Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.
Welcome back Hackers\Newbies!

Apple designed Find My Friends in 2012 as a means for better-connecting with friends and family. It's pretty useful for scenarios when you need to keep tabs at an amusement park or to get a live ETA when your buddy is coming to pick you up from the airport. You can even share your location with others so they can track your whereabouts as you go about your day.

First of all, I would like you all to meet my good friend Iggy. There he is, in all his scaly reptilian glory. As you can see, he spends a lot more time on top of his cage than inside of it. You see, Iggy here doesn't deal well AT ALL with confinement. I don't know if it's possible for a lizard to be claustrophobic, but if it is possible, then Iggy definitely is. When his previous owner gave him to me, I tried to keep him in the cage, but I quickly realized that it was a bad idea. When confin...

Will the predicted apocalyptic date — December 21st, 2012 — really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyberwars, earthquakes, or aliens actually destroyed our planet — and how you might survive.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. This past Saturday we had a great turn out for the Weekly Workshop, and we even managed to get a few of you in TeamSpeak. Thanks to all who joined in, hope you learned some awesome new things!

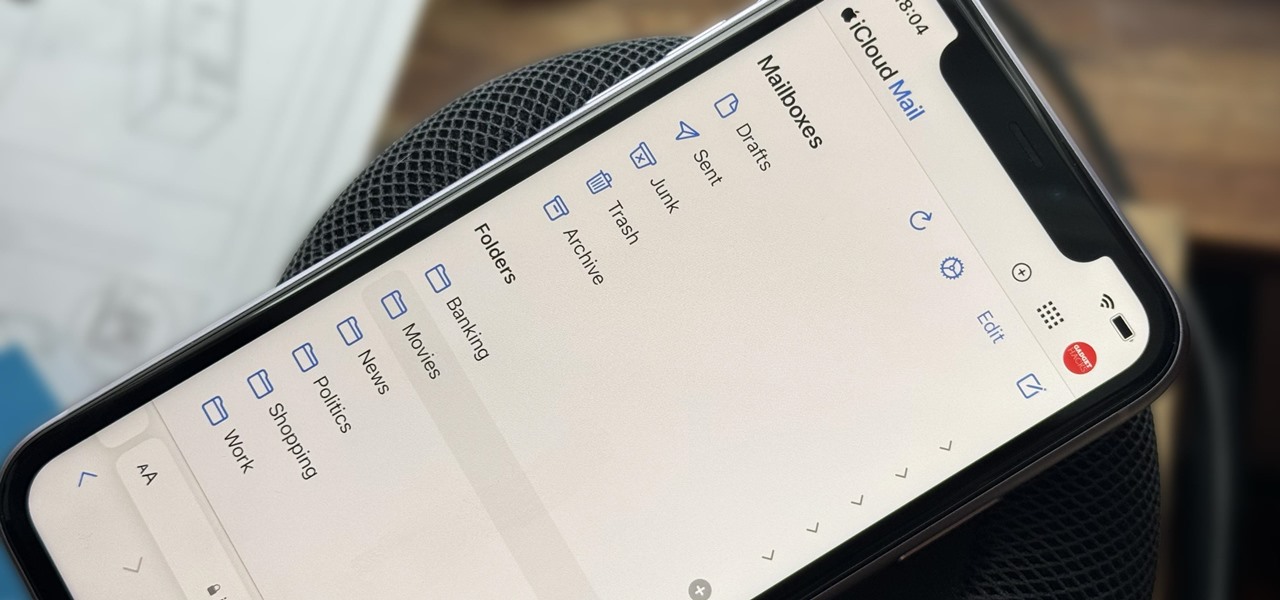
Apple includes a lot of helpful features for iCloud email addresses, but one of its best-kept secrets will give you total control over organizing your inbox like a pro.

There's a feature that every Apple Watch owner should know about — one that makes navigating menus, tapping tiny icons, and interacting with complications, among other things, much easier on the small display.

You're probably sharing a ton of information on your iPhone with other people, apps, and services without really realizing it. Now there's a new tool to show you just how much, and it can be an eye-opener as well as a fast way to manage sharing permissions and review your account security.

Your iPad has a superpower that iPhone models don't and probably never will have (even though they could) — one that will make you want to take your iPad with you everywhere you go from now on.

There are many things Apple doesn't tell you about its products, and that's definitely the case when it comes to its Messages app. Hidden features lurk in your SMS and iMessage conversations just waiting to be found, and we've unearthed some of the most secret ones.

If you haven't been using Spotlight Search on your iPhone, we've got ten reasons for you to start. Apple's made some significant improvements to the search interface available on the Home Screen and Lock Screen, and it's more useful than ever.

Without realizing it, you may be giving away the GPS coordinates of your home, workplace, school, and other important or secret locations. Unless you've blocked the feature on your iPhone, location data is stored in almost every photo and video you take, and anyone you share the content with can find out where you are or were. But there are a few things you can do to safeguard the information.

In these times of social distancing, video calling is becoming the technological substitute for face-to-face connections. For those who carry an iPhone, the art of video calling defaults to FaceTime, the native app on iOS that is exclusive to Apple devices. But what do you do if you or the other party is on Android?

Since iOS 13, your iPhone's come equipped with a fonts manager that lets you install custom fonts for use in Apple apps and supported third-party apps. To add fonts, you need to use a font provider app that'll load them on your device and register them system-wide, and one of these apps shines above all else.

Spotify has caught up to Apple in monthly podcast listenership and is even forecast to surpass Apple soon, but Apple just made some serious changes to its Podcasts app for iOS and iPadOS that could keep Apple at the top.

Apple's stock keyboard for iPhone has gone through many changes over the years. Some have been significant, and others more subtle. Overall, most of these updates have been fairly obvious, so you're probably already using them — but there are more than a few interesting features that were slipped in under the radar that you may not know about.

If you have Snap Spectacles 3, the dual camera-equipped sunglasses capable of capturing 3D photos and video, by now you've likely jazzed up the videos you've captured on the wearable with Lenses via Snapchat.

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

The iPhone has a setting that will obfuscate the content of notifications on its lock screen until you're recognized by Face ID. Google implemented this same feature in its Pixel phones, but many Android devices have no such option. At least, not by default.

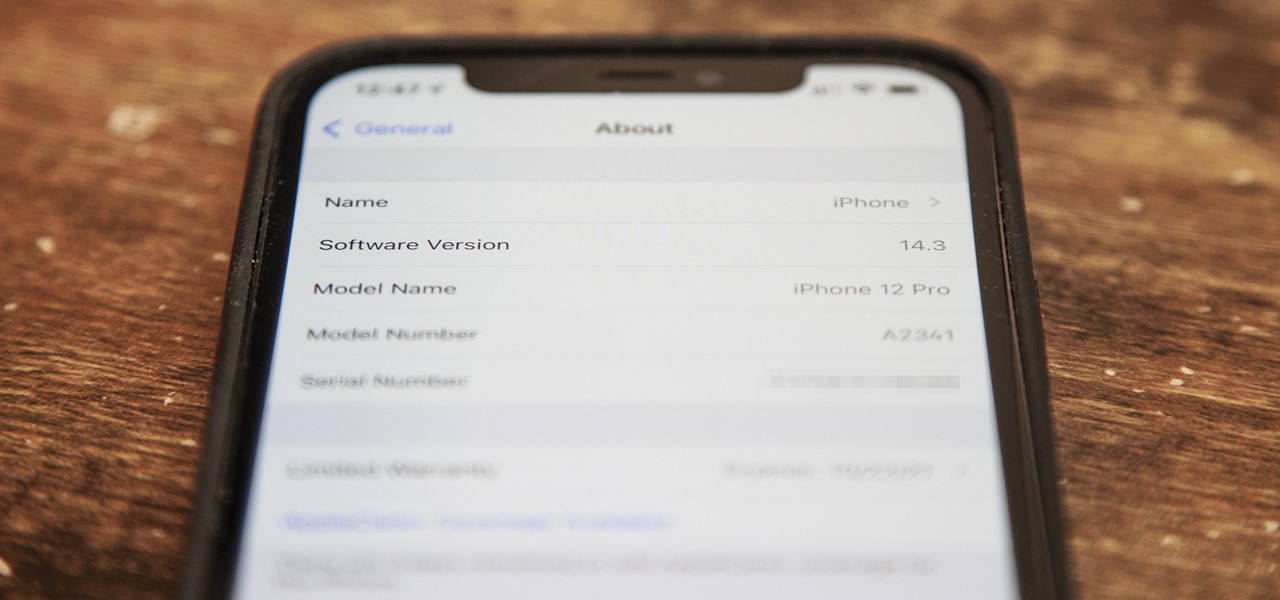
Just as expected, Apple pushed out iOS 14.3 to the masses on Monday, Dec. 14, which coincided with the pumped-up release of Fitness+, Apple's subscription workout service for Apple Watch users. It also came one day before the new AirPods Max hit buyers, and the iPhone needs iOS 14.3 to use all of its features.

VPNs add a protective layer between your data and your internet service provider (ISP) or bad actors (hackers), so it makes sense they've become so popular lately. Probably the most common one of these is NordVPN, so we explored its mobile app to find all the options worth checking out.

It's a common misconception that iPhones are impervious to cyberattacks and "more secure" than Android. And when an iPhone does get hacked, it's nearly impossible to tell that it happened.

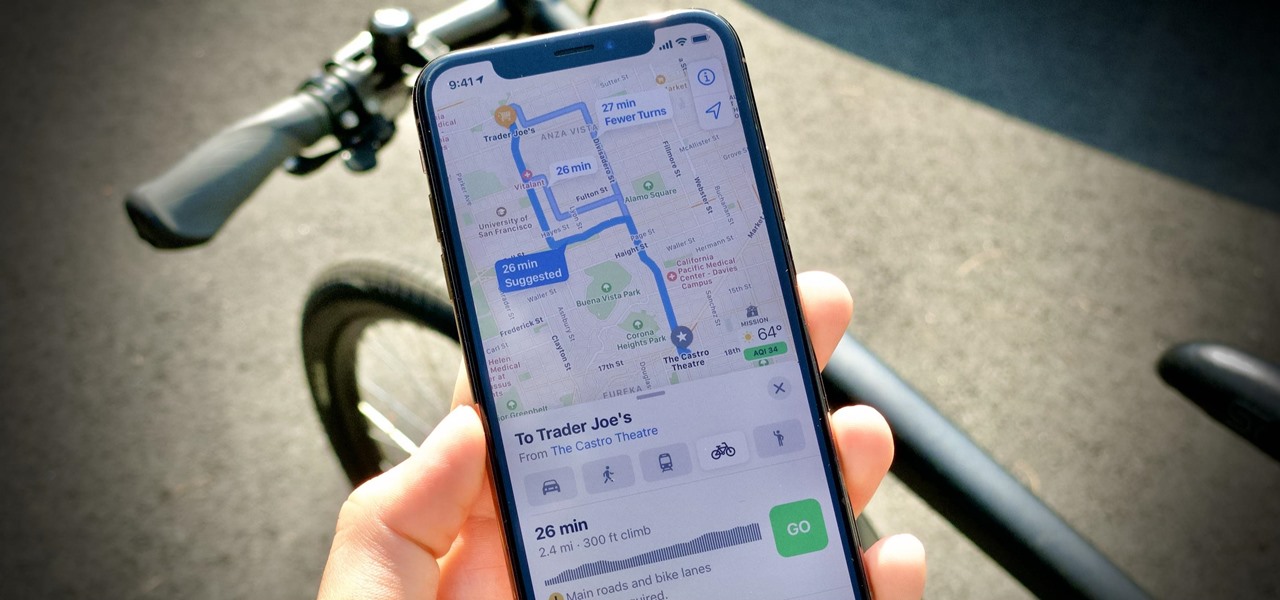
Once the laughing-stock of the navigation app market, Apple Maps is now a powerful, reliable travel companion. Apple rebuilt the platform from the ground up, placing the app in league with Google Maps. That said, there's always room for improvement, as demonstrated by its impressive new features set in iOS 14.

Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe from attackers. That's where Zydra comes in — a tool for cracking RAR files, ZIP files, PDF files, and Linux shadow files.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Overall, iOS is more impressive than ever with its stability enhancements, security tools, suite of apps and services, and intuitive user interface. With each passing update, things just get better and better for iPhone users. But don't think for a second that this is all because of Apple's genius — many of these features were at least partly inspired by tweaks made by the jailbreak community.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

This year's big iPhone update, iOS 12, aims to solve many of the issues that arose during iOS 11's controversial, buggy tenure. With that in mind, it may be tempting to jump on board the new software immediately and leave iOS 11 in the dust for good. Here are some reasons why you might want to reconsider joining the iOS 12 beta.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

Privacy and security go hand in hand, especially for smartphones. When it comes to privacy, you decide what personal information about yourself is out there to discover. Security, on the other hand, is all about enforcing those privacy decisions.

Apple AirTags are super helpful for keeping track of your keys, backpack, and other frequently misplaced items, but there are some pretty clever things you can do with them beyond finding regularly used stuff.

Phone in one pocket, wallet in the other? It's the classic combo guaranteed to give you more pocket bulge. But it's 2024. Half that stuff in your wallet is practically antique. It's time to finally ditch all the dead weight and get a MagSafe wallet for iPhone — and we've got the best picks to slim you down to the essentials.

If you bought an iPhone or iPad equipped with USB-C but didn't max out the local storage, there are some great external storage solutions beyond iCloud and other cloud storage services. And now that the iPhone lineup comes with USB-C ports, you have better-performing external drives available to you than anything you could ever get for a Lightning-based model.

Our everyday lives are inundated with displays from smartphones, computers, tablets, TVs, and other devices, so it's important to find ways to limit your screen use wherever possible to improve your overall digital well-being. One simple thing you can do if you have an Apple Watch is make your watch tell you the time so you don't have to look yourself — and this little-known feature is easy to unlock.