While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

When it comes to media players, few are more capable than VLC. With its extensive codec support, VLC is able to play almost any video file. Partly due to its open-source nature, features are constantly added. This trend has continued with a new update that added native Chromecast support.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

John Legere seems to operate under the philosophy of, "If you're going to be late to the party, throw a better one." On Tuesday, Legere announced T-Mobile's intention to build the nation's first true 5G network, following AT&T's rollout of its "5G Evolution" network. A network which many said was, to put it in polite words, nonsense.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Rumors have had Google making a foray into the mobile carrier world for quite some time, but today, the Mountain View tech giant finally made things official. The new service, dubbed Project Fi, will be a Mobile Virtual Network Operator, or MVNO, that uses existing Sprint and T-Mobile cell towers.

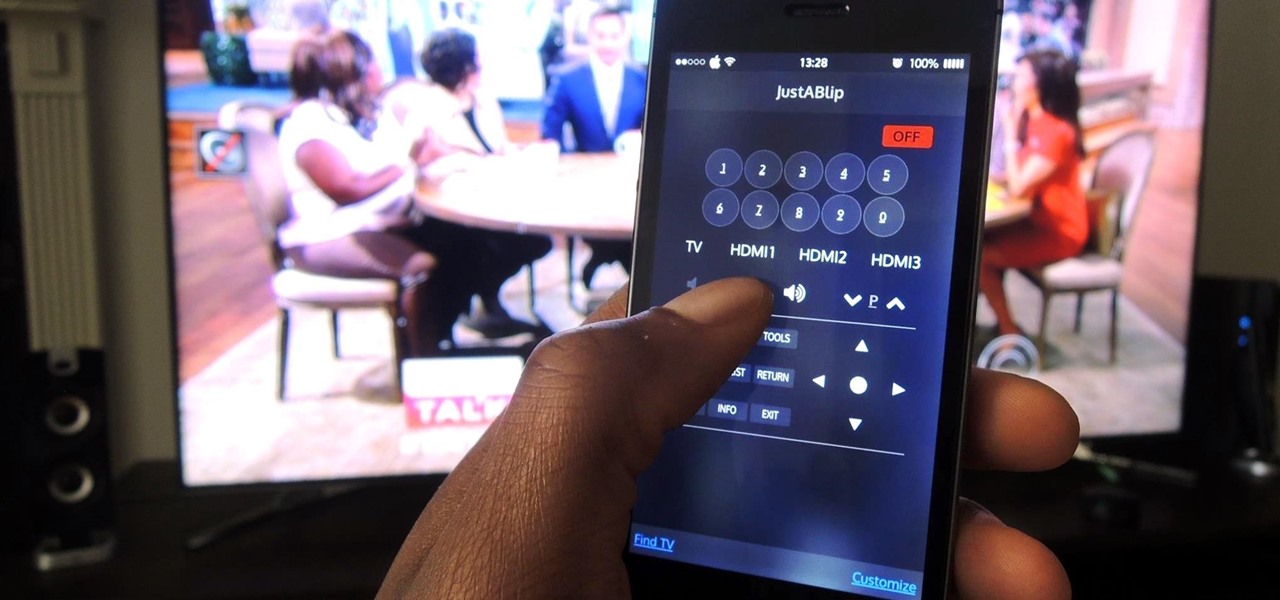
After I traded in my Samsung Galaxy S5 for an iPhone 5S, the one feature I truly missed was the Smart Remote app. My television remote was broken and the S5 saved me from, you know, actually having to get up and change the channel.

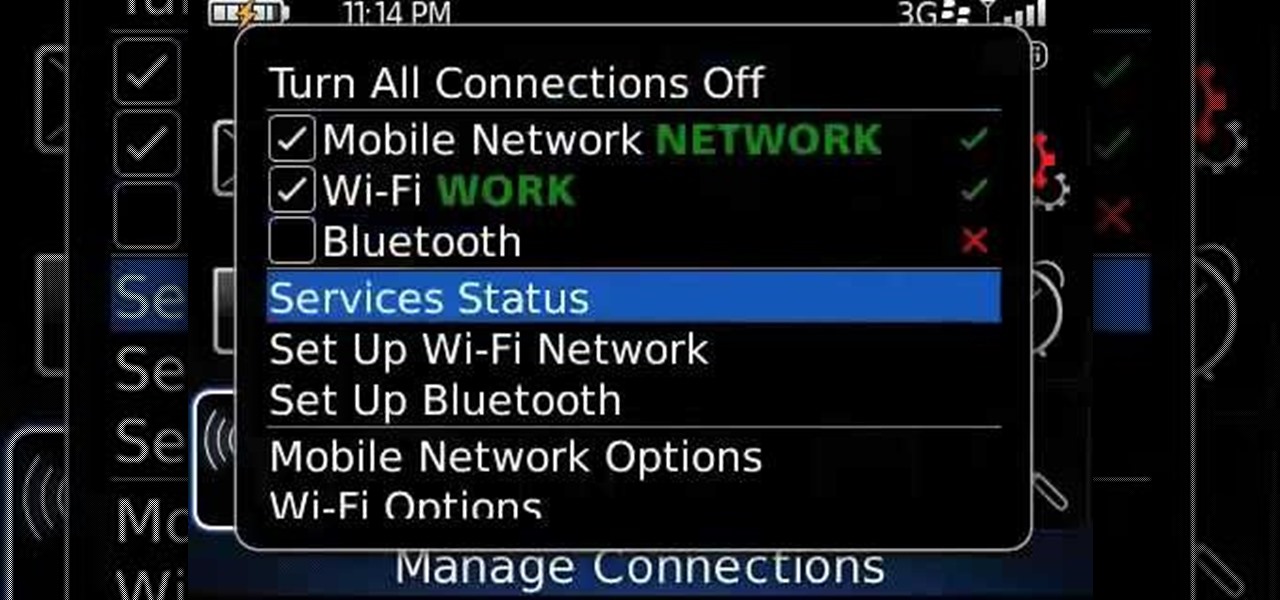
Learn how to manage your network connections through the Mobile Network Options pane on a BlackBerry phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Settling a new planet will decrease your pride ratio, because your population will increase when you're settling a new planet. If you're not sure how to even settle planets...

In order to spy and gain intelligence on your Conrohl enemies, you need to make an intelligence agency. Then you recruit your spies to perform simple espionage.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Learn how to update the software on your BlackBerry device over a WiFi or Wi-Fi network. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

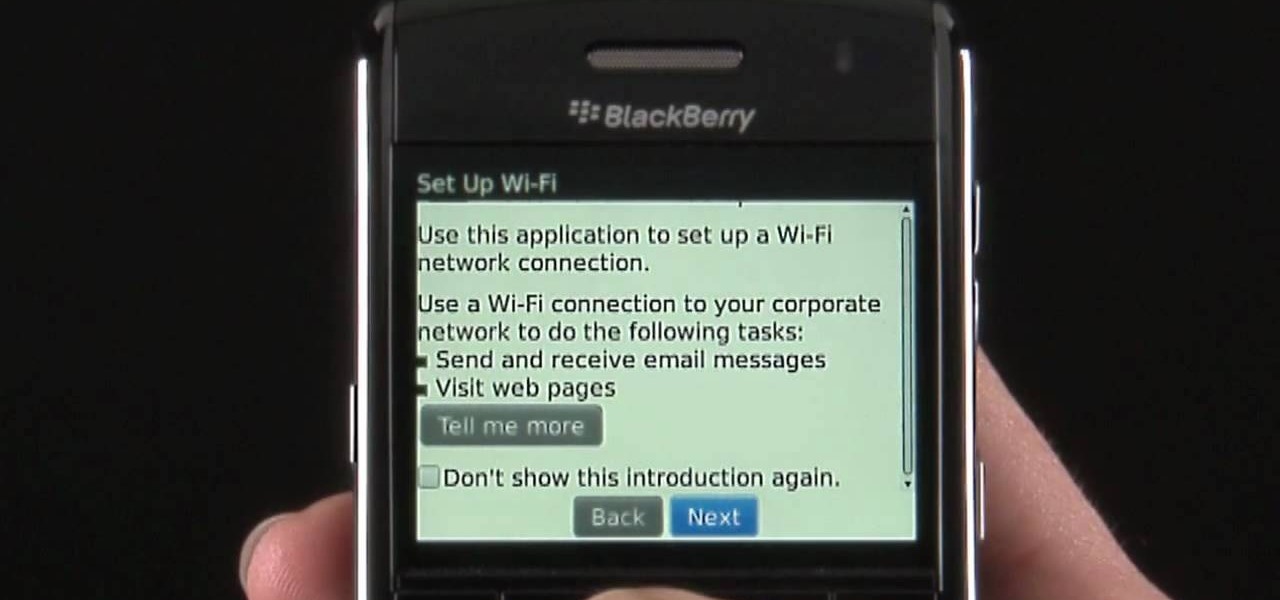
Learn how to discover and connect to close-by wireless (Wi-Fi) networks on your BlackBerry Pearl 3G. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

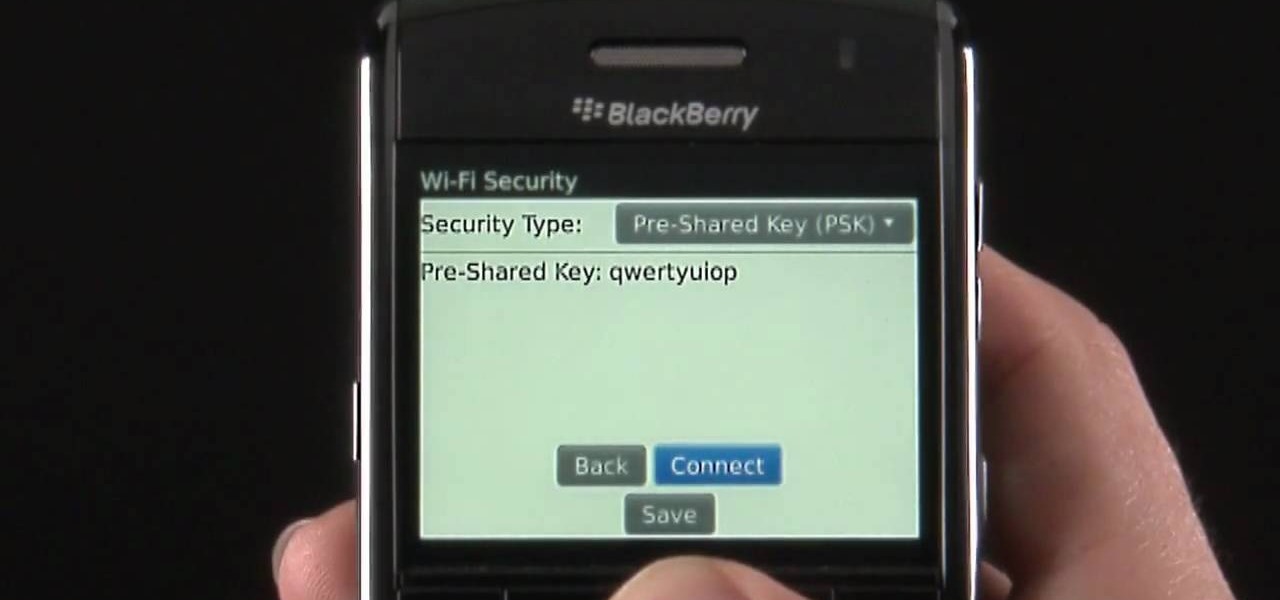
Learn how to force your BlackBerry Pearl 3G to connect to a specific wireless (Wi-Fi) network. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

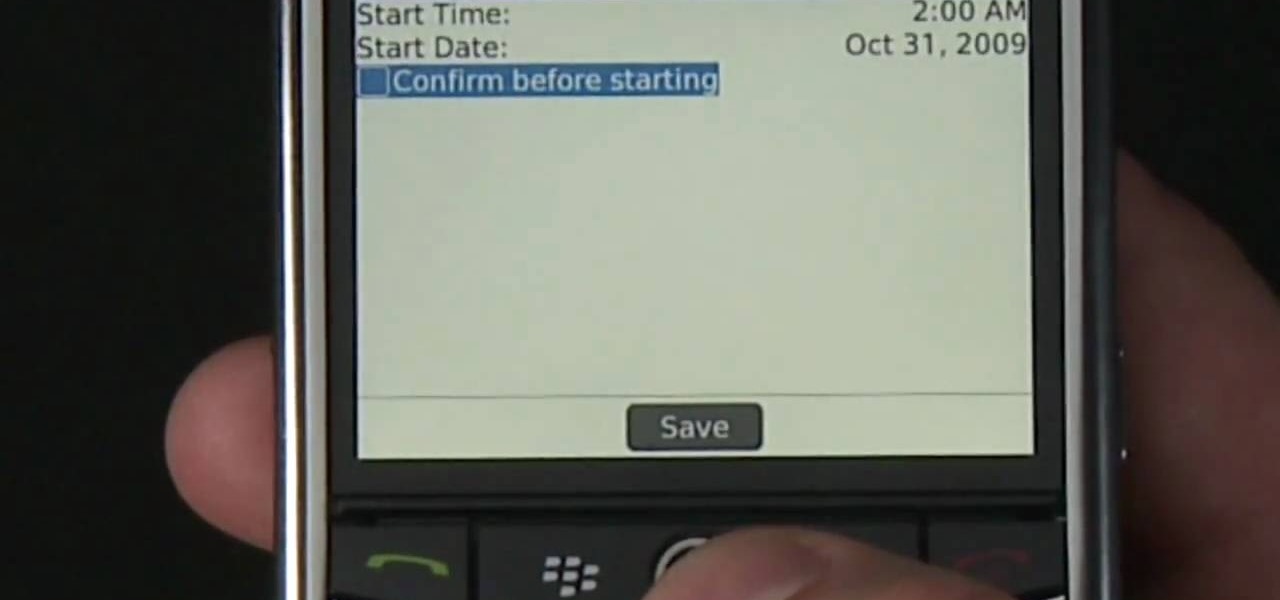
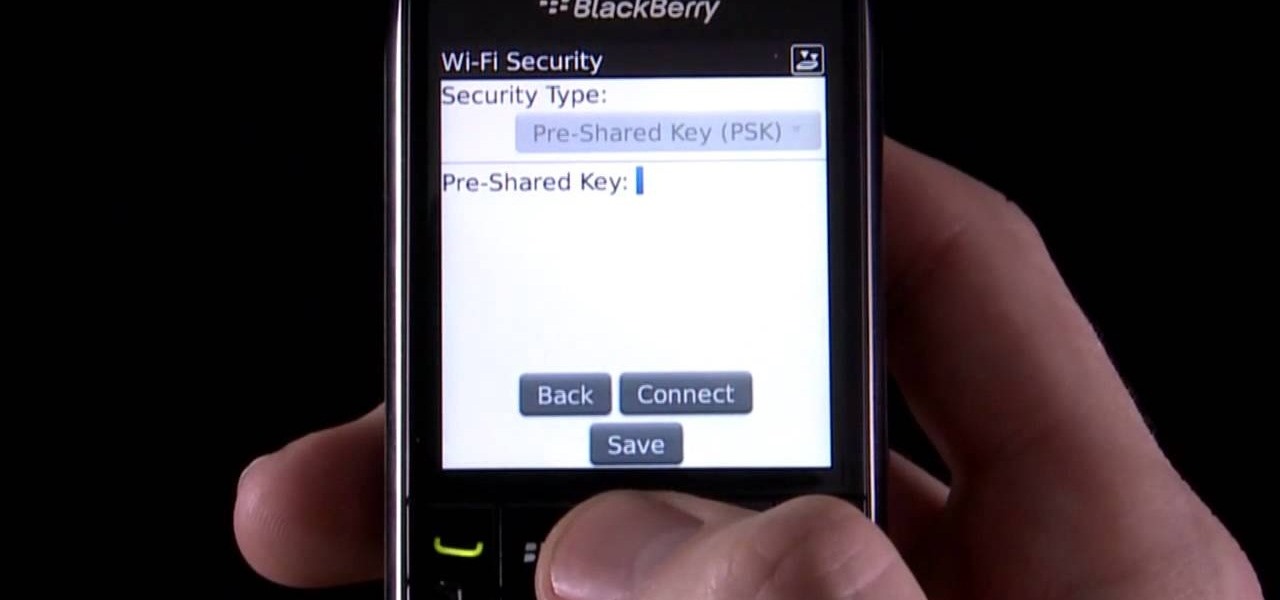
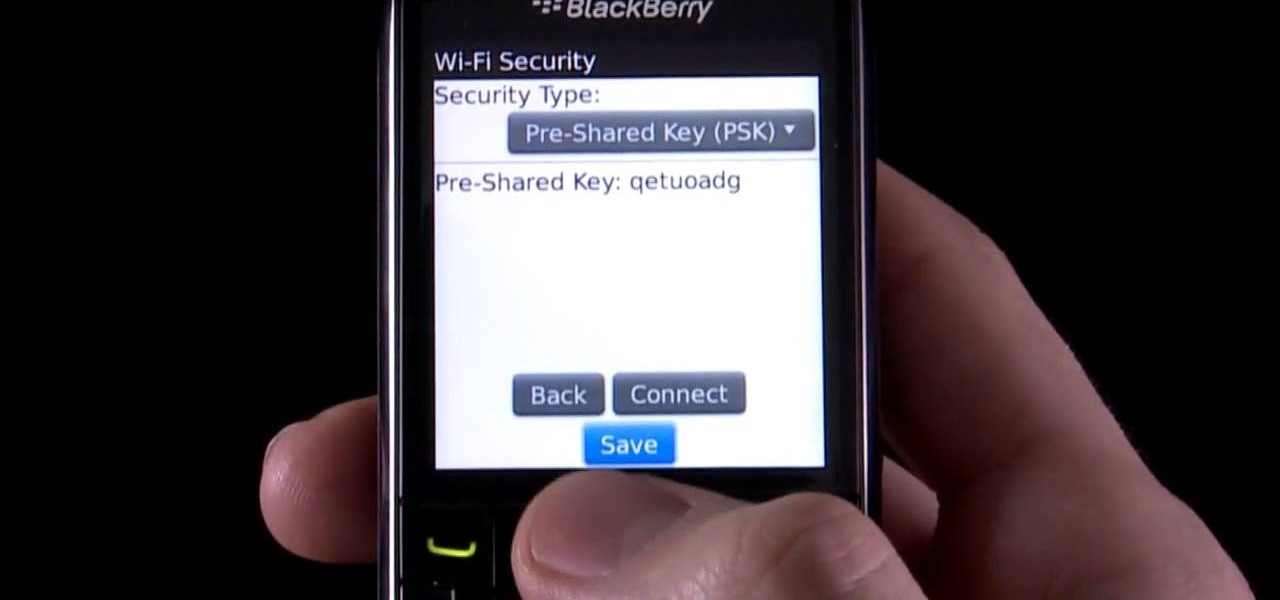
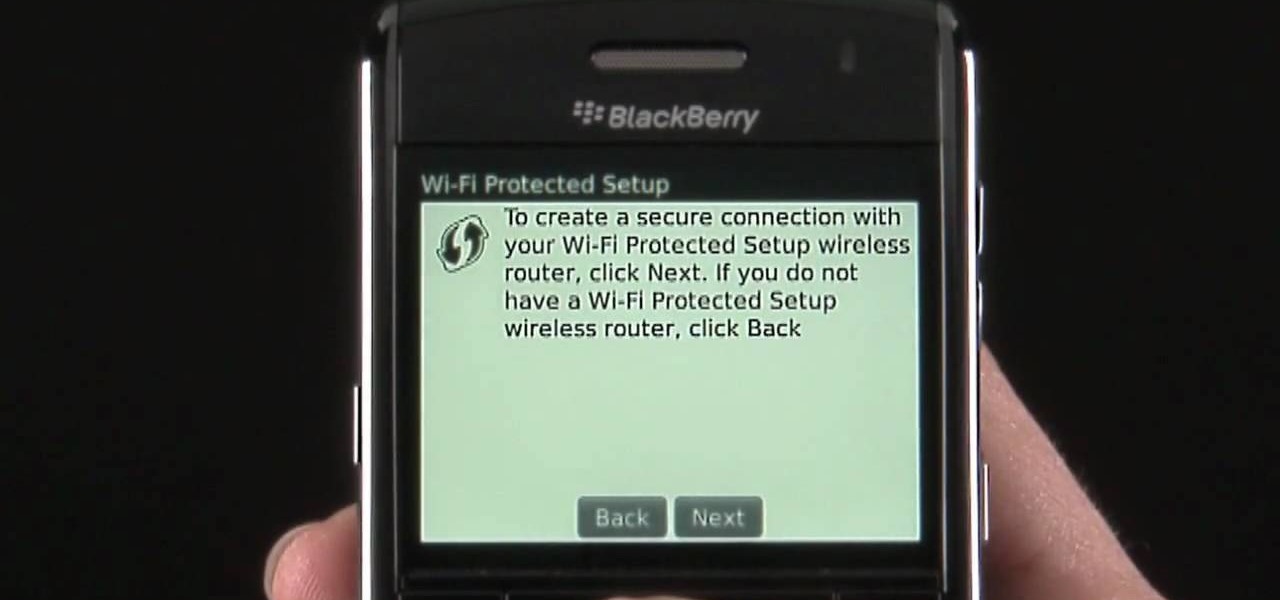
Learn how to use the Push-Button tool on your BlackBerry Bold 9650 phone to join a wireless network. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Learn how to find open wireless networks with a BlackBerry Bold 9650 phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Want to know how to manually connect to a wireless network on a BlackBerry Bold 9650 phone? This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

The XBox 360 is a big, beefy console that can perform all sorts of multimedia tasks. Did you know that one of its many abilities allows it to play media files from a networked PC? This video will show you how to connect your XBox 360 to a network PC with Windows Media Player 11 or higher and stream movies and music from the latter to the former. Now you're much closer to maximizing the potential of that expensive little console you've got there.

The Sony Dash is similar to an iPad and works like a PC without a keyboard. In this tutorial, learn how to connect your Dash to your home wireless Internet network so that you can go online and download updates. This clip comes straight from the pros at Sony and tells you everything you need to know about accessing WiFi on your Sony Dash.

This video shows you two methods to connect to XBox Live using a laptop. For the first method, go to your start menu and open up your control panel. In the control panel window find the area marked Network and Internet and select the option View network status and tasks. In this new window, select Change adapter settings in the left hand pane. You will be presented with another window that has your network connections listed. Right click on your Wireless Network Connection and select properti...

In this video the instructor shows how to map a network drive in Microsoft Windows XP. Network drive is similar to the disk drive that is present on your computer like C drive, D drive but instead of pointing to a hard disk on your computer it points to a server that has enabled shares. Shares allow you to create or edit files and folders. By mapping that server share to a folder in XP you can use that share as a normal drive. To do this go to start menu, right click on My Computer and select...

Veronica from Tekzilla teaches you how to monitor network activity on Windows 7. Go to ITSamples and download the Network Activity Indicator program. Install it and run it. This will add a new icon on your system tray. It blinks to reflect incoming and outgoing packets. You can right click to see a more detailed report. You also get statistics and a menu for your network and firewall settings. So to get the popular windows XP type network indicator icon all you need to do is follow the steps ...

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

Iphone is a innovative product from Apple, which can be used for many purposes. Some times even when using different applications and having a collection of music in your Iphone you may still be left with some space on it. Now you can use this space to fill it with other files which are not necessarily supported by the phone. Air sharing is a wonderful application which lets you drag and drop files into your Iphone. You can now browse it from any connected computer in your local network. So a...

In this tutorial, we learn how to map network driers from a remote server. First, go to run on your start menu, then type in the id address or server name for what you want to access and press enter. Now, right click on the folder you want to map and click on map network drives. Choose any letter you want from the drop down menu, then click next to the "reconnect on logon" text. Click on the finish button, then open your newly mapped network drive from your computer. You can do this for any s...

In this Electronics video tutorial you will learn how to tether a laptop to a Droid Smartphone for free Wi-Fi. For this you will need the android wifi tether application. Download the version for your device from here and install it. Then launch the app and press the icon to start tethering. In your laptop, go to settings and then to wi-fi. You will see a new network called android tether. Connect to the network and you will see that it works. As with any other network, you can change the nam...

We are now in the age of 5G. Carriers worldwide are upgrading their networks to the newest standard for mobile, which will dramatically improve your phone experience. How? By giving it download speeds and latency that surpass Wi-Fi. But before you upgrade, there are few things you should know first.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Similar to last year, LG is mixing up its releases. Instead of the G series in the first half of the year and the V series in the second half, LG is releasing both heavy hitters together. However, unlike last year, this is a true upgrade from its predecessor, the LG V50 ThinQ 5G.

Google's MVNO carrier, Project Fi, can save you a ton of money in the right circumstances, but it's always had a limited selection of supported phones. Because the service uses Sprint, T-Mobile, and US Cellular towers as its backbone, you could only use Project Fi with a Pixel, Nexus, or the Android One Moto X4 until now.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Even though your phone has a built-in media player, it's got nothing on VLC. The popular third-party video player supports virtually every codec and file format, and even better, you can use it to stream movies, shows, and other video files from your computer to your phone.

Say hello to the Sony Xperia T3, a light and slim Android smartphone—in fact, it's the thinnest 5.3" smartphone on the market.

In this tutorial, we learn how to set up and secure a wireless router. First, take your cable and plug it into your modem from your computer. After this, plug in an Ethernet cable into your modem to a wireless router. Now, plug the wireless router and modem into the wall. Now, look for the icon on your computer that says you have connected a new device to it. Go through the set up wizard to make a new wireless network, once it doesn't find one, connect a USB to the computer. Now, click on the...

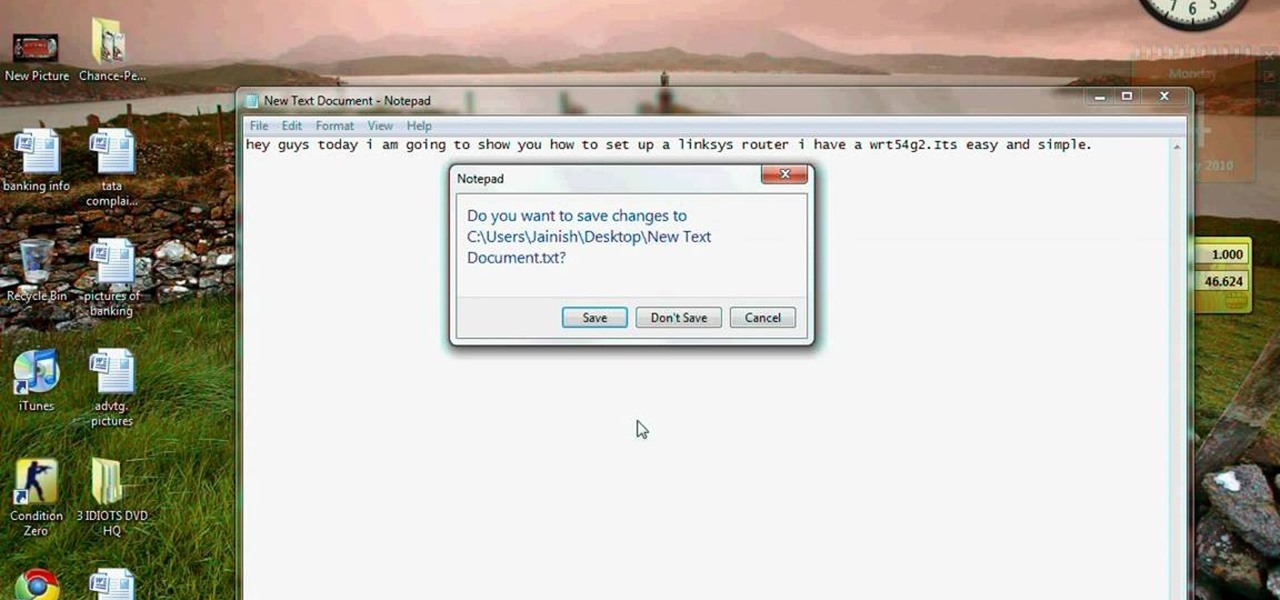
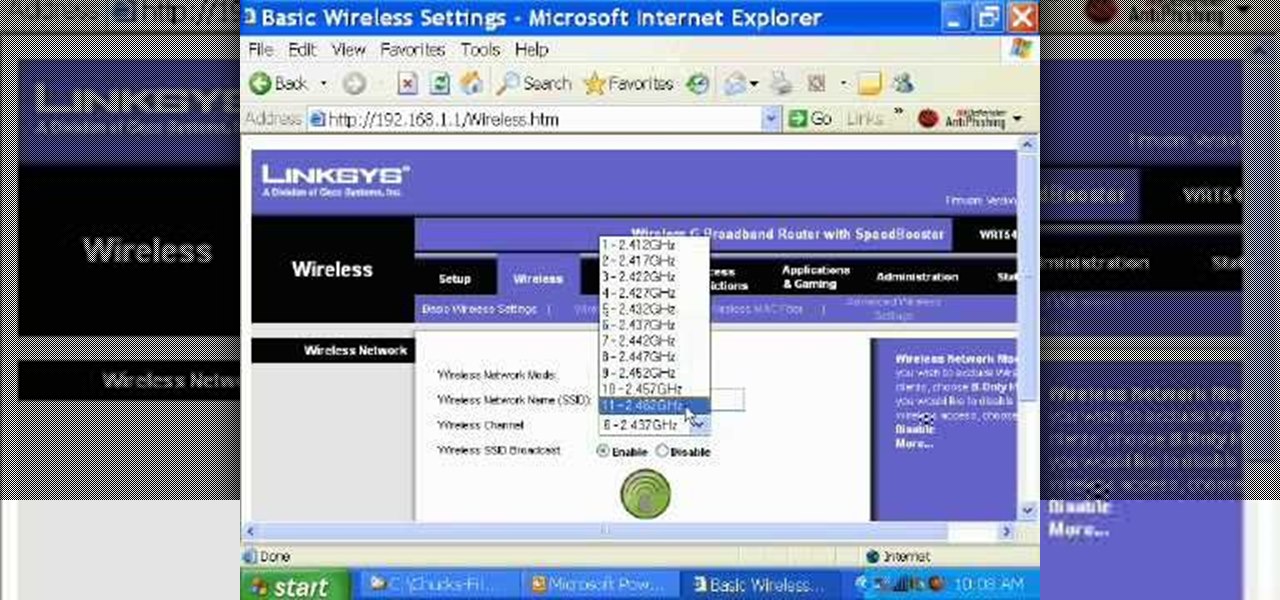
This video tutorial is in the Computers & Programming category which will show you how to set up a Linksys WR54g or WRT54g2 wireless router. First you connect to your Linksys router. Then go to http://192.168.1.1 and type in "admin' as your password in to log in window and click "log in'. then go to the "wireless' tab and enter your wireless network name. In the wireless channel select '11 2.462GHz' and click save. Next go to "wireless security' and type in the wireless network key. This is t...

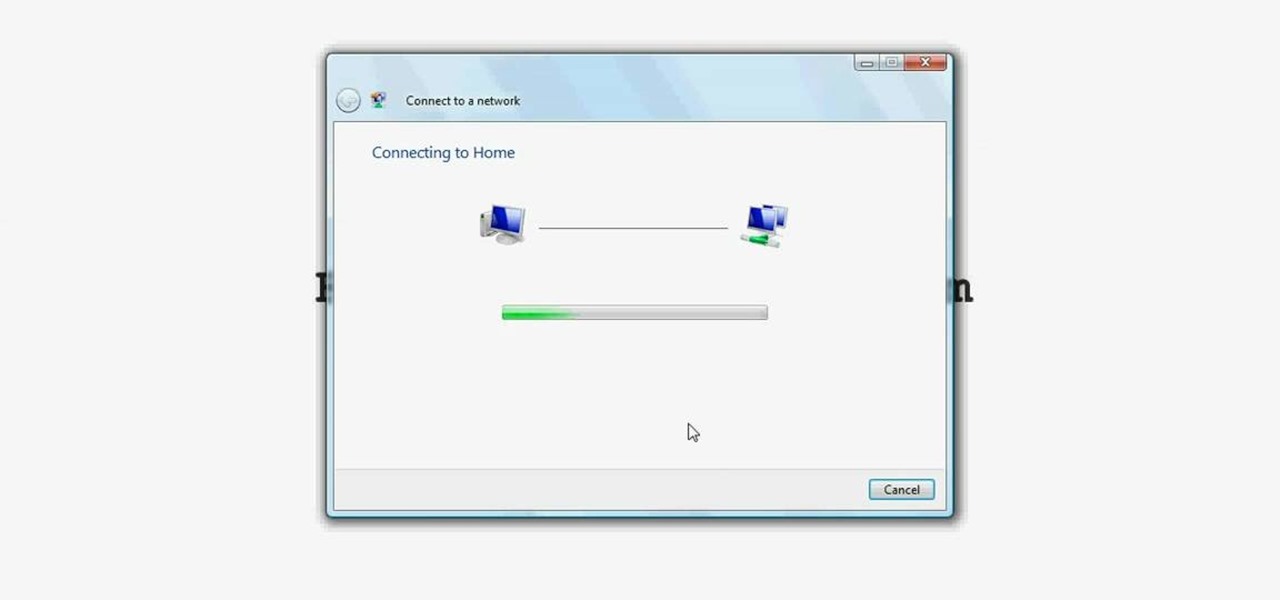
Wireless networks are really the only way to go these days. With WiFi you can access the world wide web from almost anywhere, at anytime, and not have to worry about annoying wires or cords. In this tutorial, learn how to set up a wireless connection in a Windows Vista based machine.

Ever had router trouble? Got router trouble? Well don,t worry the people over from quickcert.com have made this video to help! More specifically a linksys 802.11g router. All new routers come with a standard Ethernet cable, which must be plugged into one of the four ports on the router and connected to your computer as well. This is necessary to change settings, using Microsoft IE (internet explorer) when the routers IP is typed into the address bar. It is strong recommended to change the def...

Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.