
News: Apple to Start Augmented Reality Smartglasses Production Later This Year, Report Says
The Apple rumor mill is getting its first real workout of 2019, and this time the whispers are more exciting than usual.


The Apple rumor mill is getting its first real workout of 2019, and this time the whispers are more exciting than usual.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Admit it: you've been caught muttering to yourself under your breath in very public places. Maybe you've gotten stares while wandering the grocery store talking to yourself out loud. If you're like me, you might even talk yourself through various tasks, giving the atmosphere a little background noise.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Loaded with a gorgeous display and a powerful processor, the Kindle Fire HDX is an impressive all-around tablet, especially when it's used for what Amazon Kindles were built for—reading electronic versions of novels, textbooks, and other printed works.

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Step1. Determine the type of job you want. Make sure that you have a detailed and complete profile on ‘linkedin’. You must also have a number of connections. Then decide which job you are looking for and the typical functions and titles. Also choose which type of industry you would like to work in and also choose what locations. You also need to write down specific names of organizations that you want to work for and who are they.

Watch this video tutorial to learn how to book the best hotel room for your money. You've spent all year saving up for your dream vacation. The last thing you want is to end up in a hotel room that ruins the whole trip.
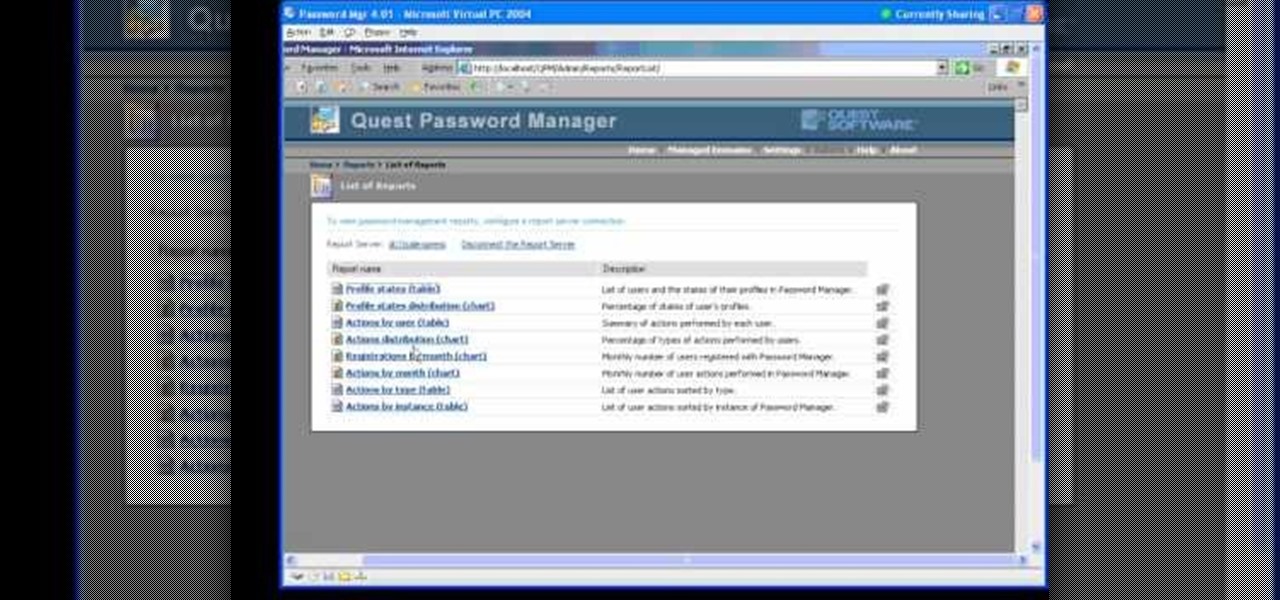
In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

Video: . The author started with a written introduction of the importance of the executive summary as part of the business plan.
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...

No matter what age you are or what kind of life you've lived you can put your story out there by writing an autobiography. Every life can be interesting if written about in a well formulated, and honest manner.

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

The impact of the COVID-19 pandemic caused by the novel coronavirus has practically guaranteed that the virus, along with the phrases "social distancing" and "flattening the curve," will rank among the top search terms of 2020. USA Today combined the phrases in its latest augmented reality experience, which quizzes your knowledge in the best practices of social distancing.

Like other popular social media apps, TikTok features a tagging system — dubbed TikCode — to follow people in your immediate vicinity. Instead of searching for their username, you can scan their TikCode, and TikTok will launch their page immediately. Of course, you have a TikCode of your own, so you can share yours with others in the same way.

A little over a year after emerging from stealth, augmented reality gaming startup Illumix has launched its first title using a familiar formula, but with a new twist.
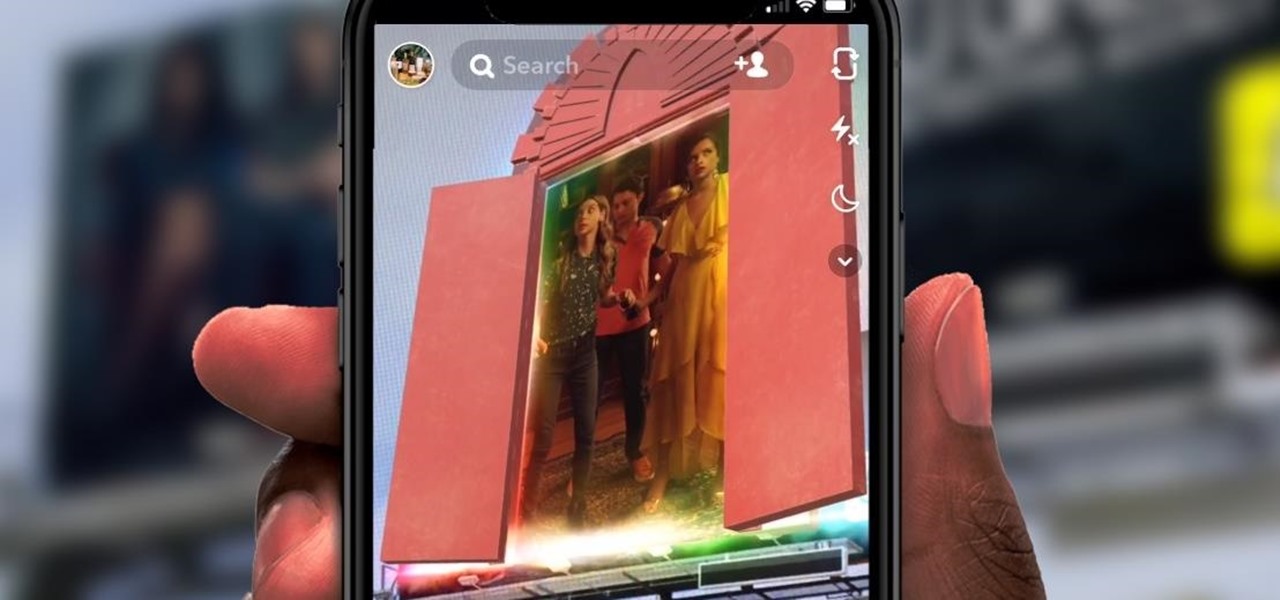
It looks like Snap's foray into augmented reality billboards last year was successful, as the company has returned with two more outdoor advertisements for its Snap Originals series.

Haptic feedback is one of the iPhone's most underrated features. With Face ID, you'll feel a satisfying tap or two when buying something in the App Store or iTunes, unlocking protected notes, viewing saved passwords in Settings, and the list goes on. For the first time, Apple has added haptic feedback when unlocking your iPhone via Face ID, as well as a way to disable haptic feedback for Face ID entirely.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

On Tuesday, Blue Vision Labs, one of three Google-backed companies working on AR Cloud platforms, announced its acquisition by ride-sharing company Lyft.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.
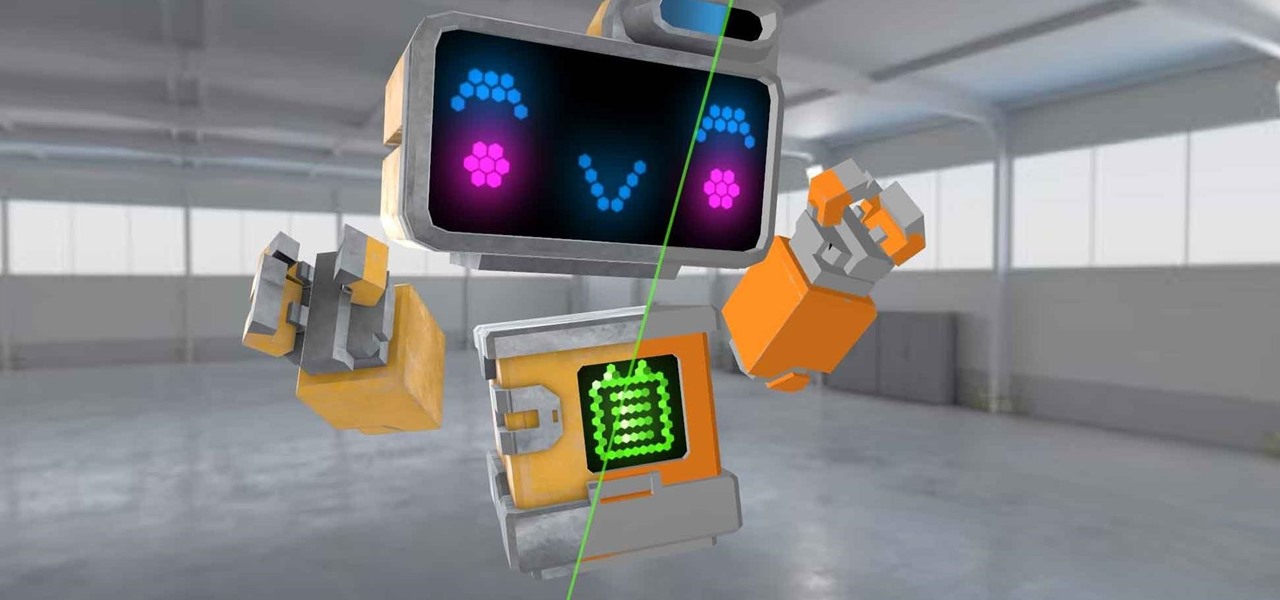
Following San Francisco-based Occipital's successful Structure Sensor Kickstarter campaign, the release of its Bridge AR/VR headset, as well as a string of technology and company acquisitions, the company has built a rather strong name for itself in the AR community. And now, with the first public release of its Bridge Engine on Thursday, the company continues to expand the features its platform has to offer, with hopes of bringing in more developers to utilize it.

One of the most popular mobile games out there for kids has added an augmented reality mode that brings the titular character into the real world.

Snapchat just fast-tracked the majority of its app user base into the world of augmented reality production by making its Lens and Filter tools available to anyone with a web browser.
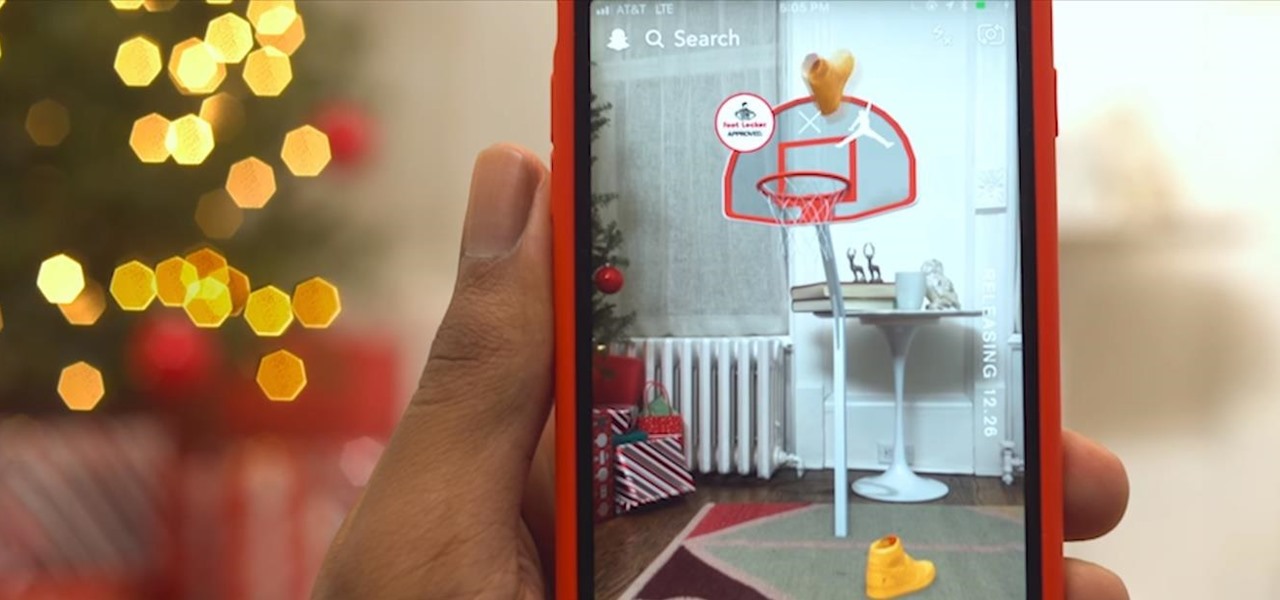
After closing its 2017 financial books on a high note, Snap, Inc. is planning to ride the momentum of its augmented reality products into the new year. That's the main takeaway following the company's 2017 earnings conference call, which was held on Tuesday.

After Vuzix's scorching hot week at CES, the future of AR is so bright, we have to wear (smart) shades. Luckily, Vuzix is making it easier for consumers to grab a pair.
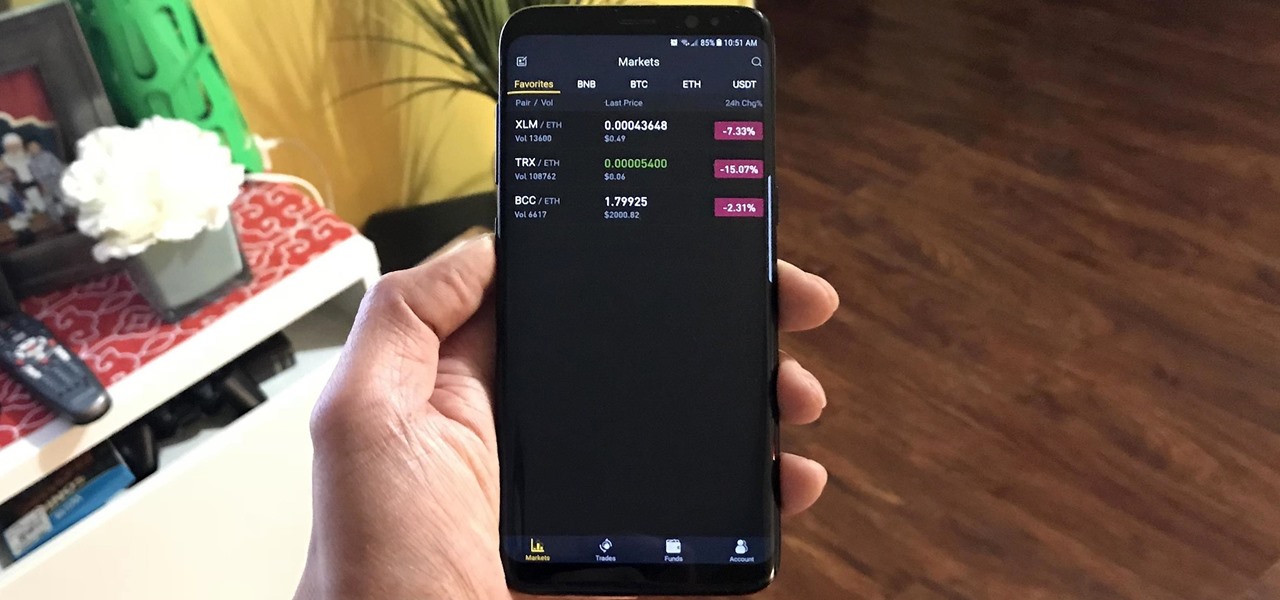
With the sheer number of alt-coins that you can buy and sell on Binance — Ripple (XRP), Stellar (XLM), and NEO to name a few — keeping track of coins you're interested in is a hassle. But with the tap of a button, you can mark trades and alt-coins that are on your radar for quick access on your Binance account.

Continuing its unrelenting (and mostly successful) campaign against Snapchat, on Tuesday, Facebook announced the addition of "World Effects" to its Messenger app.
For every cool new thing Android Oreo brought to the table, Android 8.1 adds a bit of polish. After a brief but successful beta period, Google started rolling out the official 8.1 update to its Pixel and Nexus devices today, and it's everything Android 8.0 should have been.

Rabbit ears and dog noses are fun and all, but Kay Jewelers is here to class up Snapchat.

While most of Hollywood and its celebrity class are enthralled by virtual reality, a new augmented reality experience featuring some of the music and film world's top talent is preparing for virtual liftoff.

Ever since the planet went crazy trying to find augmented reality creatures in Pokémon GO, we've been waiting for the next virtual object game capable of delivering a similar hit. And now, we might finally have one coming, direct from the magical world of Harry Potter.

Augmented reality headset maker DAQRI today named chief product officer Roy Ashok as the company's new chief executive officer to accelerate the company's growth.
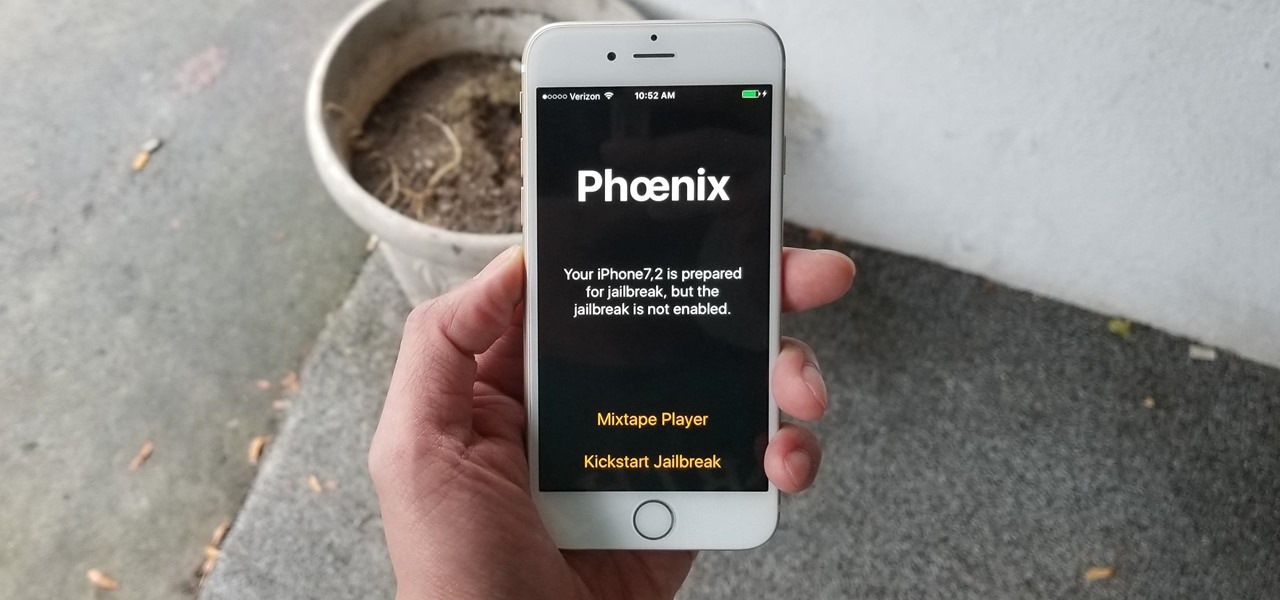
Unlike fully untethered jailbreaks such as Yalu's iOS 10.2 method, semi-tethered jailbreaks require users to re-enable the mod each time their device is turned off. Fortunately, the process of kickstarting a jailbreak is easy to do, since it's already embedded in your iPhone's OS and doesn't require reinstallation.

A top executive from Baidu's telematics division believes the company will become the word leader in driverless by 2020, according to a report in today's South China Morning Post.

Rising on the world stage, dengue fever is transmitted by mosquitoes — and apparently air travel too.