Know thy enemy — wise words that can be applied to many different situations, including database hacking. It is essential to performing adequate reconnaissance on a system before even thinking about launching an attack — any type of attack — and this is no different for SQL injection.

On Wednesday, Scope AR, makers of Remote AR, the augmented reality video conference calling and remote assistance solution, announced that the app is finally available for HoloLens. Next Reality had a chance to talk with the founder and CEO/CTO of Scope AR, Scott Montgomerie, inside this new version of Remote AR.
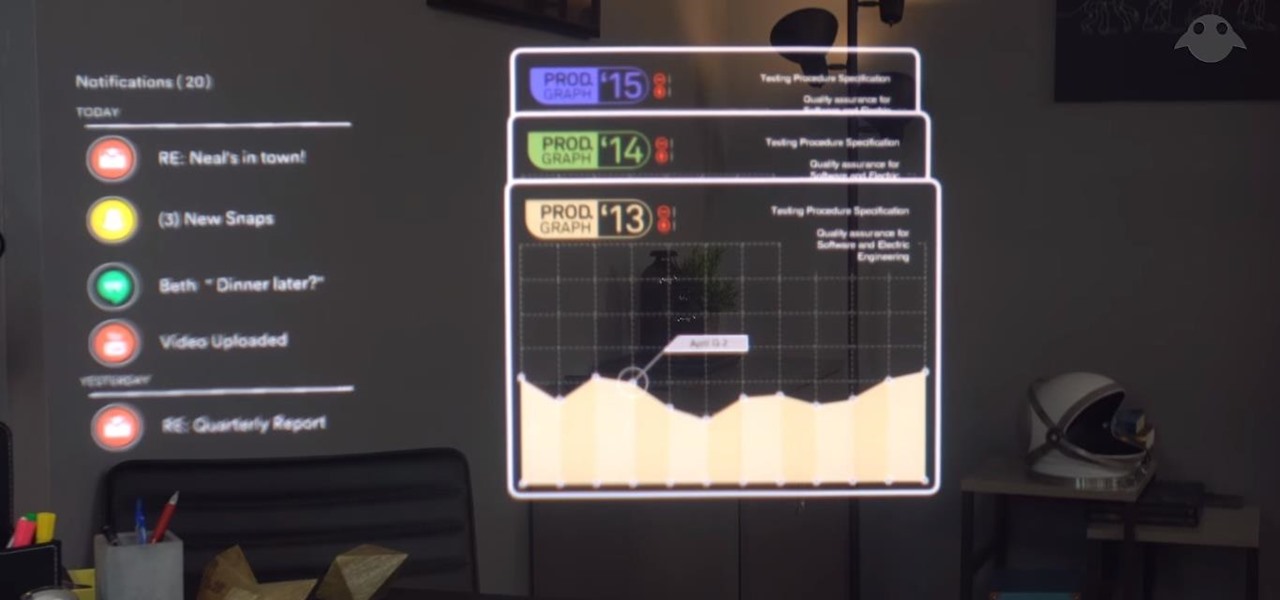
For a company who hasn't released a product and has a reputation for being secretive, Magic Leap sure has a tendency to make waves. Over the past few weeks, they've refreshed their website design, released an abstract YouTube video, and announced a partnership with Madefire to offer mixed reality comics on its device whenever it launches. Next, they are gearing up for another round of funding.
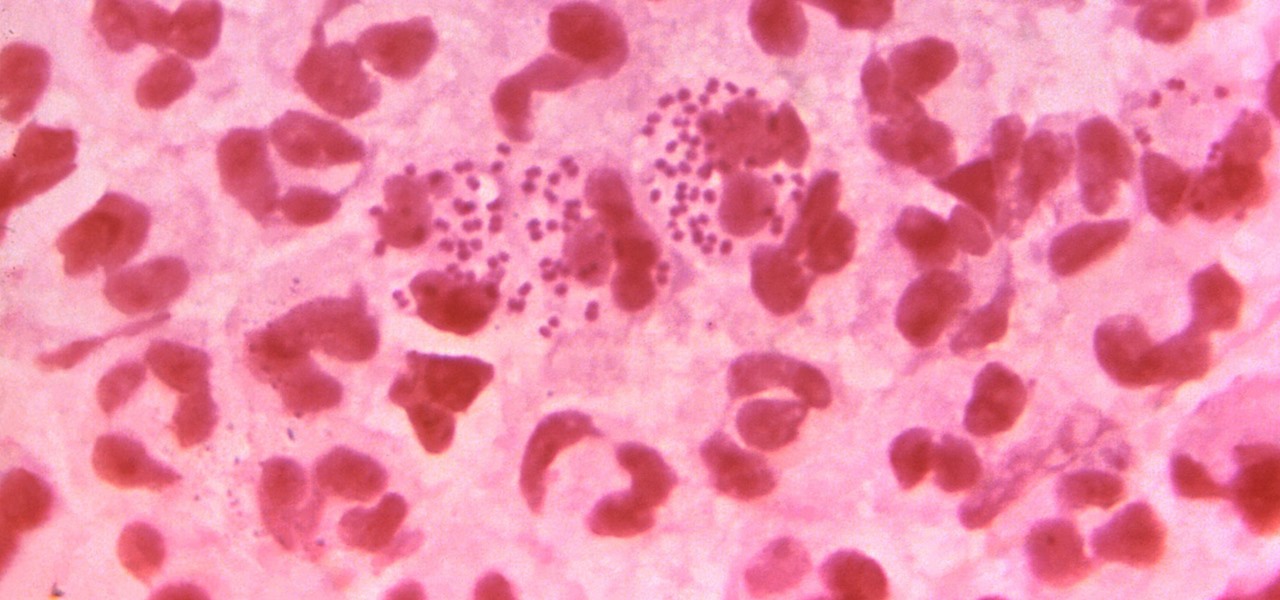
In the race to outsmart "untreatable" antibiotic-resistant gonorrhea, one of the three new treatments on the track is about to enter Phase 3 clinical trials. Hopefully, it'll be widely accessible sooner rather than later, for the 78 million people who are diagnosed with gonorrhea each year.

Natural remedies used through the ages abound, especially in Asian medicine. The willow-leaved justicia plant, found throughout Southeast Asia, has traditionally been used to treat arthritis, but scientists have just discovered it contains an anti-HIVcompound more potent than AZT. AZT was the first drug approved to treat HIV, and is still used in HIV combination therapy today.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Keeping your computer organized and your desktop clutter-free can be pretty difficult. And with last week's official release of Windows 8, users have another screen they need to get used to organizing—the new Metro-style Start Screen. It uses large rectangular or square tiles in place of the standard icons you've seen on older Windows operating systems. For better organization and grouping, you can group similar items onto a page (similar to many smartphones), you increase or decrease the siz...

The single-player campaign mode in Call of Duty: Black Ops may be intense, but the multiplayer mode is a bloodbath of pure addiction. Black Ops takes the super successful formula of Modern Warfare and adds its own special twist. There's some changes, and Jessica Chobot from IGN Strategize is going to tell you all about them!

Drawing human subjects can be tough if you're not an experienced artist. getting every detail just right it quite a task, because of the intricateness of the human body. But Merrill is going to show you how it's done.

The PSP has never had the software support that it needed to be a really commercially successful system. Since Sony blew it already, you may as well go the extra mile to make this expensive little thing you bought more useful right? This video will teach you how to hack a PSP 3000 or 2000 with firmware version 5.03. This is a complete hack, meaning that you will be able to play .iso games and everything when you are done. Get to it! This should let you unbrick your psp 3000.

The new Splinter Cell video game has a co-op mode now, which means you don't need to play online anymore just to play against a human. You can have your best friend sitting right next to you… playing on the same Xbox 360. Forget the absurdity of playing in separate rooms, play in the same room. Splinter Cell: Conviction for the Xbox 360 is the way to go.

This how-to video is about how to use the Ribbon and Backstage view in Microsoft Office Excel 2010.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

If you've ever had a little trouble trying to program your calculator, you may find a little relief with this four-part video tutorial. Here, a Texas Instruments (TI-84 Plus) calculator will be used to explain the programming process. The four parts include:

In recent years, Google's Arts & Culture project has been leading the way in terms of innovating the practice of using technology to preserve landmarks and great works of art via digital 3D copies. Increasingly, these efforts are also giving history buffs the chance to experience classic works and spaces with unparalleled intimacy through the wonders of augmented reality.

The once blurry and mysterious vision of Magic Leap's future is slowly coming into focus in the present, despite the company's obsessive attempts to keep any and all information under wraps until the next reveal is absolutely necessary. A new tidbit of information hints at an addition to the company's unfolding story that almost no one had accounted for: retail stores.

While the mainstream consumer market waits for cool augmented glasses to arrive from Magic Leap, or maybe even Snap Inc. (Spectacles 2.0??), AR headset maker DAQRI and its business customers are finding new, money-saving and time-saving use cases for the technology today.

A recently confirmed polio outbreak in Syria is connected to low levels of vaccination, worsened by conflict. It is the first confirmed incidence of polio in Syria since 2014. Before 2013, the last case of polio in Syria was in 1999.

This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are legitimate companies who sell their services to governments—Vupen, being one of the most famous and lucrative).

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

For the most part, nobody makes money off of Facebook. Sure, some people make a living by updating pages for businesses and celebrities, but hardly anyone gets a dime from the site itself.

Firstly, I'd like to say that I have nothing against iPhoto; it's a great application that works wonderfully in Mac OS X. Unfortunately, when you no longer have iPhoto on your MacBook—and you don't want to pay for it—looking for an alternative is a necessary endeavor. I could sit here and try to explain to you how I updated to Lion and then inexplicably dragged the iPhoto application into the trash—and proceeded to empty said trash. I could tell you guys that story, but I fear you might judge...

In this outdoors how-to video from fitclimb.com we're shown how to make a fire in the snow. The first step is to find a good flat spot, or make a flat spot yourself. Next, we look for trees with dead branches and break those dead branches off for the wood. The key here is to be organized because you'll have to carry this wood back to your camp. Next, you want to make a platform for your fire to keep it from sinking down as the snow melts. Here, we're using the bark from a dead stump for a pla...

Find Osman in the Cathedral Square to deliver Alexander's message to him in Mission 5 on the Sony PSP. Make your way to the Cathedral area, at which point the red delivery icon pops up and denotes Osman's rendezvous point. The only problem is that the area is swarming with guards and that Altair must make successful contact without being detected. Climb up the first buildings in front of you and hop across toward the icon. Silently dispatch the archer on the roof and then head around to the o...

Learn how to teach your dog to high-five. Make your pooch the hippest dog on the block by teaching him how to greet you with a high-five.

Rolling over is a simple trick that any dog can master, and it will help you build confidence in your dog. Learn how to teach your dog to roll over with this how to video.

Okay, just because the new Verizon Wireless Droid X comes with an HDMI-out port doesn't mean you're limited to just that. Motorola has made it possible for you to play video, music, and pictures to your television without any wires at all. With the Droid X's DLNA media sharing application, you can easily stream to an PS3 or Xbox, send pics to your PC, and stream videos to your TV. Check out this video walkthrough to learn how to use the DLNA services to connect your Droid X to the PlayStation 3!

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

Generally speaking, in terms of modern devices, the more simple you make an interface to navigate, the more successful the product is.

Amazon's first venture into the wireless phone market was a crash and burn moment — and that's us being kind. Their FirePhone went down in flames almost instantly, no pun intended.

There's a new operating system on the horizon, and this one's so big that it may actually live up to its galactic moniker. Andromeda, a merging of Android and Chrome OS, has the potential to bring Google to the ubiquitous status that Microsoft's Windows enjoyed in the '80s and '90s.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

You've got to be sick of it by now. Those meaningless and unsatisfying articles, lists, and videos you were duped into clicking on because their headline made them impossible to resist.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

Text adventure games, such as the well-known Zork series, were some of the first computer games ever made, second only to the likes of Spacewar! and the better-known Pong. So let's travel back in time for a moment, to a time that never was.

You've manage to get your hands on some ruthenium, and now you want to destroy the hard silvery-white metal of the transition series. Well, you're going to try all kinds of ways to dissolve this odd metal, but the only successful way to dissolve ruthenium is with a common household cleaner… bleach.

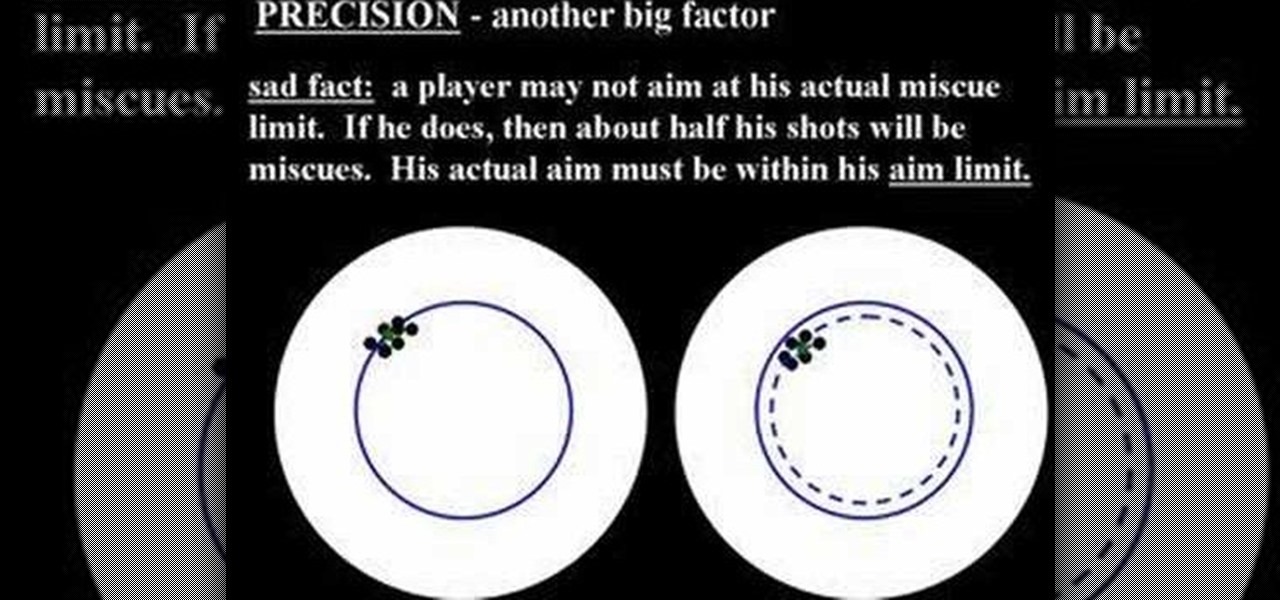
Cue ball draw refers to the way a cue ball strikes a rack of balls. In particular, if the cue ball is hit low on the ball, when it strikes a rack of balls, for the break, it will have enough backspin to wind its way back to the shooter.