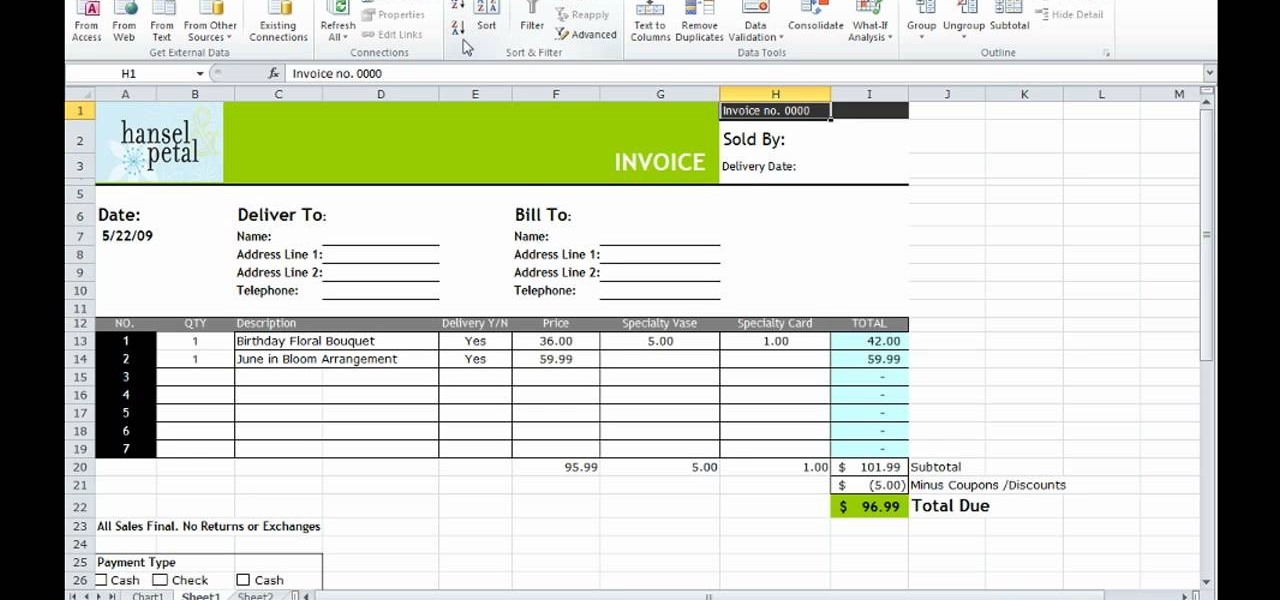
How To: Use the Ribbon and Backstage view in MS Excel 2010
This how-to video is about how to use the Ribbon and Backstage view in Microsoft Office Excel 2010.


This how-to video is about how to use the Ribbon and Backstage view in Microsoft Office Excel 2010.

If you've ever had a little trouble trying to program your calculator, you may find a little relief with this four-part video tutorial. Here, a Texas Instruments (TI-84 Plus) calculator will be used to explain the programming process. The four parts include:

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

Welcome back, my budding hackers! Previous to this tutorial, we've focused mostly on hacking the target system. If we're successful in owning the target system, we'll then want to make certain that the system administrator doesn't know we were there, and that he or she cannot track us.

Are you an avid runner who's jogged almost every day since your twenties but have found recently that you just can't run as long, or that you start to feel pain more easily? Then check out this running video for a helpful series of technique drills that will help you strengthen your muscles and correct your form.

Running uphill is way harder than tumbling downhill or running on a flat surface due to the incline. And when you're running on natural terrain, like a hill, the incline can change quickly and can also be clouded by rocks, plants, and other things that get in the way.
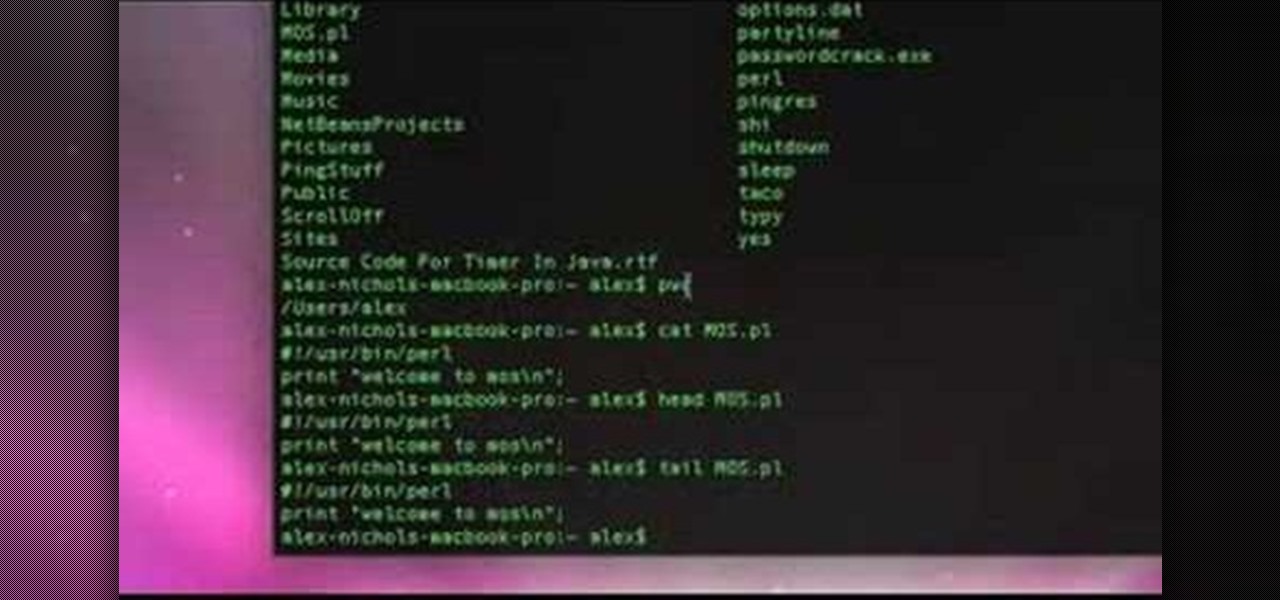
Every Apple computer running Mac OS X comes with a handy application called Terminal… MacBooks, MacBook Pros, Mac Pros, iMacs, etc. They all have Apple Terminal, and it can be found in your Utilities folder in Applications. Which means you can use it.

This shows us how to run faster by following a few tricks which we neglect without knowing them. This would help the athletes to run faster without wasting much of their energy with wrong postures. By taking care of these little things shown in the video one can make proper use of their stamina. Not only athletes but those who workout daily for their fitness of their body would be benefited.

In this outdoors how-to video from fitclimb.com we're shown how to make a fire in the snow. The first step is to find a good flat spot, or make a flat spot yourself. Next, we look for trees with dead branches and break those dead branches off for the wood. The key here is to be organized because you'll have to carry this wood back to your camp. Next, you want to make a platform for your fire to keep it from sinking down as the snow melts. Here, we're using the bark from a dead stump for a pla...

Find Osman in the Cathedral Square to deliver Alexander's message to him in Mission 5 on the Sony PSP. Make your way to the Cathedral area, at which point the red delivery icon pops up and denotes Osman's rendezvous point. The only problem is that the area is swarming with guards and that Altair must make successful contact without being detected. Climb up the first buildings in front of you and hop across toward the icon. Silently dispatch the archer on the roof and then head around to the o...

Learn how to teach your dog to high-five. Make your pooch the hippest dog on the block by teaching him how to greet you with a high-five.

Rolling over is a simple trick that any dog can master, and it will help you build confidence in your dog. Learn how to teach your dog to roll over with this how to video.
(Series designed to help explore whether your ideal employment ideas should be formalized into a business venture or as an employee or volunteer value added problem solver).

You've manage to get your hands on some ruthenium, and now you want to destroy the hard silvery-white metal of the transition series. Well, you're going to try all kinds of ways to dissolve this odd metal, but the only successful way to dissolve ruthenium is with a common household cleaner… bleach.
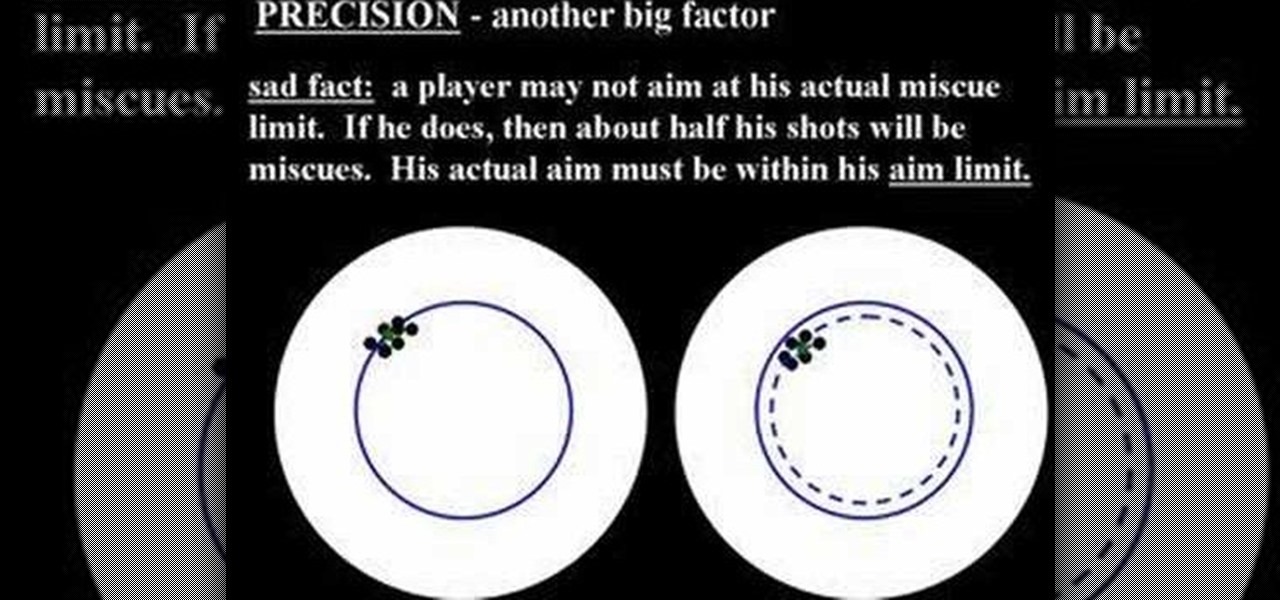
Cue ball draw refers to the way a cue ball strikes a rack of balls. In particular, if the cue ball is hit low on the ball, when it strikes a rack of balls, for the break, it will have enough backspin to wind its way back to the shooter.
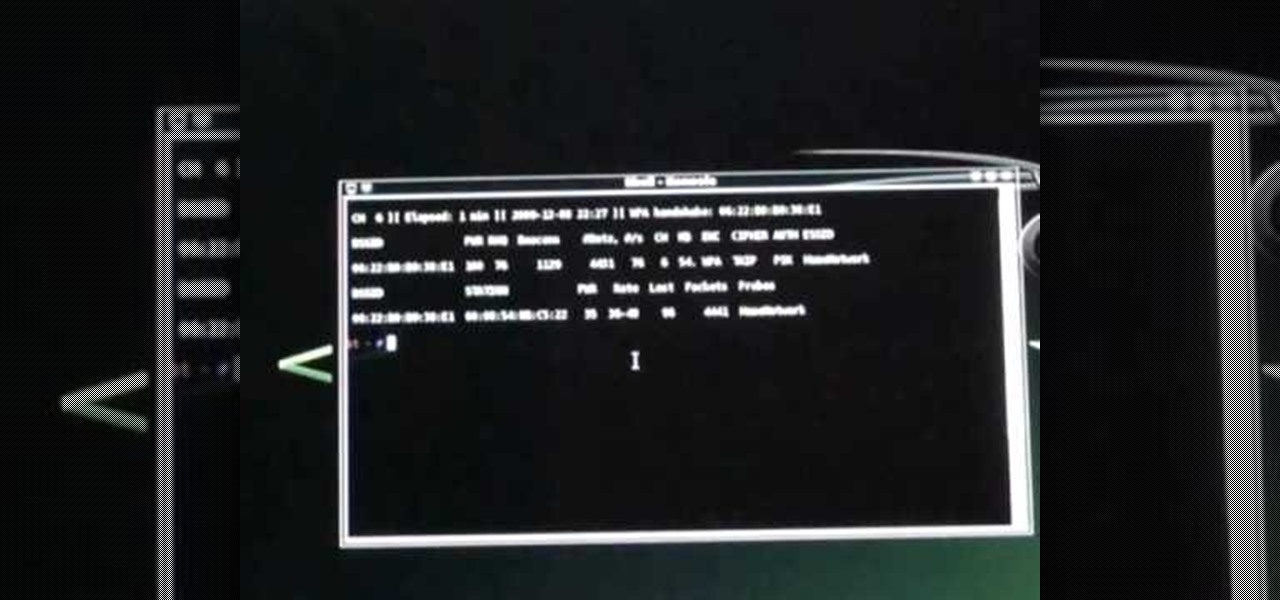
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...

Pushups are a great workout at any level of bodybuilding. However, if you feel that you're ready for something more advanced, dumbbell rows are a good option for the next step in your advancement. They offer a new challenge and a different way to work out the same muscles you do with pushups.

In this how-to video, you will teach your dog how to target objects with its front paws. You will need a clicker, treats, and a target such as a yogurt lid or ball on a stick. Take a treat and hide it under the object. Click when the dog does any paw movements towards the object. After ten successful tries, pretend to put a treat. Once the dog paws the object, show that there is no treat but still give the dog a treat. Once this is done, wait until the dog paws the object, and give a treat. I...

One of the key fundamentals to playing a successful game of golf is to master your grip on the club. Stand in front of the club with your hands relaxed at your sides and let the club fall into your hands. Next, bring the club around front and set it down. When you position the club to hit the ball you will see two to three knuckles of your left hand. Your right hand will be hanging relaxed at your side. Bring your hand up like you are shaking hands with somebody. When you look down, the V sha...

In a 2010 Toyota 4Runner, you can connect your phone to the car via Bluetooth. To do this, make sure the car is stopped. Then click the info button next to the navigation screen. Press "Phone" and confirm that you want to connect a new phone. Press "Add New". The car's system will begin searching for Bluetooth devices. Make sure that your device's Bluetooth feature is on. When prompted, enter the code on the car's navigation screen into your phone. A message that says "Bluetooth connection su...

This is a video that teaches you how to connect a Nintendo DSi to the internet. In order to connect a Nintendo DSi to the internet, you have to do this.

Making a batch of candy this holiday season? To make a successful batch of candy, you need the precise temperature, consistency, and timing during the cooking process. Watch this video to learn how to use a candy thermometer.

Whether you're hanging out at the beach, laying by the pool, or walking around in sandals, having nail fungus is not the most attractive thing to flaunt.

If your personal food pyramid replaces “Grains” with “Pizza” and “Fruits and Vegetables” with “Taco Sauce,” it’s time to make some changes.

Longing for the coziness of a fire? Follow these tips for a safe and successful experience. You Will Need

Whether you're on a job interview or a first date, follow these simple steps to give the impression that you're quite intelligent – even if you're quite average.

Check out this video tutorial on how to make free phone calls from your iPod Touch or iPhone to any other phone out there. You will be using a free application from the iTunes App Store called Fring. This allows you to make VOIP phone calls.

Train is a dice game in which the object is to build a train. Learn about the train dice game in this free dice games video from a successful poker player.

A lot goes into making a hunt successful, and most of it happens before you take to the field--like making sure your rifle is properly sighted in. It's not hard to do if you follow a few simple steps: first, and this is the first step when you do anything with a firearm, make sure it's unloaded. Make sure your scope is properly mounted and the mounting screws are tight. Remove the bolt from the rifle and sight through the barrel to make sure you're lined up with a sight-in target placed at 25...

Check out this video to learn scoring techniques of joining two pieces of stiff leather-hard clay. Following are some steps you will see demonstrated

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

The once blurry and mysterious vision of Magic Leap's future is slowly coming into focus in the present, despite the company's obsessive attempts to keep any and all information under wraps until the next reveal is absolutely necessary. A new tidbit of information hints at an addition to the company's unfolding story that almost no one had accounted for: retail stores.
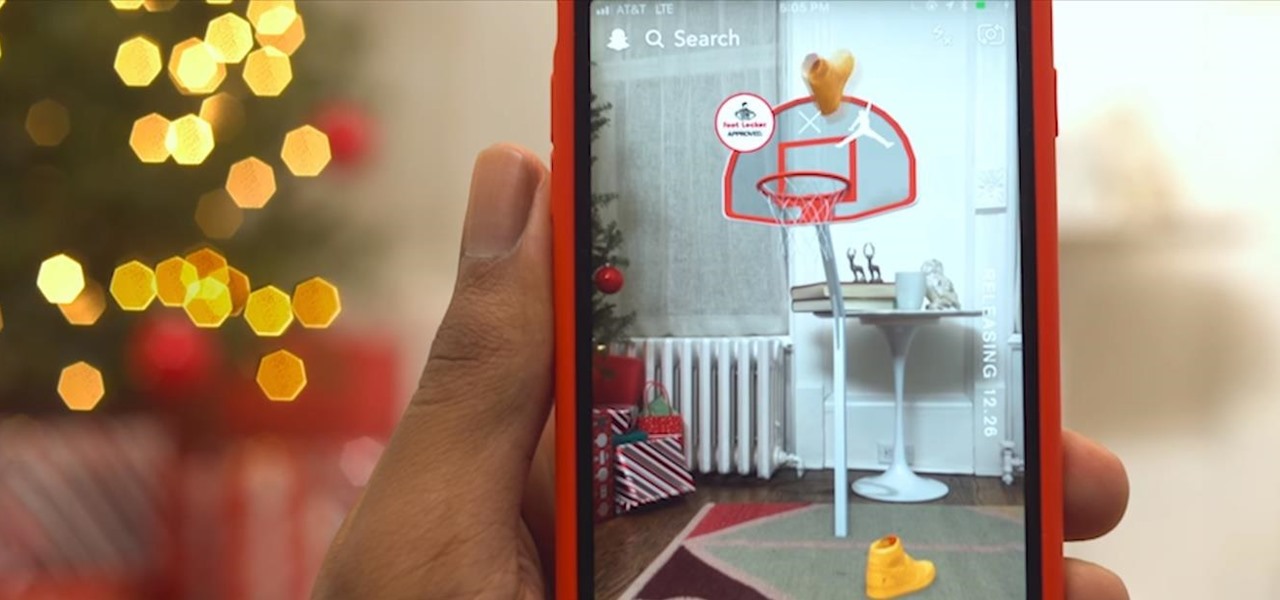
After closing its 2017 financial books on a high note, Snap, Inc. is planning to ride the momentum of its augmented reality products into the new year. That's the main takeaway following the company's 2017 earnings conference call, which was held on Tuesday.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.
For every cool new thing Android Oreo brought to the table, Android 8.1 adds a bit of polish. After a brief but successful beta period, Google started rolling out the official 8.1 update to its Pixel and Nexus devices today, and it's everything Android 8.0 should have been.
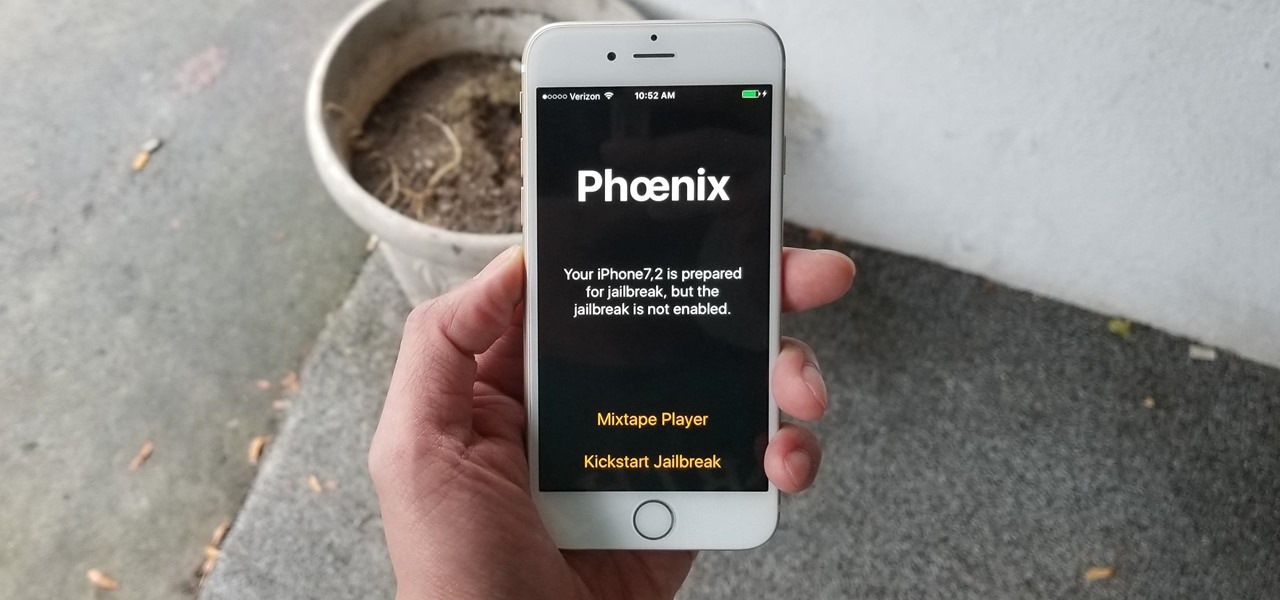
Unlike fully untethered jailbreaks such as Yalu's iOS 10.2 method, semi-tethered jailbreaks require users to re-enable the mod each time their device is turned off. Fortunately, the process of kickstarting a jailbreak is easy to do, since it's already embedded in your iPhone's OS and doesn't require reinstallation.