
News: T-Mobile & ZTE Add New Entries in the Budget Phone Race
The battle of the budget phone is well and truly underway, as both T-Mobile and ZTE have launched affordable new devices simultaneously.


The battle of the budget phone is well and truly underway, as both T-Mobile and ZTE have launched affordable new devices simultaneously.

A video showing what is alleged to be the new Apple iPhone 7 has appeared online. The uploader of the video claims that it was shot on one of Foxconn's assembly lines.
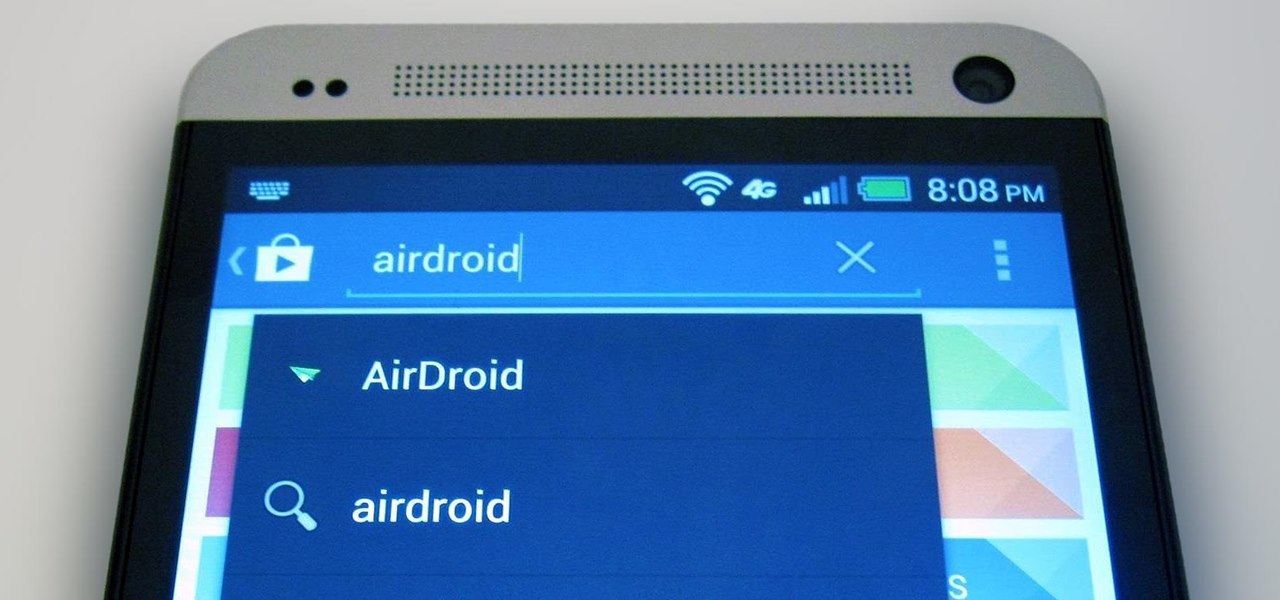
The first thing I do when I get a new phone is ditch the USB cable. At least, when it comes to data transfer. My brand new HTC One came with a USB cord that feels sturdy, but like any other cable, it will eventually fall apart from overuse. It will probably still charge just fine, but at that point it will be unreliable for transferring data. Lucky for me, there's a solution. Transfer files over the air. This will let you save that USB cord only for charging and the occasional situation when ...

For most people, the battery life on a DSLR is more than sufficient, but if you want to do a really long exposure or time-lapse, one charge might not last long enough to get the shot you want. You can always connect it to an extension cord to charge while you shoot, but that can be really annoying to work around.

Even if you're not a hipster with your own self-sufficient garden, making your own edibles at home can be pretty cool. And while it's obviously easier to pick up a bottle of 7-Up at the store, there's something undoubtedly fun about making your own. For those addicted to their fizzy drinks, DIY soda is a great way to save some cash and make their drinks healthier with natural flavors and sweeteners, instead of something like corn syrup or aspartame.

This video is a tutorial on how to weave a solomon bar bracelet with two colors. The author shows how to weave a solomon bar bracelet with two colors where there are vertical loops of one color and horizontal loops of yet another color. Combining this video with the author's previous video on how to weave a solomon bar bracelet (How to Make a Solomon Bar by TIAT) should provide sufficient information on completing a two colored solomon bar bracelet. While this way does work, it is mentioned i...

The man in the video shows us how to peel an egg open in 5 seconds by slamming the egg down on the counter (not to hard but at a sufficient speed) and rolling it for a bit then peeling it off with ease. As shown with the comments on the video's page, this task is not as simple as the title states. It takes a lot of practice to crack the egg just right without smashing it, but if done correctly, gets you that perfect, out of the shell, hard-boiled egg. This video teaches you that practice make...

With non-fungible tokens (NFTs), particularly those that are 3D in nature, holographic displays are becoming more indispensable for those looking to show off their valuable works of art.

When you're talking about collectibles, in 2021 it's heresy not to include the world of sneakerheads. Nowadays, a single, limited batch of newly designed sneakers from Nike can quickly sell out and then go on to be resold for many thousands more than they were purchased for at launch.

The hype surrounding non-fungible tokens (NFTs) has reached astronomical levels over the past few weeks, and now the technology has intersected with augmented reality's orbit in a fantastic way.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

It's always a good idea to know how an attack works at the very basic level. Manual techniques for exploitation often find holes that even the most sophisticated tool cannot. Sometimes, though, using one of these tools can make things so much easier, especially if one has a solid foundation of how it works. One such tool can help us perform a cross-site request forgery with minimal difficulty.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

The Galaxy S9 is now in the hands of millons of excited users. Getting a new phone is always fun, but it's important to think about protecting your device. Perhaps the most popular cases for the Galaxy S9 are the official OEM options from Samsung. There are a plethora of cases, whatever your preference and needs may be. Let's take a look at each case individually, along with the pros and cons.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

On Wednesday, June 6, the people at Magic Leap finally (FINALLY) decided to give the public a dedicated, slow, feature-by-feature walkthrough of the Magic Leap One: Creator Edition. How was it? About as good as it gets without actually getting to see what images look like through the device when wearing it.

We're on the verge of an amazing evolution of technology where we can work and play in virtual worlds that merge with our own—or let us escape into our imaginations entirely. But creating virtual, mixed, and augmented reality experiences requires resources and hardware that not everyone has access to. If you want to build something awesome with the Microsoft HoloLens (or one of the other awesome platforms), we want to help you do just that.

Microsoft enjoyed a few months in the spotlight after releasing the developer version of the very first mixed reality (MR) headset, but now we're starting to see the competition jump in.

There are a million (okay, slight exaggeration) ways to peel an egg, and countless numbers of tips, tricks, and hacks that are supposed to make that deviled egg appetizer you agreed to make for the party an absolute snap. More often than not, though, experiences vary... and pock-marked, greyish-yolked boiled eggs find their way into your collection whether you like it or not.

Coffee is a topic that everyone has a strong opinion about, especially when it comes to brewing the perfect cup. Even if you buy the best beans and grind them yourself, chances are you're skipping one necessary step to make sure your coffee tastes the best it can: cleaning your coffeemaker the right way.

Camping in the rain sucks. It's not enough to deal with your clothes and tent being soaked—it makes starting a fire nearly impossible if you're not carrying waterproof matches. You can buy them pretty much anywhere that sells camping gear, but if you've got regular matches and a candle at home, they're just as easy to make yourself..

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Shark jumps Steampunk, experts unsure of the meaning. Cape Town -- In an unprecedented move today, a Shark have jumped a steampunk couple as they were attempting to work on their hobby steamboat.

You may or may not care about this, but sometimes it physically upsets me when I see gears stuck together haphazardly, with no concern for whether their teeth interlock. I mean, what do you do with non-interlocking gears?
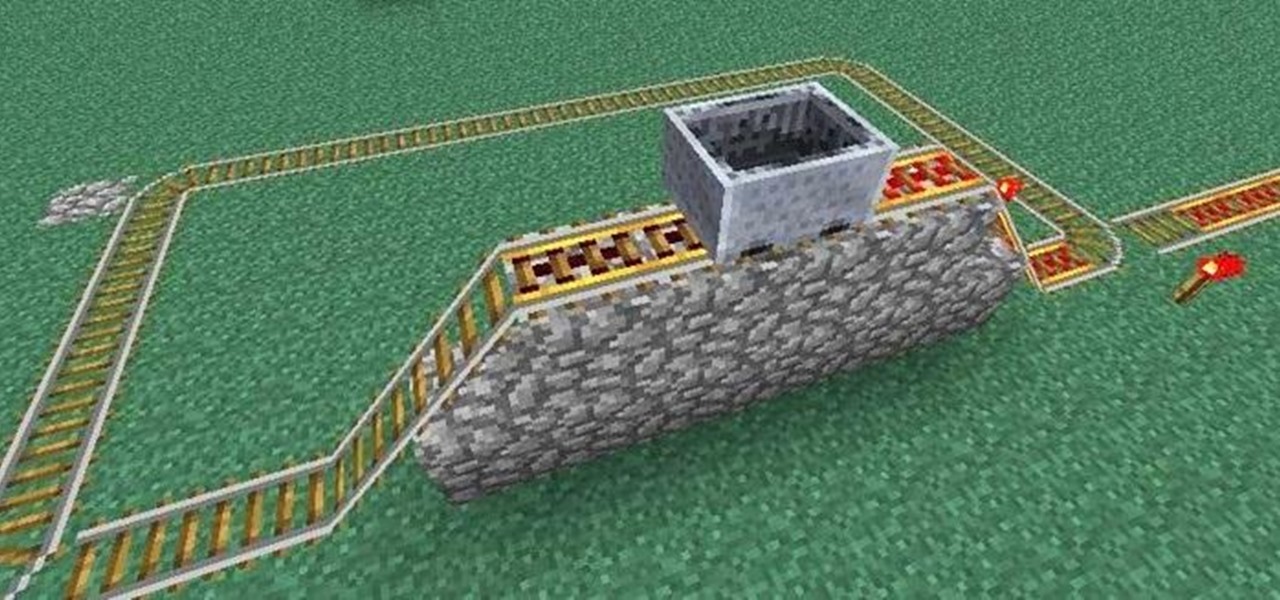
What's nice about Minecraft 1.3 is that it makes minecart stations so simple. Before, you needed redstone and buttons and powered rails in order to make a good minecart station. Now you hardly need anything at all! That said, if you want to be snazzy, all of the minecart stations we covered in this earlier article are still completely functional. You may also want to check out this article on how to make empty minecarts come back to you, if you want some extra bells and whistles.

Everybody should have plants in their home. Not only do they give off oxygen, but they add a whole new level of decor and awesomeness to an otherwise drab room. So naturally, if you want to improve a room, just display a few plants.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

Peter Fiduccia from Field and Stream explains how to use the tending grunt sequence when hunting deer. The tending grunt is a grunt made by a buck when following a doe. The grunt is made in order to let the doe know that he wants to breed. The key to making the call is to be soft. Bucks don't make this call with aggression or loudly. The first step is to take the call and cup your hand around the end. Blow gently into the call. For more resonance in the call, grab the call with both hands at ...

Digital artist Beeple's $69 million NFT art auction at Christie's has a second act called Wenew, and includes attempting to open the digital art floodgates to mainstream collectors and artists alike by using physical goods.

With NFTs taking the art world by storm, it's a bit refreshing to know that you can enjoy world famous masterpieces in the comfort of your own home via augmented reality without emptying your cryptocurrency wallet.

Snapchat may trail Facebook and Instagram in terms of daily active users, but a new partnership with Samsung may get those innovative AR Lenses onto the mobile devices of a lot more users.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

Now that we have our payload hosted on our VPS, as well as Metasploit installed, we can begin developing the webpage which will trick our "John Smith" target into opening our malicious file. Once he has, we can take over his computer.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.