Are you a mom or a dad that has run into a road block with your kids? Are they out of control disobedient? Follow this advice on how to raise well-behaved children and raising your children will be much more rewarding.

Keeping the filter clean improves your dryer’s performance and avoids the risk of fire from lint buildup. By leaving your lint filter full, you run the risk of also breaking your dryer, leading to an expensive repair or an expensive new dryer.

Have some spare time and looking to pick up a new skill? Learn how to paint with watercolors in this tutorial. Watercolor painting is a great medium for all skill levels.
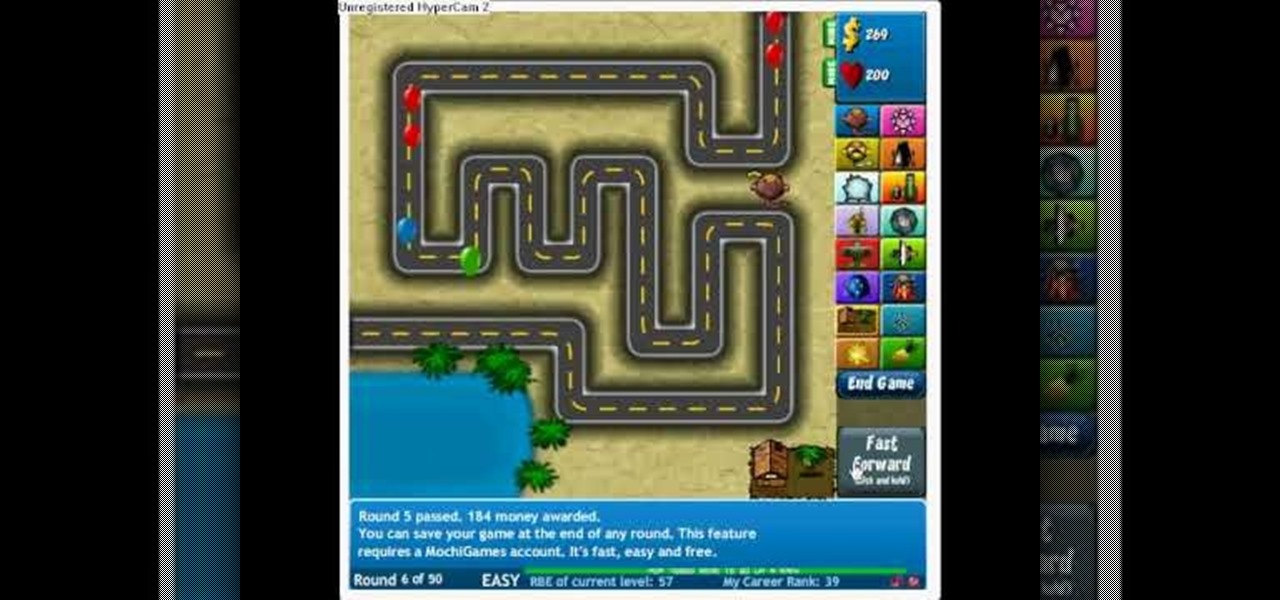
Bloons Tower Defense 4 cheats are here. And you guessed it… this one uses Cheat Engine. If you want to hack the game, you have to know how to do it, and Cheat Engine can be kind of a complicated process if you've never used before.

If you or anyone in your family suffers from allergies, there are some simple ways to make your home more hospitable.

If your blood pressure is 140/90 or higher, you need to get it down! The good news is that many of the steps you can take are painless, and some are downright enjoyable.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to edit Super Mario World levels with Lunar Magic.

Watch this video tutorial to learn how to make your own all-natural face masks. Tired of spending a lot of money on facial products that don’t even work? Try on some masks made from items you already own—they’re all natural and good enough to eat!

Many ways to help the environment are costly, but using less electricity is one measure that will save you money. Learn how to lower your electric bill with this how to video.

Brian Brushwood and Scam School give you another way to score free booze at the bar. Memorize a few configs and you'll hold the key to another unbeatable game and loads of free drinks!

Don’t laugh—butter sculpture is a true art form that originated in Tibet in the 7th century. It is now one of the highlights of many American harvest fairs. Learn how to make your own butter sculpture.

Wearing vintage clothing is one of the best ways to reduce the environmental impact of your fashion choices—short of walking around naked.

There’s an art to packing boxes without breaking your good china—or breaking your back. You Will Need

Grab your acoustic guitar, strap, and your pick and check out this free guitar lesson. This video tutorial will teach you country rock guitarists how to play a Luke Bryan song. Not just any Luke Bryan song, but one of his greatest: "Country Man." And just so you know, here are the lyrics to go along with this instructional guitar lesson:

Want to mix and scratch like a professional DJ? To be a good DJ you need to understand the concepts of mixing tracks, adding cool effects, and of course you need a good sense of rhythm to line up the beats. This how to video sequence explains how to cut and chop on a DJ mixer. There are loads of ways of describing this technique: editing the track, washing up, mowing the lawn, or drying your hair.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Use knot tying skills to anchor loads, in rescue situations, and for lashing. Learn how to tie knots and what they're used for in this free outdoor skills video series from an Eagle Scout.

Learn how to do alternating T push ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

Squats are probably the most useful exercise you can do at the gym—no other single exercise encourages more muscle growth. With a range of motion that incorporates many different muscle groups in the legs, core and upper body, squats not only strengthen those muscles, but also strengthen the tendons and ligaments that connect them. In addition to their strength-building benefits, squats also teach you core stabilization, which is important for almost any athletic endeavor. Learn how to do dum...

This is a refreshing spring update on your classic hamburger slider. Instead of using a ground beef patty, I am using shrimp tempura. This recipe calls for fresh truffles, but fresh truffles are hard to come by so feel free to use truffle oil (it is much more affordable and what I usually like to use). The flavor will be just as good.

Data analytics is crucial to the operations of any modern business these days. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics.

What could Apple be planning here? Are we going to see some revolutionary new features for the iPhone? Will we see mostly bug fixes and security patches? It's time to find out, as Apple just released the first developer beta for iOS 13.4.

So you've managed to get a shell on the target, but you only have measly low-level privileges. Now what? Privilege escalation is a vast field and can be one of the most rewarding yet frustrating phases of an attack. We could go the manual route, but like always, Metasploit makes it easy to perform local privilege escalation and get root with its exploit suggester module.

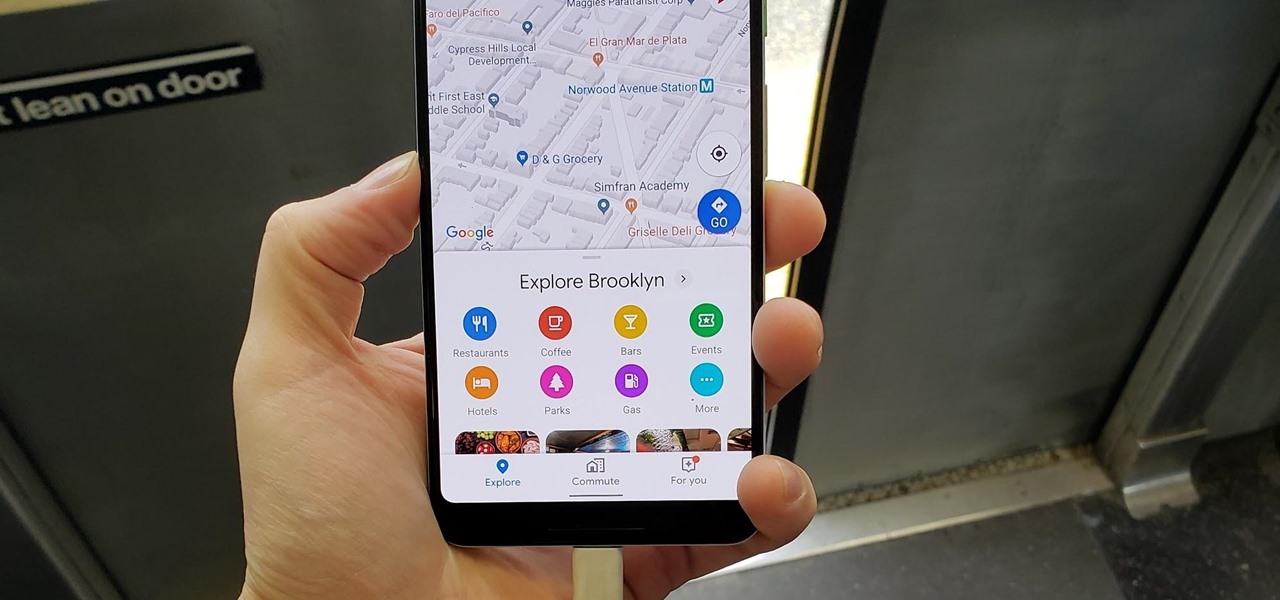
Google's "Go" line of apps are lightweight counterparts designed to be limited speedy alternatives to their full-featured sibling apps. There is a Go version of Photos, Search, Maps, and more — but are they the right apps for you?

Filmic Pro has a superb suite of professional settings — bit rate, frame rate, and mic choice, to name a few — which can enable you to capture the best footage possible. But different shots require different setups, and it can be frustrating to change settings on the fly. Filmic Pro lets you skip that whole process by saving your favorite settings as presets for quick and easy access.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

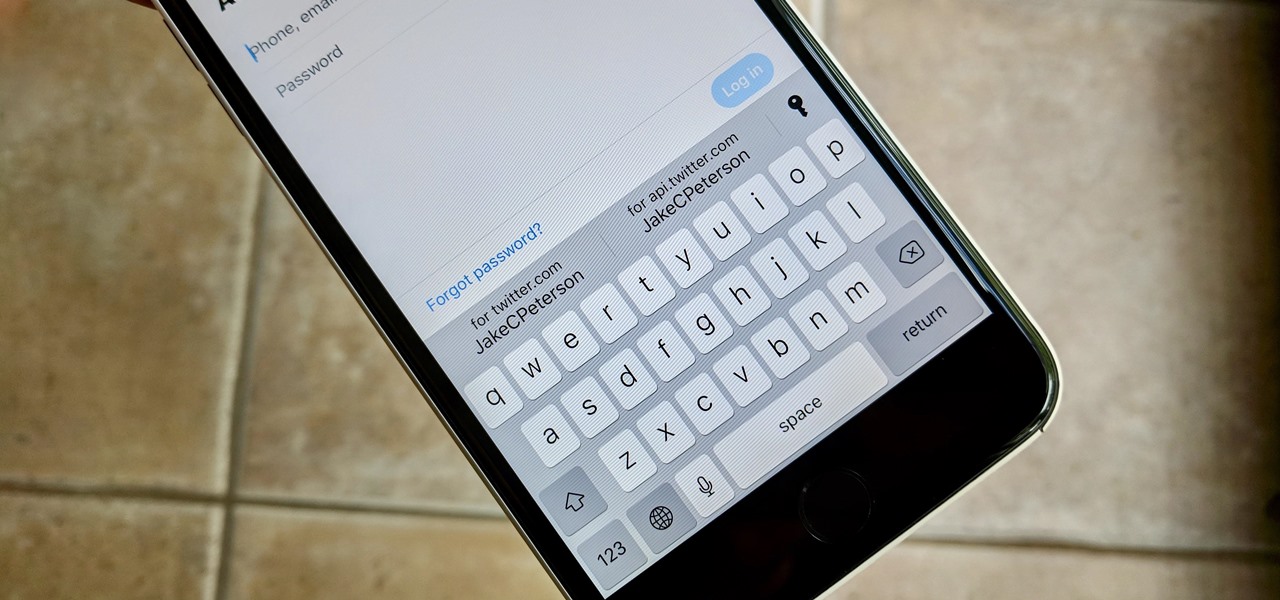
Apple's dedication to iPhone security is one of the company's biggest selling points. It's no surprise then that iOS 12 offers users a simple yet powerful way to make, save, and auto-fill strong passwords to your iCloud Keychain when creating accounts in both Safari and in apps. The best part? You hardly need to do a thing.

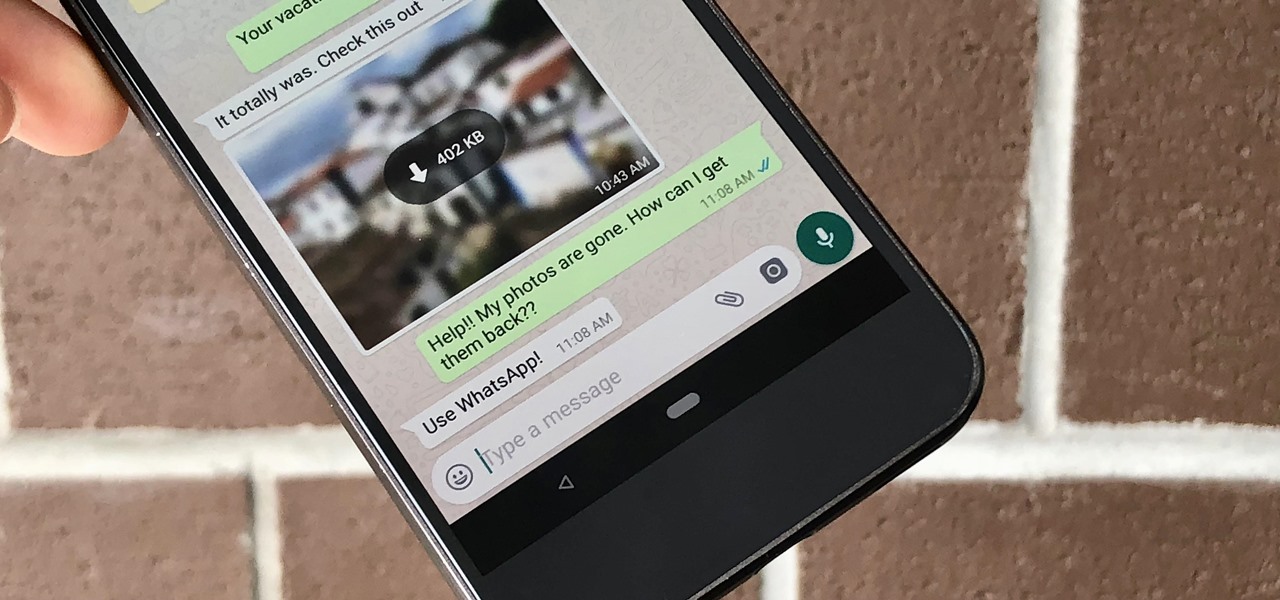
Thanks to cloud storage's increasing accessibility, permanently losing photos is becoming less and less common. Still, if you accidentally delete a picture from your smartphone without first making a backup of some sort, that data is pretty much toast — unless we're talking about photos from WhatsApp.

While numerous startups are competing to convert the AR Cloud from a pie-in-the-sky to a reality, Wikitude is thinking smaller with the latest edition of its augmented reality SDK.

Business cards are a great way to keep tabs on the contacts we network with. So why shouldn't our smartphones make them even more useful? Enter Google Lens, which will help you save, search, and expand on the contact information found on all of the business cards you've collected.

Outside of early military applications, augmented reality is a relatively new technology. It stands to reason that the next company to make a splash in AR would be a startup, and Techstars wants to help.

A new study shows the Zika virus is present in saliva — but it may not be enough to make you sick. The Centers for Disease Control and Prevention notes there is "no evidence that Zika can be transmitted through saliva during deep kissing." Given the results of research published in the journal, Nature Communications," the agency may need to revise its guidance.

The internet's an amazing place. The entirety of human knowledge is now accessible in an instant, and all sorts of media can be streamed directly to the palm of your hand. But, of course, that also includes the darker side of humanity, so there's plenty of NSFW content floating around out there that's certainly not suitable for children.

The YouTube app for Android doesn't exactly offer the greatest user experience. For one thing, it opens to an arbitrary "Home" tab instead of your subscriptions, so you see a list of what YouTube thinks you want to watch instead of your favorite channels. In addition to that, videos are loading at a mere 144p playback resolution for many users lately, which is downright terrible quality.

If you could save the world by eating a burger, would you? Two companies, Beyond Meat and Impossible Foods, are on a mission to redefine veggie burgers and eliminate all of the downsides of animal farming on our planet. With over five years of research and product testing, they've finally figured out how to make a plant-based burger look, feel, and taste just like real meat.

Most people I've talked to agree that Shake Shack has mastered the upscale, fast food hamburger quite well. So when a new burger comes out on the ultra-popular fast food chain's menu, you've got to take notice—even if you live nowhere near one.