We're a little butter-obsessed here, and that includes topics on why butter should always be browned, the rationale behind clarifying butter, and even how to make a DIY butter candle. And while some may consider the problem strictly one for the first world, we're always very interested in ways to spread cold butter on toast without ripping the bread to shreds. If you read that post, you know the ingenious solutions are many and range from grating your butter to buying a heated butter knife.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Clash of Clans is one of the most successful games ever to come out for Android and iOS. It has been downloaded over 50 million times from Google Play alone, and shows no signs of decline.

Communication is the key to any healthy relationship, and when I say any, I mean human and non-human. Previously, one of the biggest culprits for not understanding what you meant was Siri, but now it looks like it has some competition with the new Kinect system, which can control practically everything on your Xbox One—if it can understand you.

You may not notice it when you're intoxicated and banging your head to the music, but when you're at a club or concert, your ears are getting seriously damaged. The noise level is usually above most people's pain threshold for sound, which begins around 120 to 140 decibels. At that level, it only takes a few minutes to damage your hearing. For me, there's something even worse than long-term hearing loss in a loud environment—not being able to hear or talk to your friends.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

In this tutorial, learn how to start out with wall running. Wall running is basically the ability to hop on a vertical surface and not only climb it but run, full speed all the way across. This is a pretty awesome move and will make you look just like a character in a sci-fi movie or video game like "The Matrix." Check it out!

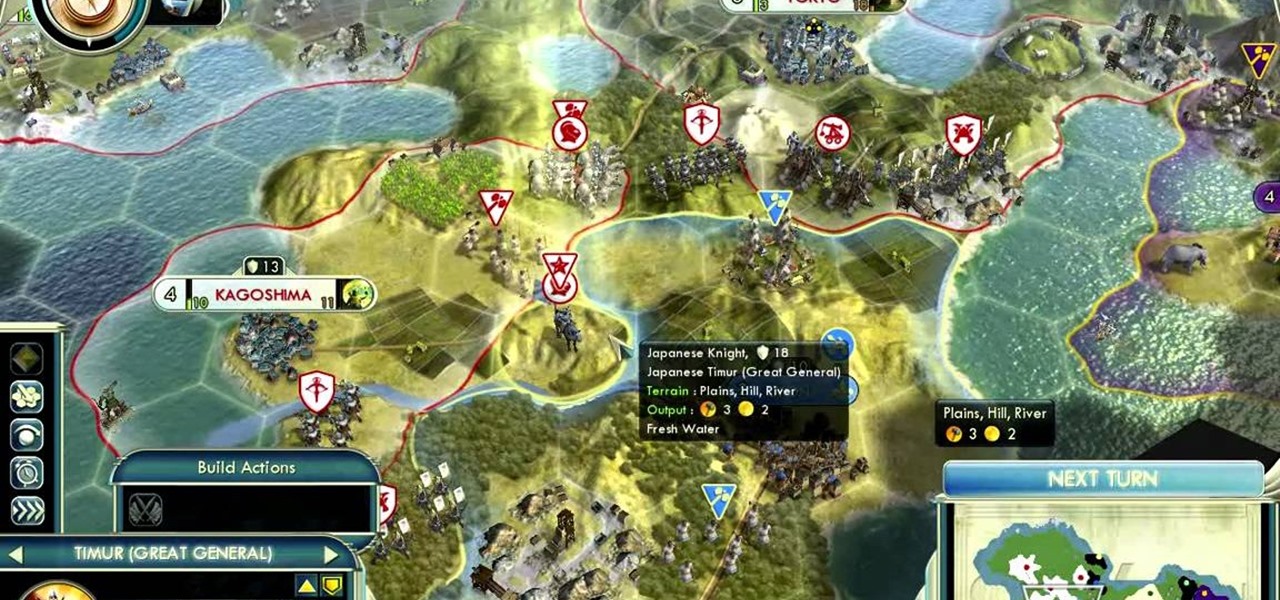
Crush your enemies beneath your well-equipped and well-trained boots! Whether you're primarily a defensive or offensive player, and no matter what civilization you are playing, you'll need to know how combat works to be able to win at the newest and most popular real time strategy game, Civilization 5.

The worldwide health crisis around the coronavirus has gripped the live events industry, particularly in the tech sector, with the cancellations of Mobile World Congress, the Game Developers Conference, Facebook's F8, Google I/O and now South by Southwest.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

Generally speaking, in terms of modern devices, the more simple you make an interface to navigate, the more successful the product is.

Amazon's first venture into the wireless phone market was a crash and burn moment — and that's us being kind. Their FirePhone went down in flames almost instantly, no pun intended.

There's a new operating system on the horizon, and this one's so big that it may actually live up to its galactic moniker. Andromeda, a merging of Android and Chrome OS, has the potential to bring Google to the ubiquitous status that Microsoft's Windows enjoyed in the '80s and '90s.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

My first ever post on here was 'Keeping your hacking identity secret' and it did very well, and its not something I see here on null byte. So read along.

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.

Admit it: you've been caught muttering to yourself under your breath in very public places. Maybe you've gotten stares while wandering the grocery store talking to yourself out loud. If you're like me, you might even talk yourself through various tasks, giving the atmosphere a little background noise.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

You've got to be sick of it by now. Those meaningless and unsatisfying articles, lists, and videos you were duped into clicking on because their headline made them impossible to resist.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

Text adventure games, such as the well-known Zork series, were some of the first computer games ever made, second only to the likes of Spacewar! and the better-known Pong. So let's travel back in time for a moment, to a time that never was.

This how to video show you how to keep your shoe from sliding up and down your heel while running. This will making those longs runs less painful.

Seems like it should be easier, but running downhill takes as much strength and control as running on the incline. Pick up the technique and you'll pick up your race time. You will need properly fitted running shoes

There's nothing wrong with running Windows on your OS X machine: all you need is Boot Camp, right? Wrong. There's a better way: virtualization software, such as the Parallels Desktop for Mac or VMware's Fusion. If you run virtualization software, you can run Windows operating systems like XP and Vista inside of OS X. Features like "Coherence" or "Unity Mode" even let you run a Windows application as if it were just another OS X app. But which software should you choose? In this tutorial, CNET...

This is the ultimate guide to running with the bulls in Pamplona. The Pamplona Posse who has been running with the bulls for over 30 years, give expert advice about how to run with the bulls with Musis by Fast reaction

Feeling a little slow when you're running around in Battlefield 3? Find out how to run faster by using jumps while you sprint forward. This guide will show you exactly how to use the jumps so that you don't slow down.

If you're interested in seeing what it would be like to run Android on a real computer rather than a tablet or smartphone, you don't have to wait. This Android project has now made it possible to run Android in a virtual machine on either a PC or a Mac computer. You'll need the following command to merge the ISOs:

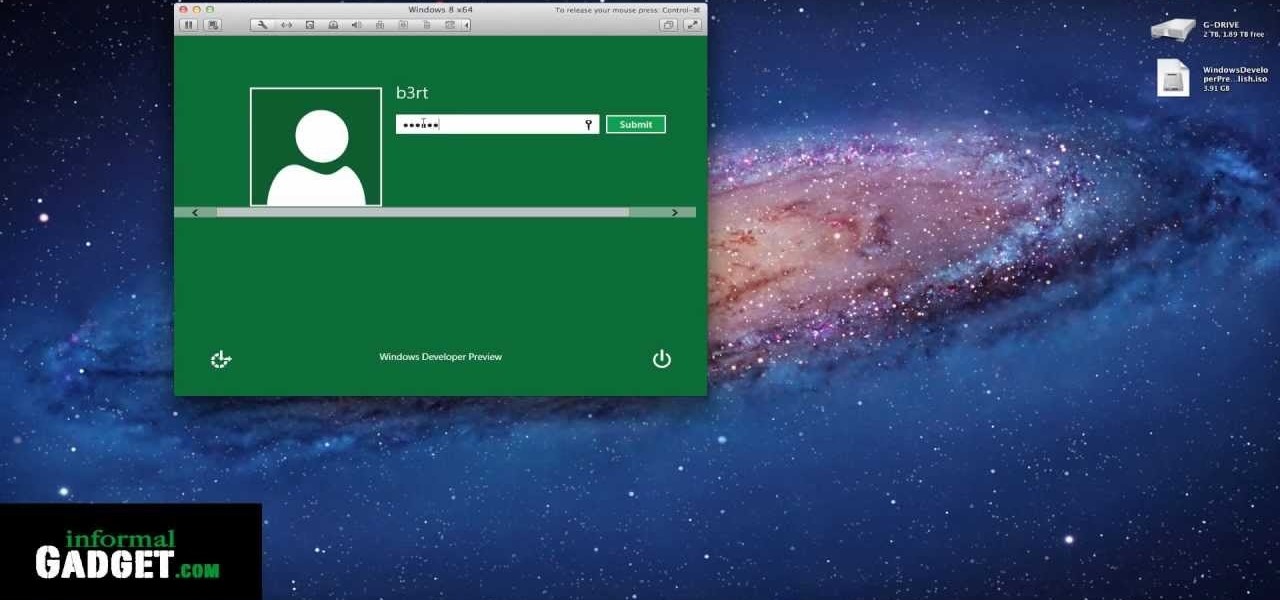
You can give the Windows 8 Developer Preview a spin on your Mac laptop or desktop by installing and running it with VMWare Fusion 4. VMWare Fusion 4 allows you to run Windows from within OSX so that you can have access to both programs and operating systems at the same time.

If you want to run Windows 8 inside of Windows 7 so that you can give the Windows 8 Developer Preview a try, take a look at this guide on how to run Windows 8 inside of VirtualBox. This will allow you to run Windows 8 within a virtual machine.

Run rabbit run! Well, your rabbit can't run unless you build it a place TO run! Check out this video and see how-to make a space in your backyard for your bunny to get its hop on. You'll need some tools, including a saw, screw gun, or hammer and nails and a skill saw. The dimensions are 80L x 43W x 36H. (measured in inches) This project takes about 4.5 hrs to build. Get building and give your fluffy little pet some outdoor love. Know what? He'll return it in leaps and bounds. And hops.

Running over someone's head or burying them alive so that they can rise from the grave are dangerous, and not worth using in filmmaking generally speaking. But yay, there are special effects! Watch this video for a guide to running over someone's head with a car or burying them alive for your film using After Effects and some fun props.

If you've just finished your paint job on your vehicle, then you're not done yet— you still have to clean up, and making sure the paint gun you used is properly cleaned is the key to successful future spray painting. This video shows you how use clean the spray gun with a paint gun washer.

The Android operating system for cell phones from Google lets you run multiple applications at the same time! By long pressing your home key (touching and holding) you can easily go back and forth between your most recently used apps. When you listen to music, you can easily switch to other apps while still enjoying your tunes! This video shows you the gist of it. Learn to run multiple apps on your Android-powered phone.

1. Open Web Browser and go to WWW.Google.com and type crucial memory mechanic and press enter. 2. Click the first result found on the search page( i.e., lolo memory mechanic)

Wedding insurance, vacation packages, travel discounts – the American Automobile Association offers its members more than free towing.

In this short automative customization and restoration tutorial Chris shows you how to properly mount your running boards on your vintage VW. He also give you tips on what to look out for before buying a Beetle. Watch and learn how to replace or add some running boards to your Volkswagen beetle bug in this classic restoration tutorial.

Movement, awareness, and anticipation make racquetball strategy successful. Learn about racquetball strategy and court positioning with this free video tip from a professional racquetball player.

This tutorial for Devil May Cry 3 covers the basics of jump canceling and the overall advantages it will provide the player once mastered. The whole concept of a Jump Cancel (JC/JCing for short) is the cancellation of an aerial technique with a jump.

United States Womens Softball Team members discuss and illustrate how to run the bases correctly. The main techniques used are how to lead off then steal each base as the technique is different for each one, and perform the hit and run. The breakdown is great!

When running for more than 30 minutes, you'd better hydrate along the way. For every 1% dehydrated you get, your performance can suffer up to 5%.