Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Hi Elite Hackers! Welcome! to my 4th post. This tutorial will explain, how to extend a (hacked) AP's range with a wireless adapter. I made this guide because after hacking an AP it was difficult to connect to it (poor connection) and further exploit it. You can also use this:

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

At last month's I/O event, Google demonstrated a set of cool new features that were said to be coming to the Chromecast soon. While we may not be able to set custom backgrounds or cast content without being on the same WiFi network just yet, the biggest feature of them all has started rolling out to devices today: Screen mirroring.

Whenever a new version of a phone comes out, there's always that one cool feature you wish you had on yours. For me, that's Group Play.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

Whether you have AT&T, Verizon, Sprint, T-Mobile, or any other mobile carrier, chances are your smartphone is sold locked to only work on that specific carrier's network. Sure, you could unlock your carrier-subsidized device, but that would mean breaching the Library of Congress' latest Interpretation of the Digital Millennium Copyright Act—making the whole process illegal. As softModders, boundaries and regulations are things that we don't take lightly, although many times we have to begrudg...

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

Early last month, Sony released PlayStation Mobile, bringing PlayStation games to the PS Vita and other certified phones and tablets. The list of certified phones isn't as extensive as it should have been, consisting of only Sony devices (a few tablets and Xperia) and a couple of HTC ones. For anyone with a supported device, you can head over to the PS Store for the download and installation instructions.

Stay secure on public wireless networks by making your own FREE virtual private network (VPN). This tutorial shows you how to set up an OpenVPN server and connect to it from your laptop.

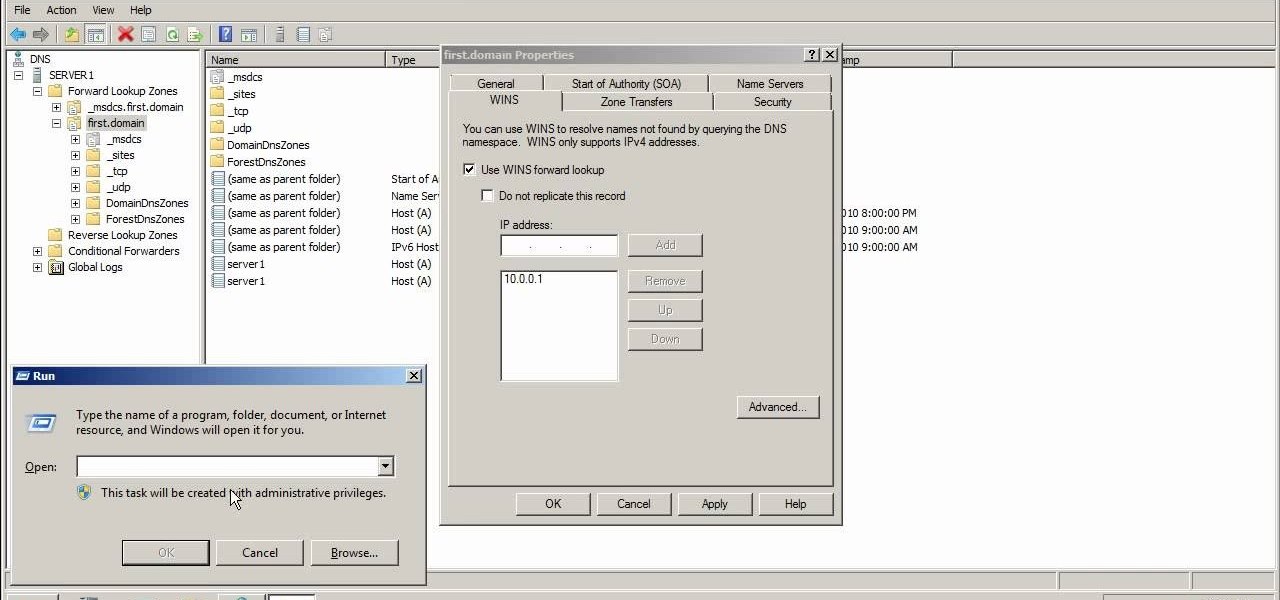
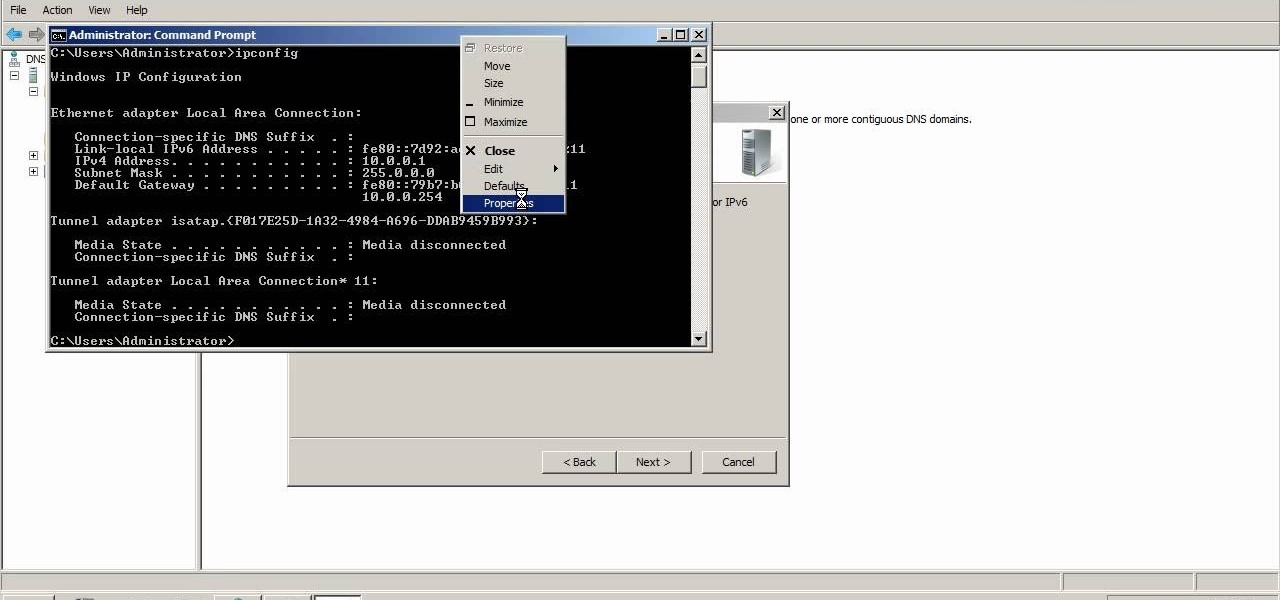
This video explains how to modify your DNS server to perform WINS lookups. Using Microsoft Windows Server 2008, you can perform WINS lookups across several networks which can resolve to a common resource. While Server 2008 cannot act as a WINS server, Server 2003 can.

A reverse lookup zone will allow you to translate IP addresses to fully qualified domain names (FQDN). This can be a tremendous help against phishing in large organization. Keep your network secure by creating a reverse lookup zone in Windows Server 2003 or 2008.

In this tutorial, you'll learn a few standard methods for resolving less common and more complicated wireless network problems. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

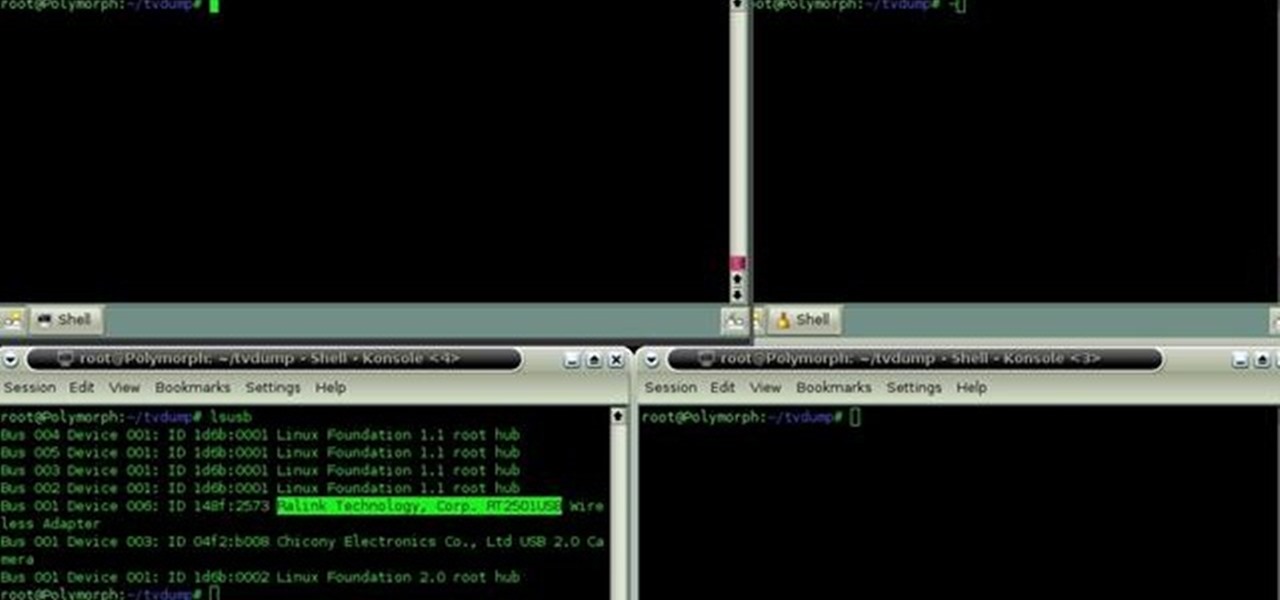
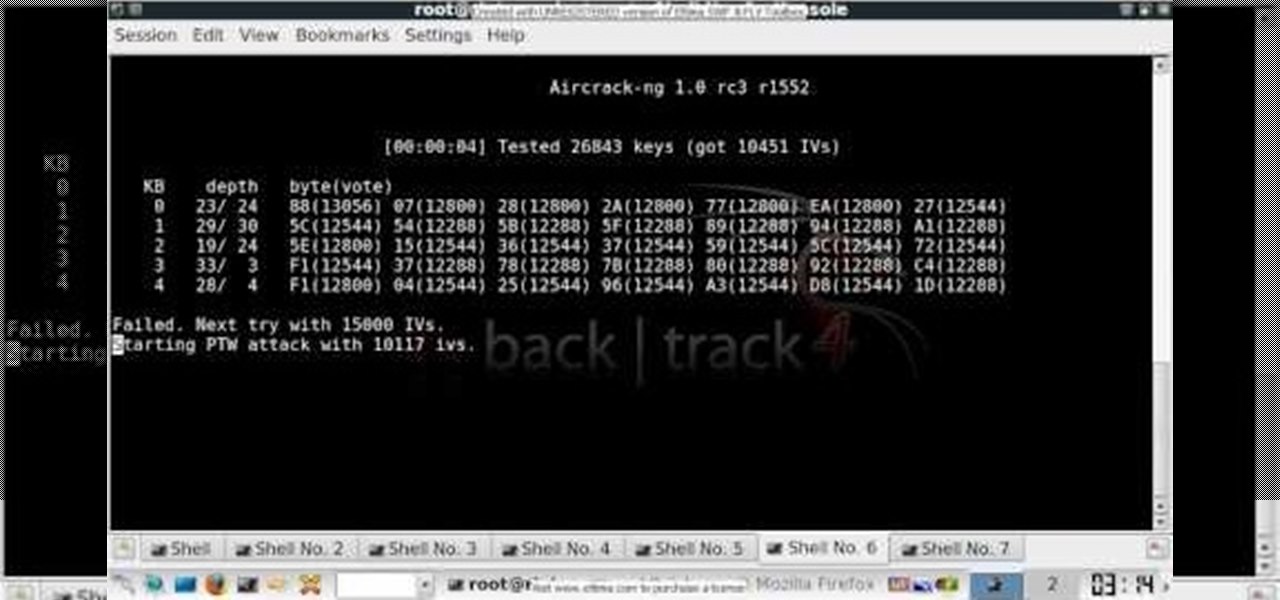
Learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a 64-bit WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to crack a WEP or WPA key on a GNU/Linux computer with GRIM WEPA. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

In this clip, you'll learn how to use the Backtrack Linux distro and the Aircrack-ng WiFi security app to crack a WEP key. The process is simple. For more information, including step-by-step instructions, and to get started testing the security of your own WiFi networks, watch this hacker's how-to.

The iPhone has always has one very big problem: that it is tied to AT&T. AT&T is a terrible network, and many iPhone users out there are probably dying to switch network but keep their awesome phone. Well now they can! This video will show you how to unlock you jailbroken iPhone 4, 3GS, or 3G using a program called Ultrasn0w, leaving it ready for use on any cell carrier in the country. Except Sprint, they don't have SIM cards.

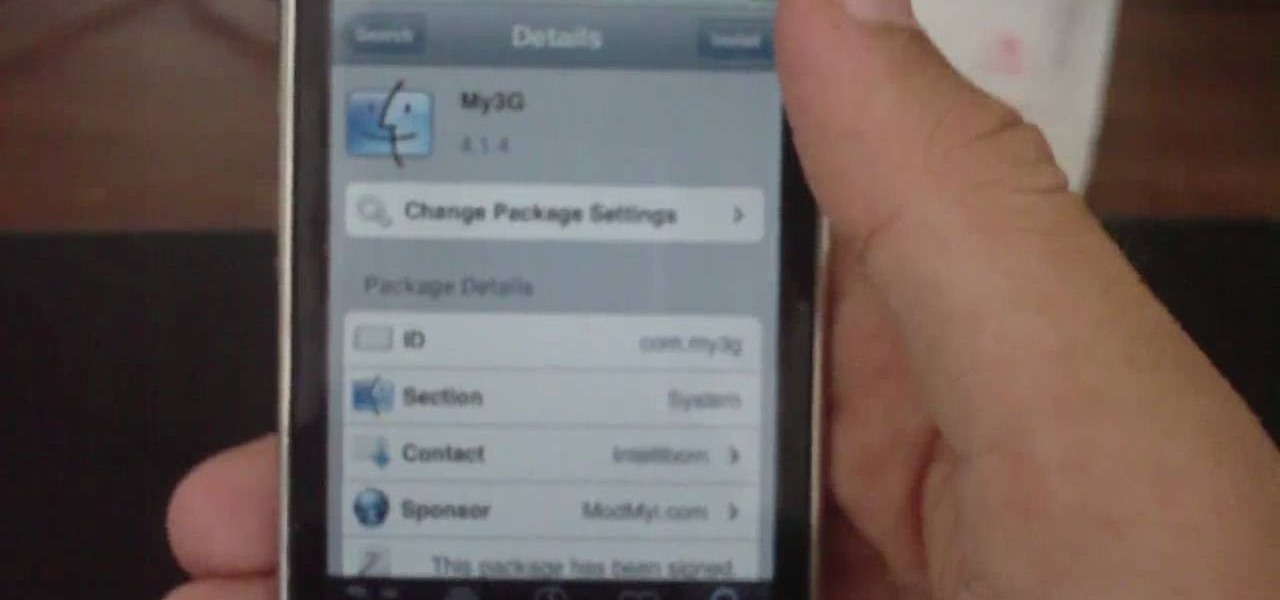
FaceTime is a very cool Apple App that makes video chat possible on the iPhone, but only if you're on a wifi network. Officially, at least! One of the many cool things that you can do after your jailbreak you iPhone 4 is use FaceTime on the 3G network! This quick video will show you how to enable Face Time 3G use using a jailbreak App called MY3G.

We all want to put our best face forwards on our social networking profiles. Facebook, MySpace, Twitter and all the rest are the best places to show great photos of yourself. You never know who might be looking. Employers, potential suitors, ex-high school classmates.. they are all snooping to see what you're doing and how you look these days.

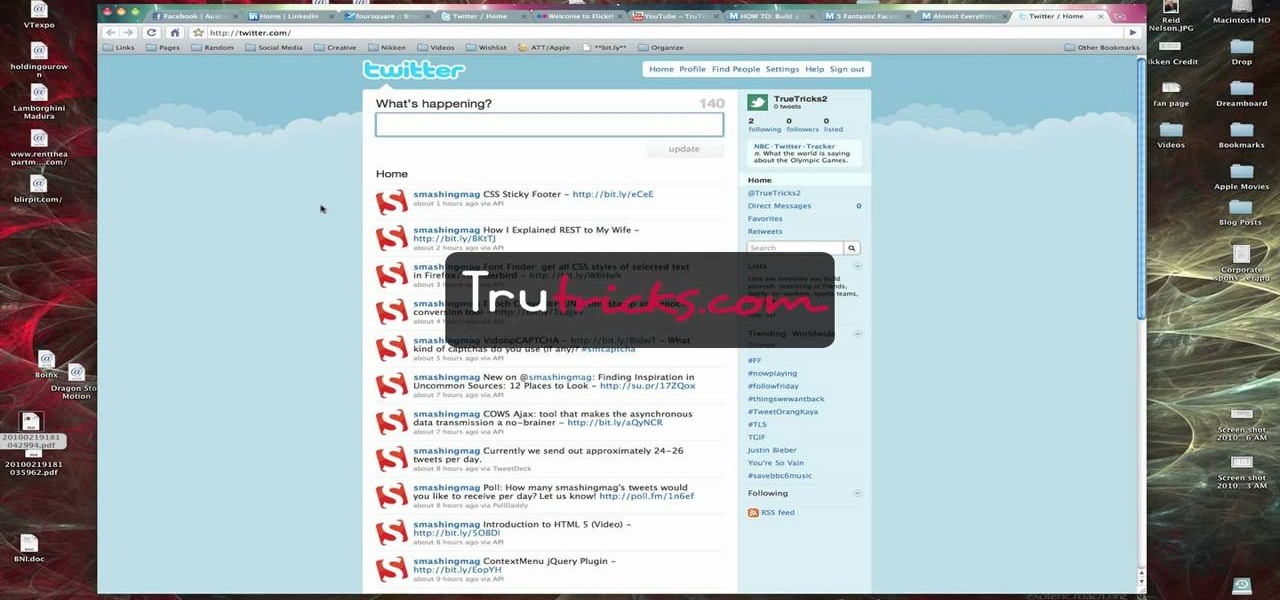
Brian explains us how to use Twitter, one of the best social media networks out there. One thing to notice is that Twitter allows you to send text messages up to 140 characters. In the right corner you can see you account name and your avatar which can be changed from the settings menu. Twitter allows you to follow people and be followed by people. Basically when you follow people you will be able to see messages they post and when people follow you, they will see what you post. Twitter is a ...

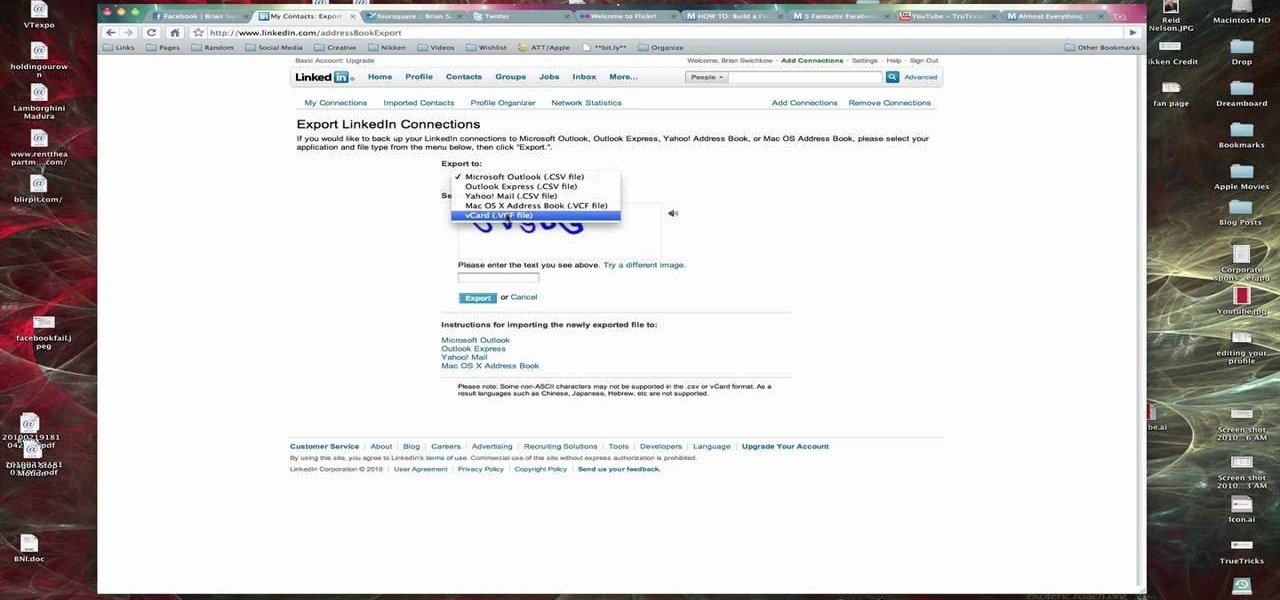
In this Computers & Programming video tutorial you are going to learn how to export LinkedIn contacts to an address book. LinkedIn is great for keeping your contacts in your professional network. To export your contacts go to home page and click on ‘contacts’. Now your full network of contacts will be displayed. On the right hand bottom, click on ‘export contacts’. On the next page select where you want to export the contacts, type in the security code and hit ‘export’ and all the contacts wi...

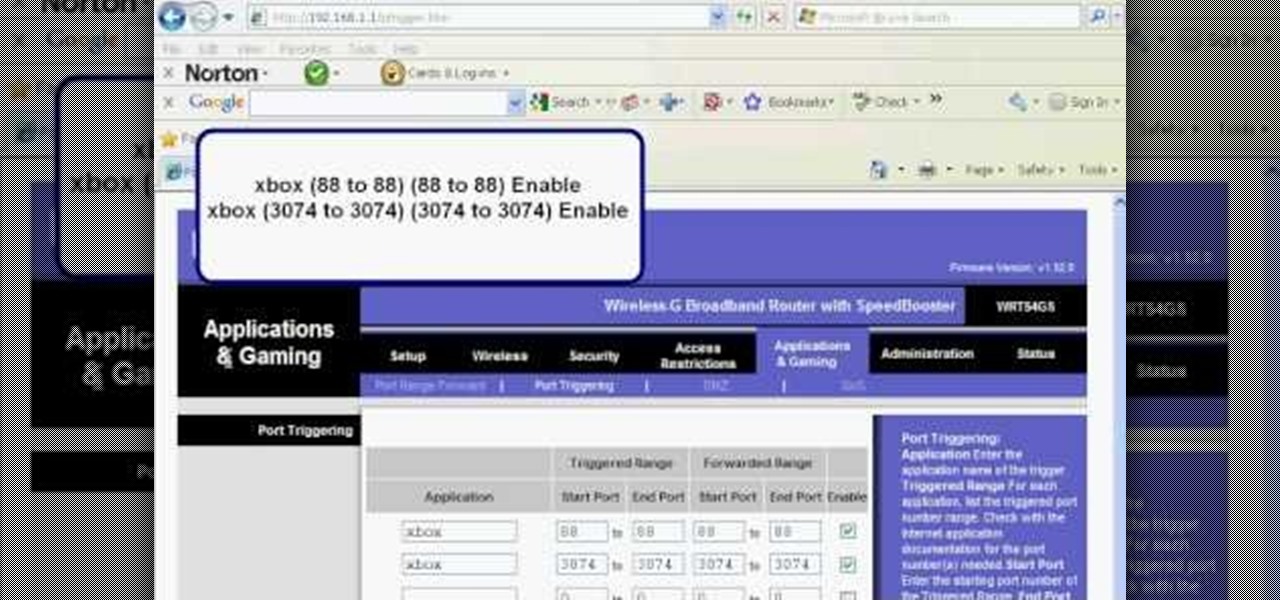
Before you can use Xbox Live 360, you'll have to allow your console to use certain ports that, by default, it may be blocked from using. One way to open up those ports is with port triggering. This helpful home networking how-to will walk you through the process of getting triggering set up in your own wireless router.

Elie Krieger from Food Network bakes up a scrumptious chicken pot pie. Her version will give you a healthy boost because she added extra vegetables and cut down on the fat. This southern dish is sure to warm up tummies everywhere and you can customize the ingredients based on your family's tastes. For example, you may want to use turkey instead of chicken, or possibly beef. Maybe your family likes different vegetables. This particular recipe uses chicken, onions, carrots, celery and green bea...

Take a look at the first place winner's tutorial on making a dress out of old tees for the Generation-t tee recon contest! Follow along with the steps in this fashion design video and make your very own quick and easy dress.

Overcome hardware differences in just a few simple steps- share files between your mac and PC and make your network truly seamless.

Use an old PC that has been setup as a server to perform helpful tasks such as backing up computers on your network, storing media files in a central location, share one printer with every computers computer in the house.

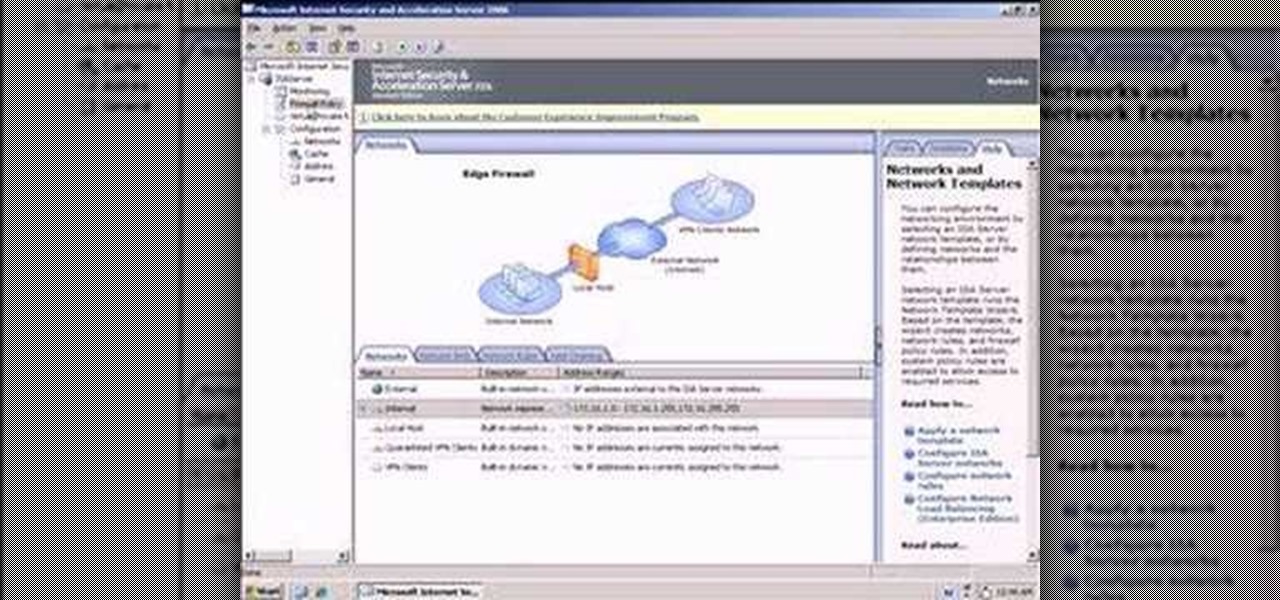
So what exactly is ISA Server? ISA Server, which stands for Internet Security and Acceleration Server, is Microsoft's software-based firewall, proxy, and web caching service/product. Now what does all of that mean? This video helps explain it!

Garret Brown's original Steadicam® is an icon that revolutionized filmmaking. Being the first and the best, it naturally and justifiably commands a premium price. It is for this reason that homemade DIY Flying Camera Supports have been around since at least 1977, just one short year after Mr. Brown's invention. With this tradition in mind, learn the two fundamental principles behind the Steadicam and how to build your own Flying Camera Support by watching this video filmmaking tutorial.

Want to hack a LAN? Well, hacking local area networks is easier than you'd think. And by watching a few short videos, you can become a master hacker, something every techie wants to achieve. And what's the best way to hack a LAN? Ettercap, a password sniffing program.

In general, hacking and information security is not just one discipline, but a number of them, and today we will look into some of the networking concepts.

Learn how to set up an Epson printer wirelessly when you bring your new printer home you will want to start by installing the software that came with the new printer. You can set up your printer to work without wires and it will print from all over the house. There are 3 ways to set up the printer including the Epson way, with cables, and WPS. To determine is you need to use WPS, which is more complex, check your router to see if it has a sticker on it that says Wi-Fi Protected Setup. If that...

In this tutorial, we learn how to get additional codec support in iTunes. It's not easy to find this support online, but if you go to Xiph, you will be able to find what you need. This site has tons of things to download to give you codec support on your iTunes. If you don't use this, you will have to use a different player to watch many things, because apple doesn't support many different file types. If the program stalls, just wait for it to load or you can uninstall and re download. These ...

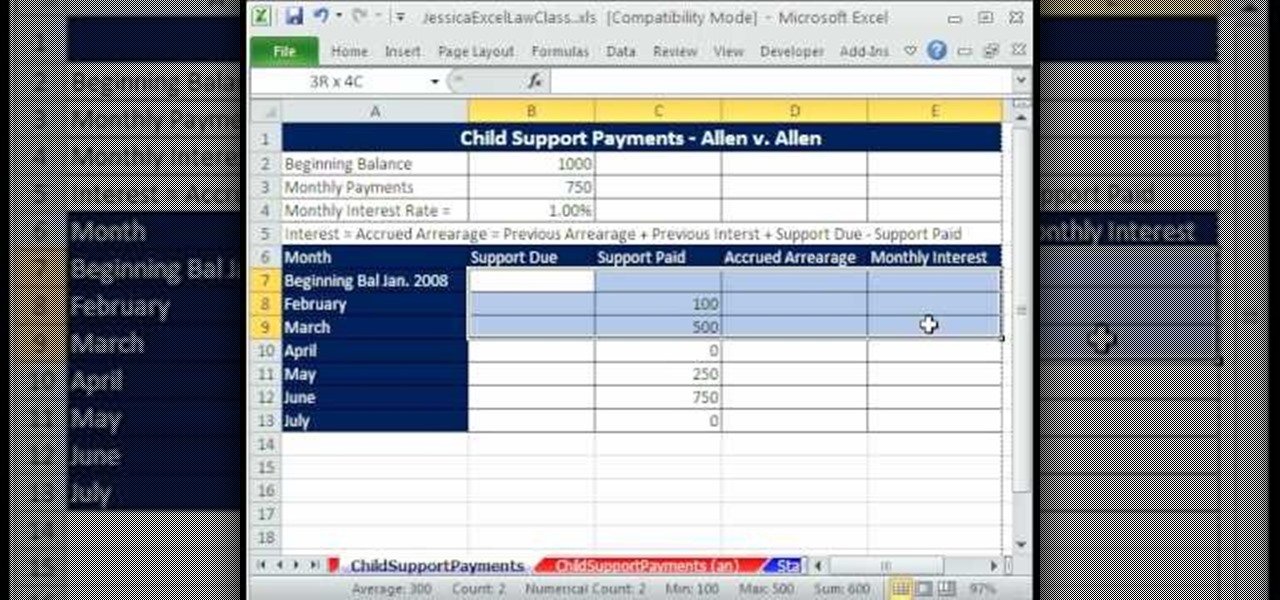
Looking for a primer on how to calculate child support payments in a Microsoft Excel spreadsheet? You've come to the right place. In this free video tutorial from everyone's favorite MS Excel guru, YouTube's ExcelIsFun, you'll learn how to do just that. For more information, including detailed instructions on how to find child support payment amounts yourself, watch this helpful how-to.

In many urban areas, GPS doesn't work well. Buildings reflect GPS signals on themselves to create a confusing mess for phones to sort out. As a result, most modern devices determine their location using a blend of techniques, including nearby Wi-Fi networks. By using SkyLift to create fake networks known to be in other areas, we can manipulate where a device thinks it is with an ESP8266 microcontroller.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

Although not quite as common today with the always-connected world we live in, you still might be having bandwidth wars in your home right now. If the internet connection in your area is mediocre, you know the feeling well. Google Stadia recommends having a 25 Mbps connection for playing in 4K, so you can expect to need at least that much to maintain a smooth, high-quality gaming session.

Some of the leading big tech companies are still working in the lab on actual products, but at least some of their leadership did have some thoughts to share on the future direction of the technology this week.

A long-standing request for the iPhone has been a way to quickly browse and connect to available Wi-Fi networks and Bluetooth devices without having to dig through the Settings app. With iOS 13, Apple has finally built this essential feature into Control Center, giving you quick access to wireless settings from anywhere, including the lock screen.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.