Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

You may not notice it when you're intoxicated and banging your head to the music, but when you're at a club or concert, your ears are getting seriously damaged. The noise level is usually above most people's pain threshold for sound, which begins around 120 to 140 decibels. At that level, it only takes a few minutes to damage your hearing. For me, there's something even worse than long-term hearing loss in a loud environment—not being able to hear or talk to your friends.

Search Engine Optimization is important for every successful SEO or blogging campaign. Therefore it is required to be implemented in the correct manner. Google consider many factors while ranking a webpage and it keeps on changing. Some of the common SEO mistakes which you must avoid are as follows:

While the majority of America was watching the Super Bowl yesterday, the crew over at the evad3rs was finishing its work on their untethered iOS 6.1 jailbreak called evasi0n. Well, the wait is finally over!
The first alarm clock in recorded history can be traced back to ancient Greek philosopher Plato, known for laying the foundations of Western philosophy and science. Plato was said to possess a very large water clock with an alarm signal similar to that of a water organ.

Disney's animated film Toy Story 3 beat all expectations at the box office, and is now the highest-grossing movie of 2010 in North America and second worldwide. Can Disney Interactive Studio's Toy Story 3: The Video Game match the success? Who knows, but no matter how successful it is, it's still a fun game full of animated delight, and this Mahalo video walkthrough series will show you the entire gameplay for the game on the Xbox 360.

PGA golf professional Frank Ganley explains how to hit a golf ball with an iron. In golf, a player has a variety of clubs to choose from, but should only have one type of swing. Frank emphasizes that in order to learn how to hit a golf ball with an iron, the player needs to use the same swing that he uses when hitting the ball with a wooden club. The key to a successful hit is in the players ability to adjust for the difference in the lengths of shafts of the clubs. This because a wooden golf...

This video shows how to do a 'kick flip' on a skateboard. The man instructing begins by getting the things he will need, which are a skateboard and a pair of shoes. He demonstrates where to place your feet, with the left foot on the middle of the board and the right foot on the end. The next step is to kick the board up with your right foot and flick your left foot up and off, then quickly jump back on after the board flips. He shows a real life example of a successful 'kick flip', and then g...

This video gives instructions on how to cite sources when giving a speech. When giving a speech, you want to appear persuasive and credible to the audience. In order to do this, you must cite the sources of your speech's content. Prior to giving your speech, research materials relevant to your topic. In the course of giving the speech, mention where you got your data. In this case, the speech is about Emotional Intelligence in the Workplace. While making your first main point, mention that "a...

Accidents will happen. This brief how-to will guide you through the process of disassembling your HP iPAQ hx2100, hx2190, hx2400 or hx2700 series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to those who wish to learn more about the guts of their iPAQ PDAs without actually disassembling their units.

Accidents will happen. This brief how-to will guide you through the process of disassembling your HP iPAQ rw6815, rw6818, rw6828 series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to those who wish to learn more about the guts of their iPAQs without actually disassembling their units.

Accidents will happen. This brief how-to will guide you through the process of disassembling your HP iPAQ hx2000, hx2100, hx2110,hx2115, hx2141s, hx2190 (hx2190a, hx2190b), hx2400, hx2410, hx2490 (hx2490b, hx2490c), hx2495b, hx2700, hx2750, hx2755, hx2790 (hx2790b, hx2790c) or hx2795b series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to those who wish to learn more about the gut...

Accidents will happen. This brief how-to will guide you through the process of disassembling your Hewlett Packard iPAQ h3870, h3875, h3835, h3860 or h3830 series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to those who wish to learn more about the guts of their iPAQs without actually disassembling their units.

Accidents will happen. This brief how-to will guide you through the process of disassembling your HP iPAQ h2210 or h2215 series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to those who wish to learn more about the guts of their iPAQs without actually disassembling their units.

In this video series for puppeteers, learn how to start your own puppet company home business, with tips on where to get puppets, what equipment you need and how to train puppeteers to put on a successful puppet show. Also learn how to market your company to schools and corporations, and how incorporate yourself.

The volleyball attack can excite the crowd and devastate the opposing team. The approach, jump and landing are the basic aspects of a successful volleyball attack. Learn how to attack in this volleyball video tutorial.

A field hockey team will not win if the offense does not score points, so they must work together with the rest of the team to be successful. Learn how to play offense in field hockey in this video tutorial.

With the LG KU990 Viewty, you can take and view a crystal clear photo. Packed with high-quality camera features, this camera phone enables you to capture a high-definition image using a 5 MP camera lens certified by Schneider-Kreuznach and edit your photo on a large, clear, 3-inch display just like a professional photographer.

With the Dark Knight being one of the most successful movies of all time, the Joker is sure to be a sought after Halloween costume. While the make-up might seem tricky to apply, this video shows how to recreate it. Watch this video special effects tutorial series and learn how to do the makeup for the Joker from Batman's Dark Knight movie.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

While Magic Leap World gets its share of fun apps for playing with Porgs, watching TV, and exploring the ocean's depths, developers are making a strong business case for the Magic Leap One as well.

A new profile on Apple's exiting design chief Jony Ive, the man behind many of the company's most successful products, paints a fuller picture of what led to his departure.

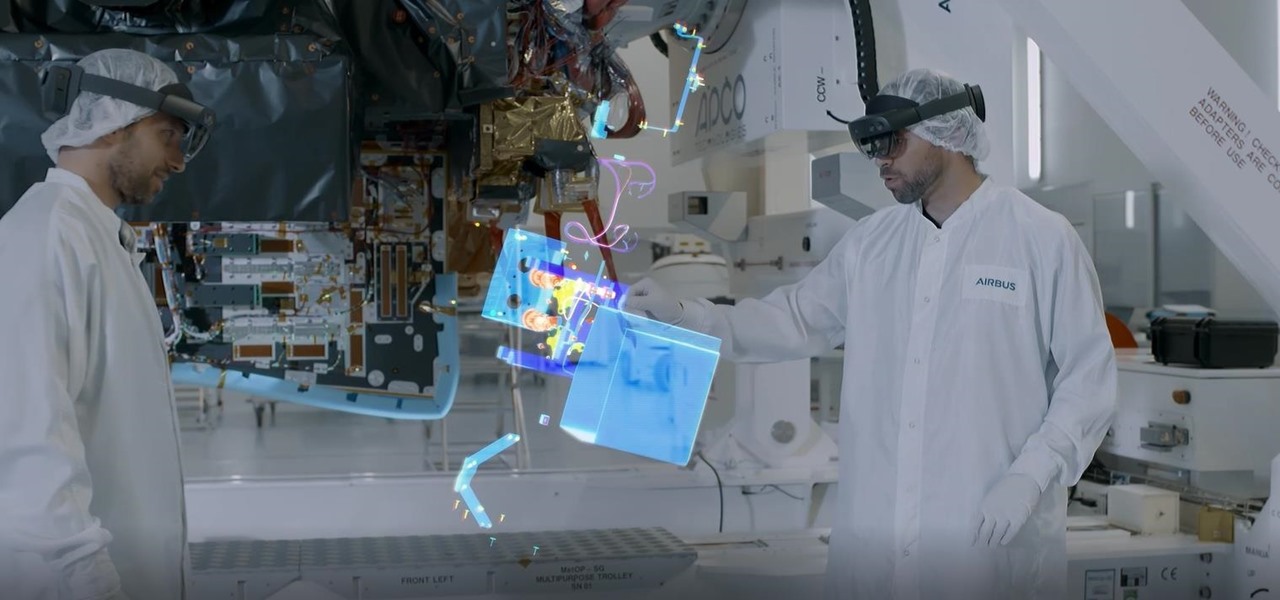
Aircraft manufacturer Airbus is so impressed with the boost in productivity it has gained from Microsoft's HoloLens, the company will begin offering augmented reality software to its customers.

While augmented reality industry continues to grow, analog board games are also making a comeback. So, why not join the two together?

Next to Apple, Snap is currently one of the most important companies on the planet in terms of delivering products that are moving augmented reality into the mainstream. That's why it's no surprise that Facebook, which is also focused on AR and tried to acquire the company for $3 billion several years ago, duplicates many of the smaller company's features.

Ten days after Magic Leap declared that it had selected the winners of its Independent Creators Program, the company has officially released an almost full list of grant recipients.

The era of smartglasses designed for consumers has officially begun, as shipments of North Focals began arriving at its stores this week. And the company now has plans to expand its retail footprint.

Spotify integration in Bumble has been around for a few years now, allowing prospective matches to view the artists you listen to the most on the popular music streaming service. It definitely helps people connect, but sadly, it doesn't work as well as it should because it rarely updates to show what you're listening to now.

There is no shortage of defenses against cross-site scripting (XSS) since it is so prevalent on the web today. Filters are one of the most common implementations used to prevent this type of attack, usually configured as a blacklist of known bad expressions or based on regex evaluation. But there is hope with a wide variety of techniques that can be used to defeat these filters.

It turns out that attending the L.E.A.P. conference last month may have mostly been best for demoing the Magic Leap One in person, as the company has now uploaded the majority of the insider panels held at the event in Los Angeles.

Less than three weeks after Rovio Entertainment announced the game, the augmented reality adaptation of Angry Birds is now available for the Magic Leap One.

In a leaked company memo, Snap CEO (and NR30 member) Evan Spiegel has made it clear that the future of the company lies not only augmented reality but also hardware that enables those AR experiences.

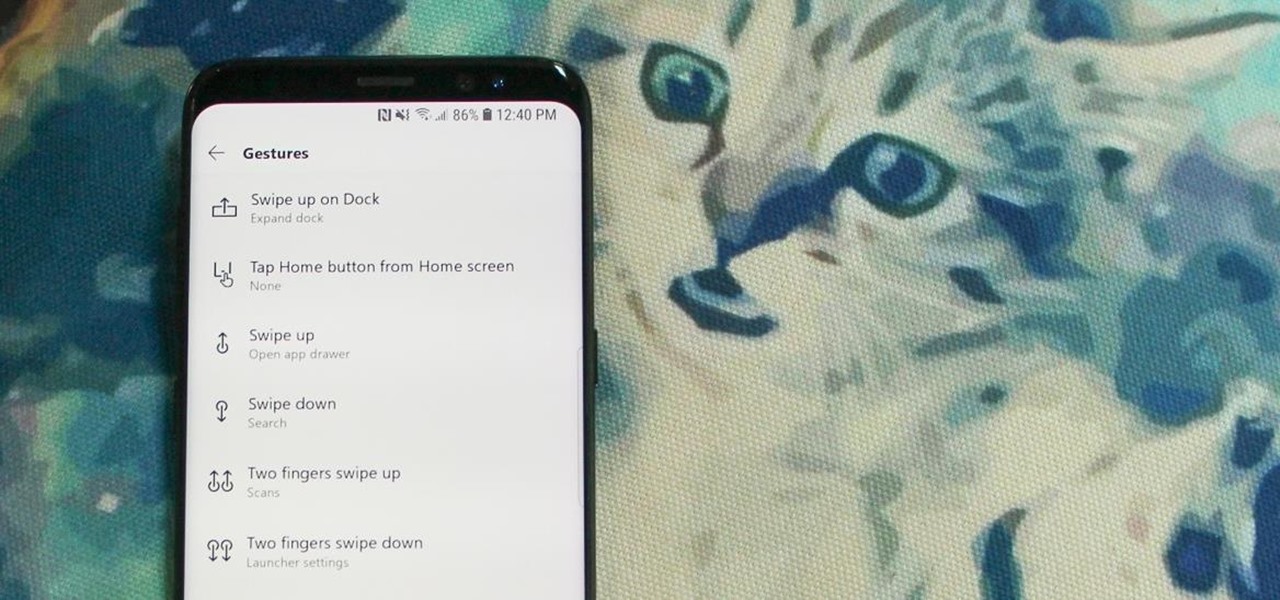
Ever-shrinking bezels and disappearing hardware buttons make for good looking phones, but they also increase the need for gesture controls. Android Pie comes with seven new swipe gestures, but if you don't have the update yet (or find its default gesture options to be lacking), you should take a look at the Microsoft Launcher.

Just in time for Women's Equality Day on Aug. 26, Treasury Wine Estates is breaking out a line of wines with augmented reality experiences that pay tribute to historically famous women.