The US driverless market has become a competitive – and crowded – arena, with big names like Google, Apple, Uber, and even Intel intent on leading the pack. Not to be outdone, the EU is also getting in on the automated car action with self-driving fleets launching in both the UK and the Netherlands within the next two years.

In Bhopal, India, a place nestled in between the royally pink city of Jaipur and the dry (i.e., alcohol forbidden) state of Gujarat, is a team of developers determined to make a fully driverless car suitable to the complexities of Indian traffic. An algorithm elaborate enough has yet to be made by any other company, but is the fundamental key to handling the intuitive habits of Indian drivers, the often intense and gridlocked traffic, and the country's vast expanse of jarring roads.

The internet's an amazing place. The entirety of human knowledge is now accessible in an instant, and all sorts of media can be streamed directly to the palm of your hand. But, of course, that also includes the darker side of humanity, so there's plenty of NSFW content floating around out there that's certainly not suitable for children.

If you're a tech geek who cares about the environment, you probably concerned with your personal carbon footprint. You may feel like your love for gadgets is slowly contributing to the degradation of our planet, but tech is your life. And in this scenario, small changes matter.

Are there any benefits to watching a movie in a holographic mixed reality headset, or should you just stick with your TV? It's not as cut and dried as you might think. While TVs have some advantages, so does the virtual screen of a Microsoft HoloLens.

To be twentysomething is an awkward time for entertaining. As we graduate college and begin to work in “the real world,” there is a yearning to transition from keg parties into dinner soirées. However, though the desire is there, often the bank account is not. Here are some ways to do in the kitchen what twentysomethings do best: fake it until you make it. (In other words, host a fabulous dinner party for four and still be able to make rent this month!)

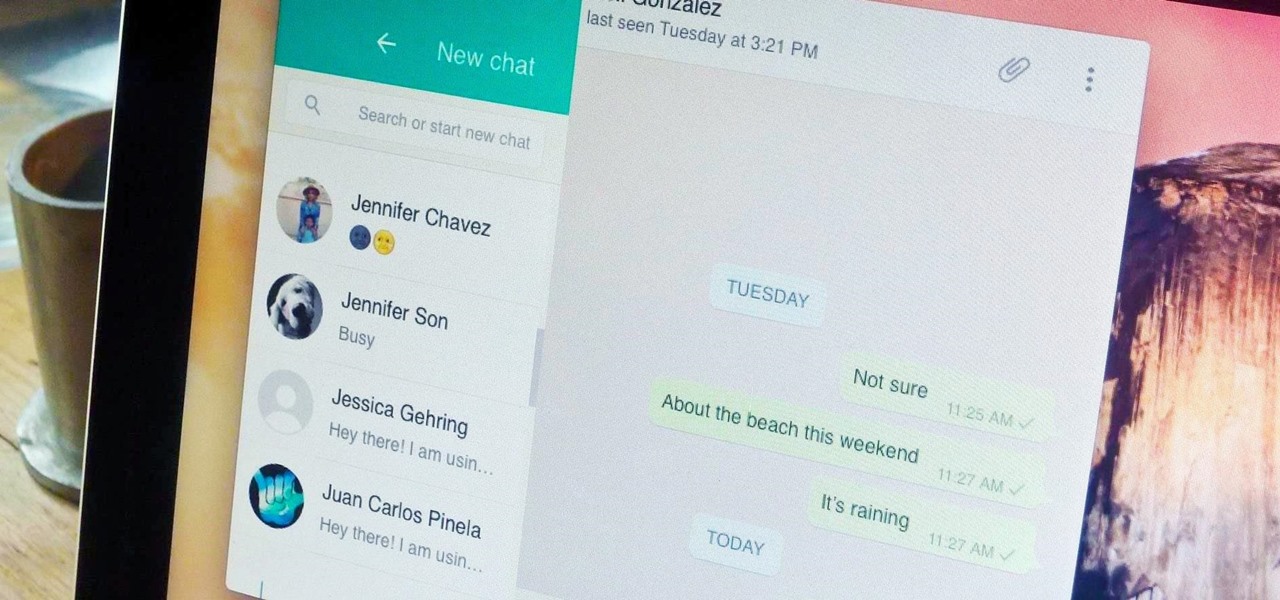
Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

Hello my fellow hackers, Welcome to my republished revision of the ruby programming language, Part 1.

"Cooking" with liquid nitrogen seems like one of those activities that should be strictly limited to pros who are appearing on Top Chef, but it's the only way you'd ever be able to make Dippin' Dots at home. If that isn't enough of a reason for you to get some LN2 for your kitchen, check out this dose of pretty:

It's really amazing how much you can do with root access on an Android device. From various themes to porting exclusive funtionality from other devices, the power of Superuser privileges is truly awesome.

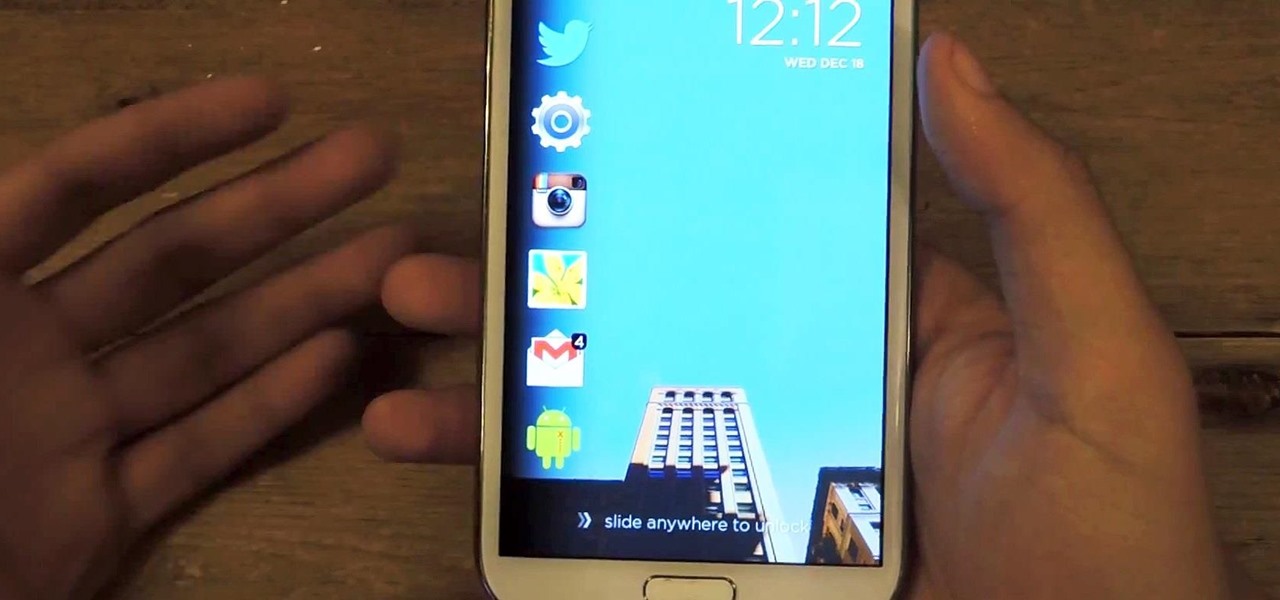
Not particularly good looking, TouchWiz's lock screen adequately supplements the clunky and almost cartoonish-look of the infamous user interface on the Samsung Galaxy Note 2. While there are hundreds of lock screen options in the Google Play Store, I've never quite discovered one that I've thoroughly enjoyed, due to the obfuscation from so many options.

There are loads of reasons for somebody to want to recover a Windows password, and there are lots of different ways of doing it. My favorite of all of these ways is to use a piece of software called Ophcrack because:

Update your nasty, ugly ceiling grid in your home or office. With this video tutorial, see how to restore rusty ceiling grid systems. Ceiling Armor Grid Cover will update rusty and discolored ceiling grid systems for a fraction of the cost of replacement. This unique cover snaps on to a standard grid system without any special preparation. This washable solid vinyl cover is suitable for standard ceiling grids in kitchens, restaurants, bakeries, pools, rest rooms and outdoor ceiling locations.

As an adult you will come a cross a point in time when you need to make the right impression by writing a formal letter. Follow the format and you will be able to be most effective at conveying the information in your letter.

Dying leather is a great option to revamp or change the look of an existing leather piece. Choose a dye that provides the qualities you are looking for, be it flexibility or depth of color. The possibilities are endless.

Super Mario Run has been one of the most insidiously addicting iOS games to come out in recent years for iPhone. And now, as of March 22, Android users can get in on the fun, too.

The frustration of searching for the perfect image can be overwhelming. Then there's the issue of copyrights: Can you use it? Do you have to give credit? Are you allowed to manipulate the image?

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Dark mode is everywhere. Both Android 10 and iOS 13 added the feature natively, and many of your favorite apps now include the option. So far, Google has been on a mission to add it to all of its apps, and Google Photos is no exception.

Finland-based Rovio, one of the pioneers of mobile gaming, is now ready to break new ground in augmented reality with its Angry Birds franchise.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

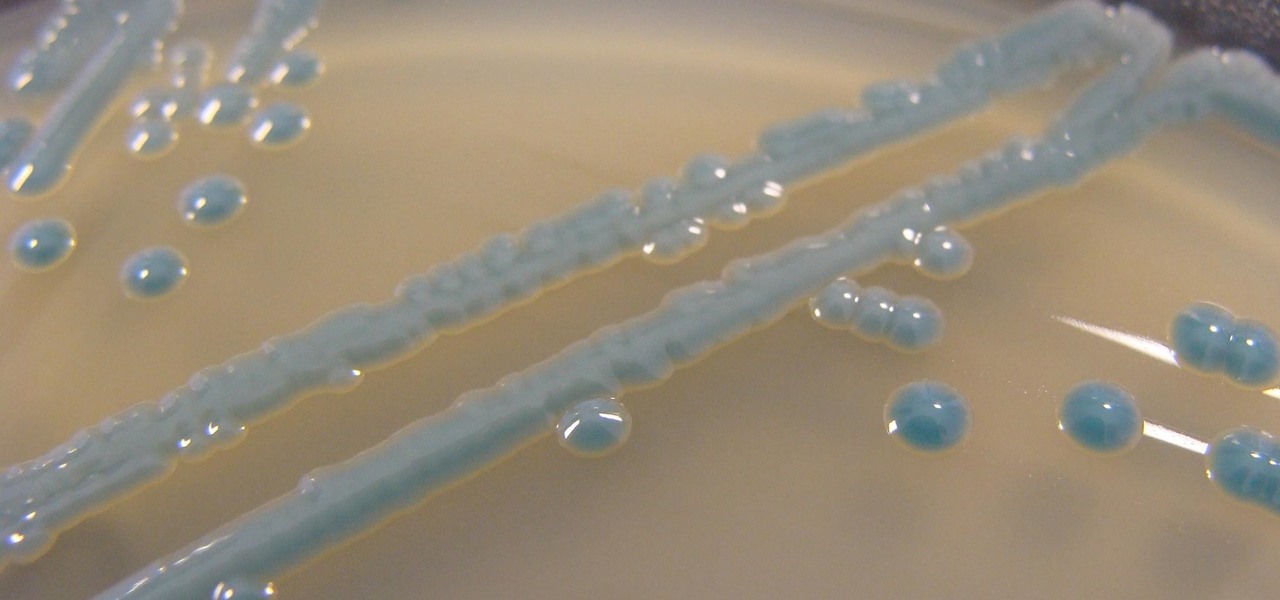
The growing list of dangerous antibiotic resistant organisms has just acquired three new members. Researchers have discovered three new species of Klebsiella bacteria, all of which can cause life-threatening infections and have genes that make them resistant to commonly used antibiotics.

The Great Barrier Reef in Australia is the largest living system on the planet. Yet more than 90% of the reef is bleaching because of the loss of a tiny algae that lives within the coral.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

This is an in-depth look at how to drive a Peugeot 308 ALLURE SW (2015, 2016, and 2017 European model) with an automatic gearbox and transmission.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

How to patch a hole in drywall / plasterboard / Sheetrock. Everyone at some stage in their life will need to patch a hole in drywall / plasterboard / sheetrock. Instead of doing some dodgy patchwork, watch this video to see how simple the job is. The steps are as follow in point form. This method is particularly suitable for holes that are larger than about 100mm or 4 inch's in size.

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

One of the greatest consoles ever to exist in the world of gaming is the PlayStation 3, which even lets you do a million different things unrelated to games. But no matter how big of PS3 fan you are, you have to admit that the internal browser is not the greatest. Far from it. While you can access most websites from the PS3, a lot of those site's functions are limited, including Facebook. After reaching over one billion users earlier this month, Facebook is undoubtedly one of the most popular...

There's only three weeks left until the spookiest holiday of the year, which means stores and costume shops everywhere are bringing out their Halloween inventory full force. So now's a good time to start prepping your Halloween costume—because you really don't want to do it last-minute again, do you?

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

You've decided you want to lose weight or build lean muscle. That's great! Now grab your smartphone. It's a valuable asset that can help you achieve your physical fitness goals, whether to improve your health or enhance your appearance, and I'm going to show you how.

A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it comes to helping you stay fit.

Choosing which programming language to learn next can be a truly daunting task. That's the case regardless of whether you're a Null Byter just beginning a career in development and cybersecurity or you're a seasoned ethical hacking and penetration tester with years of extensive coding experience under your belt. On that note, we recommend Python for anyone who hasn't mastered it yet.

The landscape of podcasting has exploded in recent years, with everyone from dedicated longtime podcasters reaching the mainstream spotlight, to traditional media personalities moving from TV, radio, and newspapers to grab a slice of the listening pie. The good news is that the barrier to entry is relatively low, so even if you're not a celebrity or media luminary, you can still get your voice out there by starting a podcast.

With all the talk about privacy concerns recently, Google's name keeps coming up because they are a very data-driven company. As an Android user, they know basically everything about you based on your device usage. That can easily scare some people off who are worried about their privacy and security. You do have some say in what personal data Google controls, but what if you want total control?

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

UAC is something we've all dealt with on Windows, either as a user, administrator, or attacker. It's a core feature of the Windows security model, and for the most part, it does what it's supposed to. But it can be frustrating as a hacker when attempting privilege escalation, but it's easy enough to bypass UAC and obtain System access with Metasploit.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.