network.

Silence spreads over these mountains like nothing I've ever felt. If I didn't have Moby blasting in my earphones, there'd probably be no other sounds around. Well, except for someone, Phil probably, murmuring in a nearby tent just low enough to make his words indiscernible.

Stories are everywhere in social media today, but that wasn't always the case. In 2013, Snapchat introduced the world to these temporary windows into our daily lives. Since then, stories have infiltrated other popular apps. However, to stand out, you can't solely rely on the app where the story will be posted. Instead, you need a suite of apps that can turn your story into something special.

With the list of available mobile apps for moviegoers constantly expanding and improving, seeing a film at your local theater has never been better. With the right apps for your iPhone or Android phone, you can research movies, find out if showings are sold out, reserve seats, save money on tickets and concessions, preorder popcorn and soda, and even find dull bathroom-worthy scenes.

For many, phones are starting to replace televisions as the primary device for watching videos. Thanks to their portability and easy to use apps, it's often simpler to watch Netflix, Hulu, YouTube, or Prime Instant Video on the smaller screen. But not every phone is suited to fit this need, so we did some testing to find the best of the best when it comes to streaming videos.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why you might want to reconsider joining the iOS 12 beta.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

While many of the features in the iPhone 16 and 16 Pro series build on what we've seen in previous iPhone models, Apple has packed the 2024 lineup with iOS 18 and plenty of fresh upgrades worth considering.

A man-in-the-middle attack, or MitM attack, is when a hacker gets on a network and forces all nearby devices to connect to their machine directly. This lets them spy on traffic and even modify certain things. Bettercap is one tool that can be used for these types of MitM attacks, but Xerosploit can automate high-level functions that would normally take more configuration work in Bettercap.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

The App Store has been around for almost 14 years now, and during that time, we must have seen over a million games come and go and stay and expand. But only a tiny fraction of those games have become blockbuster sensations because of the mighty App Store's reach on iPhone and iPad, and many of the first big hits are still alive today for you to relive the good ol' days of mobile gaming.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

If you bought an iPhone or iPad equipped with USB-C but didn't max out the local storage, there are some great external storage solutions beyond iCloud and other cloud storage services. And now that the iPhone lineup comes with USB-C ports, you have better-performing external drives available to you than anything you could ever get for a Lightning-based model.

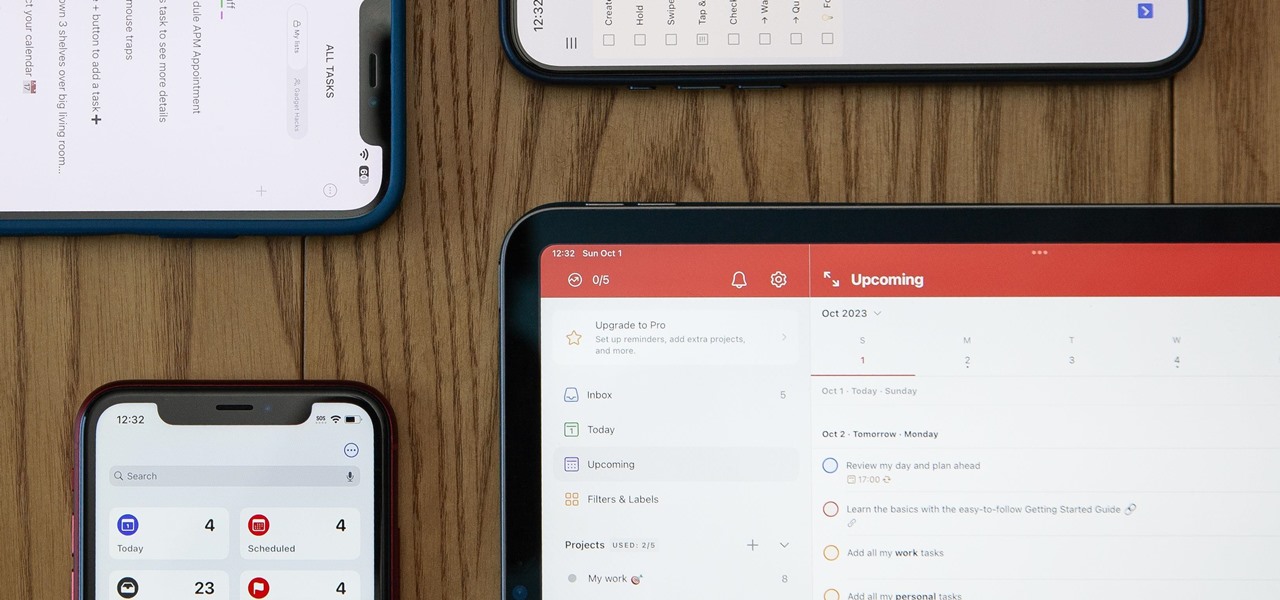
When you want a helpful task manager on your iPhone or iPad, any of the nine apps in this guide should be at the top of your list. But we'll review each app's features to help you determine which one might be best for your workflow.

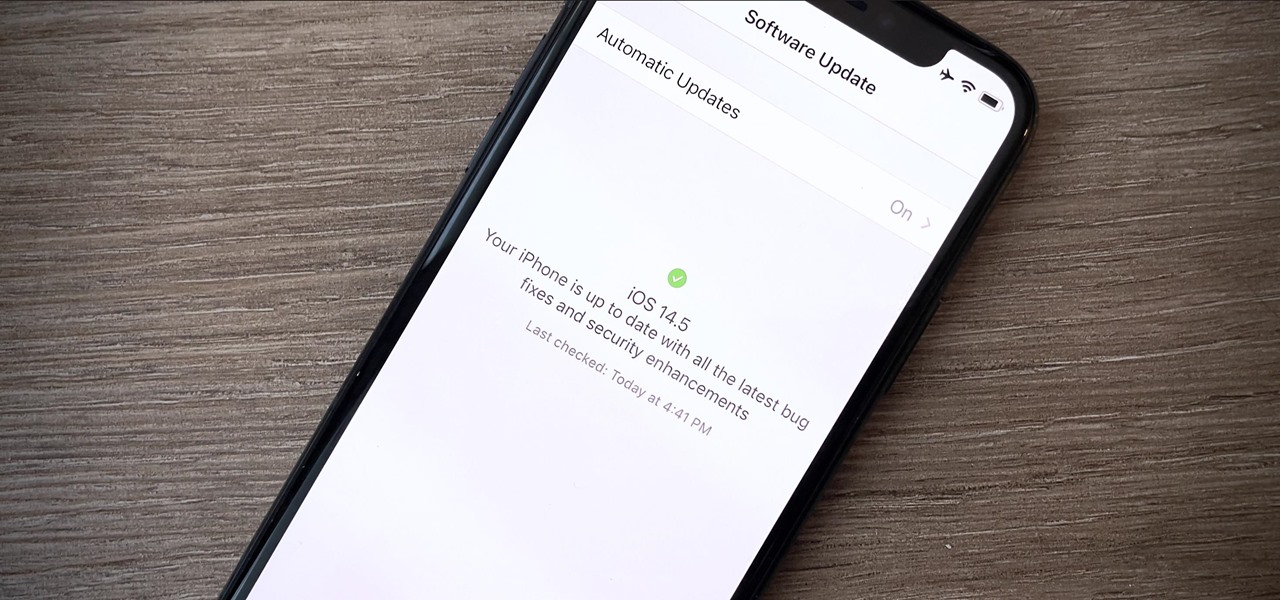
Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy about.

If you've been struggling to get ChickHEN R2 installed and running on a PSP 3000, check out this video.

You either love politics, or you don't, but office politics are entirely different than your local elections. It could mean respect, raises, or could even mean your job. Just staying out of it could stunt your career. Here’s how to jump in and get ahead – without getting burned.

The big problem with sowing seeds indoors is that the light comes from one side and your seedlings will get 'drawn' (stretching towards the light). You can help to get healthy, sturdy seedlings and increase your chances of success if you make a simple box to reflect the light back to your plants. Use this with a propagator or just stand plants in pots in the box. You'll be amazed at how effective it is and it costs virtually nothing. All you need is a cardboard box, which is cut away on one s...

Tests can be anxiety provoking even when you are confident on the material. Try to relax and further put your mind at ease by having a good strategy for dealing with a multiple choice test . With a little bit of practice you’ll by acing tests in no time.

Earning more money in YoVille doesn't have to be hard and take forever. You can make more cash simply by hacking your way to success with the notorious Cheat Engine program.

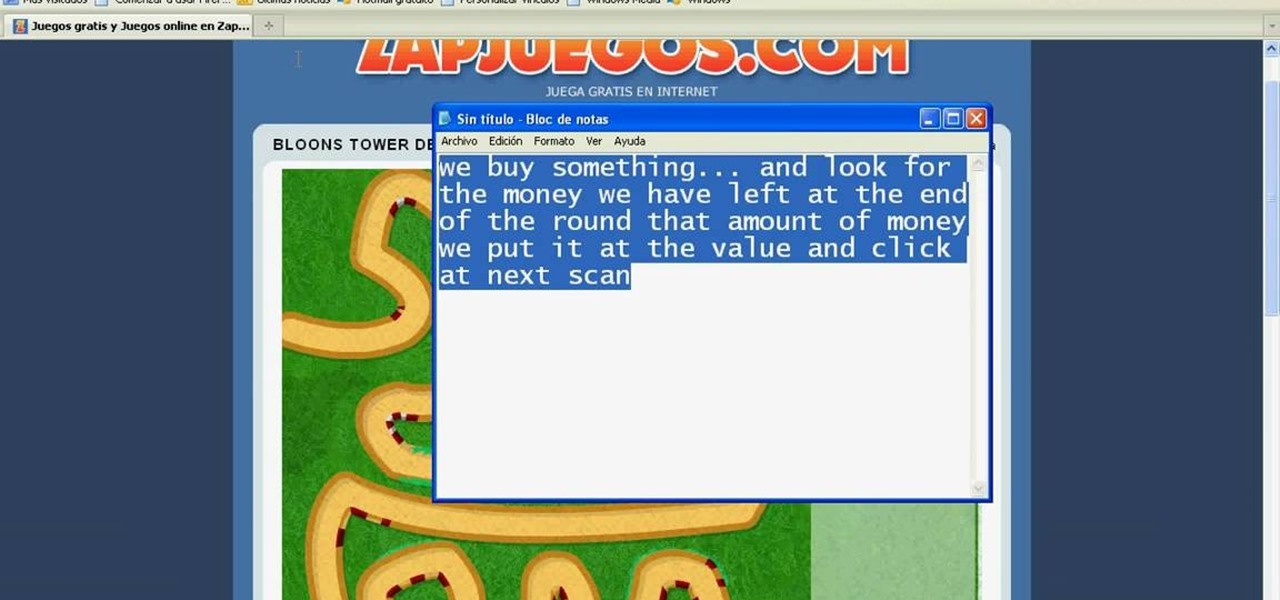
Hacking money in BTD3 is the key to success. And how do you plan to hack Bloons Tower Defense 3 money? With Cheat Engine, of course.

In this video series, watch as graphic design expert John Moore teaches how to design a logo. Learn what software you need for logo design, how to prepare for logo design, the importance of text, the importance of color, the use of different fonts, how to manipulate graphics, how to use filters to enhance text, and how to use wingdings to design a logo. Coming up with a recognizable brand and logo is essential to the success of any company or small business, so let the experts at Expert Villa...

Understanding the different types of horse racing is crucial to your betting success. Researching a horses background will help you pick the winning horse. Making sense of the numbers is very important. Watch this video tutorial for all you need to know to wager correclty on the right horse at the tracks.

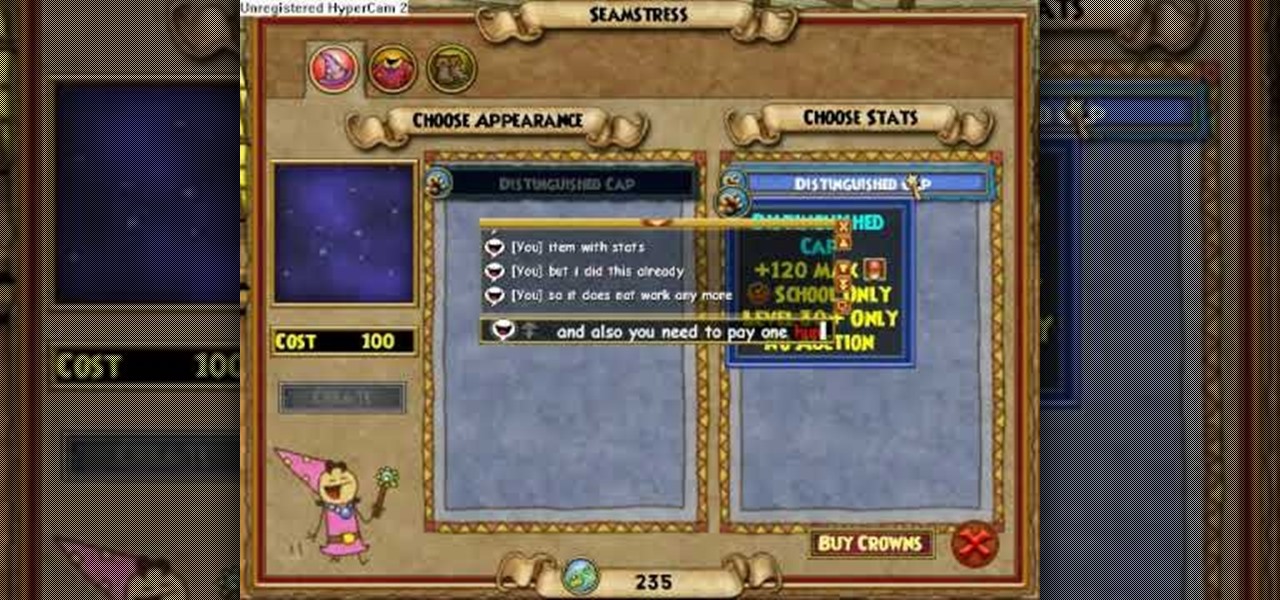
Hemming and stitching in Wizard101? Yep, learn how to stitch itms together and make an awesome wizard-like costume.

In this how-to video, you will learn how to use a song to read palms. Memorize these lines to music to help you. First, if you have a rich line, you are the rich and you get much money. If you have a sun line, you are popular. Everyone likes you because you are the sunshine. Check your palm. Check your life line. If it is thick, you have a powerful body. If it is thin, you are weak. Check the head line. If you have a short line, you quickly decide and act. If it is long, you need to think fir...