
Hack Like a Pro: Metasploit for the Aspiring Hacker, Part 7 (Autopwn)
Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.


Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

We are living in a golden age of craft beers. Originally invented by the ancient Egyptians, every culture now has its own tastes regarding beer. The process of making beer is so multi-faceted, it's a miracle that any gets made at all.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.
Because of Android's massive array of supported smartphones that carry vastly different display sizes and resolutions, the operating system uses a value known as DPI to determine the size of icons and visual assets that will best suit a given screen.

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

If you're anything like me, every time you travel you end up in a desperate panic for a decent W-Fi connection. Whether you want to post your photos, research the best beaches, or kill time during an overnight layover, a hotel's Wi-Fi quality is of paramount significance in making a reservation.
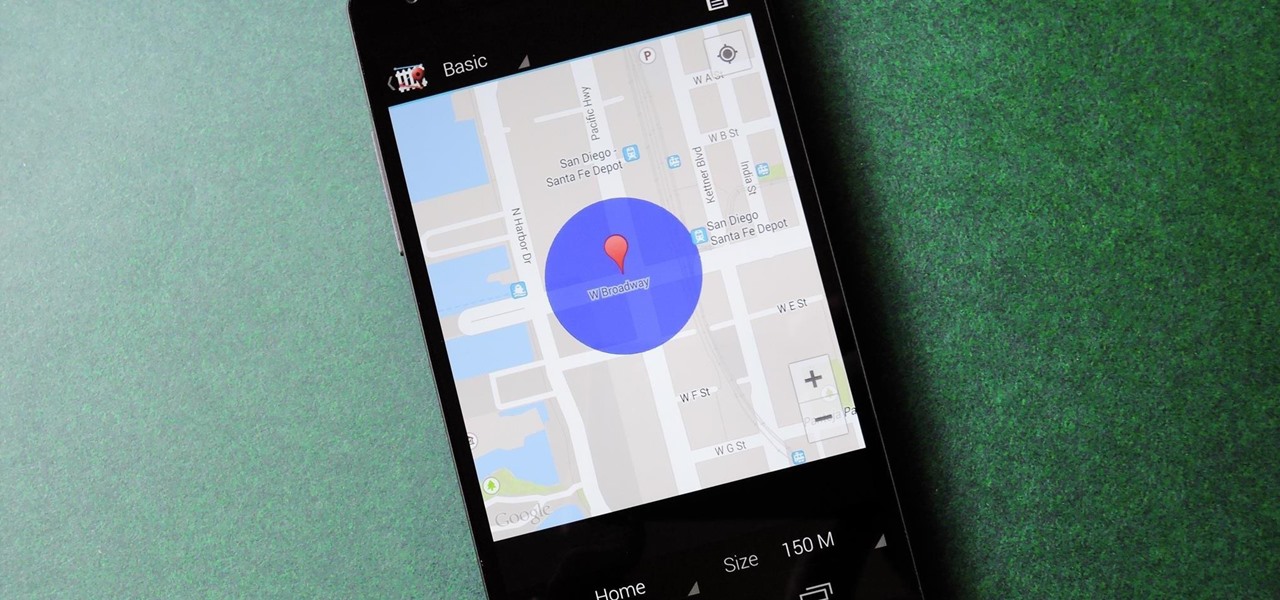
We live, work, and play in drastically different environments, so it only makes sense that we'd want our Nexus 5 smartphones to automatically adapt to our needs when in certain locales at certain times.

You know you've had a long day when you head home with a headache, back pain, and eyes so sore they feel like they might roll out of your head. Turns out your medicine cabinet isn't the only place you can find help—instead of popping painkillers, just open up your wallet for instant pain relief.

Look away from this screen and try to remember the sound of your childhood hero's voice. Did you do it? Do it again, and this time pay attention to your eyes.

Now that Hangouts is Android's default messaging app, it's given us a lot of cool new features. A bouncing ellipsis lets you see when the other party is typing, and an indicator shows you whether they've read your message or not. You can even answer the age-old question of "Where you at?" with a tap of a button, sending a map of your location.

The Samsung Galaxy S5 was just officially announced at Mobile World Congress. The new flagship device will be available worldwide beginning April 11, 2014, including all major U.S. and international carriers. With over 200 million Galaxy devices sold to date, the S5 doesn't stray too far from the trend, at least not aesthetically. We've still got a high-grade plastic shell with perforated back covers, and four color choices at launch. Our highlights of the release event are as follows.

When it comes to the user interface, you're pretty much limited to the stock one that comes on your Samsung Galaxy Gear smartwatch—a carousel of large black and white icons representing the features and applications on the watch.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

Welcome, my neophyte hackers!

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

I'm sure that there are plenty of people out there who have no idea what a plague doctor is/was, so I'll start with an explanation.

Our attention spans have vastly shortened thanks to the Internet and our subsequent procurement of information from it at a rapid pace. It's tough to pay attention to something for a good amount of time, unless it's ridiculously interesting and stimulating. It's gotten so bad for me that I keep checking my phone every ten minutes—I even did it during a midnight showing of The Dark Knight Rises.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

Here at WonderHowTo, we've been following the Minecraft LEGO set for quite some time, through its development on LEGO CUUSOO (a LEGO site where users can submit ideas for LEGO sets) to its eventual implementation.

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

If you don't work in construction or are a woodworking master, you probably aren't entirely sure what all those marks are on a tape measure. Sure, you likely know the basics, like there are 12 inches to a foot, but what are all those little tick marks for? Don't let all those little lines dissuade you from using a tape measure. Follow these guidelines to help you read all those little ruler marks.

When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers.

Aircraft equipped with ADS-B are constantly shouting their location into the radio void, along with other useful unauthenticated and unencrypted data. In this guide, we will make an ADS-B receiver using a Raspberry Pi with a software-defined radio (SDR) dongle, which we can use to track aircraft anywhere in real time.

Tired of drawing delicate flowers and ready for something a little darker? You can draw a wicked skull by following the method and including all the qualities you should include to really get your sketch to look like a skull.

With its latest version of Apple Maps, Apple has made perhaps its strongest push since the launch of the app to dethrone Google Maps from its perch atop the App Store rankings.

Apple's Tapback is a great way to react to iMessages you find funny, surprising, confusing, and anything in between. However, in group chats, keeping track of who reacted with which Tapback can be difficult; iOS often just shows you how many people reacted but excludes many of the names. Luckily, there is a way around this — it's just a bit hidden.

As businesses flocked to Zoom, Microsoft Teams, Google Meet, and other video conferencing platforms to bridge the gap, we wondered aloud -- why aren't more companies leaning even more heavily on augmented reality?

There are at least 24,000 different Android devices, and they all have varying hardware components. This is why many developers publish several unique variants of their apps, which, among other things, helps accommodate all of the different display sizes and resolutions on Android phones and tablets.

The Galaxy Note 20's speakers are so loud and capable that they almost never need to be set to 100%. But by the same sense, it can be hard to find that just-right volume level since one increment represents a bigger change in sound output. Believe it or not, there's actually a first-party tool to fix this problem.
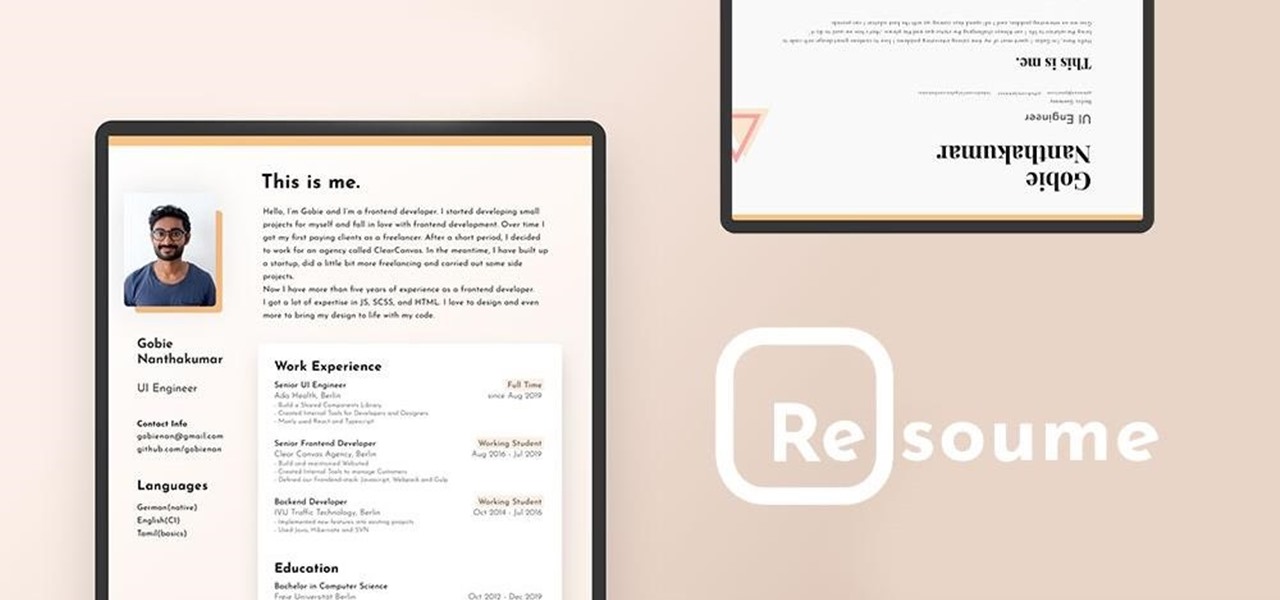
While the job market is slowly rebounding, competition remains fierce. Don't get caught behind when a new opportunity presents itself. Preparation is key to landing your new big job.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

Up until Android 5.0 Lollipop, the actual text of incoming notifications would scroll by in your status bar. These ticker style alerts didn't pop on screen or interfere with what you were currently working on, but you could still read the message. They were replaced by the new "heads up" alerts, but you can still bring them back.
There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

The words of three of tech's most important executives in the last 48 hours are providing some valuable insight into the near term future of augmented reality and the cloud infrastructures that support it.

For years, Apple's Notes app has been a reliable way to jot down important ideas, tasks, plans, and more. While there are apps on the market that advertise themselves as being more feature-filled than the stock iOS option, Apple is now giving them a run for their money. Here are 14 new features and changes you'll see with Notes in iOS 13.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.