How To: Create and map a network drive on Windows XP
How to create and map a network drive using XP home.


How to create and map a network drive using XP home.
A basic overview of how to setup a wireless network on a Mac.

In this episode, Brandon Jackson joins D.Lee Beard to present an in-depth review of the Slingbox A/V, explore where to find free downloadable audiobooks online, and to answer viewer questions on using an iMac as a display and how to share files over a local network between a Mac and a Windows PC . Be sure to check out our next video to learn how you can win the Techies' Slingbox and begin watching your home TV from all over the world via the internet.

5G is undoubtedly the future of mobile networks, and there's a good chance your next phone will have it. But just like with 4G, as carriers race to get the best 5G coverage, the ones running behind are abusing marketing terms to make themselves seem further ahead than they actually are.
In November 2016, the RCS Universal Profile (Rich Communications Services) was introduced. The technology takes text messaging to the 21st century, emulating many of the features found in IM apps like WhatsApp and iMessage, but working through your phone number like regular SMS or MMS. The only thing is, your carrier needs to support RCS-UP to use the feature. Thankfully, the list is growing.

Giving up your Wi-Fi password can be giving up more control than you think. Because of the way Chromecast and other IoT devices communicate, anyone on the same Wi-Fi network as your device can often make it do whatever they want. With a script called "Cast All the Things," we can hijack a Chromecast to play nearly any kind of media with a single command in terminal.
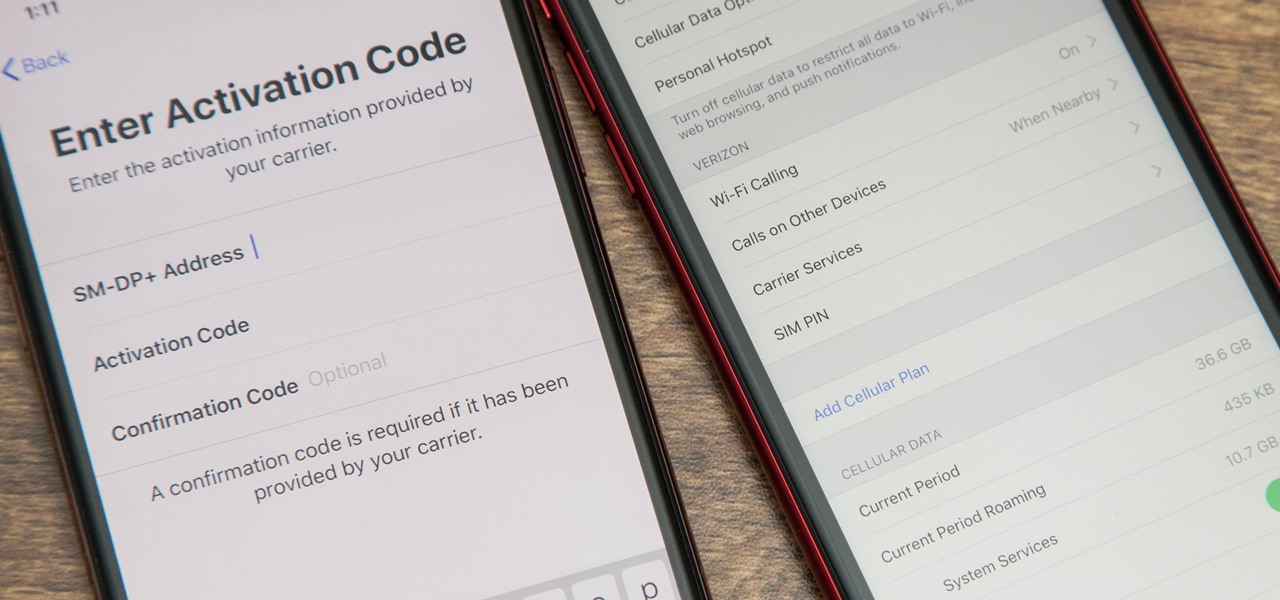
With an iPhone that includes a digital eSIM option aside its standard Nano-SIM card, you can have two cellular service accounts. One can be your primary line with your main wireless carrier, and the other can be from your main carrier or another provider. The eSIM account can be prepaid or postpaid as well as data-only, which is great for traveling. But which wireless providers support eSIM?

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

At the moment, the iPad is officially locked to the AT&T network in the USA. If you would like to use your iPad but do not intend on leaving your current mobile carrier, check out this video.

Gigafide explains that with so many different social networking sites, it is hard to keep information up to date on all of them. He first introduces TweetDeck, an amazing desktop application that allows a user to update information for their Twitter, Facebook, MySpace, and LinkedIn accounts. If you don't want to go through the hassle of installing TweetDeck on your computer, there is HootSuite, a web application that allows you to do this and if you're interested in keeping track of much more...

In this video tutorial, viewers learn how to play the game, Borderlands online with Hamachi private network. Users will need to first download the Hamachi private network. Then open Control Panel, and select Network and Sharing Center. Under Tasks, click on Manage Network Connections. Click on the Advanced menu and click on Advanced Settings. Move the Hamachi network up and click OK. Now open the Hamachi and create a new network or create on. Type in the network ID and password. This video wi...
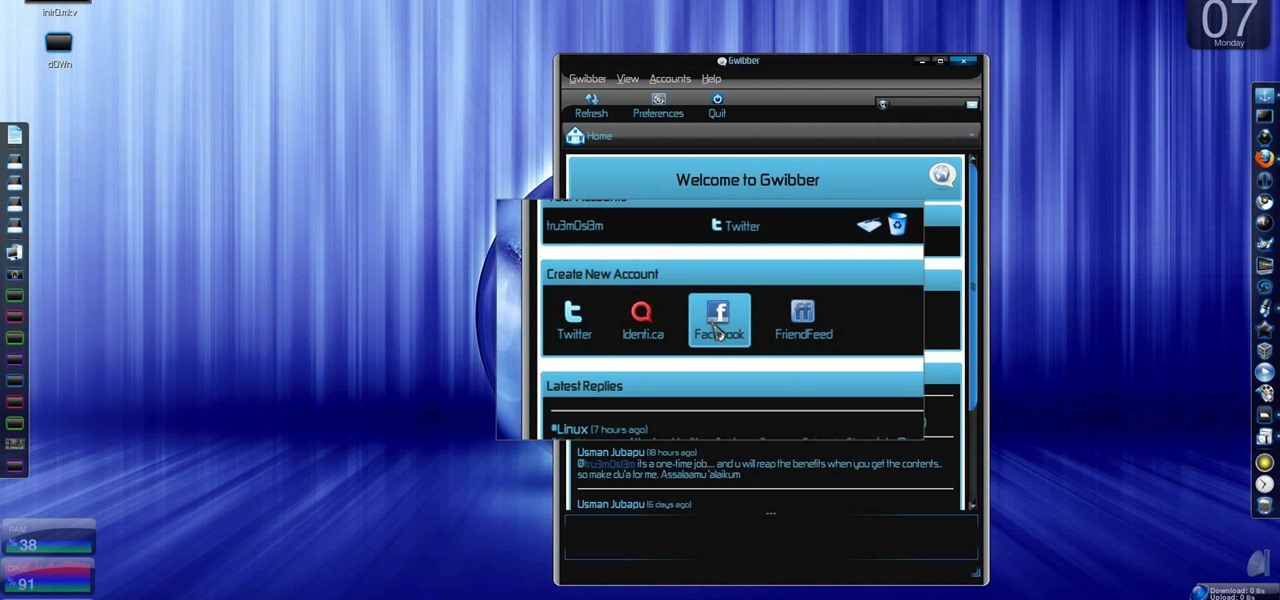
Twitter has consumed the world, so make sure you're up to date on your Tweets. One way to do that is with Gwibber 2.0 on Ubuntu Linux, the computer operating system that could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to retrieve unlimited tweets with Gwibber 2.0 on Ubuntu Linux.
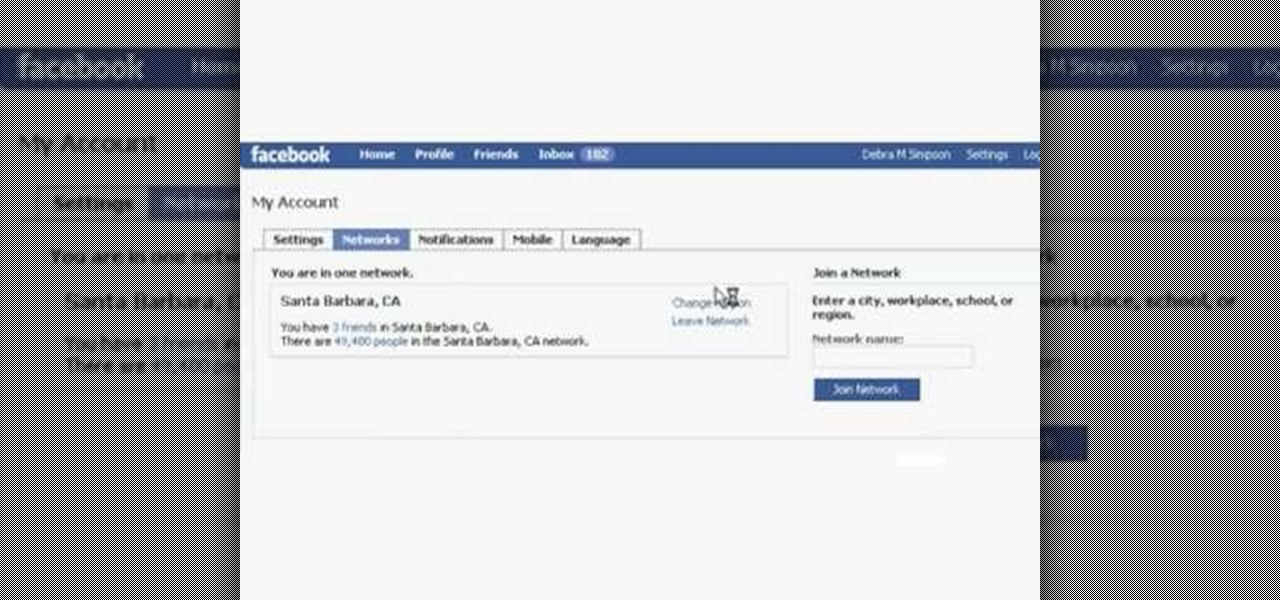
Magicinwords teaches viewers how to change their facebook network! First, you will want to log onto Facebook.com. When signed in, go to the settings tab on the right of the screen. Under this, click on 'account settings'. Under account settings choose the tab that reads 'networks'. Here, you can click 'change your region' and then you can update it. Be sure this is right though, you can only change your regional network twice every 60 days. Under this same tab, you can also join any other net...

The video shows how to join a home group on a Windows 7 network by helves shows you how to join a home group on a Windows 7 network of computers. It is approximately one minute thirty seconds long. To join a home group on a Windows 7 network you first go to control panel, then you click on Network and Internet, after that you click on network and sharing center, and finally click join a home group in the top right. You now select what file types you want to share with the other Windows 7 comp...
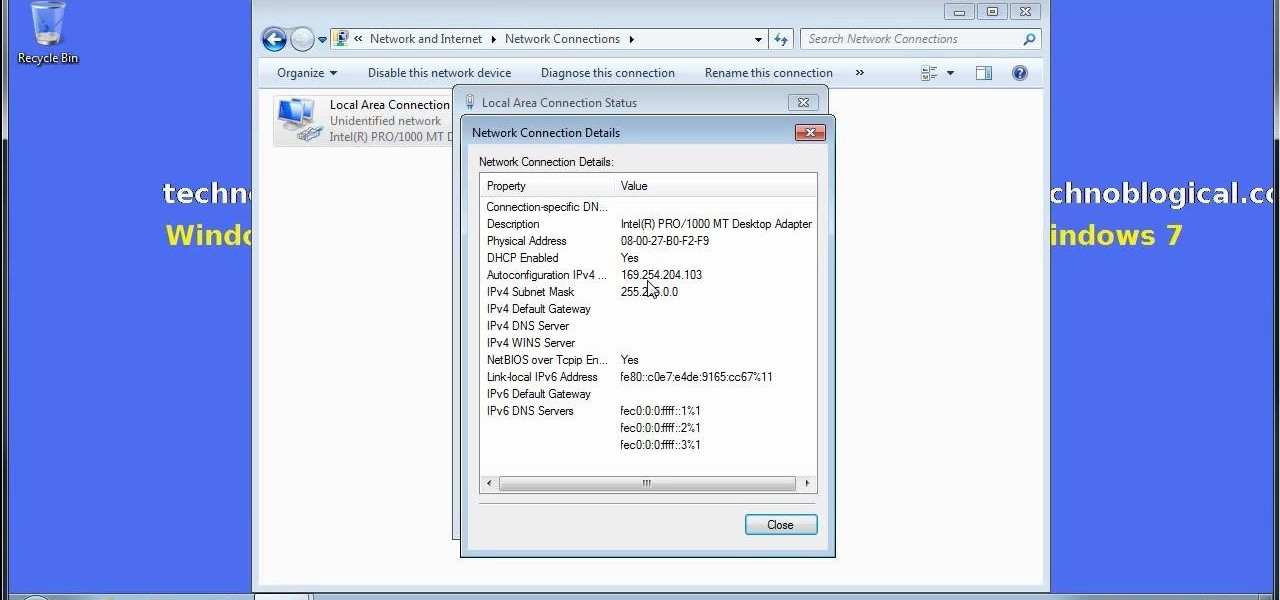
Want to share Internet connectivity between two computers without a wireless network but have an extra CAT5 ethernet cable? You're in luck. This home networking how-to will show you what to do to get your machines talking not only to one another but the web at large.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

If you're in the market for a new smartphone, you'll likely scan spec sheets and read reviews of the top phones, compare display size and technology, RAM amount, and processors. But one factor that is often overlooked is cell reception — and for T-Mobile subscribers, there's only one device that has flagship specs and an exclusive antenna that will actually improve your signal.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Last week, T-Mobile CEO John Legere got salty. He announced ever so cheerily T-Mobile's intentions to release the first true 5G network in coming years, all while gaily smacking AT&T around for their bogus "5G Evolution" reveal. But could Legere be wrong to say T-Mobile will be the nation's first 5G carrier? It looks as though that title may have to be shared with Sprint ...

Download a popular, legit app from the Google Play Store. Decompile it. Add malicious code. Repackage the app. Distribute the now trojan-ized app through third-party Android app sites. This is how advertising malware Ewind, what Palo Alto Networks calls "adware in applications' clothing," infects Android users.
So you're finally ready to head out on that big trip you've been planning for months, huh? It's an exciting time, but there are plenty of things you'll need to prepare before you head out. For instance, it's hard to imagine life without a smartphone these days, and with useful traveling apps like Google Translate and maps, you'll almost have to make sure that you have a working smartphone when you arrive at your destination.

Sprint and T-Mobile have agreed to a $31.6 billion deal that, if it gets through federal regulators—which is far from a sure bet—would create a formidable carrier to really compete against AT&T and Verizon. The deal comes packaged with a $1 billion "breakup" fee that Sprint would have to pay T-Mobile in the event the deal does not go through. After the deal, Deutsche Telekom, which owns about 67% of T-Mobile, would maintain a 20% ownership stake.

In this video tutorial, we learn how about the basics of setting up a simple wired network. It's easy. So easy, in fact, that this home-computing how-to from the folks at CNET can present a complete overview of the process in just over two minutes. For more information, including a complete demonstration detailed, step-by-step instructions, take a look.

Getting a Playstation Portable to connect to your wifi network can be tricky. If you own a Buffalo router, this tutorial walks you through the process to get your PSP connected to your home wifi network. Now you can check your email and surf the web on your PSP!

In this tutorial, we learn how to set up a Wi-Fi network with a Linksys router. First, go to your cable modem and remove the yellow Ethernet cable. After this, plug the Ethernet cable into the very first port of the router and plug the other end into your computer. After this, connect any other electronics you have with cables, then plug the router into the wall to give it power. Next, turn the power to the modem and router back on. When finished, you should see a new Wi-Fi network appear in ...
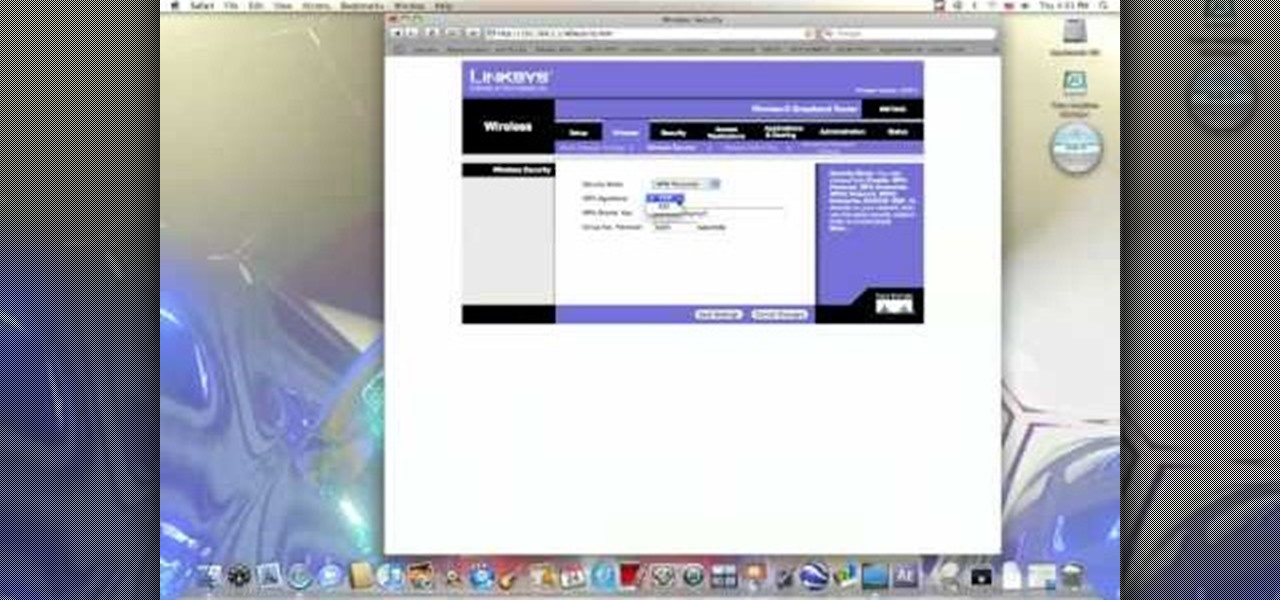
In this video from benjamoon we learn how to secure a linksys wifi network from a Mac. First type in your IP address in your browser bar which is 192.168.1.1 then press enter. If it asks for a password it is admin. Click on Wireless and here you can edit your name and who can access your wifi network. Under wireless security, go to WPA personal from the drop down menu. When you make your password, make it very challenging. He recommends just banging your hand against the keyboard, as long as ...
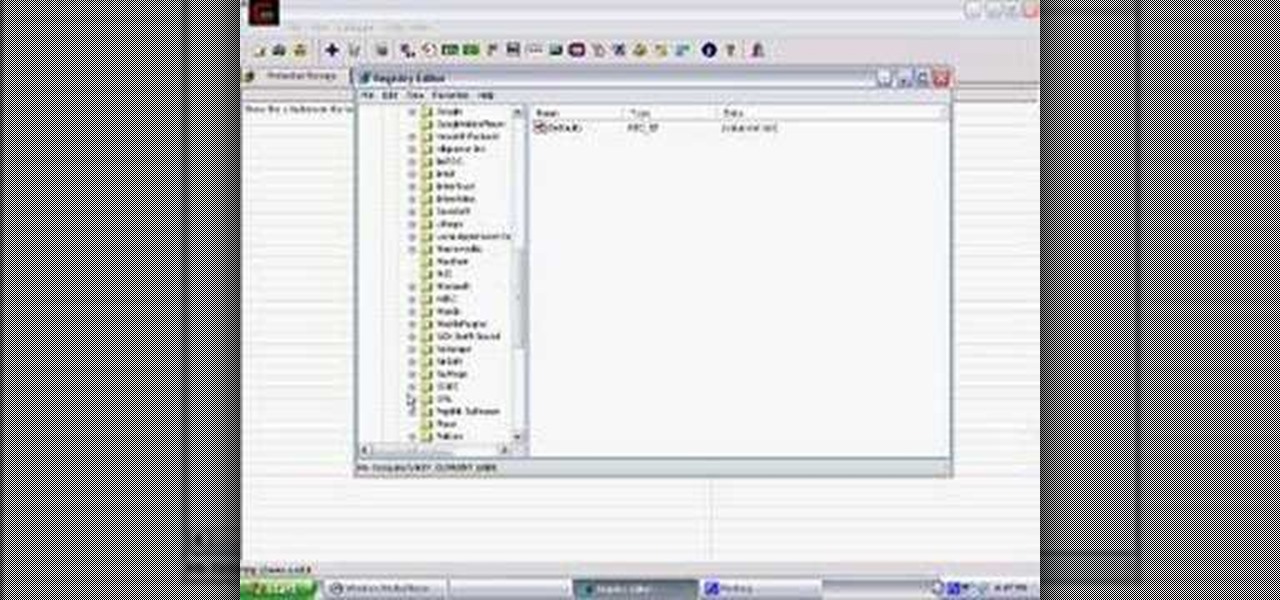
Hack a network computer by decoding Virtual Network Computing (VNC) hex passwords with Cain.
Watch how to configure LDAPS Authentication on the BIG-IP Edge Gateway with BIG-IP LTM functionality. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.

This video shows you how to set up XBox Live using a laptop and Ethernet cable. The materials you will need are an Ethernet cable, an Xbox 360, and a laptop or desktop computer. First, you will need to connect your computer to your wireless network. Next, you must connect your computer to your Xbox 360 using your Ethernet cable. Power up your computer, go to the start menu and select network. In the window that appears, select the Network and Sharing Center located below the address bar. A ne...

In this video the tutor shows how to sign on to the Playstation network using Playstation 3. To connect to a Playstation network you will need a PS3 Controller and the PS3 itself. First signing on to the system, go to the System Settings. Then go to the network settings and you will need to configure your internet settings as shown in this video. It shows the different ways connecting to an internet like in custom mode or advanced mode, also the wired or wireless option. Finally after connect...

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...
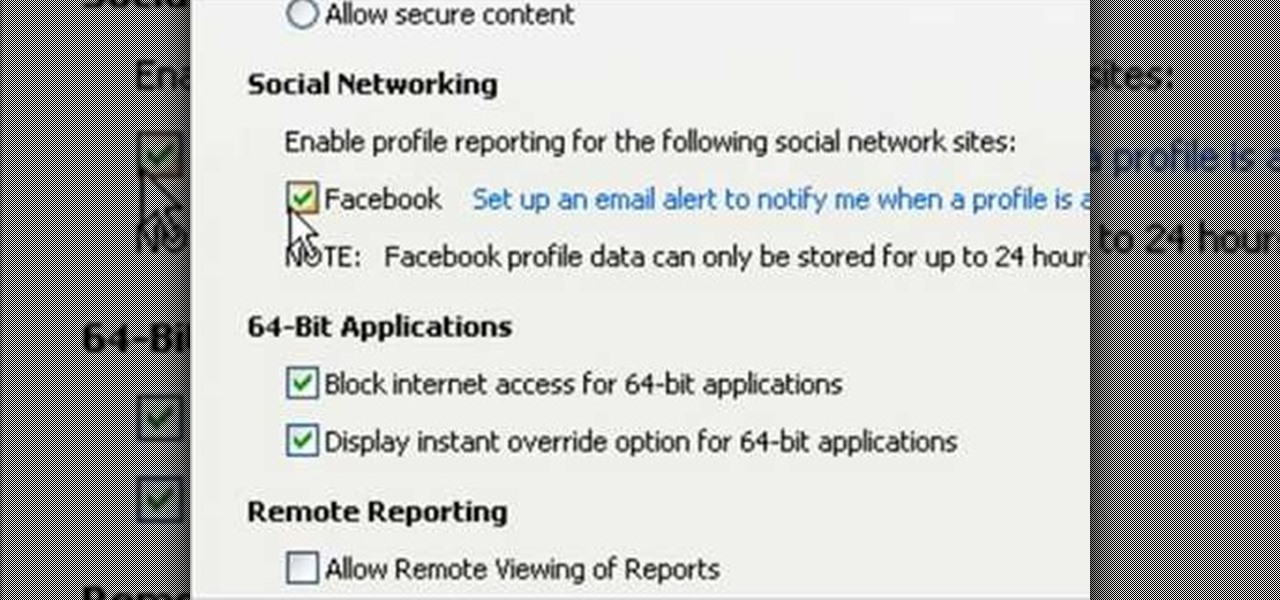
Danny with Top Ten Reviews will show you how to monitor social network activity with the Net Natty program. This will be helpful for monitoring social networking accounts on websites such as Facebook and MySpace. First, open Net Nanny. Go to the dashboard and select Additional Settings under Filtering. With this section, social networking sites that have been used on the computer will be listed. You can check whichever account you want to monitor. Under the dashboard, go to Reports and select...
This video tutorial will teach you how to troubleshoot a HomeGroup network in Windows 7. In order to do this follow these steps: Go to the Start Menu and then go into Control Panel. Now go to Network and Internet and then in Network and Sharing Center. Now click the Troubleshoot Problems link located on the bottom of the window. Here you can select which part of networking you want to troubleshoot, in this case select HomeGroup. A process will start and you will have to answer the questions t...

There's a lot of talk about 5G these days. You might even think your iPhone is 5G-ready, since, well, it says so right in the status bar. 5G E, right? Sorry to burst your bubble, but no iPhone is capable of connecting to 5G networks yet, no matter how much you pay for that 11 Pro.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.
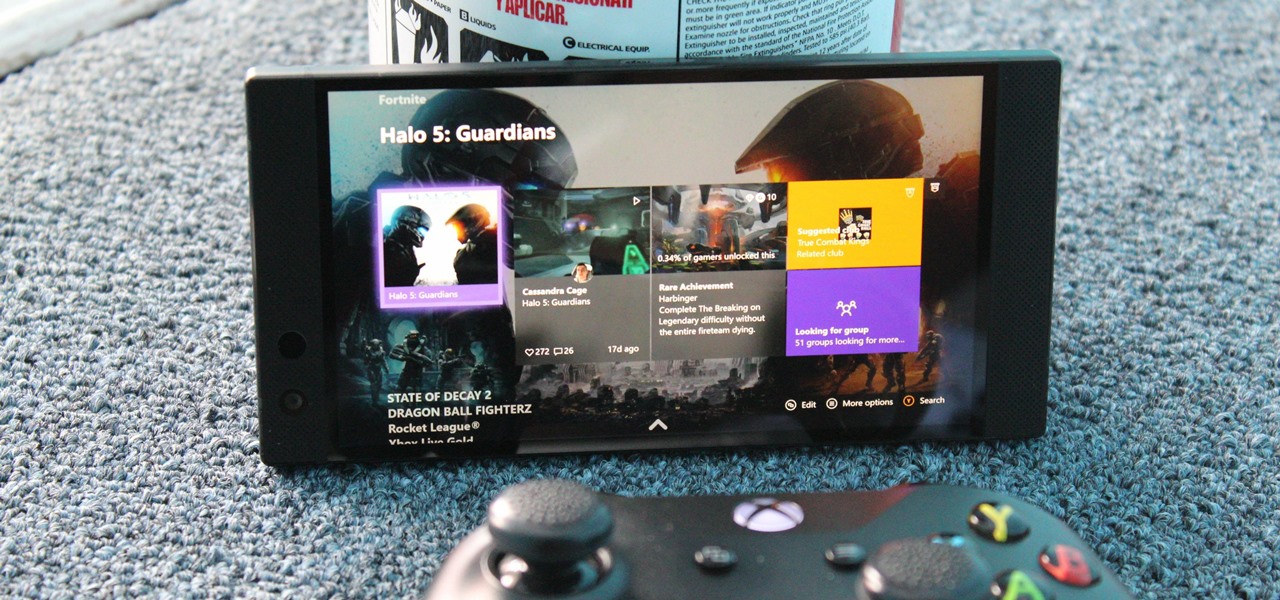
Game streaming has never been better. Not only can you watch your favorite Twitch streamer play, but with the new tools being added to YouTube, you can even play along with them. And now, with a solid internet connection, you can stream your Xbox One games to your phone to enjoy console games on the go.

While AT&T is gradually showing off the powers of its 5G technology in the US via the Magic Leap One, another major wireless company is doing the same in the UK using the world of fashion.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.