Honeywell recently completed successful testing of virtual window technology that enabled drivers to maneuver an otherwise windowless combat vehicle on rough terrain at speeds exceeding 35 miles per hour.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.
According to the French Blog iGeneration, Apple Maps is hoping to get itself back on the map. How? By taking a page out of Google Maps' book and hiring freelancers from TryRating to manually check the accuracy of their locations.

Google Home now helps users to discover new music with an added "Listen" tab in the app. The feature offers suggestions based on the Cast-enabled apps on a phone, while offering other apps to download if you'd like to broaden your musical horizons. The playlists are curated to your individual taste and will adjust for different artists and activities, which is a pretty nifty feature. This means that Google Home can cater to your momentary mood change with music, which is a welcome addition to...

Independent game developer PlayFusion announced today a partnership with NEXON Korea Corporation, resulting in a Series A preferred share round to fund development of their entertainment platform. PlayFusion's platform applies augmented reality, Internet of Things (IoT), and audio recognition to Lightseekers, an original property that combines mobile gaming with smart action figures, trading card games, and other media.

After a successful Kickstarter campaign, a new smartphone manufacturer named Nextbit emerged, then released its first flagship device—the Nextbit Robin. The headlining feature of this colorful gadget is its cloud-based app storage, but the phone itself comes with a very polished and sophisticated suite of software.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

While your iPhone may have a built-in time-lapse feature, it's nowhere near as smooth as Instagram's newish Hyperlapse app, and it doesn't give you any speed control like the latter does. If you haven't tested out Hyperlapse yet, check out the short promo video to see just how well its stabilization algorithm works.

E3, or the Electronic Entertainment Expo, is the 20th annual trade show for video games and gaming tech. The event takes place on Tuesday, June 10th at the Los Angeles Convention Center, and you can watch a live stream of the event on Twitch.

Apple released the new Mac OS X 10.10 Yosemite in the Mac App Store for everyone to download and install for free on October 16th, 2014, but downloading a 5+ GB file for each of your computers will take some serious time. The best thing to do is download it once and create a bootable install USB drive from the file for all of your Macs.

Even if your business is mostly online and computer related you will need paper, which in other hand will need classifier to be sorted out and easily accessed. The paperless office is as much of a myth as the paperless toilet, so accept it, if you are serious about business, you need paper. Important contracts between customers signed on papers, leaflets, reminders, advert previews, drafts for preview at the table. The paper is always used even in today highly computerized epoch.

If I could think of one thing the world was missing, it would surely be more tablets. While people struggle between shelling out 200 to 500 dollars for a new iPad, Nexus 7, Kindle Fire, Microsoft Surface, or one of the hundred other tablets on the market, the folks over at DreamWorks have decided to make their own, aptly named the Dreamtab. The Dreamtab will have an 8-inch screen and favor applications with the use of a stylus, for coloring and the like. Total cost is rumored to be under 300 ...

Thanks to the popularity of casual gaming on smartphones, handheld gaming consoles like Sony's PlayStation Vita have been on the decline. But if you own a new PlayStation 4, the Vita is a nice thing to have, since you can easily connect it to your PS4 for Remote Play.

My wallet is useful for pretty much two things. The first, holding my credit cards, lottery tickets, and money (or lack thereof). Second, making my ass number whenever I'm driving.

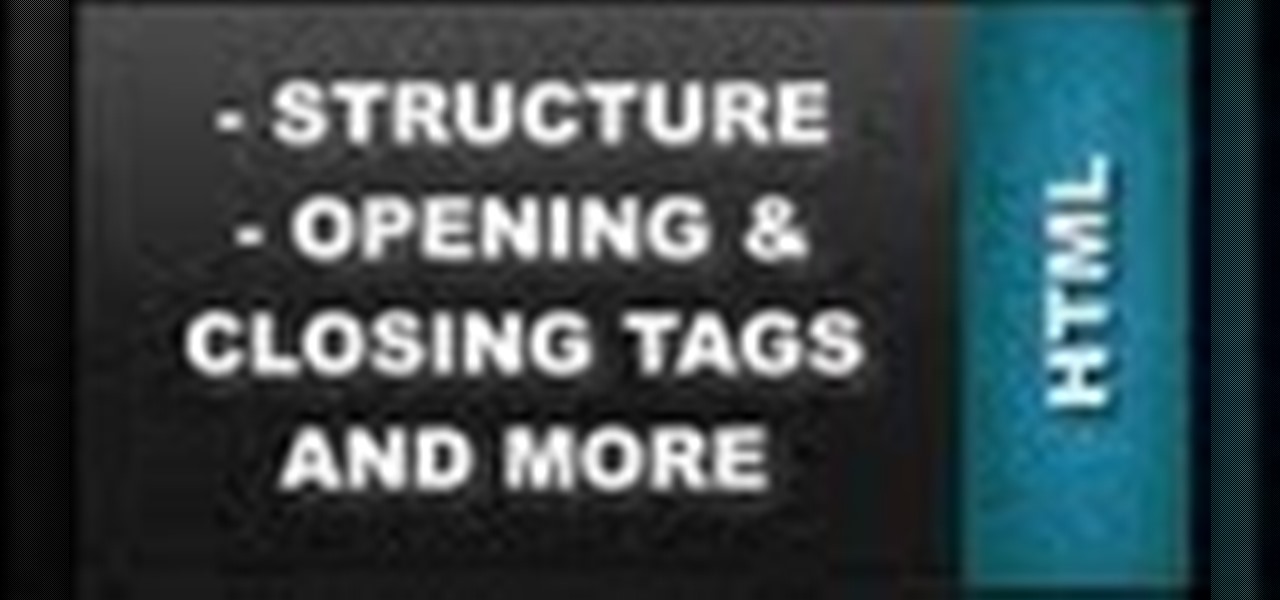
Learn how to setup up a basic structure for a HTML web design document, define the HTML version, open and close HTML tags and learn how to apply the proper file extensions when saving document in notepad. This web design tutorial is by no means a complete structure for HTML coding and is only a brief introduction to HTML web design. This video will only go over a brief introduction to the structure of an HTML document and in a future tutorial we will go over additional components that are nee...

The Samsung Galaxy S4 has already received a ton of hype, as it follows one of the most successful Android phones ever—the Galaxy S3. While the phone isn't set to be available for a least another month, it does boast some pretty awesome features.
In the business world, it is always best to have the people you work with. For you to become the best you could give, here are at least 5 tips in using team building tools.

Cooking isn't something that interests me much, unless it results in a fast burning fuel and a successful rocket launch!

Earlier this month, Adam Cudworth, 19, launched a camera attached to a weather balloon into the edge of space. Battling tough winds, freezing temperatures, atmospheric pressure and tumbling speeds, the teenager from Worcestershire, England was able to capture these amazing pictures of the Earth's upper stratosphere. How to Send a Camera into Space

Christopher Nolan's Batman trilogy has been one of the most successful film series of all time, so it comes as no surprise that everyone wants their own real-life versions of the Dark Knight's gadgets and vehicles.

For years, astronomers have been trying to figure out how our galaxy came to be. Even with the help of high-performance computers, no model of a spiral galaxy has ever been able to recreate the Milky Way, until now. An international team of researchers has created the first successful simulation of what happened 14 billion years ago to give our galaxy its unique shape. Turns out, all they needed was a bigger bang. Photo by IntelFreePress

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Apple seeded software testers iOS 14.5 public beta 6 today, Wednesday, March 31. The update includes a new battery calibration for iPhone 11, 11 Pro, and 11 Pro Max, as well as two new Siri voices.

Apple just seeded developers the sixth iOS 14.5 beta today, Wednesday, Mar. 31. The update includes a calibration for battery health measurements for the iPhone 11 line, as well as two new Siri voices.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Ever a hacker can have their own business that goes beyond cashing in on profitable bug bounties. With the right skill set and certifications, an ethical hacker could build a cybersecurity firm, become a penetration testing for hire, or even just consult on preventive measures to defend against black hats. But learning how to start and grow a business is rarely easy.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

Like other popular social media apps, TikTok features a tagging system — dubbed TikCode — to follow people in your immediate vicinity. Instead of searching for their username, you can scan their TikCode, and TikTok will launch their page immediately. Of course, you have a TikCode of your own, so you can share yours with others in the same way.

A little over a year after emerging from stealth, augmented reality gaming startup Illumix has launched its first title using a familiar formula, but with a new twist.

It looks like Snap's foray into augmented reality billboards last year was successful, as the company has returned with two more outdoor advertisements for its Snap Originals series.

Haptic feedback is one of the iPhone's most underrated features. With Face ID, you'll feel a satisfying tap or two when buying something in the App Store or iTunes, unlocking protected notes, viewing saved passwords in Settings, and the list goes on. For the first time, Apple has added haptic feedback when unlocking your iPhone via Face ID, as well as a way to disable haptic feedback for Face ID entirely.

On Tuesday, Blue Vision Labs, one of three Google-backed companies working on AR Cloud platforms, announced its acquisition by ride-sharing company Lyft.