In this how to video series, learn basic Judo techniques from expert Judo martial artist Cesar Lazcano. Cesar will teach you how to stretch for Judo training and why Judo is a successful martial art. He will teach and demonstrate Judo techniques such as the arm bar, the guard position, how to pass the guard position, choking techniques, how to get an opponent in a leg lock, how to avoid a leg lock, and how to do a Judo ankle lock.

This video series explains how to write a good news article. Writing for a newspaper is not like writing an essay for school or a book. Watch this series and learn some good tips to writing successful articles.

Project managers — and those hoping to become one — should rejoice at this killer deal. The Project Manager's Essential Certification Bundle Ft. Scrum, Agile & PMP usually runs for $1,990 but is only $49.99 for a limited time.

One of the hardest parts of entering the IT and computer science field — other than the difficult material and intense competition — is the time and financial cost of learning everything you'll need. Learning to code isn't just learning one language; you have to learn a variety of languages used for different purposes, and then you have to get experience using them.

A successful startup needs more than a good idea. To get your startup off the ground, you need to know how to make a plan, fund it, and market it. Trying to learn how to do all of that on your own is impractical and unnecessary.

Becoming a successful web developer is more than knowing coding languages. Learning to craft functional, intuitive designs is as much coding as knowing how the user will interact with what you've built. The Complete Become a UI/UX Designer Bundle can take you from introduction to mastery in designing the best user experience, and right now, it's only $34.99.

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

If you're interested in becoming an in-demand project manager or leader in today's data-driven world, you need to know more than just a few generic management strategies to lead teams and companies successfully.

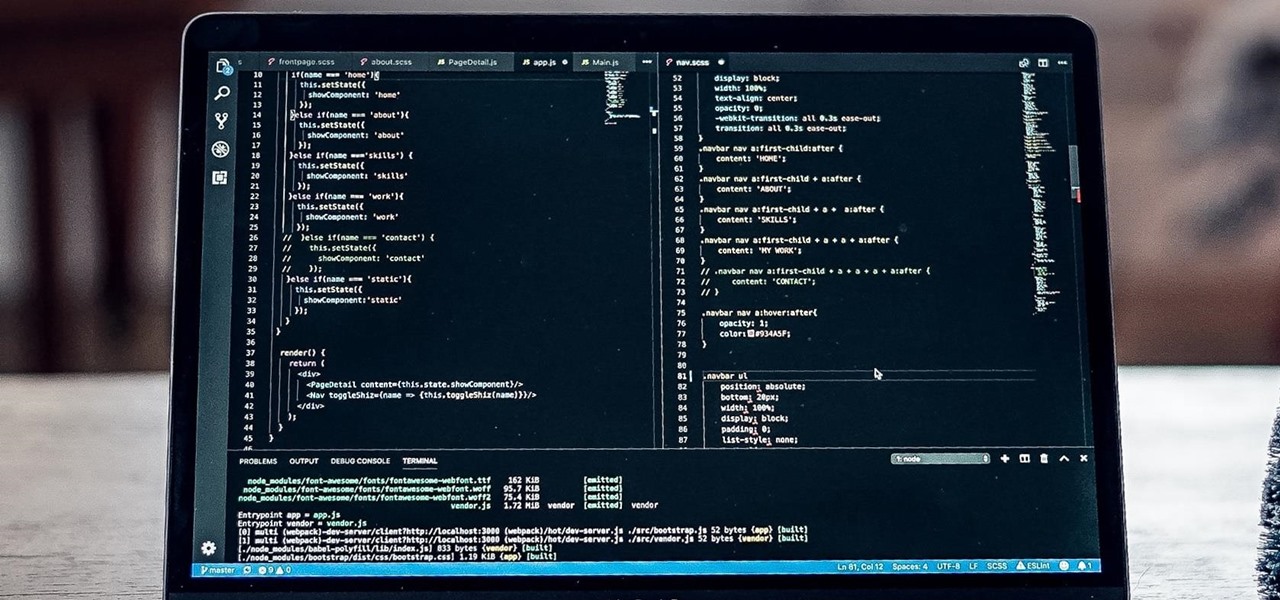
If you want to be truly competitive and successful in the world of web and app development, it's not enough to simply know a handful of programming languages and coding platforms. Today's best sites and apps require pro-level graphics and user interfaces, and knowing how to work with a wide range of graphic design tools is essential if you want to land lucrative positions as either an employee or a freelancer.

It's common knowledge that when it comes to your child being happy and successful in life, giving them access to an excellent education is paramount. Whether your son or daughter grows up to be an engineer or an artist, they should be well-rounded in a wide range of diverse disciplines to take advantage of all the opportunities that will inevitably come their way.

This year, over 2.7 billion gamers will spend nearly $160 billion dollars. That number is predicted to increase to over $200 billion in just three years. If ever an industry had growth potential, this is it.

Invented by Motorola engineer Bill Smith in 1986, Six Sigma's methodology defines a series of steps with specific value targets. These targets can be used, for example, to eliminate costs and process cycle time while increasing profits and customer satisfaction.

If you're a frequent Null Byte reader, chances are you're already up to speed with at least one or two programming languages or development platforms. But in a world that's becoming increasingly reliant on high-powered apps and responsive websites, knowing the fundamentals of just a few go-to programming languages isn't going to cut it if you want to be competitive and successful.

Since its introduction in iOS 11, the Screen Recording tool has been a great way to show less tech-savvy users how to use their iPhones better. It's never been easier to show your grandmother how to disable Live Photos or lower screen brightness. However, banner notifications can appear during a recording, forcing you to start over. They can even interrupt a screen share during a Zoom or Skype meeting.

Determining the antivirus and firewall software installed on a Windows computer is crucial to an attacker preparing to create a targeted stager or payload. With covert deep packet inspection, that information is easily identified.

It's OK to want an extended break when you're working or learning from home. Maybe you want to play a video game, spend more time with your family, hang out with your dog, or FaceTime with friends. But how can you do that when you're supposed to be in a Zoom video conference or class? Thanks to one Zoom feature on your iPhone, it may be easier than you think.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

It looks like Pokémon GO players may get a surprise gift from the game's developer, Niantic, this holiday season.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

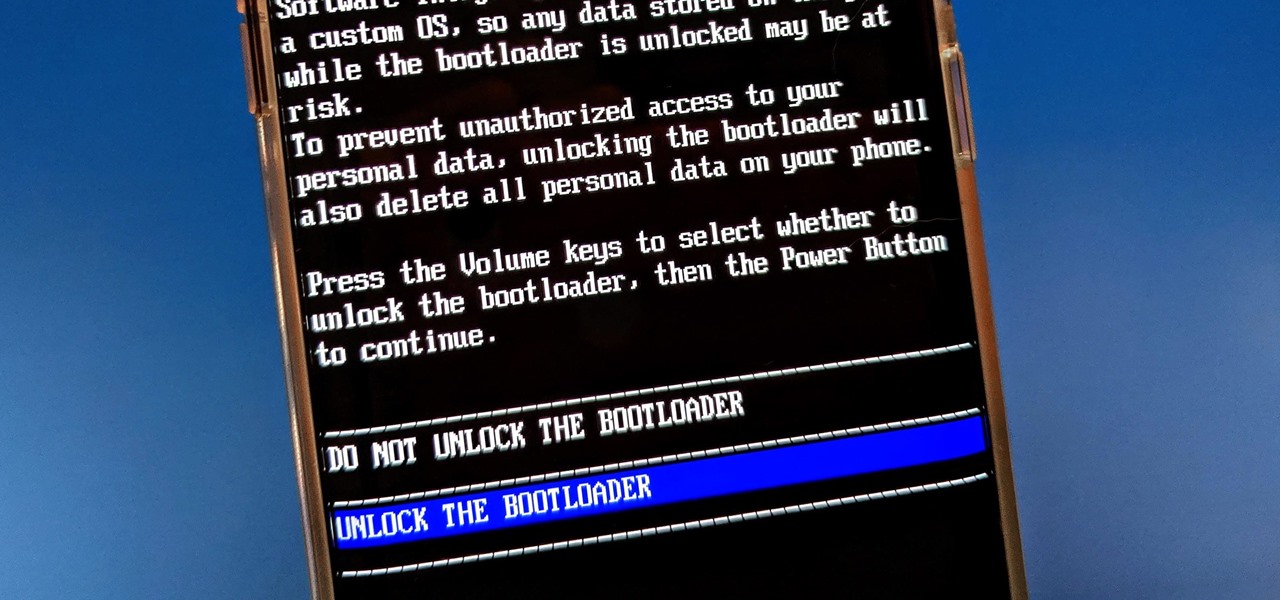
Apple's innovations often involve more taking away than adding on. The company has released seven iPhones that omit the home button, the latest batch including the iPhone 11, 11 Pro, and 11 Pro Max. If you recently picked up one of these devices for the first time, you might be a little confused on how to enter DFU mode when your iPhone acts up.

Sticky notes and the refrigerator go perfectly together, like chocolate and peanut butter. They're particularly popular among families with young kids, so they've been a key part of our personal lives for many years now. But what if you could turn those sticky notes into a digital format? Now you can.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

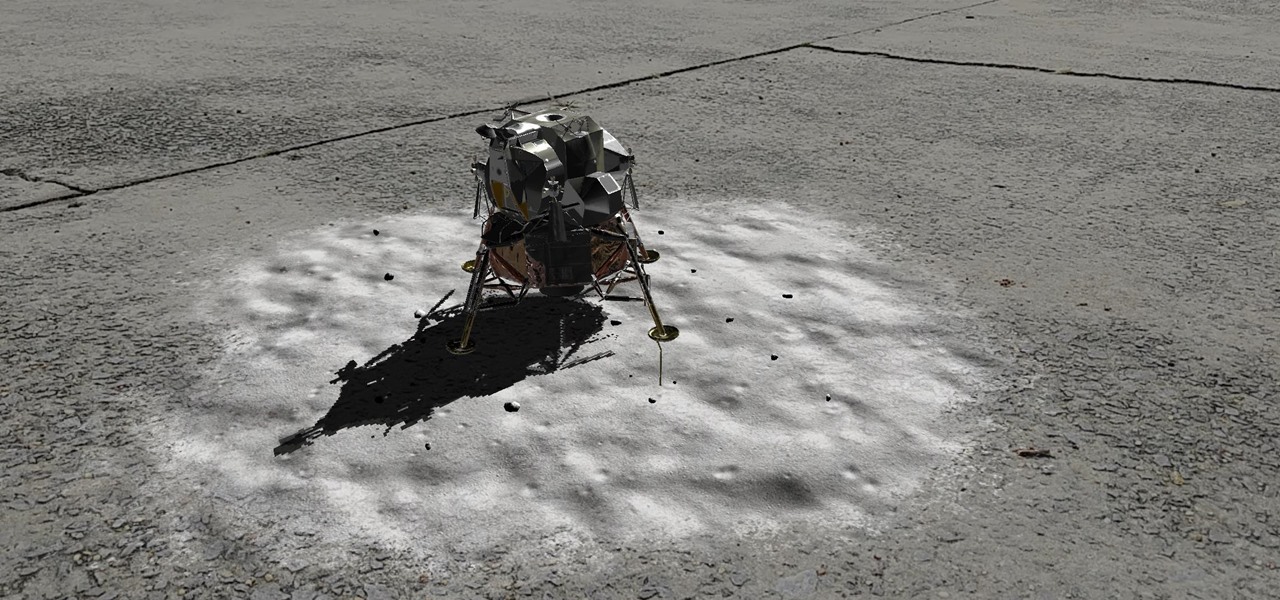
Unless you've been hiding under a (moon) rock for the past month, you already know that Saturday, July 20 is the 50th anniversary of NASA's Apollo 11 lunar landing.

The future of smartglasses for consumers seems ever dependent on Apple's entry into the market. Coincidentally, the exit of Apple's long-time design chief Jony Ive has shed some light on that eventual entrance.

One of the best ways to dig into a website and look for vulnerabilities is by using a proxy. By routing traffic through a proxy like Burp Suite, you can discover hidden flaws quickly, but sometimes it's a pain to turn it on and off manually. Luckily, there is a browser add-on called FoxyProxy that automates this process with a single click of a button.

The OnePlus 7 Pro is truly the best phone that the company has ever created to date — it's even one of the hottest phones around regardless of OEM. It offers an awesome display with minimal bezels, a smooth 90-hertz refresh rate, a pop-up selfie camera, and the best triple camera system in a OnePlus phone so far. It can truly compete with other flagship phones while keeping the cost down.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

If you want your photos to look like they came straight out of a movie scene, the best method is to use split toning. Many Hollywood producers use this effect to recreate the cinematic look of cameras before the digital film era, which is why most people associate split toning with a cinematic feel.

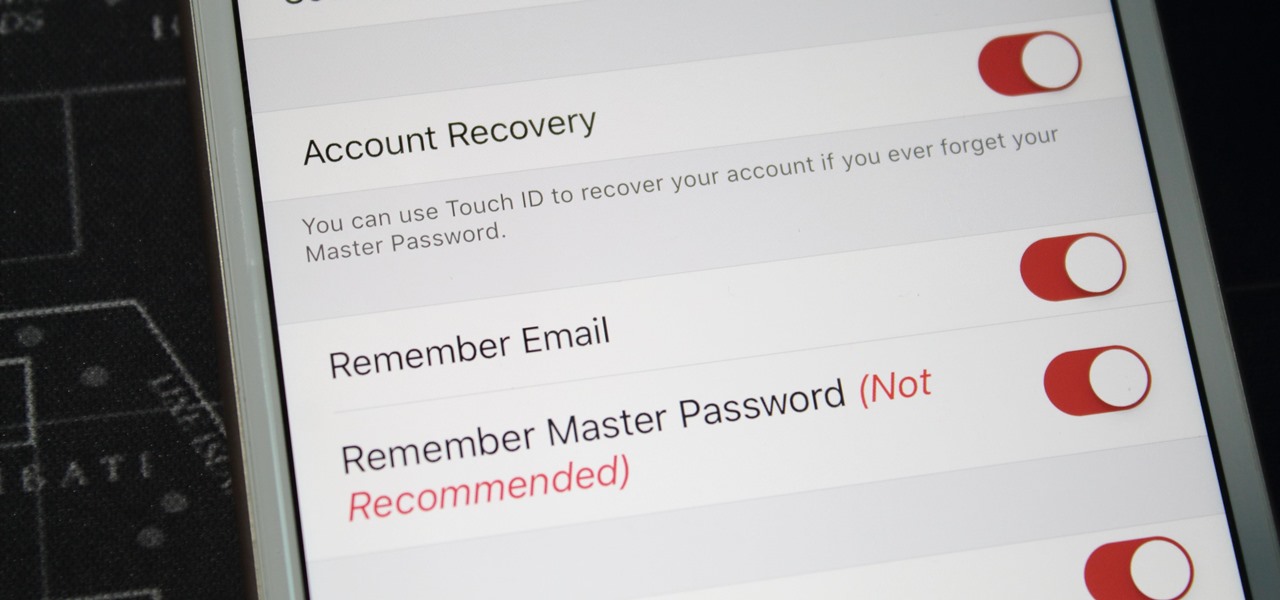
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.

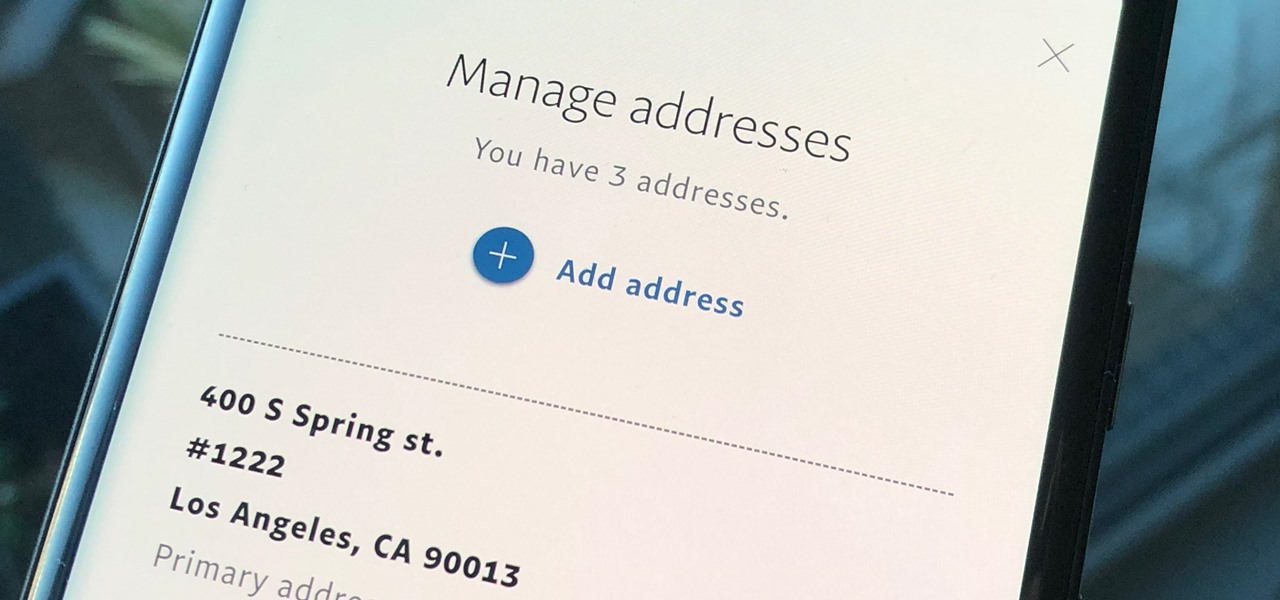
Whenever you move into a new home, whether that's a house or apartment, changing addresses on all your online accounts is one of the most monotonous tasks that needs to be done. It's even more tedious when you have to update both shipping and billing addresses. But it's necessary, and if you regularly use PayPal, it'll be one of the first places you'll want to update.

Over the past two years, the tech industry has formed a series of symbiotic relationships that are now converging in the augmented reality space. This week, we took a look at these interrelated technologies and how they are shaping the future of AR.

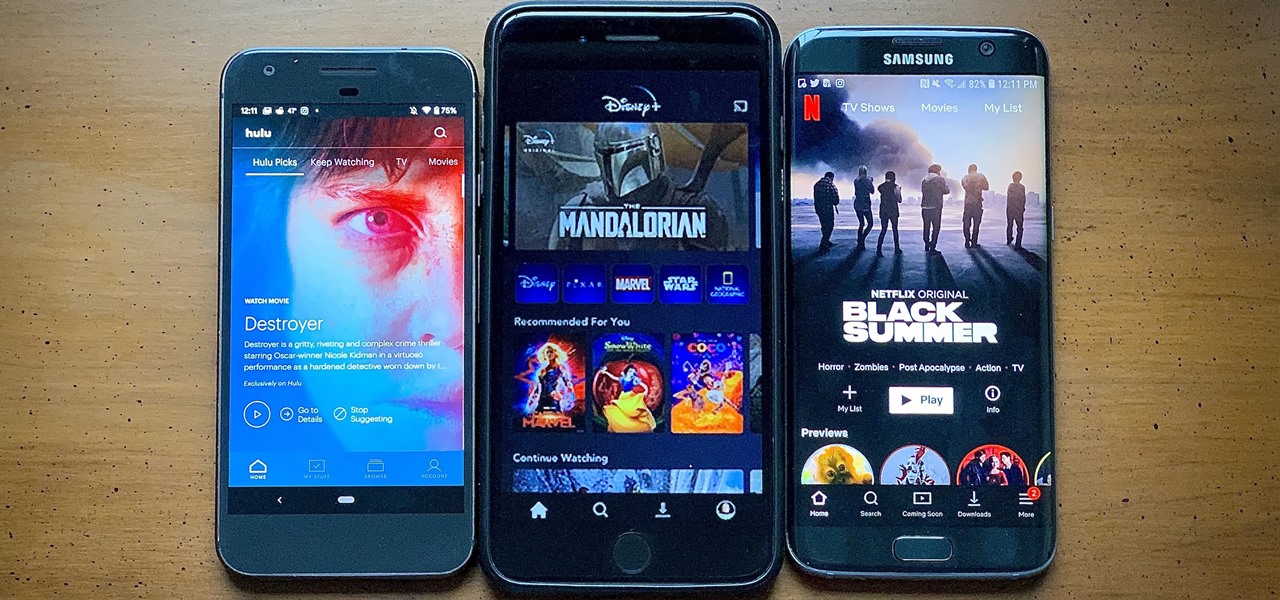
After much anticipation, Disney finally revealed its plans for its exclusive streaming service. Disney+ launches Nov. 12, and with it, all of the Disney content you know and love. But do you really need another streaming app in your life? We asked the same thing, so we broke down what we know about Disney+ and compared it to the current competition.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

If you use the internet regularly, it's nearly impossible to avoid memes. They are the epitome of internet culture, demonstrating how jokes can spread and change like wildfire. While there are many different types, the most common ones you'll come across are images and GIFs with humorous text accompanying them, and we've found the best iOS apps to help you create your own.

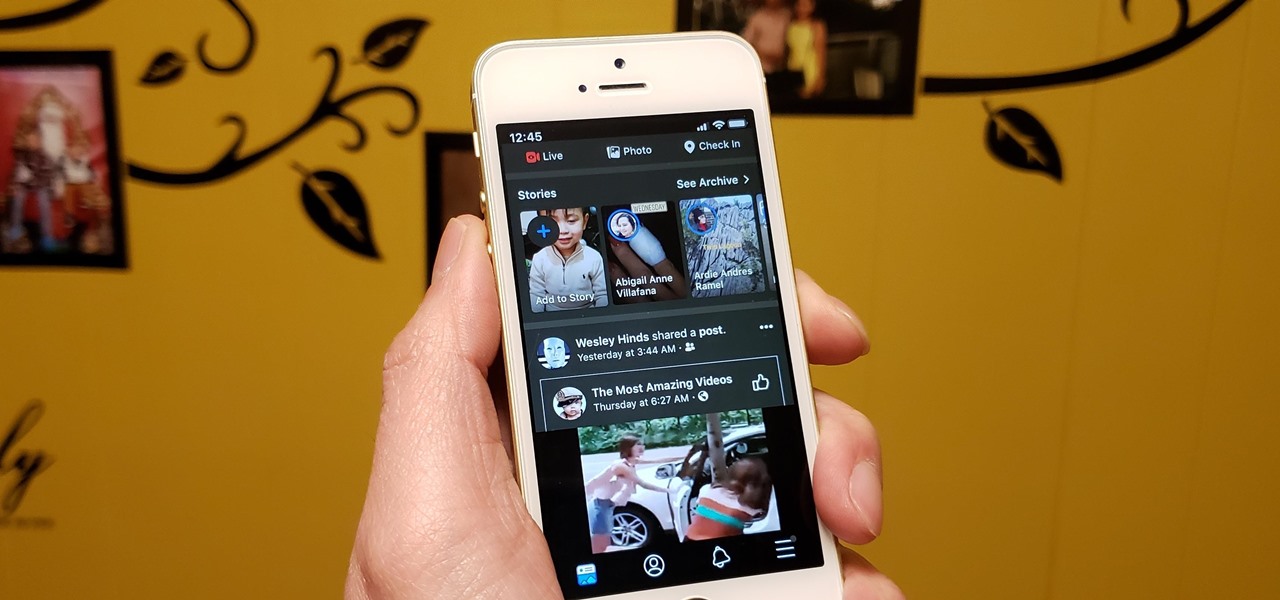
Dark mode support has steadily made its way to mainstream acceptance, with big-name apps like YouTube, Reddit, and Twitter adopting the feature to satisfy user demands. In this regard, Facebook is lagging, yet to offer the sought-after feature for easier viewing in low-light conditions. If your iPhone is jailbroken, however, you don't have to suffer like everyone else.

Things that are supposed to make life easier for developers and users are often easy targets for exploitation by hackers. Like many situations in the tech world, there is usually a trade-off between convenience and security. One such trade-off is found in a system known as Distributed Ruby, which can be compromised easily with Metasploit.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

The saga of augmented reality startup Meta appeared to be at end, but there are new developments unfolding in real time that may either sink Meta deeper into trouble, or provide a tenuous lifeline for the beleaguered augmented reality company.