In this Autos, Motorcycles & Planes video tutorial you will learn how to drift in your car easily. In this video Bryan Norris tells you about basic drift techniques and counter steering. While at high speed when you turn a corner, the car will start to spin. What you do now is to counter steer. That is you turn the steering wheel in the opposite direction. As you come down the hill, step on the brakes. What this does is it transfers the weight of the vehicle from the rear of the car to the fr...

In order to set up your email in Outlook Express IMAP, you will need open Outlook. In accounts, enter your user name in the box above: "for example John Smith". Switch the incoming mail server to IMAP. Fill in your server and outgoing mail SMTP.

Access your computer's BIOS settings

In this video the instructor shows how to create and mount ISO's using Ultra ISO. You can user daemon tools to work with ISOs but this video shows you an alternative to it. Download the Ultra ISO software and install it. After installing it run the program. In the tool bar select the Tools button and in the drop down box you can select the various option like create a new image, mount an image to a drive or convert images between formats. Select the mount option and it prompts for the file. B...
This is a video teaching how to use the Wiiflow USB loader with an external hard drive. This will allow you to store Nintendo Wii games in an external Desktop hard drive. The narrator shows you his consoles and his hard drives while loading the cover on his Wiiflow. The Wiiflow will let you store all of your Wii games onto a large hard drive, instead of your Nintendo Wii. It allows you to play the games from the USB loader without a game disc. This is a convenient way to play your games witho...

In this video the instructor shows how to install a program or a game which is in ISO format. The first thing you will need is the ISO file that contains the game or program. Next you will need a program that can open the ISO file. Use the daemon tools for this purpose. Right click on the daemon tools icon in the notification area. From the menu choose the mount image option and point to the virtual disk. Now browser and select the ISO file that you want to open. This mounts the image to the ...

We can't actually lighten you load but we can make it seem that way. This simple trick of stacking your heavy box on top of an empty box will make it feel lighter. Moving a heavy box is a unpleasant so try this fun trick.

Here are a few handy tips to help you care for your Powder Vibe for Glass Enamel Powders and how to load it safely. The Powder Vibe tool is a motorized device for the dispensing of glass enamel powders. This tool helps with health and safety by reducing dust and the need for enamel powder sifting when lampworking glass jewelry. The powder vibe tool keeps your enamel powders clean and gives you great control. Use the tool to add smooth streams of glass powder and enamel powder onto your lampwo...

In this series of videos you'll learn how to connect and use a 2D scanner. Electronics & media expert Tony Ramirez shows you step by step how to load the drivers and software onto your computer, how to adjust the scanning settings, and how to save and print an image you've scanned.

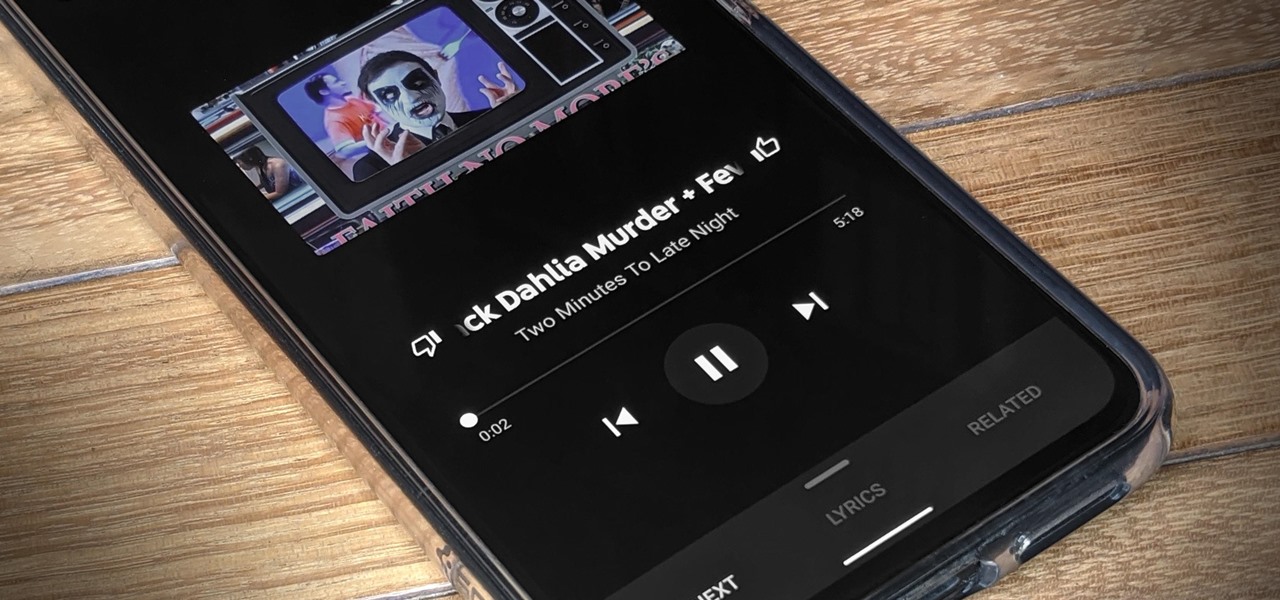
If you enjoy watching music videos, live concert recordings, or bedroom cover songs on YouTube, then YouTube Music is worth your consideration. In fact, YouTube will show a "Switch to YouTube Music" button on some music videos that opens the song in the YouTube Music app — but not always.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

Every year, Apple releases a new version of iOS. Each iteration promises new features to make using your iPhone that much better. This year, iOS 13 introduces over 200 new features and changes, including system-wide Dark Mode for the first time on iPhone. That said, you might want to pump the brakes before dashing to download and install the new update right away.

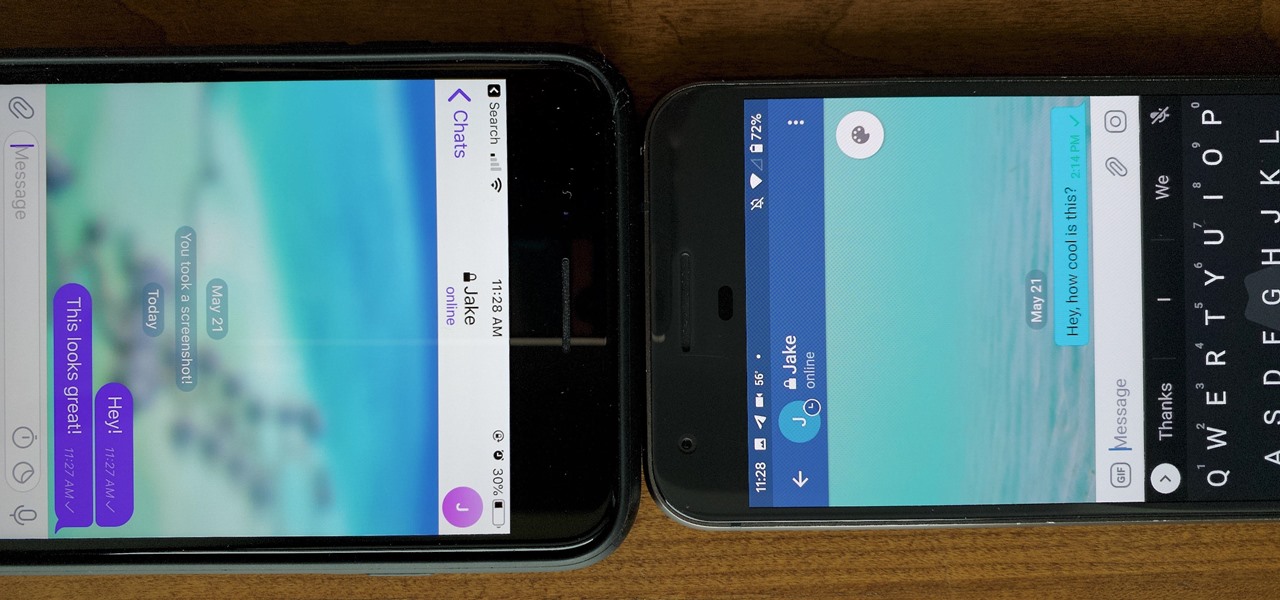
One of the more competitive aspects to chat apps these days is customizability. It seems every messenger wants to offer the largest number of options for users to make the app feel like a truly personal experience. Telegram is no stranger to this customizability, offering tools where you can select backgrounds and chat bubble colors.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

In five short years, three generations of ultra-low-cost Raspberry Pi devices have challenged the boundaries of what a person can do with a $35 computer — especially with Kali Linux.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

If playing Metal Gear Solid didn't make you want to crawl on the floor of your living room throwing imaginary flash grenades, then I don't think we could be friends. Solid Snake was the man. Period.

Atari was one of the very first video game consoles, bringing the joy of arcades right into the living room. Now gaming consoles are a dime a dozen, but there's still something about those old retro systems that makes me want to travel back in time.

The first film I saw without any parental supervision was Pokémon: The First Movie. At the time, there wasn't a 5th grader around who didn't know who Pikachu was or what Pokémon was all about. The franchise was one of the most popular video games of all time, right after Mario.

Nothing can beat a portable system designed specifically for gaming. There are tons of emulators available on Google Play, but most have awkward controls, large game files, resolution issues, and hardware compatibility problems. The list could go on...

This 3D software modeling tutorial series shows you step by step how to create a suitable model for Google Earth within SketchUp. The series will start by showing you how to export data from Google Earth to use for reference, how to build and optimize the modle, texture it in Photoshop or Picasa and export and load it to Google Earth.

This video shows you how to control your computer from your iPod touch. 1. Go to UVNC. Click on Installation. This will take you to download options. Download the latest stable version. 2. Install Hamachi, which helps you find your computer's IP address. Click on Download Here link, fill in the registration information, and click submit. 3. Install a VNC listener on your iPod so it can connect to your desktop. Jailbreak your iPod, and open the installer. Click All Programs; scroll down until ...

If you’re having trouble getting games on your memory stick, this video will walk you through the steps of just what you will need to do to compress files onto a thumb drive. There are a variety of steps you will have to follow and you’ll have to have a little bit of time to wait for your game to compress but the effort is well worth it.

Try adding some weighted bar exercises to your workout routine to not only strengthen you arms but to increase your core and back strength as well. Use heavier weights to build larger muscles and more reps at a lighter weight for lean strong muscle.

Learn how to use the S-31 Lego gun from this video tutorial. This video shows how to make the Lego brick bullets, grease the S-31 Lego gun, load the toy weapon as well as how to fire it.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

Apple just released iOS 13.5 for public beta testers today, Monday, May 18. The GM (golden master) for iOS 13.5 arrives just three hours after Apple released it to iPhone developers, and 12 days after the release of iOS 13.5 dev beta 4.

Apple just released iOS 13.5 for iPhone developers today, Monday, May 18. This GM (golden master) update comes 12 days after the release of iOS 13.5 dev beta 4, which introduced updated COVID-19 exposure notification logging settings and the ability to share your Medical ID with first responders when placing an emergency call.

As government officials scramble to contain the new coronavirus outbreak with bans on large gatherings, travel restrictions, and school closures, the rest of us have to worry about how we're going to safely purchase water, toilet paper, groceries, and other household goods during the global COVID-19 pandemic.

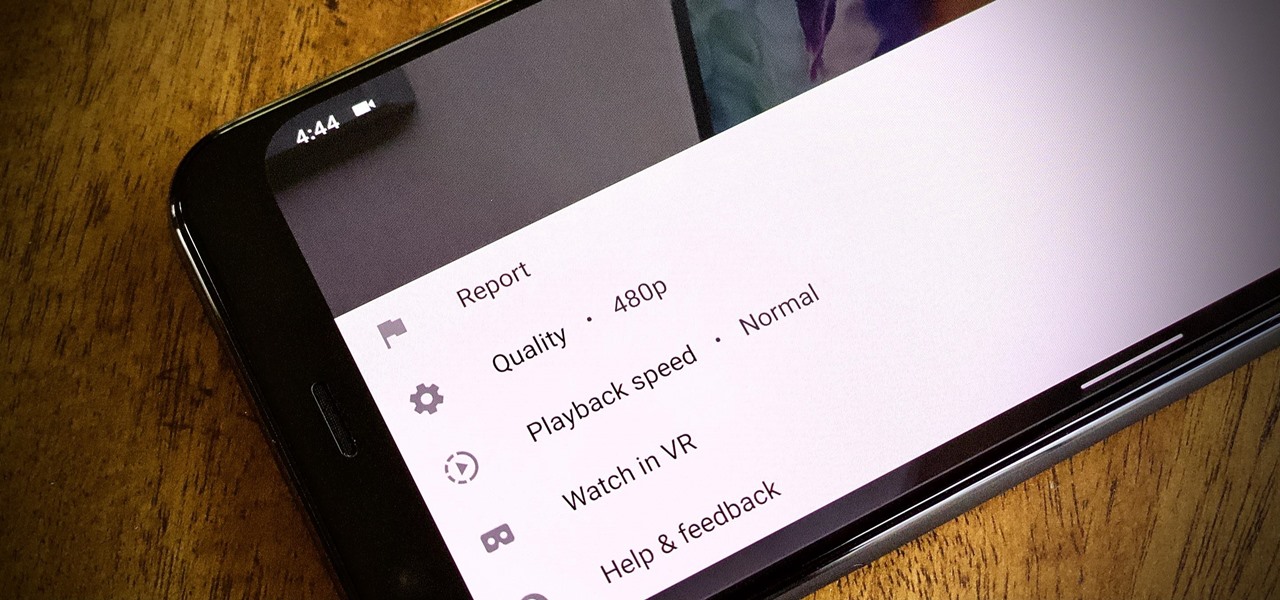
To reduce stress on internet bandwidth during the COVID-19 pandemic that the novel coronavirus is causing, Google decided to set YouTube's default video quality to 480p. That said, even when you could stream at HD quality without adjusting anything, you still couldn't switch the default to whatever you liked. We have a few methods on hand to help you change that.

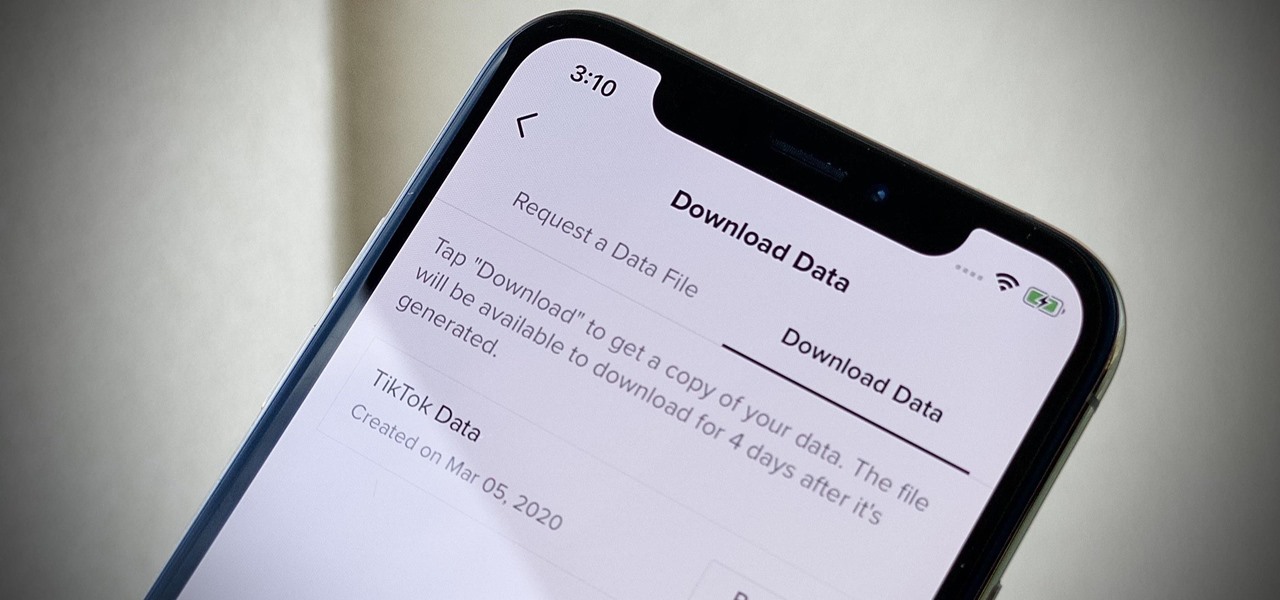
If you're concerned about your privacy, TikTok might not be the app for you. Its shady practices with user data have been the subject of concern, criticism, and even legal action by the US government. Then again, it's just so addicting. If, like me, you're not going to stop using TikTok anytime soon, you should at least know how to view the personal data it has collected on you.

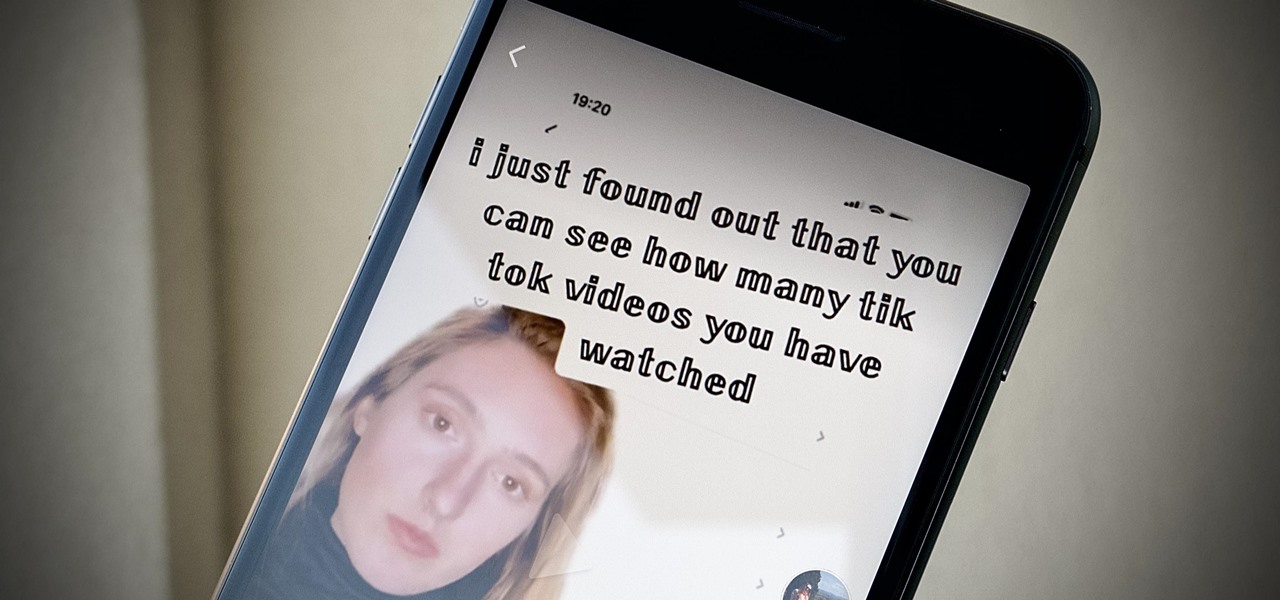
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?