Just about a year ago, Google launched an update to the Gmail app for Android that let you link accounts from other email services to Gmail, allowing you to read and respond to everything in one place.

If you're anything like me, clutter scattered across the bathroom counter, on the shower floor, or on any other available space is maddening. Who enjoys a mess of shampoos, scrubs, and sponges strewn around their feet or just out of reach in the shower? What can you do when space is limited?
To contemporize a popular quote, "A cluttered desk(top) is a sign of a cluttered mind." Of course, it's difficult to maintain a tidy desktop... as you read this, mine is cluttered with screenshots, folders, Word documents, videos, pictures, and apps.

We tend to assume that eating is mostly a physical act, but the mind has so much to do with the choices we make.
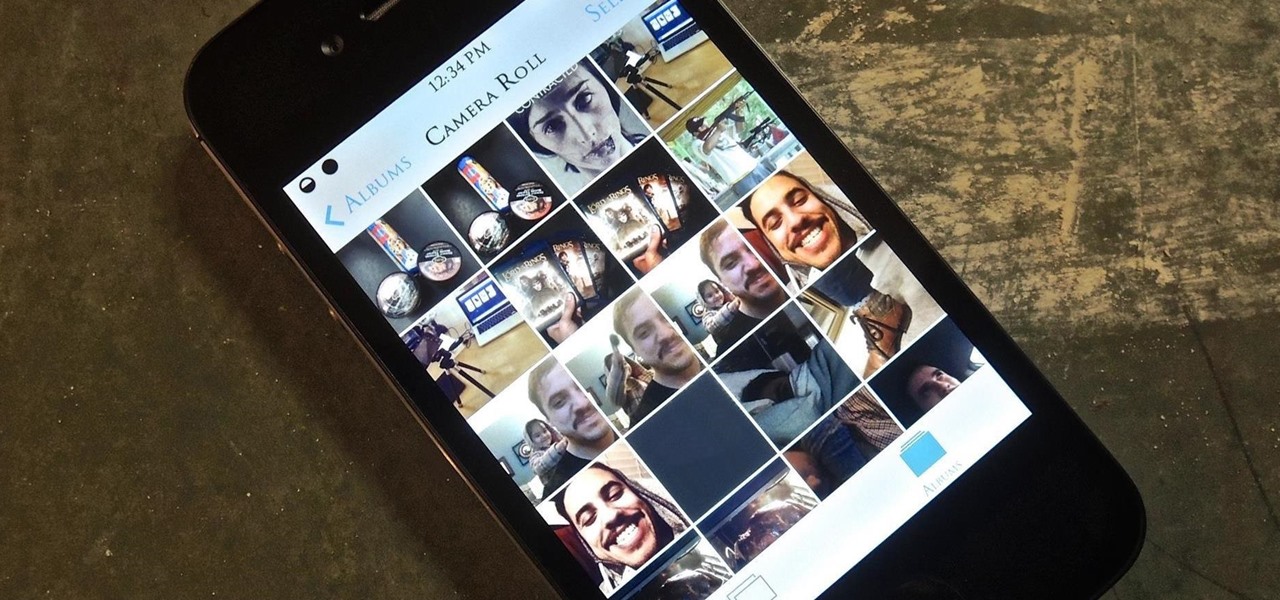
I have over 400 photos on my iPhone, and I don't even know where half of them came from. Scrolling through all of those pictures is a pain in the ass, but it's not nearly as bad as trying to actually find an old image. Organization is not my strong suit, so I'm definitely not the type to create new albums to sort through my 400+ photos.

Today I'm going to show you 7 easy ways to organize your room. They are really simple and cheap so I hope you find them useful!

Apps sure do run great on Android tablets! If you caught that little whiff of sarcasm, you probably already figured out I was lying. There is a definite lack of good, high-quality apps specifically made for Android tablets. If you've ever tried Facebook or Twitter on a tablet, you know exactly what I mean.

When we surf the web, we tend to do it for selfish reasons. Whether it's on Facebook, Twitter, YouTube, Pinterest, or Wikipedia—we're trying to connect with people, voice our opinions, watch funny videos, or do research for that 12-page paper due tomorrow. Whatever it is, it's usually to benefit ourselves. Well, what if you could not only benefit yourself while surfing the web, but benefit others in need, without even having to alter your habits?
Part of the process to answer the topic question is to discover the answer to three other questions, which are: (1) Who am I? (2) Who do I want to help? (3) How do I want to help?

Disney's animated film Toy Story 3 beat all expectations at the box office, and is now the highest-grossing movie of 2010 in North America and second worldwide. Can Disney Interactive Studio's Toy Story 3: The Video Game match the success? Who knows, but no matter how successful it is, it's still a fun game full of animated delight, and this Mahalo video walkthrough series will show you the entire gameplay for the game on the Xbox 360.

Is your fridge getting out of control? Can't identify that raunchy smell that has invaded your ice box? Can't find your ketchup? The best way to alleviate these problems is by organization. Organizing and keeping your fridge tidy is the best way to go, but it could be hard in a roommate situation where one said roommate will never give a damn. Nonetheless… chill out! Use these helpful tips to get your refrigerator organized.

How much time have you wasted, wandering around your home trying to find one particular book? Without a good system of organization, finding the book you're looking for can become a hopeless task. Organize your book collection at home by following this tutorial.

Accidents will happen. This brief how-to will guide you through the process of disassembling your HP iPAQ hx2100, hx2190, hx2400 or hx2700 series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to those who wish to learn more about the guts of their iPAQ PDAs without actually disassembling their units.

Accidents will happen. This brief how-to will guide you through the process of disassembling your HP iPAQ rw6815, rw6818, rw6828 series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to those who wish to learn more about the guts of their iPAQs without actually disassembling their units.

Accidents will happen. This brief how-to will guide you through the process of disassembling your HP iPAQ hx2000, hx2100, hx2110,hx2115, hx2141s, hx2190 (hx2190a, hx2190b), hx2400, hx2410, hx2490 (hx2490b, hx2490c), hx2495b, hx2700, hx2750, hx2755, hx2790 (hx2790b, hx2790c) or hx2795b series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to those who wish to learn more about the gut...

Accidents will happen. This brief how-to will guide you through the process of disassembling your Hewlett Packard iPAQ h3870, h3875, h3835, h3860 or h3830 series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to those who wish to learn more about the guts of their iPAQs without actually disassembling their units.

Accidents will happen. This brief how-to will guide you through the process of disassembling your HP iPAQ h2210 or h2215 series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to those who wish to learn more about the guts of their iPAQs without actually disassembling their units.

In this video series for puppeteers, learn how to start your own puppet company home business, with tips on where to get puppets, what equipment you need and how to train puppeteers to put on a successful puppet show. Also learn how to market your company to schools and corporations, and how incorporate yourself.

The volleyball attack can excite the crowd and devastate the opposing team. The approach, jump and landing are the basic aspects of a successful volleyball attack. Learn how to attack in this volleyball video tutorial.

A field hockey team will not win if the offense does not score points, so they must work together with the rest of the team to be successful. Learn how to play offense in field hockey in this video tutorial.

With the LG KU990 Viewty, you can take and view a crystal clear photo. Packed with high-quality camera features, this camera phone enables you to capture a high-definition image using a 5 MP camera lens certified by Schneider-Kreuznach and edit your photo on a large, clear, 3-inch display just like a professional photographer.

With the Dark Knight being one of the most successful movies of all time, the Joker is sure to be a sought after Halloween costume. While the make-up might seem tricky to apply, this video shows how to recreate it. Watch this video special effects tutorial series and learn how to do the makeup for the Joker from Batman's Dark Knight movie.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

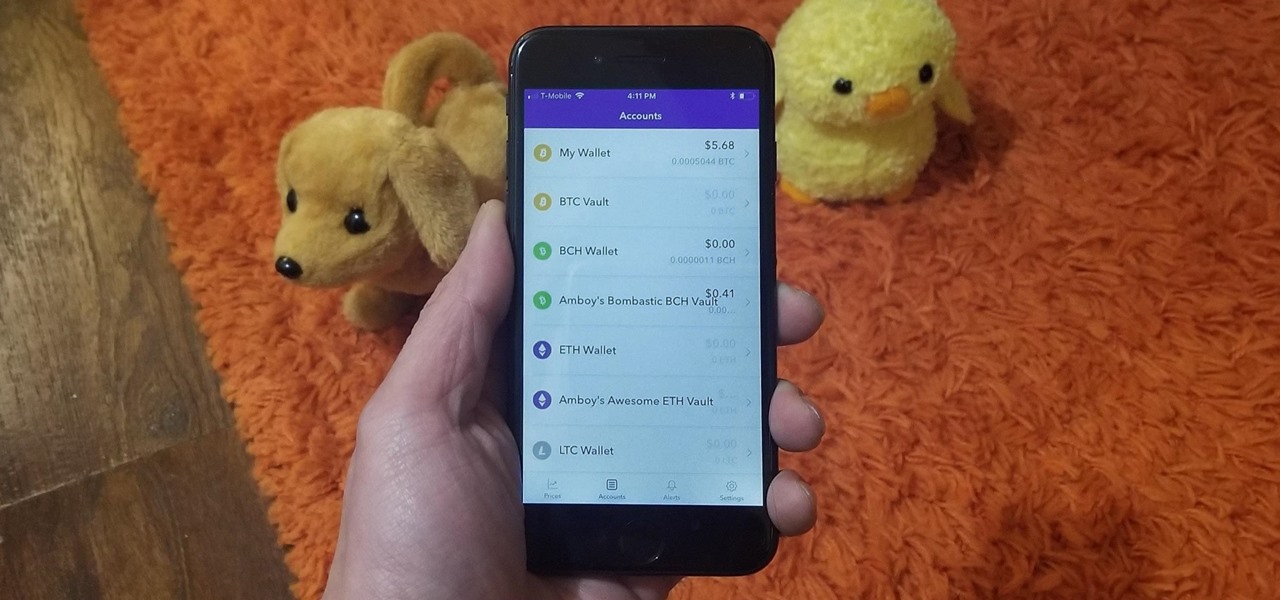
As cheesy as it sounds, #HODL became a thing for a reason. A lack of discipline when dealing with cryptocurrencies can lead to impulse buys and panic selling, and ultimately, depleted funds. Luckily, Coinbase has a way to safeguard your cryptocurrency savings to not only protect them against thieves, but to also help you resist the urge to sell off your investments.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

A 6,000-year-old forest inhabitant awakens to find life in the forest around it in crisis. Plants, trees, animals, and birds are moving north to escape increasingly heated air, even as mass extinctions take place around the world. The inhabitant stirs and remembers it has lived this before and knows what to do.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

If you've ever played the game of Would You Rather, you've probably been given the ultimatum between eating insects or doing something else that sounds absurd, like licking a cactus. I'm advising you to always choose the insects, and here's why:

Welcome to my tutorial where Voidx and I will be expanding on my previous article to provide more clarity into the logic of the code.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.