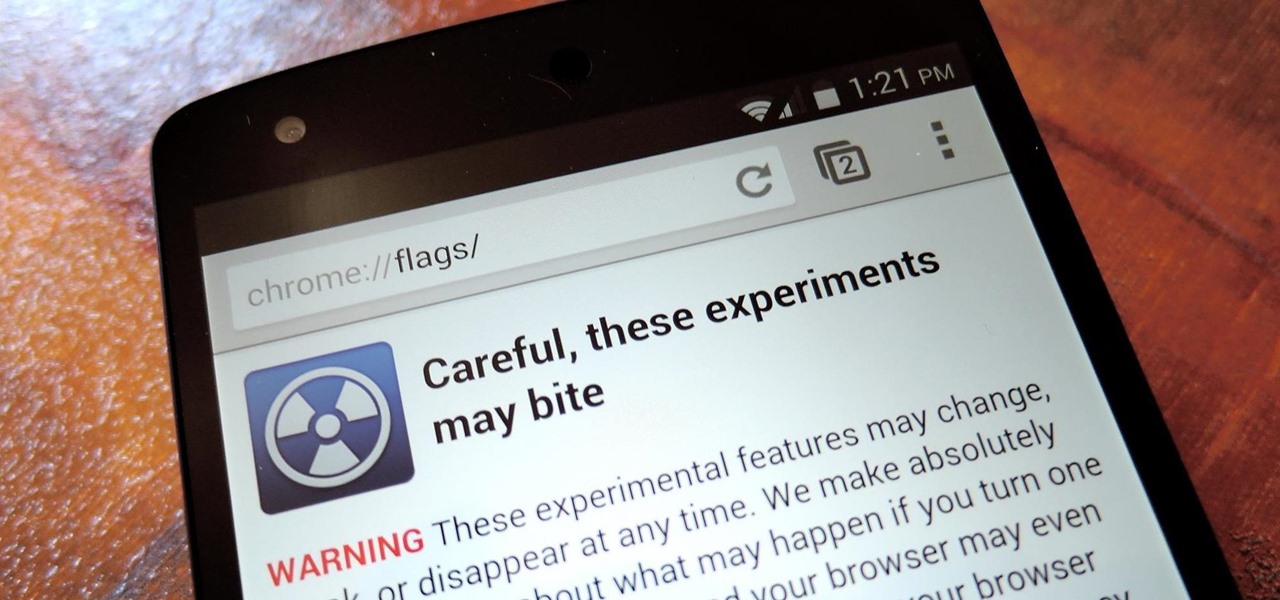
A while back, we told you about NoChromo, a no-root ad-blocking browser based on Google Chrome's open source code base, Chromium. That browser was wildly successful, as it offered an identical interface to regular Chrome, but without any ads. Sadly, the developer abandoned NoChromo, but a new ad-blocking Chromium port called Bromite has been released to fill its void.

Volvo Cars' claims it will offer Level 4 models by 2021 means the premium carmaker will likely have to finalize the driverless design to meet the aggressive timeline by next year at the latest.

Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

With Touch ID enabled, your iPhone needs to scan your fingerprint before you can access your home screen or last app used. Before it unlocks, your iPhone might request that you press the Home button, adding an unnecessary step between you and your data. However, you can turn the feature off so that you don't need to click any buttons to unlock your device.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

In my last post I introduced how to use ncat to connect to your Pi remotely, but what's the point to if you can't actually hack? This tutorial I'm gonna show you how to use very simple tools for a much bigger purpose. With that said, boot up our Pi and lets wreck havoc.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.

As you might know, there are a multitude of tools used to discover internal IP addresses. Many of these tools use ARP, address resolution protocol, in order to find live internal hosts. If we could write a script using this protocol, we would be able to scan for hosts on a given network. This is where scapy and python come in, scapy has modules we can import into python, enabling us to construct some tools of our own, which is exactly what we'll be doing here.

There may be no kitchen appliance as controversial as the garlic press. Professional kitchens and many avid cooks despise it, while others staunchly defend it.

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Loaded with a gorgeous display and a powerful processor, the Kindle Fire HDX is an impressive all-around tablet, especially when it's used for what Amazon Kindles were built for—reading electronic versions of novels, textbooks, and other printed works.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

With the release of Jelly Bean, Chrome became the default web browser on Android. The wildly successful desktop browser was now fully entrenched in the world's largest mobile operating system.

In order to unleash the full potential of your Samsung Galaxy Note 3, you've got to root it. These days, it's easier than ever, and can be done by just plugging your device into a Windows computer and pressing one button. It's so easy, your grandmother could do it, so what's stopping you?

Welcome back, my fledgling hackers! Awhile back, I demonstrated one of my favorite little tools, netcat, which enables us to create a connection between any two machines and transfer files or spawn a command shell for "owning" the system. Despite the beauty and elegance of this little tool, it has one major drawback—the transfers between the computers can be detected by security devices such as firewalls and an intrusion detection system (IDS).

Google's Nexus 7 tablet has just been released, and for only $199, it seems like a great deal. Now, some of you are probably immediately thinking that you're going to want to root this thing as soon as possible to install all of your tweaks. Luckily, some clever hackers have already developed a fairly automated solution to rooting the device. Here's how it works. A word of caution however, rooting your tablet will very much void the warranty and there's no 100% guarantee that this procedure w...

Curious about fishing? Looking for an easy pattern to start off with? Check out this instructional video and learn how to tie a simple calf's tail jig. This fishing jig is particularly successful in the fall season.

Calf drops are simple exercises that produce big results. Calf drops involve standing up on your toes on an elevated plank, shifting your weight to one foot, and then lowering yourself down.

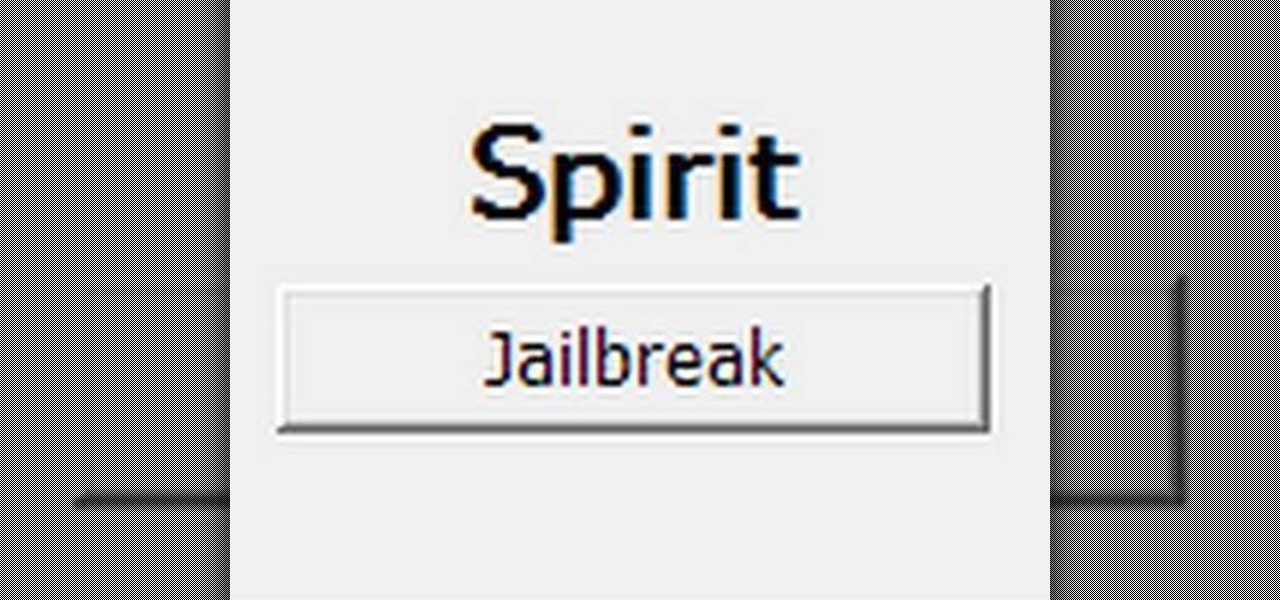
Now that you're officially allowed to do it, jailbreaking your iPhone, iPod Touch, or iPad is a better idea than ever before! This video will show you everything you need to jailbreak a wide variety of Apple devices, including the iPhone 3G and 3GS, the iPod Touch 2G and 3G, and the iPad wifi or 3G model. All you need is a program called Spirit, iTunes version 9.2, and you device and you're good to go! This particular method is great because the jailbreak is untethered, meaning that you can t...

If you want to run multiple windows operating systems at the same time you first need a Windows computer, the installation disk for the operating system you want to run, and Windows Virtual PC 2007. To install this, first type in Virtual PC 2007 to Google, go to the Microsoft link and download and install the program. Now, open the Virtual PC and click next on the wizard. Name your hard disk and click next until you choose where you want this at. Now your virtual hard drive is created. Now, p...

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install the latest Wine on Ubuntu Linux.

Running on a track might be a little repetitive, but it’s also easy, even and a simple way to measure your pace.

Toilets are some of the best prank aides, and this video will teach you a novel way to use them. All you do is connect the hose that fills the tank with water to another longer hose, then run it to under the sink and attach it in a position to spray outward. Then wait for your victim to flush.

In this video, we learn how to do the Prologue Speed Run achievement in Mirror's Edge. You can unlock this after finishing the main story. The prologue has a qualifying time of three minutes. Rather than jumping to the left, you can jump straight and hang onto ropes. You can also jump along a beam and that will save a lot of time. Make sure you grab the left bar and then you can maneuver around a lot more easily. Continue to run through the level doing a fast speed. Once you are finished, you...

In this clip, we learn how to jailbreak an Apple moble device running iOS 4.1. This, of course, includes the iPhone 4, iPod Touch and iPad. Learn how to download an run the limera1n jailbreak tool with this hacker's how-to.

The Running Man was everywhere in the 1990's, and we do mean everywhere. From Will Smith to random kids on the street trying to look cool, the move was popularized by the likes of MC Hammer and Vanilla Ice.

This video is about your magical bathroom device— the toilet. The toilet is a thing that sees a lot of use in the house, and problems can arise from time to time. One of the biggest bathroom issues is a toilet that runs on after flushing, or starts running or flushing by itself. It's a possessed porcelain poltergeist. Lowe's knows that's this problem can really run up your water bill, and they have some advice to stop that leaky toilet.

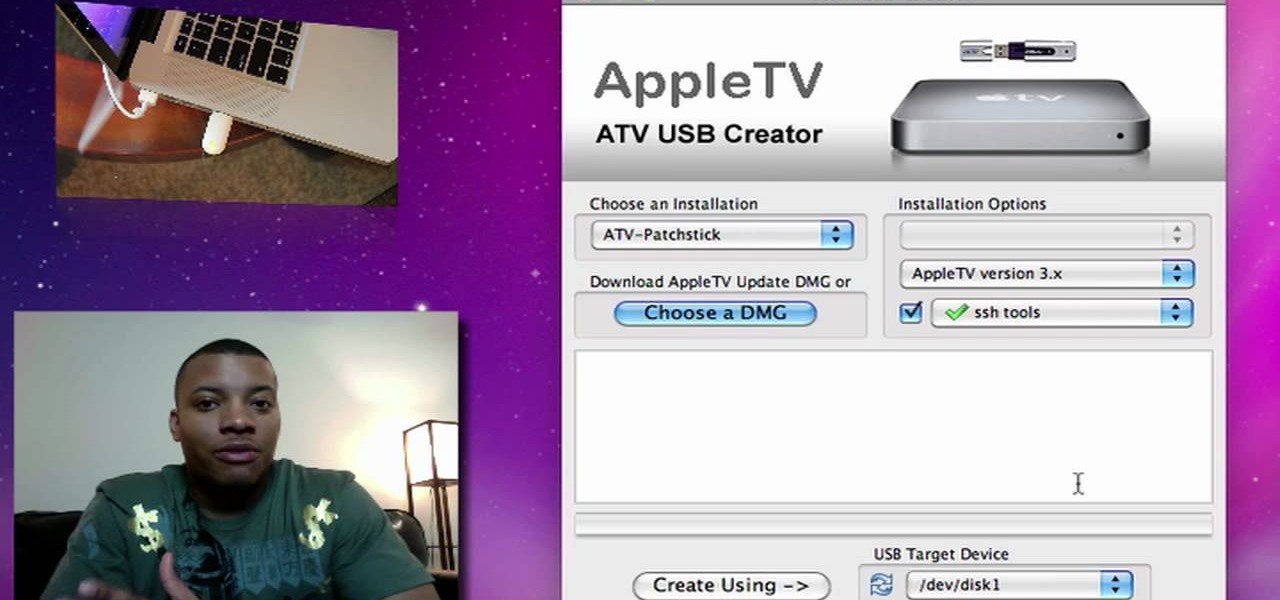
This useful step by step tutorial shows you how to download the ATV USB creator, which will allow you to create a patch stick for your AppleTV. Once you load this usb stick onto your Apple TV, you'll be able to run Boxee and get streaming Internet content directly to your Apple TV.

By loading Boxee onto your AppleTV, you can use it to watch content from Hulu, Comedy Central, CBS and other streaming TV websites. You can also play Internet radio, listen to your mp3s and view your photo library without ever having to go near iTunes. All you need is a patch stick with the right program installed, run it, and then update the Boxee software from the Apple TV system.

Patrick Norton and Dave Randolph show you several ways to hack or mod your new AppleTV to increase functionality. Namely, you can increase the hard drive space, set up an RSS feed, and get your Apple TV running SSH and Xvid.

This tutorial will work for iPhone, iPod Touch or even the iPad to jailbreak your Apple device by going to spiritjb.com, downloading the program and running it on your PC or Mac computer. Once you've downloaded it, all you need to do is run the program while your device is connected to the computer.

Do the Melbourne shuffle Running Man kicks

Are you tired of getting annoyed that your computer is running Windows XP too slowly for you? Increase your computer's speed by checking your disks for errors and defragmenting your hard drive, or updating your hardware to more advanced technology.

Learn how to browse and play voice memos you've recorded on a BlackBerry phone running version 5 of the BlackBerry OS. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Learn how to record new voice memos on a BlackBerry phone running version 5 of the BlackBerry OS. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Learn how to set up email on a BlackBerry phone running version 5 of the BlackBerry OS. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

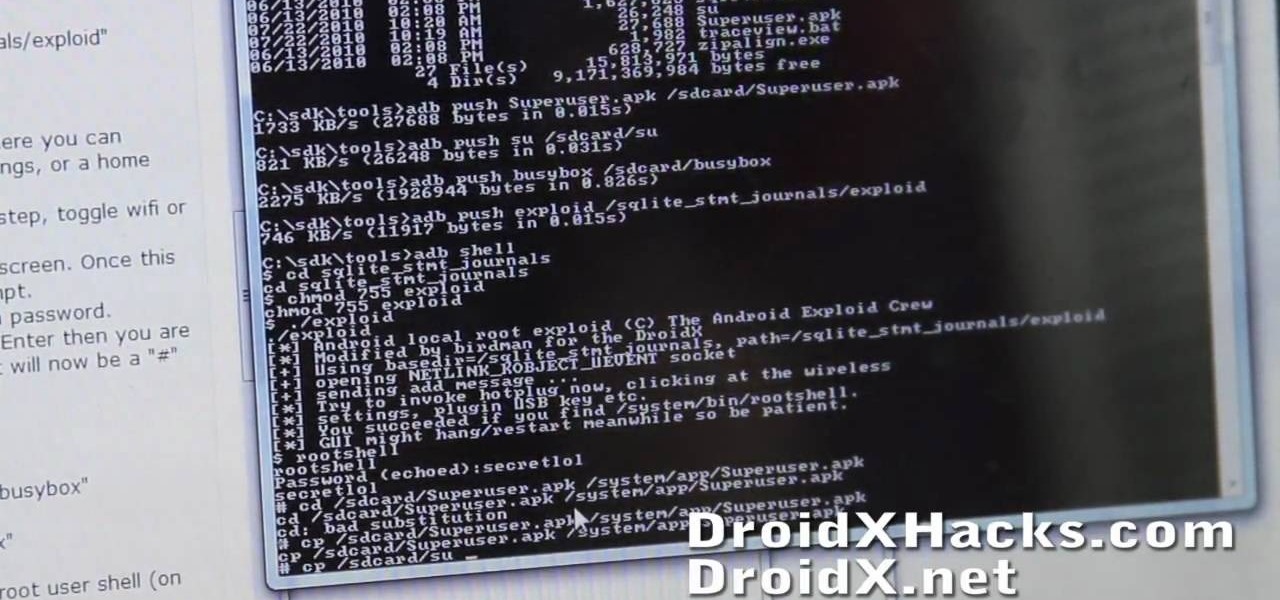
Root your Droid X Google Android smartphone and run custom ROMs! This hacker's how-to presents a thorough, step-by-step overview on unlocking and rooting a Motorola Droid X smartphone. For detailed instructions, and to get started rooting your own Motorola Droid X phone, watch this free video tutorial.

This next tutorial is going to show you just how easy it can be to check your vehicle's alternator. There isn't really much that you need, just a tester or DVOM and some time.