The Files app received a big update in iOS 13. Before, it was limited to local and cloud-based files, but now you can access data from external storage devices, including SD cards and USB drives. But before you try to connect your favorite card or drive to your iPhone, there are a few things you need to know.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

It's that time a year when winter storms begin causing havoc across the United States, and when "rotating outages" are common to help sustain the electrical grid during intense cold periods. That means pretty much anybody with snow and ice in their backyard can succumb to power outages. And no electricity means no electric heat.

The warmth of a fire is great while camping or on a cold winter’s night but it can be difficult to get those log roaring. Use materials you have at home to create some easy, fool-proof fire starters that you can use the next time you need to get some logs burning.

Keeping your home clean is an endless battle with time, motivation, and the easy availability of cleaning supplies. That's where the Hard Surface Floor Cleaning Robot Vacuum comes in. This magical device will save you time by automatically keeping your floors clean, never requires motivation, and doesn't require additional supplies beyond occasionally emptying the dust bin.

Even as we look forward to returning to work in person, the last year has changed how work can be done. That means there will always be a demand for good programmers and coders who can support the digital infrastructure of the online working world. The Backend Developer Bootcamp Bundle can give you the expertise you need to become a highly qualified programmer for only $29.99.

Facebook has announced the cancelation of its annual F8 developer conference, citing concerns around the developing coronavirus health crisis.

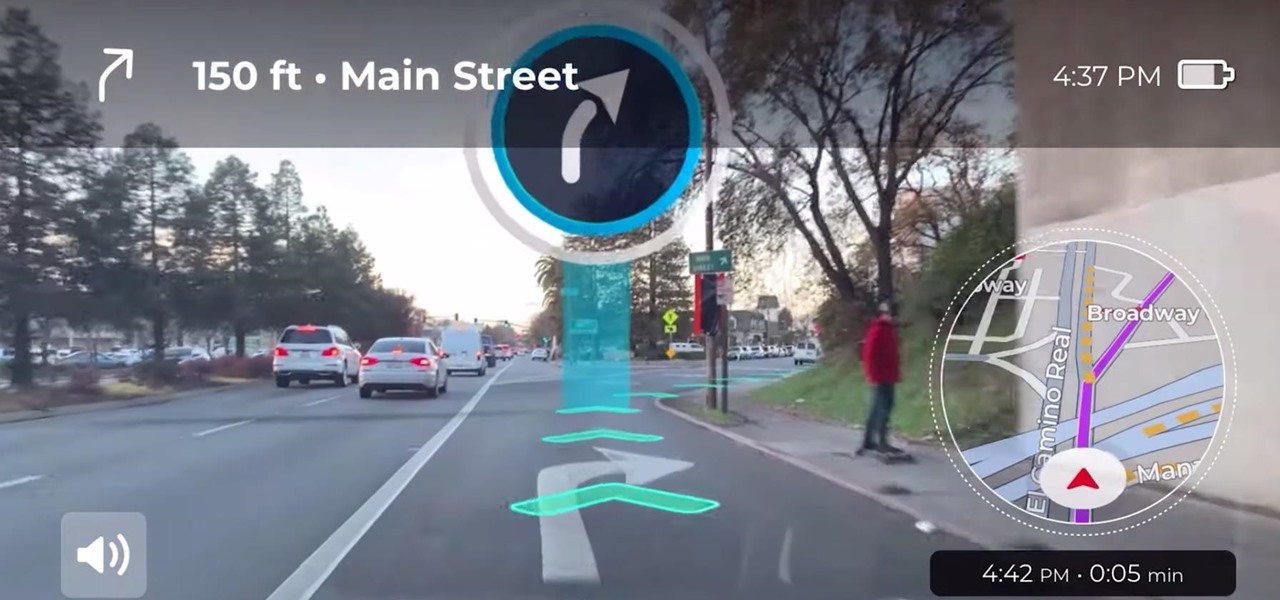
Google pushed a new kind of augmented reality walking navigation to the mainstream last year, and now startup Phiar is hoping users will use its AR app in the same way for driving navigation.

After dipping its toes into the AR cloud arena last year, Ubiquity6 is now jumping in with both feet this year.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

With the consumer edition of its Nreal Light headset, scheduled to ship in 2020, Nreal is prepared to bring the entire Android app ecosystem into augmented reality.

It's the holiday season, and the tech industry is giving consumers several AR products and apps as gift-giving options.

The next phase of the holographic display is upon us, and Looking Glass is aggressively making sure that it's at the tip of the spear when it comes to leading that charge.

Despite hints hidden in internal iOS 13 code, Apple did not unveil its long-rumored smartglasses at its annual iPhone launch event on Tuesday.

The venture arms of Samsung and Verizon Ventures, along with Comcast, are among the strategic investors backing startup Light Field Lab and its glasses-free holographic displays in a $28 million Series A funding round

When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.

Some investors play the short game, placing their bets on industries that show the quickest return on their investment, and, in the augmented reality space, that means the enterprise sector.

As promised with its teaser from Build 2019, Microsoft has unveiled the details for its augmented reality version of Minecraft for smartphones.

As the opening act to the grand unveiling of the long-awaited HoloLens 2 at Mobile World Congress Barcelona on Sunday, Microsoft showed off the standalone Azure Kinect time of flight sensor, which also happens to supply the improved human and environmental understanding capabilities of the next-generation augmented reality headset.

The week of the annual Consumer Electronics Show is supposed to be filled with good news for the augmented reality industry as AR headset and smartglasses makers show off their new wares.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

On Wednesday, in addition to uploading another batch of videos from its L.E.A.P. conference to its YouTube channel, Magic Leap also launched a new video series for developers called Spacebar.

Ingress, the godfather of location based-AR games developed by Pokémon GO creator Niantic Labs, is getting a new lease on life via Ingress Prime, a reboot of the game built on the Niantic Real World Platform.

Location-based gaming pioneer Niantic has offered a preview of its augmented reality cloud platform that could change the immersive content game yet again.

Escape rooms, those real world puzzle games that challenge teams to solve a mystery and gain their freedom from a locked room, are all the rage right now. But augmented reality games such as The Lockdown could make them obsolete.

The premise of Jurassic World revolves around splicing genes to create new dinosaurs, so it is fitting that the location-based AR game is a clone of Pokémon GO merged with the DNA of the Jurassic Park franchise.

A recent TED Talk makes a strong case for the healthcare industry to adopt augmented reality as a means to expanding access to surgical care across the globe.

Just over a week after debuting, Animal Crossing: Pocket Camp received its first-ever event geared toward the winter holiday season. With the ability to craft Christmas-themed goodies and own a full Santa suit, it's the perfect time to jump into Nintendo's latest hot mobile game.

The Pixel 2 and Pixel 2 XL were built by different manufacturers. This is pretty common knowledge among Android fans at this point — Google's smaller Pixel 2 was built by HTC, while the larger Pixel 2 XL was built by LG. What would the Pixel 2 XL look like if HTC had followed through and delivered on the larger phone for Google? Today we have some answers.

The promotional images for American Horror Story: Cult have been some of the most arresting in recent memory. They mash coulrophobia, trypophobia, and body horror together with some serious economy into a succinct, colorful, image. It's like a bad car accident that you can't stop rubbernecking. Which makes it perfect for a Halloween costume — you'll be repulsive, but no one will be able to look away. While the beehive skull hasn't made an actual appearance in Cult yet, and probably won't sinc...

You can bet Thor costumes will be prominent among the superheroes seen this Oct. 31. Since the summer, there has been no shortage of coverage for Thor: Ragnarok, and the timing of its November release couldn't be better as a tie-in with the cosplaying holiday known as Halloween. This year, the success of pulling off the Thor costume will rely on how well your new Thor helmet looks, which as it happens, you can DIY at home, using a few simple supplies and perhaps a trip or two to the craft and...

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

Clearly, the next big battlefield for tech gamesmanship between Apple and Google will be augmented reality.

When Disney teased an augmented reality game called Star Wars: Jedi Challenges running on a headset from Lenovo, fans had more questions than Disney had answers. When? How much? Can I be a real Jedi?

Elon Musk has repeatedly said Tesla models in production today have the requisite hardware to offer "full self-driving" capabilities. But for features more advanced than Level 3, Tesla will, in fact, have to revamp Autopilot's hardware to handle the extra computing load.

Regarding foodborne pathogens, eating fish is not as hazardous as it was a few years ago — but if fins are on the menu, it's good to have a heads-up about what's good and what's bad these days.

Whether your palate runs to domestic or imported, a piece of cheese can be a real treat for the senses. Its smell, taste, and texture are all parts of its appeal. A big part of what makes that savory wonderfulness comes from the microbes in and on the cheese. Thanks to a team of researchers dedicated to studying those microbes, we have a better understanding of their importance to cheese and us.

Tesla's Autopilot self-drive interface in its new Model 3 signals the carmaker is already prepping its cars for Level 4 driving years ahead of the competition.