
News: Islamic State (ISIS) Attacks U.S. Power Grid!
Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.


Those of you who have been a part of the Null Byte community for even a short while know that I sincerely and firmly believe that hacking is the most important skill set of the future.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

I love eating fish at restaurants—the flesh is flaky and tender; the scent, fresh and sweet. Cooking fish at home is a completely different story, though. Even when I do cook successful fish dishes, it often leaves this (for lack of a better description) fishy smell that permeates everything it touches. Monday's salmon becomes Wednesday's odor. It's enough to deter me from cooking fish, period.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

One of the coolest features in modern smartphones is their Bluetooth connectivity. This is how two digital devices can communicate with one another—sending data like your phone call audio or your favorite song—all while using up minimal battery life.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

There may be no kitchen appliance as controversial as the garlic press. Professional kitchens and many avid cooks despise it, while others staunchly defend it.
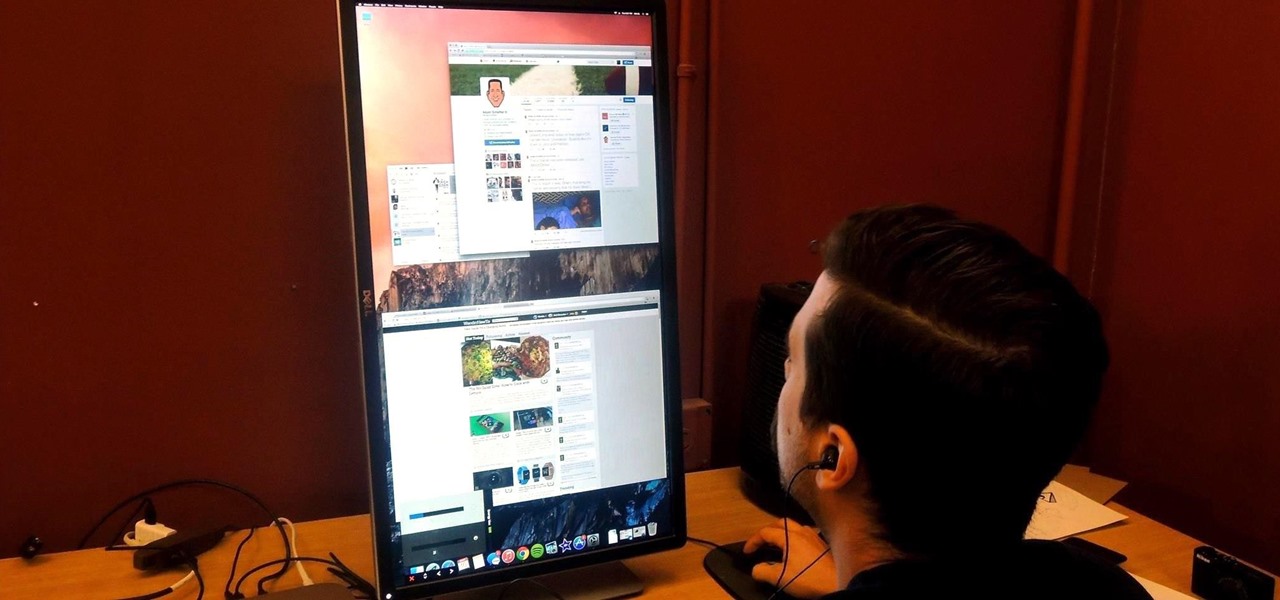
If you've got a desktop computer, I can almost guarantee that you've got a widescreen monitor set up in landscape mode. It's how just about everyone uses their monitor these days, including myself. Except that it's not always the best way of working.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Blizzard Entertainment, the wildly successful video game developer that brought us World of Warcraft and StarCraft, has finally released their popular trading card game Hearthstone: Heroes of Warcraft to the Android platform.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Alas, I have never tasted an authentic cronut (croissant-doughnut hybrid) from Dominique Ansel's NYC bakery, only its Los Angeles knock-offs. Ansel is also the guy who created a chocolate chip cookie shot glass and the flambéed ice cream s'more, so clearly he has some sort of dessert-perfecting gene the rest of us lack.

With so much Flash content still available on the web, it's unfortunate that Google no longer supports mobile Flash Player on Android. Loading a webpage only to be met with a "Plug-in Error" is never fun, and it can inhibit your mobile browsing experience as you attempt to watch a video or play an addicting Flash game.

Many game developers have finally realized that in order for their games to be successful, they have to support Android. To really win Android users over, they should also accommodate us hardcore gamers who have OTG cables with the ability to hook up controllers to our devices.

Unless you've been living under a rock for the past few weeks, you're probably well aware that the Android world has been buzzing with excitement over the recently debuted Android L preview build that was released for the Nexus 5 and Nexus 7 at Google's I/O conference.

We've already taught you how to clench your fist to make healthier food choices, and how to make sure you eat healthily at a restaurant, but it turns out there are even more mind hacks we can use in our never-ending quest to control our appetites.
Google's new camera app has a highly innovative and unique feature dubbed Lens Blur, and the most interesting thing about it is not necessarily what it does, so much as how it does it.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

I have a theory that chocolate chip cookies are the gateway drug to cooking. The recipe is easy, no special equipment is required, and at the end, you get warm, fresh-from-the-oven cookies that are simply irresistible. It's how I got hooked on baking and cooking, and anecdotal evidence (i.e. me asking my other kitchen-obsessed friends and a few culinary students) supports me.
With the release of Jelly Bean, Chrome became the default web browser on Android. The wildly successful desktop browser was now fully entrenched in the world's largest mobile operating system.

In order to unleash the full potential of your Samsung Galaxy Note 3, you've got to root it. These days, it's easier than ever, and can be done by just plugging your device into a Windows computer and pressing one button. It's so easy, your grandmother could do it, so what's stopping you?

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

Many people ultimately remarry when their first marriage eds in divorce or had mistakes written all over it. The choices you made do affect you future relationships and it is up to notice these and correct those problems so it does not happen in your next committed relationship. Learning Reasons Why Your First Marriage Culminated in Divorce

Whether you like it or not, certain songs get stuck in your head. You might be driving to work or school when suddenly Cher's 1998 lead single "Believe" plays on the radio.

Nikola Tesla is one of the most tragic figures in the history of science, a history that is practically filled to the brim with tragic figures. Francis Bacon, a 16th century philosopher and scientist, caught pneumonia and died because he was trying to stuff snow into a dead chicken. Marie Curie died as a result of her long-term exposure to radioactivity, and her papers from the 1890s are too radioactive to touch without protective gear to this day.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

Clearing the cache on your computer is (usually) a quick and easy way to help speed it up. Deleting those temporary files frees up space, helping you computer run smoother, especially if you have not cleared the cache for a extended period. However, finding the different caches in Windows 8 is a little trickier than in previous Windows systems.

Google's Nexus 7 tablet has just been released, and for only $199, it seems like a great deal. Now, some of you are probably immediately thinking that you're going to want to root this thing as soon as possible to install all of your tweaks. Luckily, some clever hackers have already developed a fairly automated solution to rooting the device. Here's how it works. A word of caution however, rooting your tablet will very much void the warranty and there's no 100% guarantee that this procedure w...

Making international calls have always been tricky and confusing. There's access codes, different digit formats, and unsupportive telephone operators. But in all actuality, making an worldwide phone call is relatively simple, but there are some numbers that you need to know. The access code, country code, city codes, and the telephone number. Once you have this down, you'll have more successful connections abroad.

Accidents will happen. This brief how-to will guide you through the process of disassembling your HP iPAQ hw6500, hw6510 (hw6510a, hw6510b, hw6510c, hw6510d, hw6510g), hw6515 (hw6515a, hw6515b, hw6515c, hw6515d, hw6515f), rw6815, rw6818, rw6828, hw6900, hw6910, hw6915, hw6920, hw6925, hw6940, hw6945, hw6950, hw6955 or hw6965 series pocket PC quickly and efficiently without damaging any of the components, the first necessary step of any successful repair. This tutorial will also be of use to t...

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Perform tasks when you’re at your best, hormonally speaking, by scheduling around your menstrual cycle.

Formal business proposals are important for starting up a business or soliciting new business. Learn how to write a successful formal business proposal with tips from a communications and public speaking expert in the free instructional video series.

Read palms for success in the hand. To focus mainly on business or workplace look to the mound of Jupiter, which should be prominent. Additionally, the first finger should be longer. A longer first finger is as long as the third finger. This shows someone who is ambitious, connected with work, and authority over others.

Eeverst isn’t for armatures. If you have the ambition of climbing Mt. Everest you will have to do a lot of preparations including physical fitness work, travel arrangements, not to mention putting aside thousands of dollars to make your dream a reality.