This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it to a DVD. Now put it in a computer with a wireless card and restart the computer so that it boots to the DVD. When it boots up, type "startx" to start the interface. Bring up the command prompt and type in "/etc/init.d/...
If you're not much for office computers, and like using your own powerful PC at your workstation, then chances are, you're going to have to login to the network. Microsoft shows you how to quickly login and join a Domain or Workgroup in an office network.

In this video tutorial, viewers learn how to fix the Wi-Fi problem on an iPod Touch or iPhone. Begin by clicking on Settings and select General. Then scroll down to click on General and select Reset Network Settings. When a confirmation window pops up, click on "Reset Network Settings". The iPod device will then reboot. Now click on Settings and select Wi-Fi. Then select a network to connect to. This video will benefit those viewers who have an iPhone or iPod Touch, and would like to learn ho...
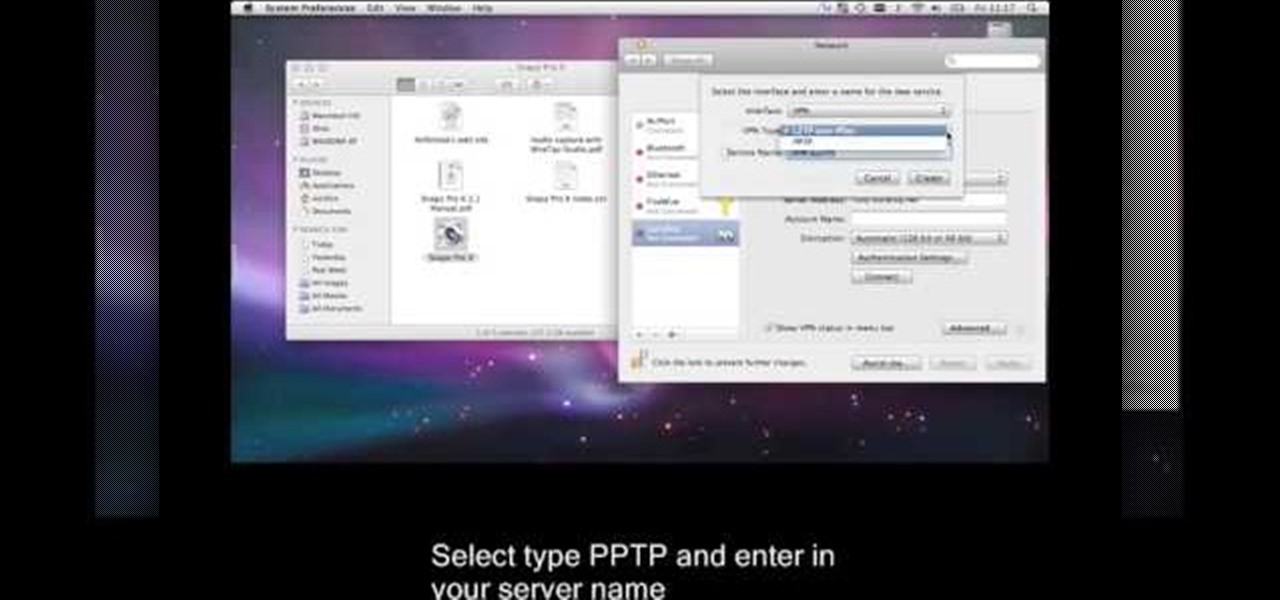
This is a video tutorial that is showing its audience how to set up your own VPN client on your Mac computer. The first step in setting up a VPN client is to go to your system preferences on your computer. Next select network and then select the plus button and type in that you will be making a VPN network. Next you should select the type PPTP and enter your server name. Then you can click on create and it will create a new network for you. Next you should enter your service address and your ...
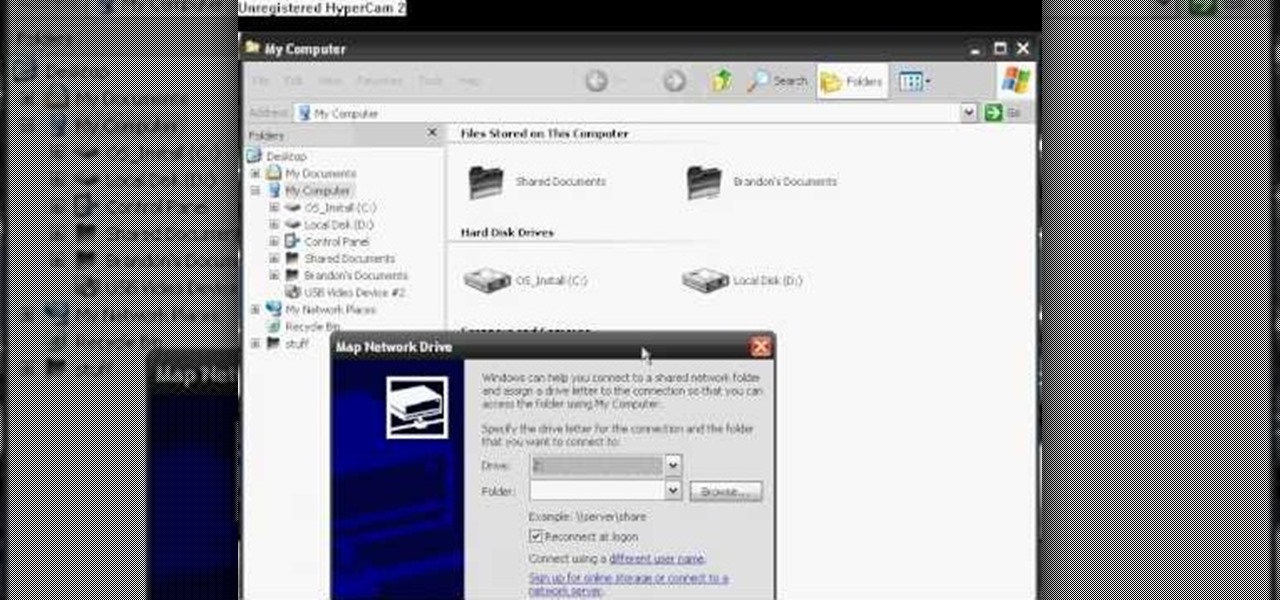
This tutorial will walk you through the steps you need to map a network drive for file access in Windows XP. By mapping your network drive you will be able to store and access files offsite and make computing easier all around.
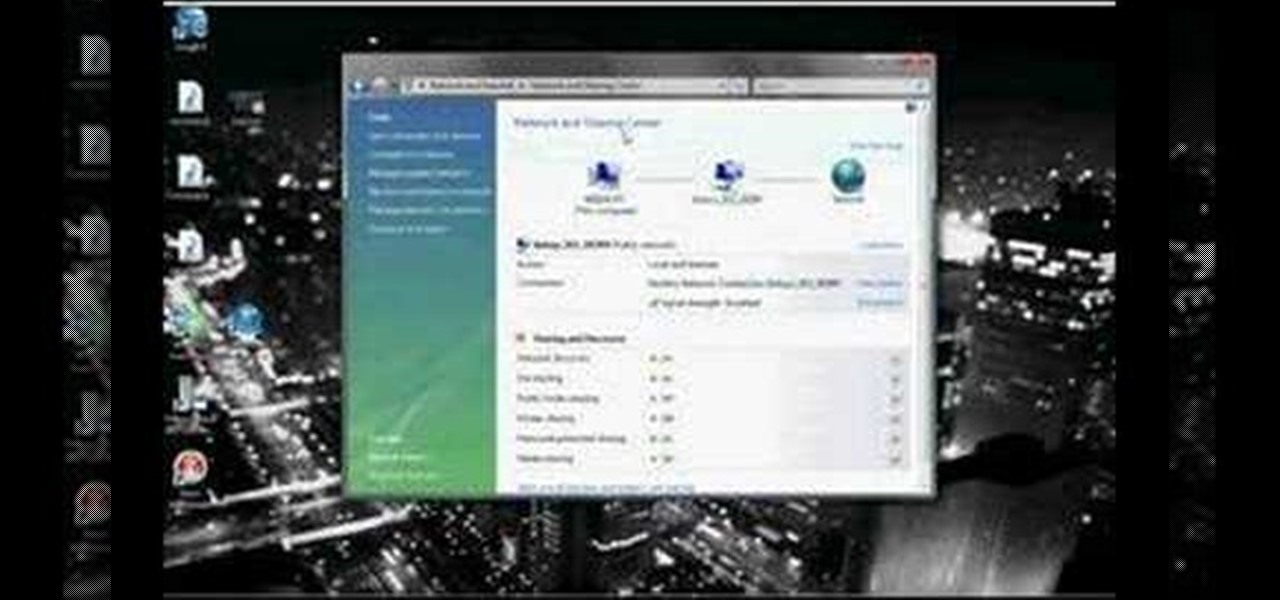
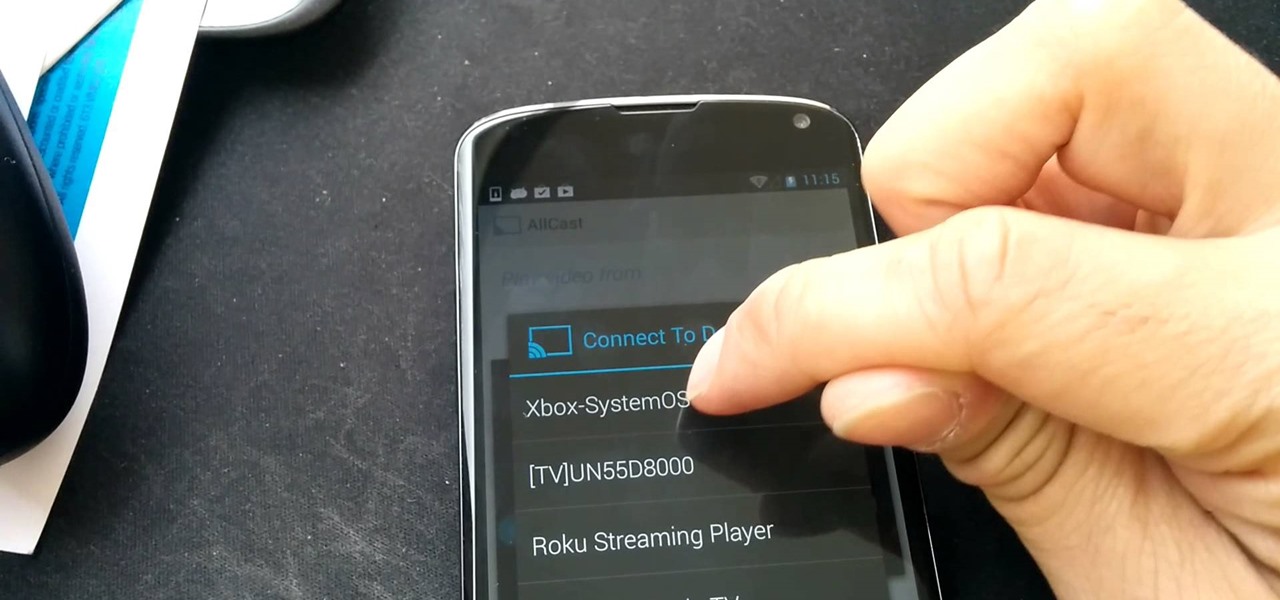
In this video tutorial, viewers learn how to connect an Xbox360 with wireless internet. Begin by connecting your computer to a wireless network. Click on the Start menu and select Control Panel. Go to Network and Internet, and select Network and Sharing Center. Under Tasks, click on Manage network connections and select your wireless connection. Right-click on the connection and select Properties. Go to the Sharing tab and check both the sharing options. Now click OK. This video will benefit ...

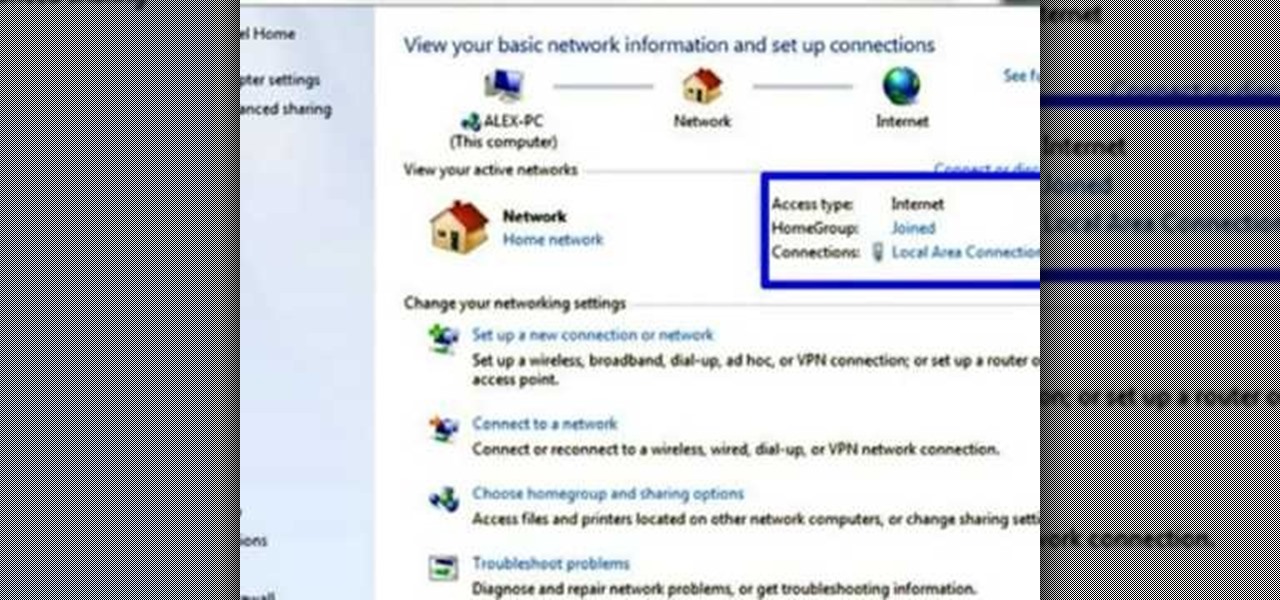
Want to access files from multiple computers at work or home? An expert from PC Remedies explains how to set up a Home Group network on Windows 7 systems. Includes a how-to of setting up your location, and managing the set-up wizard. Finally maximize your current resources by networking your work and entertainment files, as well as hardware such as printers. The excellent video gives you an exact snapshot of what you can expect to see on your own Windows 7 system. Includes advice on setting u...

Check out this video to learn how to get MMS on iPhone 3G for T-Mobile on 3.0 firmware. This works on T-Mobile's Network only!

This video tutorial shows how to get MMS on iPhone 3G for Tmobile on 3.0 or 3.0.1. Not that this works on T-Mobile's Network ONLY

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to obscure your OS fingerprint.

At first, it seemed like a clever art installation housed on the web, but now we're not so sure... the Newstweek hack may indeed be legit.

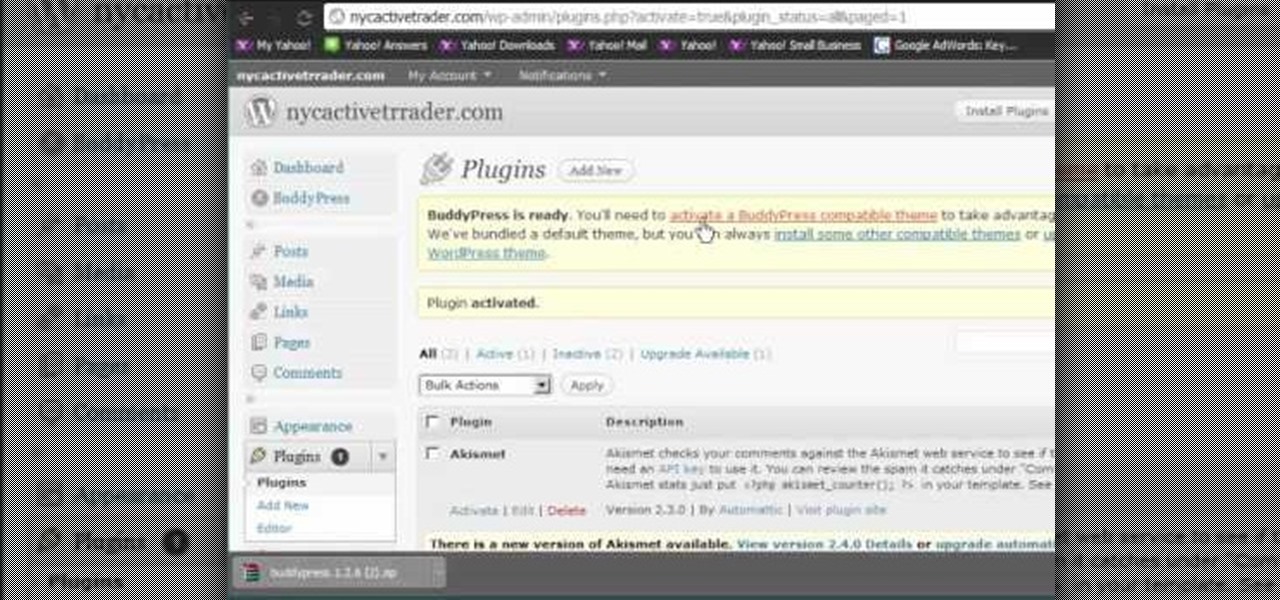
Like Facebook so much that you want to make your own version of a social network, just for you and your friends? It's totally possible, thanks to BuddyPress, a DIY social network for a tight community with the power of WordPress. This video will show you the steps to installing it and setting up your own social network.

Long-time packeteer Bob Bruninga, WB4APR, developed the Automatic Packet Reporting System (APRS), which allows packet radio to track real-time events. It deviates markedly from the usual message- and text-transfer activity. Instead, APRS concentrates on the graphic display of station and object locations and movements.

Lightweight rod support bracket from Long Valley Equipment mounts directly to front of the camera, saving weight and cost of other methods. Holds 15mm rods at 60mm spacing to support matte box, follow focus, remote focus, zoom motor.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

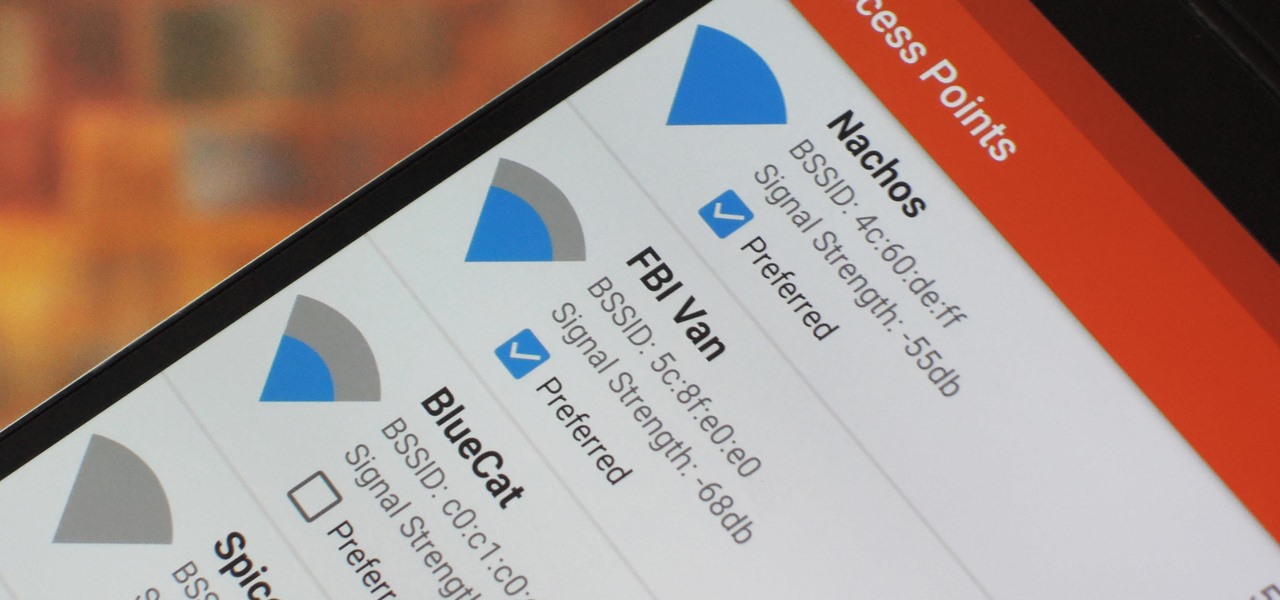
What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

The Shadow Brokers, a hacker group known for its dump of NSA hacking tools in 2016, has just leaked their remaining set of data which implies that the NSA compromised SWIFT, the global provider of secure financial services, to spy on banks in the Middle East.

Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly.

Seriously?! That's what a lot of people are saying when they found out that their Xbox One doesn't have a native streaming media player. When a new system is introduced and lacks features that the previous system had, it really pisses people off. The Xbox 360 allowed people to stream music and video files from a flash drive, as long as it was formatted with the Windows FAT32 file system.

You keep all kinds of important and sensitive information and data on your computer, and if your hard drives crashes, you're done for… unless you've backed it up. CNET has some "Insider Secrets" on how you can backup your system with an external hard drive, network-attached storage, and online services.

In this, the latest family-friendly recipe from the Food Network's Neely's, you will make garlic grilled lamb chops. These chops are irresistible and you will put them together from scratch. You won't have any leftovers after serving this great Southern style recipe. Enjoy!

What could be more perfect for a summertime barbecue than an All-American flag cake? This sponge cake is easy to make and covered in berries to give it a fresh, warm-weather flavor. If you need a dessert for Memorial Day or the Fourth of July, this is the perfect one for you. Start from scratch with the Food Network's Ina Garten, aka the famous Barefoot Contessa, in this clip.

The beauty of the iPod Touch is that it is not only for music. With the iTouch, you can access the Internet as well. You can use this Internet capability to download from iTunes, get e-mail, surf the web and many more options. In this tutorial, learn exactly how to turn your iPod on to a WiFi network so that you can take advantage of all the features your new device has to offer.

Ready to do some deep south cookin'? In this video, learn how to make fried mac & cheese with owner of Lady and Sons and Food Network's resident top southern chef, Paula Deen! ...And this isn't just any mac & cheese! This is mac & cheese wrapped in bacon and fried for a delicious crunchy finger food!

In this tutorial, learn how to make delicious French profiteroles for dessert with Ina Garten of the Food Network's Barefoot Contessa.

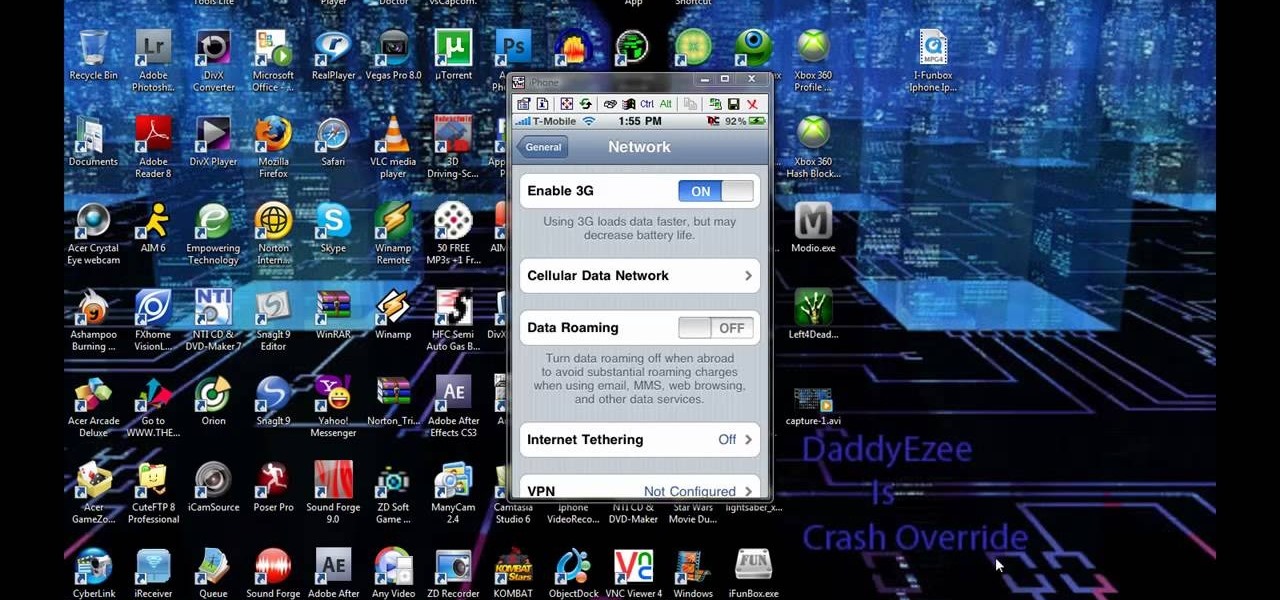
If you've already jailbroken your iPhone, but noticed that you are missing your cellular data network tab, check out this video. You will need Cydia, Winterboard, and be jailbroken on 3.0 of course.

Not 100% familiar with all the awesome features that make facebook a great storytelling medium? Check out this instructive how-to video from the cast.

Network sharing lets other iPhoto users view your photos and albums from their computers.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

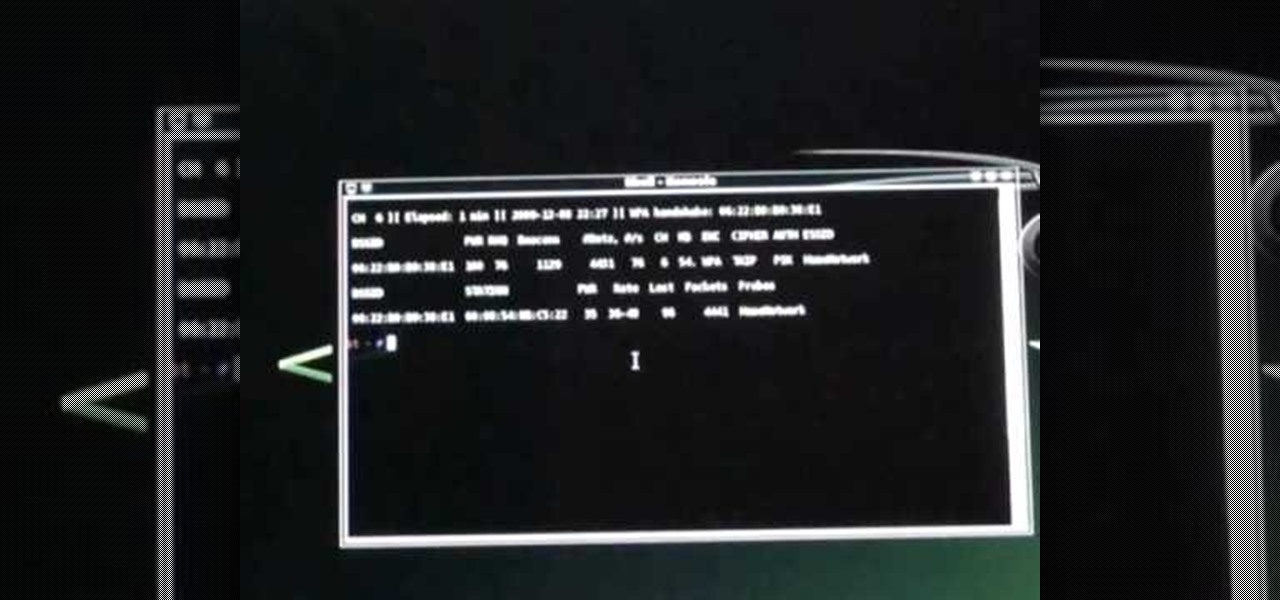
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...

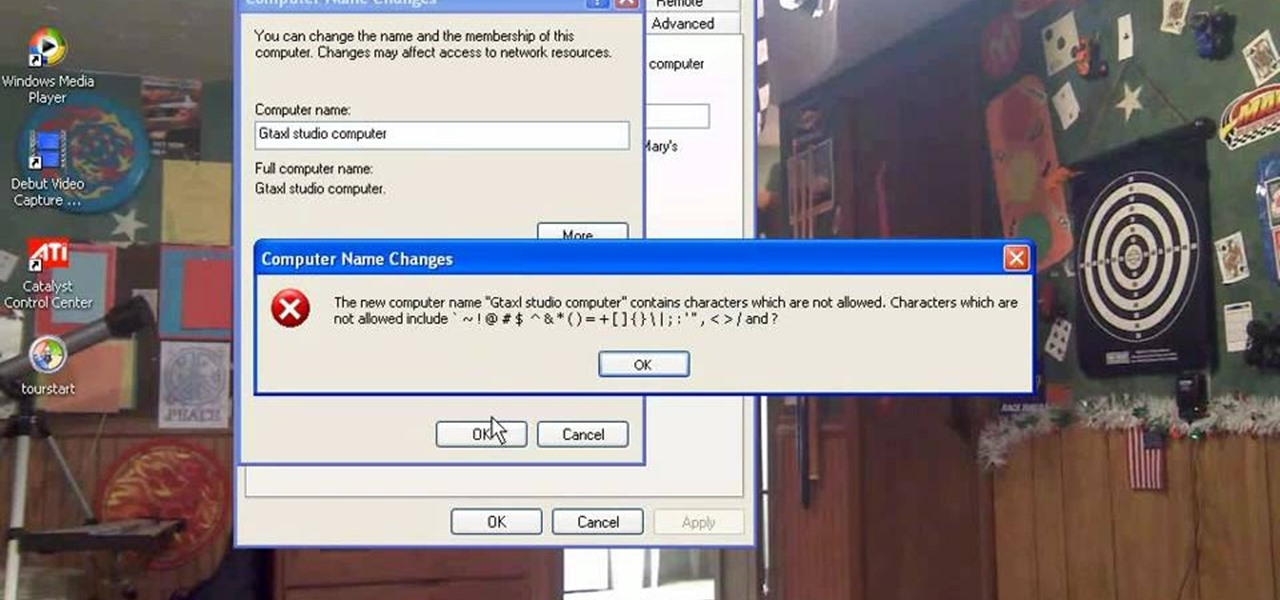
This how-to video explains how to changing the name of a computer, workgroup in a network and the description on a Windows XP.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to analyze packet captures and network taps.