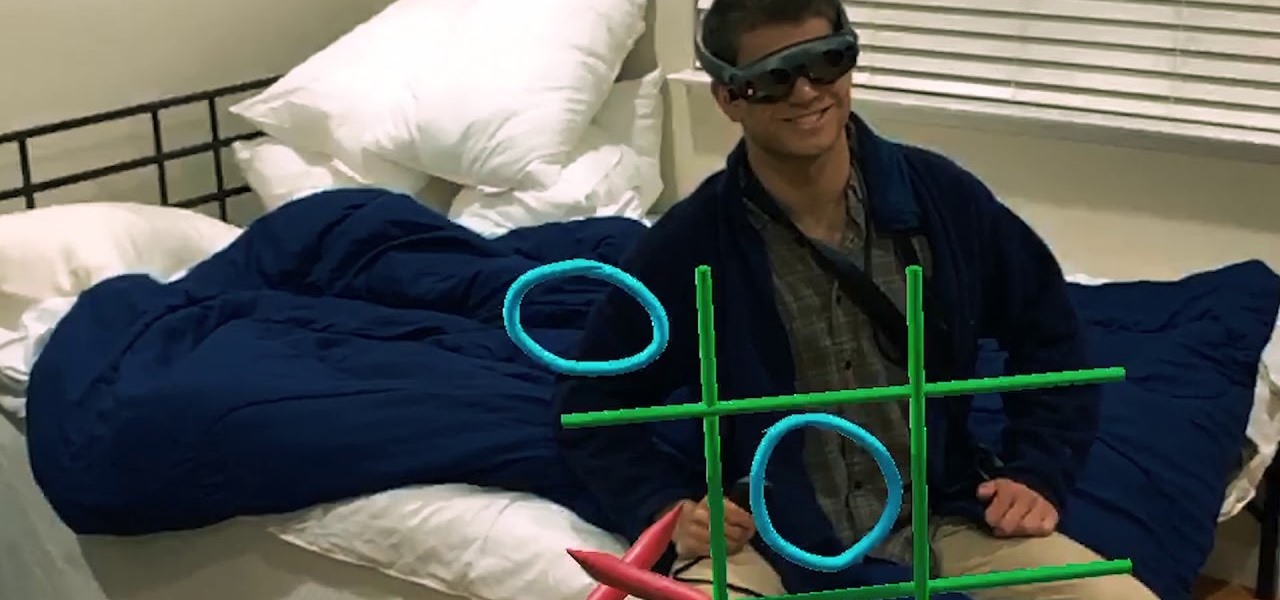
Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

It was a long time coming, but we finally have a meaningful conclusion to the legal case against augmented reality startup Meta Company.
The venture arms of Samsung and Verizon Ventures, along with Comcast, are among the strategic investors backing startup Light Field Lab and its glasses-free holographic displays in a $28 million Series A funding round

Fast-food chain Jack in the Box has decided to put an augmented reality twist on the traditional sweepstakes promotion by employing the immersive powers of Snapchat.

In recent years, augmented reality has increasingly helped to take art off museum walls and bring it (virtually) into people's homes and communities, offering new perspectives on classic pieces and modern creations alike.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

The long-awaited Dark Mode may have grabbed all the spotlight with iOS 13, but Apple has made subtle changes across the whole platform to make your iPhone even more user-friendly. A small option aimed at people who are sensitive to motion is one such example — a feature that can also be a godsend for the rest of us.

The recent industry whispers in augmented reality are mostly about Apple and its rumored fashion-friendly smartglasses, but one company isn't waiting for the iPhone heavyweight to enter the fray.

In Safari for iPhone, as far back as iOS 7, you can request the full desktop version of websites. The process was streamlined starting in iOS 9, but the process remains relatively hidden and easily missed. Now, iOS 13 shines a light on it, as well as adds functionality to set the desktop view for individual websites indefinitely.

The Music sticker is one of Instagram's best features. With it, you can add music directly to your story, incorporating a high-quality soundtrack to your favorite moments. On June 6, Instagram upped the ante on this feature, introducing live song lyrics that play throughout your story. Karaoke, anyone?

If online retail is war (and who says it isn't), then CGTrader is prepared to arm its allies with augmented reality ammunition.

I'm here at the annual AWE event in Santa Clara, California, and the venue is just as packed, if not more so, than last year.

Almost half a year after we broke the story about the demise of Meta Company, there's good news for fans of the augmented reality startup — a rebirth is at hand.

As promised with its teaser from Build 2019, Microsoft has unveiled the details for its augmented reality version of Minecraft for smartphones.

The Pixel is the phone to beat when it comes to cameras, and it's largely due to software. While its hardware is solid, Google's machine learning prowess and general coding wizardry are the biggest reasons the Pixel is so good with taking photos and recording video. What this means is that if you can get the Pixel's camera software, you can replicate the Pixel camera experience on other phones.

Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Describing how and why the HoloLens 2 is so much better than the original is helpful, but seeing it is even better.

Months after Next Reality broke the story surrounding the financial troubles at Meta Company, there's a new update in the company's ongoing patent lawsuit.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

The camera punch hole on the S10 has gotten our creative juices flowing more than any notch ever could. First, we saw wallpapers that served to camouflage the cutout or even accentuate it. Now, if you want to go the opposite direction and highlight your S10's camera hole, there's an app that turns it into a circular battery meter.

Compared to the original AirPods, Apple's second-generation AirPods have better battery life, Hey Siri support, a more stable connection, faster switching between devices and call connections, less latency for gaming, and an optional Wireless Charging Case. If you plan on preordering the new model, you might want to skip the Apple Store and opt for Amazon instead to get it at your door quicker.

Four months have passed since Mojo Vision emerged from stealth, and we are no closer to seeing exactly what its "invisible computing" technology looks like.

While painting in augmented reality is not a groundbreaking pursuit, the ability for Magic Leap One, iPhone and iPad, and Android users to collaborate remotely on virtual artwork would be.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Last week at Mobile World Congress 2019, Google put an augmented reality twist on its annual Android Partner Walk via its ARCore toolkit.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

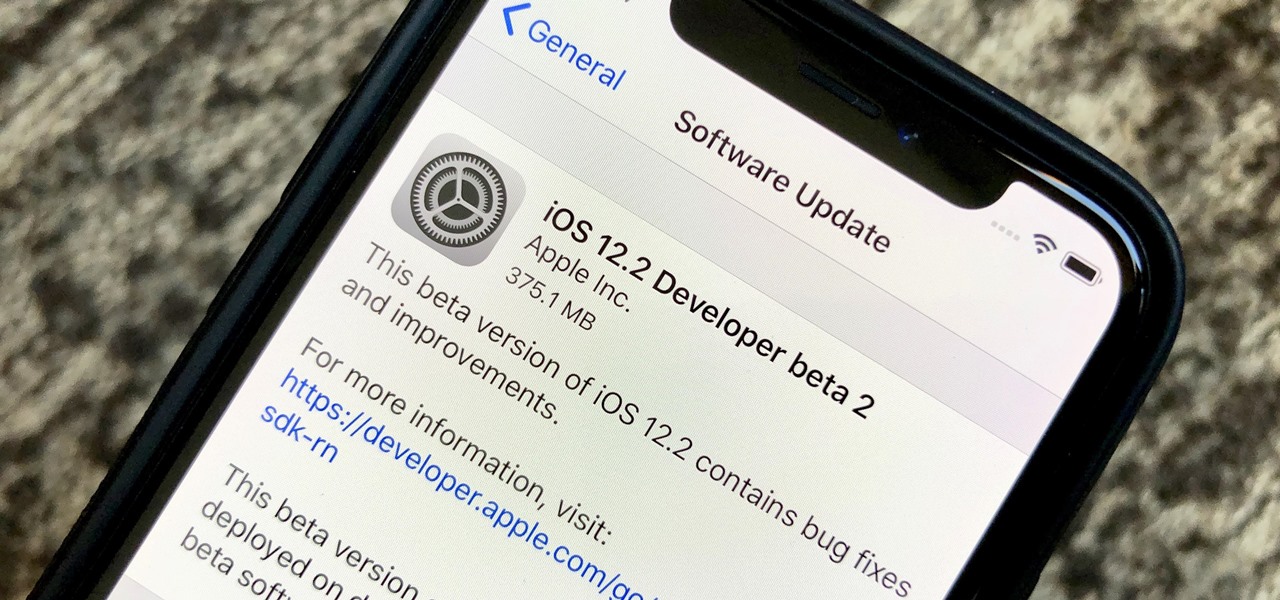
Seven days ago, Apple released the first public beta for iOS 12.2. Now, public testers have access to the latest beta update since Apple released 12.2 public beta 2 on Tuesday, Feb. 5. The company released the developer beta one day earlier, which includes bug fixes, new Animoji, and more.

On Monday, Feb. 4, Apple released the second developer beta for iOS 12.2. The update features bug fixes to users running iOS 12.2 beta 1, as well as four new Animoji for Face ID devices. Developers are strongly encouraged to update their iPhones. It's unclear at this time whether the update includes a fix for the Group FaceTime bug discovered last week.

Stories are everywhere in social media today, but that wasn't always the case. In 2013, Snapchat introduced the world to these temporary windows into our daily lives. Since then, stories have infiltrated other popular apps. However, to stand out, you can't solely rely on the app where the story will be posted. Instead, you need a suite of apps that can turn your story into something special.

With Magic Leap One approaching six months since launch, Magic Leap is fully focused on building a content ecosystem and developer community.

Move over, cosmetics companies. The athletic footwear industry wants to be able to give their customers the opportunity to try on products in augmented reality as well.

CarPlay is no doubt the best way to use your iPhone when behind the wheel since you can safely drive without too many distractions. It gets even better with all the music and podcasting apps available, as well as third-party navigation apps such as Google Maps and Waze. With more apps being added to CarPlay every day, it becomes more necessary to rearrange your home screen.

The ability for apps and devices to determine the precise location of physical and virtual objects in space is a key component of augmented reality experiences, and the latest advancements in Bluetooth technology may have a hand in facilitating such location services in the near future.

Among a crowded field of AR cloud companies aiming to power the future of augmented reality by creating a world of persistent holographic content that lives in a cloud, accessible across devices and accounts, Ubiquity6 is hoping it has found a way to differentiate its platform.

With Pokémon GO as its cash cow and the forthcoming Harry Potter: Wizards Unite and Niantic Real World Platform promising future revenue streams, Niantic has convinced investors to bet on its flavor of augmented reality

With CES in full swing, it seemed like Magic Leap would have little to announce at the major tech event, but it turns out that one of its partners has weighed in with a rather substantial update regarding the company.

While Leap Motion has given makers a DIY solution for building their own augmented reality headset with Project North Star, a self-described "AR wonk" has taken the blueprints one step further by creating an untethered version.

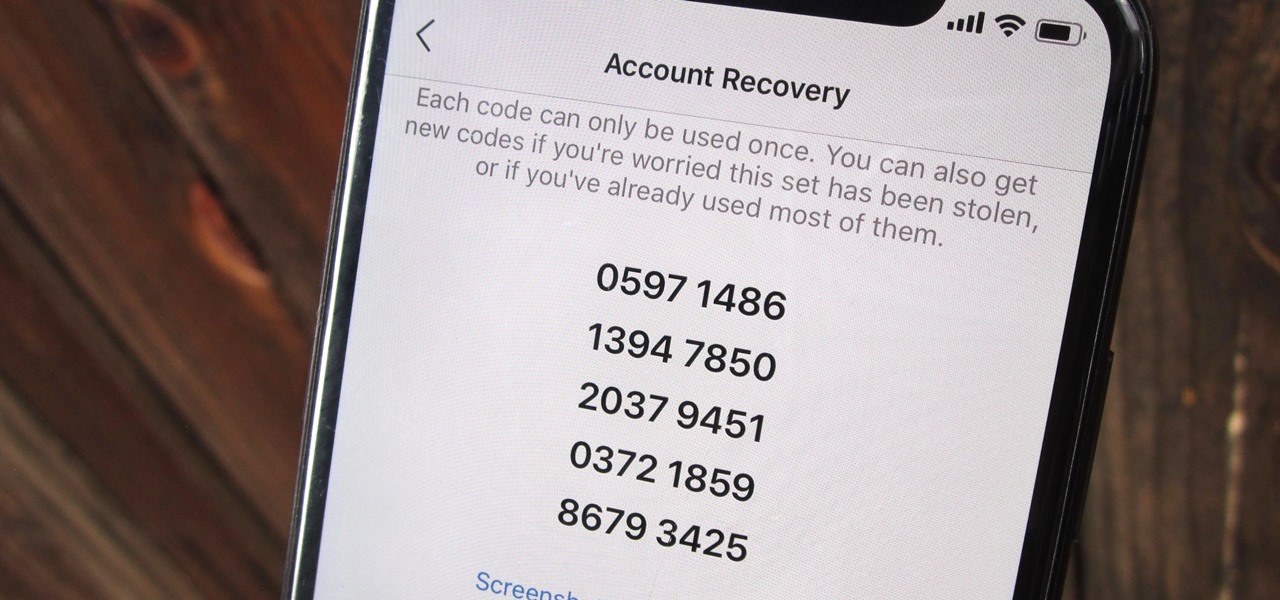
Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

Despite funding difficulties that forced Meta to place employees on temporary leave in September, the augmented reality headset maker is reminding enterprise companies that it remains a viable option for visualizing and working with 3D design models.

This year's holiday shopping season is shaping up to be fertile ground for augmented reality to show its worth, as both Walmart and Target have crafted immersive experiences designed to engage shoppers in the coming weeks.