In order to take full advantage of all the fun features on the Sony Dash, you will need to register it. Check out this tutorial, presented by Sony and learn all about how to register online (once you've connected a WiFi network to your Dash). This will allow you to download apps, customize your new Dash and much more.
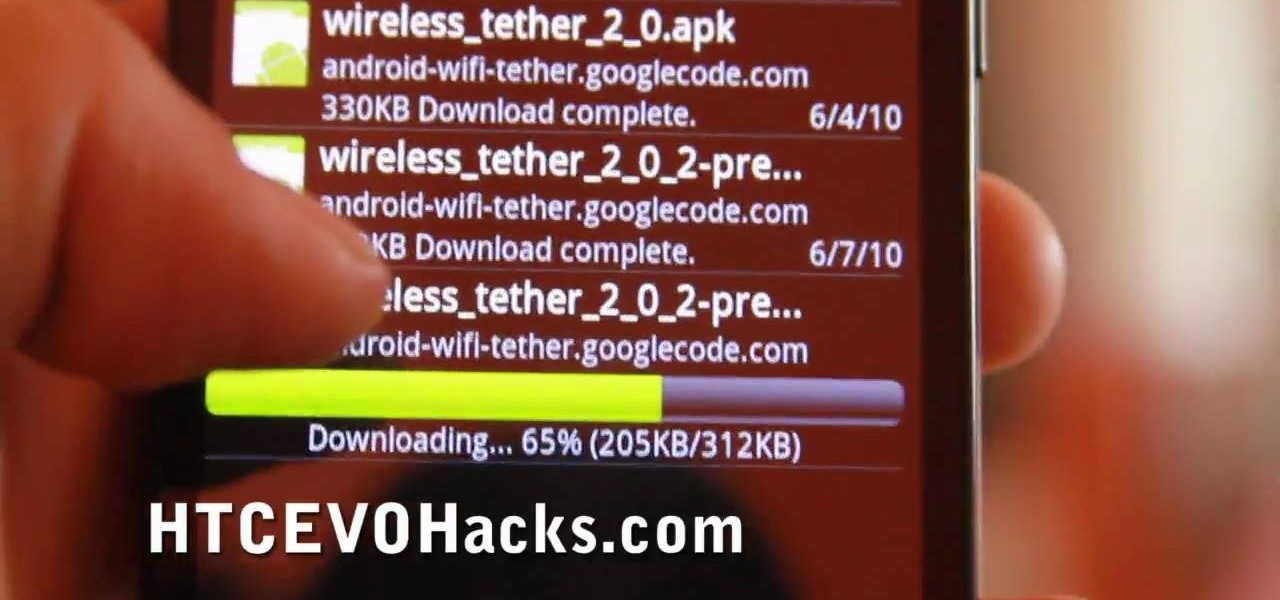
In this tutorial, learn how to access your phone's data network to enable free tethering on your new HTC EVO 4G. By tethering with your EVO you can connect up to eight other devices to your phone and use it as a wireless modem. This hack works with any EVO and will allow you to connect regardless of whether your city offers 3G or 4G signals.

Bring a genuine taste of the Mediterranean with this killer recipe for branzino with lemoms. The only way to get it more authentic than this is if you get directly from the source. Bring that flavor home with this video from The Food Network.

Avocados provide you with some of the healthiest fat you can out into your body. If you want to find a way to add more avocado to your diet without then this video from The Food Network has good some flavor coming your way. This video will show you how to make two awesome avocado dishes.

Fennel is more than just an herb that adds flavor to sausage. Add a little bit of sophistication to a classic dish by throwing in some shredded fennel the next you chop up some slaw at home. This video from The Food Network will show you how to whip up a fennel and cabbage slaw.

Here Christopher Walken shows us how to roast a chicken with pears. It is a simple recipe, recorded supposedly as an audition tape for Food Network. We cannot confirm.

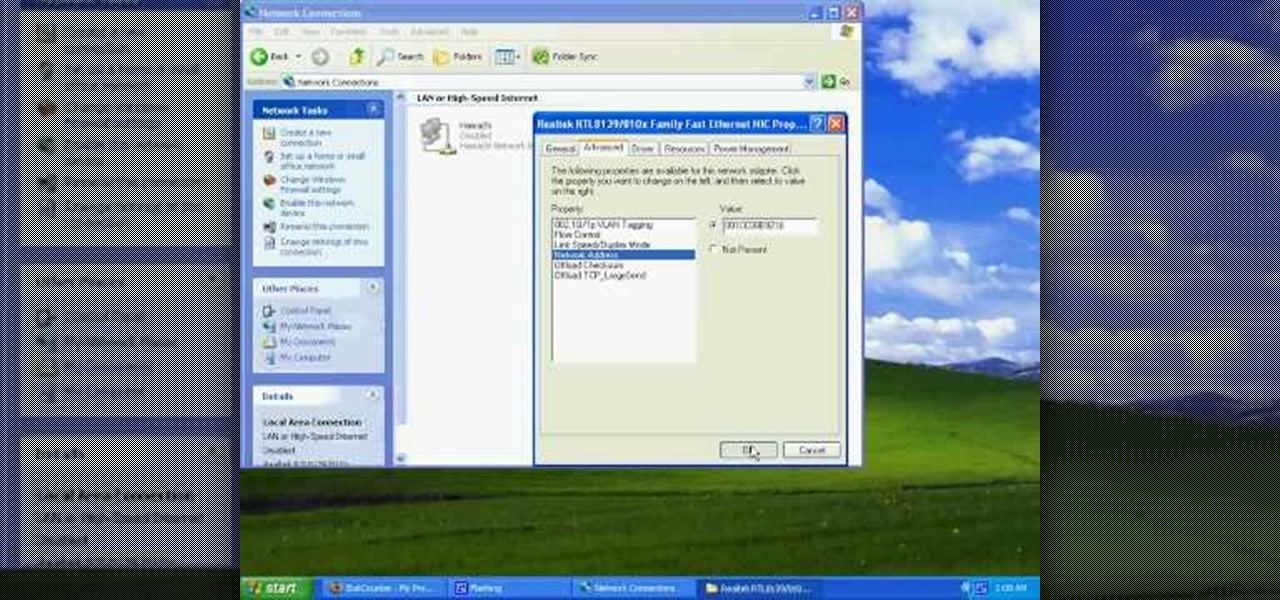
This video tutorial from tarunkumarsinghal shows how to change Mac address on Windows XP. Click Start menu and then Control Panel. Make sure control panel window is in classic view mode. If not, change it to classic from the left pane.

When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but also what type you're connected to.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

For the most part, Google Wifi and Nest Wifi systems take care of themselves. But there are still a few manual features that might come in handy, like being able to check on network activity to see which devices are using the most bandwidth when your connection gets bogged down.

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

The newly-announced Moto G7 Play offers some of the same upgrades as its sibling, the Moto G7, but at a much lower price. The upgrades are pretty significant when compared to last year's Moto G6 Play, taking this phone from the "only if you're on a strict budget" category into a great value option.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

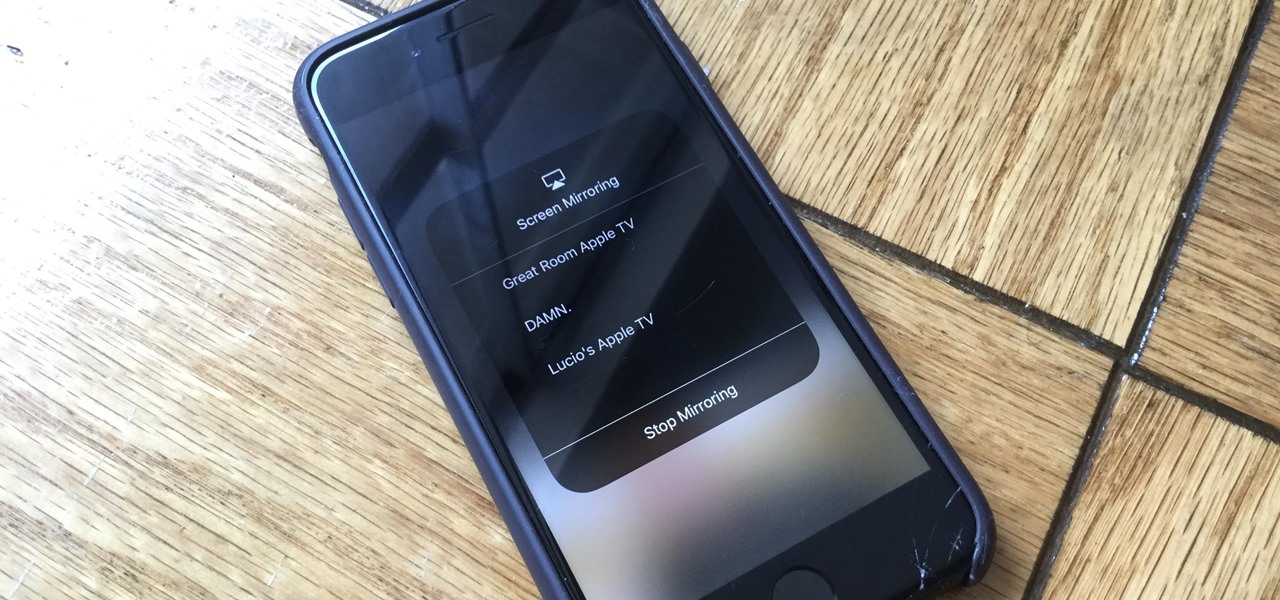
When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

2017 was a down year for HTC. First, the U11 and U Ultra were widely criticized. Later, Google purchased a large chunk of HTC's manufacturing division, leaving the Taiwanese company running with a skeleton crew after losing 2,000 key employees. But that's not stopping HTC — their flagship U12+ was just announced, and it's quite impressive.

It took a few months, but several major phones are finally receiving updates to Android Oreo. At this point, we've spent significant time talking about Oreo on the Galaxy S8, Galaxy Note 8, and Essential Phone. While an update to the latest OS is always great, there is one big Android 8.0 feature that isn't coming to every phone.

With Virtual Network Computing, you don't need to carry a spare keyboard, mouse, or monitor to use your headless computer's full graphical user interface (GUI). Instead, you can connect remotely to it through any available computer or smartphone.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

While HBO Now does not support offline viewing yet, your smartphone is the perfect way to watch your favorite shows and movies on-the-go. Whether you're in a hotel running off Wi-Fi or you have an unlimited plan and are on the bus, if you want to binge some Game of Thrones, the HBO Now app is there for you.

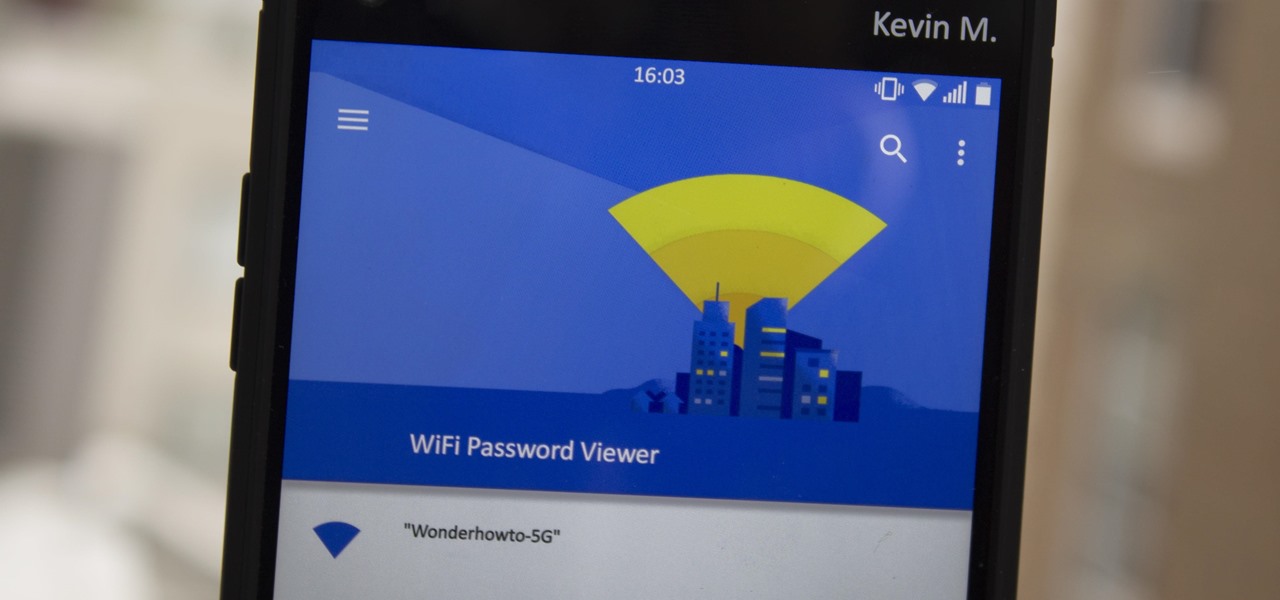
Have you ever gone to a friend's house and not asked for the Wi-Fi password? Probably not, and the same can likely be said of any friends that come over to your place. But the actual act of sharing Wi-Fi passwords is still incredibly clunky, and it's particularly hard if you have a nice and secure password with uppercase and lowercase letters, numbers, and symbols.

Hello everyone! How's subnetting going? Did you practice a lot? I hope you did, but even if you didn't we will go through some more examples so you can be feeling confident after reading this article. It's all about that bad boy binary!

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

WPA Enterprise is widely used in large corporations as it offers individual and centralized control through a server that authenticate the users (RADIUS server). In this tutorial I will show you how to break the barrier and obtain the user credentials.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

Thanks to Verizon Wireless, I pay over $220 a month for my phone bill. It's just me on the plan—no family members, and it's not even unlimited data. So, when I receive that data alert message telling me that I've used up 90% of my plan and that I've still got a few more week until my billing cycle starts over, you know that I'm left scrambling to connect to some Wi-Fi.

If you work at a large office or have a multi-story home, you're probably familiar with Wi-Fi range extenders. Since one hotspot isn't always enough to cover an entire area, Wi-Fi repeaters are generally set up in larger areas to capture and rebroadcast the original signal.

One thing I absolutely cannot stand is lag when I'm gaming. Every time I'm about to beat my killstreak record on Call of Duty, my internet connection drops and I'm a goner. It never fails. This usually happens because someone else on my Wi-Fi is streaming a movie or downloading a huge file.

If you're spending hours on your phone playing games like Angry Birds and Candy Crush Saga, or posting online to Google+ and Pinterest, you're probably being spied on. The latest releases from NSA whistle blower Edward Snowden reveal that the National Security Agency, and its UK counterpart, GCHQ, are mining the ad networks utilized in these apps to collect a trove of information on you.

Welcome back, my fledgling hackers! In one of my recent articles, I showed you how to install BackTrack as a dual boot system on a Windows computer. In this tutorial, I will walk you through BackTrack, giving you a tour of the most salient features for the hacker-to-be.

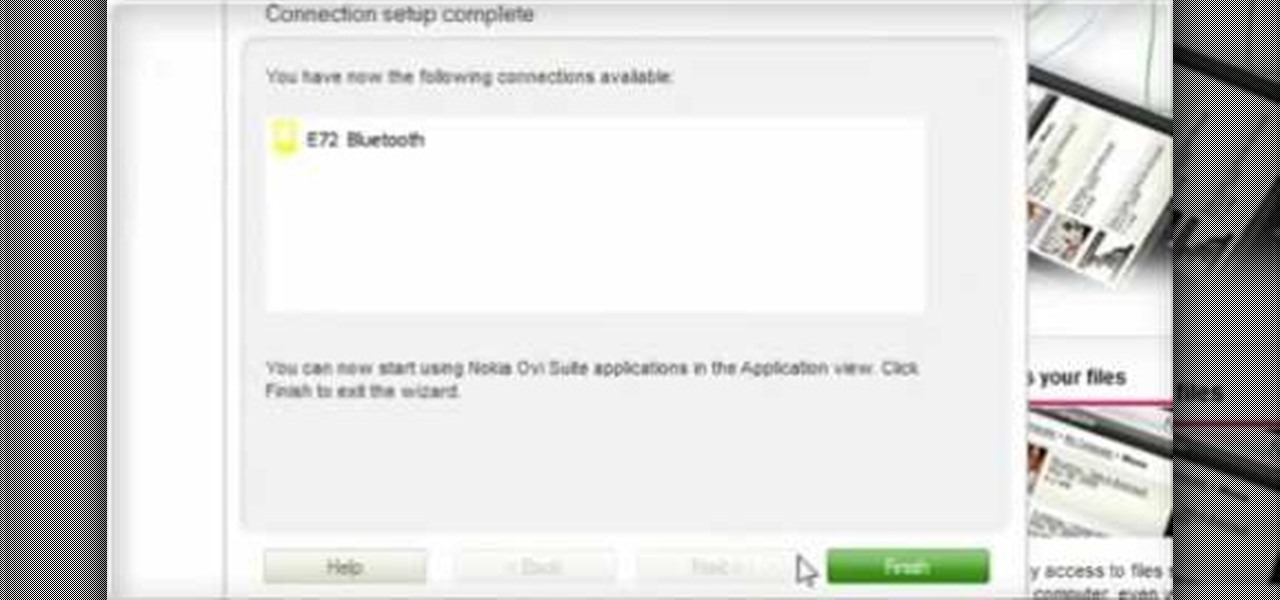
Calendar data, images, sounds, videos, and messages can be easily synchronized between your Nokia Booklet 3G netbook and supported mobile devices and phones when the two are connected using Bluetooth. To find out how to use Nokia's Ovi Suite software to synchronize your data, take a look at this tech support video from the company.

This system won't replace the need for a tripod entirely, but it's a great way to use both a superclamp and an articulated arm to give you a little extra camera support if you can't use a tripod for a particular shot.

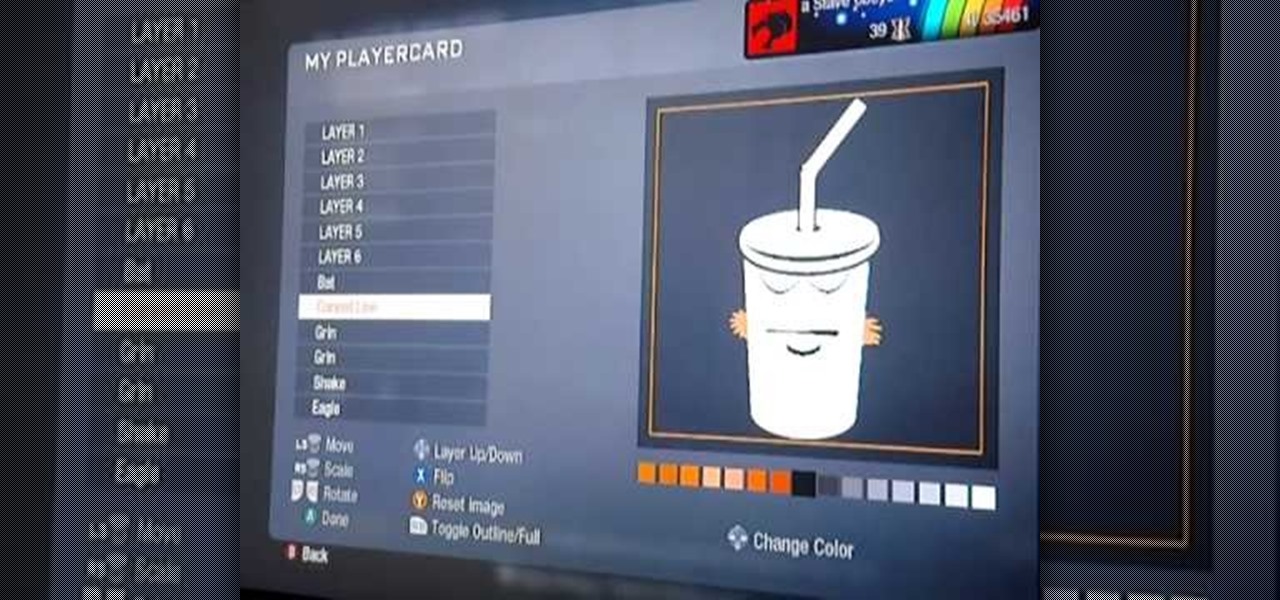
Learn how to recreate Master Shake from the Cartoon Network's Aqua Teen Hunger Force as a custom, multilayer Black Ops playercard emblem! This COD Emblem Editor tutorial presents a complete, step-by-step walkthrough of the drawing process.

This video shows you the most effective ways to use a helicopter as air support when you're playing as the cops in the hot new video game, Need for Speed: Hot Pursuit. Helicopters are especially good at laying down the spike strips.

Need to browse the web on your new Samsung Galaxy Tab? Well, first you're going to have to set up Wi-Fi on the Android device. This video shows you the complete steps to getting connected! Press MENU < SETTINGS < WIRELESS & NETWORKS < WI-FI SETTINGS and then select WI-FI to turn in on. Next, choose your network, enter the password and press CONNECT. It's that easy.

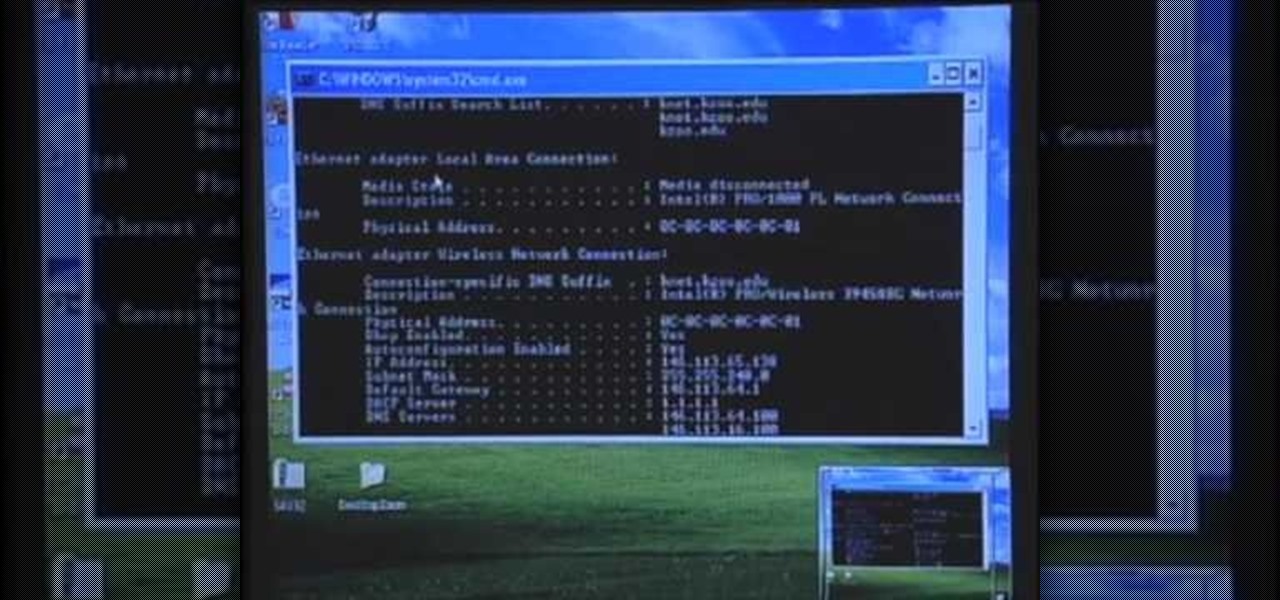
In this tutorial, we learn how to quickly find your MAC address. This is the address that identifies your computer on a network. When you go to a campus, you will need to register your computer with a resnet so you can access the internet. To find the address, you will head to the Apple menu, then click 'about this MAC'. Click on the 'more' button and then click on 'network' and 'built in Ethernet'. This is the MAC address that you will need to register your computer, you may have a few of th...

In this tutorial, we learn how to make a DIY. XBOX 360 Wi-Fi adapter. First, go to your network connection properties on your laptop or netbook. From here, you will disconnect from any connection you have going. Then, select both connections and right click 'bridge connections'. Once finished, reconnect to your Wi-Fi network. Now, you can take one end of your cable and connect it to your computer and then your XBox. From here, you should be able to connect to XBox Live and play any game you'd...