All kinds of people pretend to be someone they're not on the internet, including scammers, people attempting to wind others up, hackers and web predators. Almost all of these people will leave bases uncovered and they're all easy to expose when you understand how to. Here are my favorite ways of finding out when somebody is lying quickly. Image Search

If you are going to travel outside the United States on a ski trip with Skitravel.com, you will need a passport. From Skitravel's website you can click the "get a passport" link. The link will take you to the US Department of State's passport form (the DS11 passport form). On the Department of State's form, you have two choices, a passport book or a passport card. The passport book is good for ten years and you can travel anywhere in the world with it. The second choice is the passport card. ...

Learn one of the world's most popular games. It's actually good exercise, too! Step 1: Decide who goes first

Step 1: Score! Watch for the referee signaling a touchdown, field goal, extra point, or successful try by raising their arms straight up over their head. Raising their hands above their head with palms together signals a safety.

Need a way to keep the kids busy on a rainy day? Making a pop-up card is quick, easy, and will entertain them for hours! Watch this video to learn how to make a pop-up card.

Watch this video tutorial to learn how to calculate your carbon footprint. A carbon footprint is an equation that estimates just how much you, personally, are contributing to global warming—and all you have to do is plug some info into an online calculator. Figuring out how to make your footprint smaller, of course, is another matter.

Learn how to immobilize an ankle. The ankle is a complex joint, so when an injury occurs, and you can't get help right away, the first thing to do is keep it from moving – you'll prevent any more damage to the surrounding nerves and tissue.

Thinking of selling your car on the internet? Make sure you don’t get taken for a ride. You Will Need

Help yourself win that must-have item with these tips. You Will Need: a computer with internet access, money, & patience. Create an account. Browse the categories to familiarize yourself with the site, especially if you don’t have a specific item in mind. If you know what you want, start searching by using broad terms and synonyms to yield the most results. Add quotes around your search terms or qualifiers, such as a specific color or size, to narrow the field. You can also post on the “Want ...

Turn your possessions into cash and become an online selling machine. You will need: Something to sell, a computer with internet access, an eBay account, a digital camera, shipping supplies, something to sell,a computer with internet access, an eBay account, a digital camera, & shipping supplies.

In the world of business, etiquette and manners are important to giving and receiving respect. Brush up on your business etiquette, including meals and introductions, in this free video series.

In this video, Dominick of askmeDIY.com will demonstrate how to build a wooden pergola, a common fixture of modern gardens. Learn what materials you'll require and receive building tips in this tutorial.

Sub-q fluids should only be administered to an animal under the instruction of a veterinarian, but some pets, like rabbits, will need to receive them at home, when the veterinarian is not around. Proper procedure should be followed to ensure that the subcutaneous fluids are reaching the rabbit, and that the bunny doesn't get hurt from malpractice. Watch this video veterinary tutorial and learn how to give Sub-Q fluids to a pet rabbit.

This medical how-to video demonstrates an open emergency cricothyrotomy. A cricothyrotomy is an emergency incision made through the skin and the cricothyroid membrane. This emergency procedure is performed to ensure that a patient is receiving air. Watch and learn how this procedure is performed. This video is intended for medical students only.

This medical how-to video demonstrates an open emergency cricothyrotomy. A cricothyrotomy is an emergency incision made through the skin and the cricothyroid membrane. This emergency procedure is performed to ensure that a patient is receiving air. Watch and learn how this procedure is performed in an emergency room. This video is intended for medical students only.

Remodeling your bathroom can be expensive unless you know know how to do things yourself. This how to video is a quick excerpt from a DIY show. Watch and learn how to build a support system for a whirlpool bathtub.

This short video tutorial will outline the process of making acoustic wall panels using a simple wooden frame and rockwool insulation. These DIY broadband acoustic panels, or bass traps for treating music studio rooms, performance rooms or home theater rooms, will save you tons of money.

Everyone should be able to perform basic first aid, even those with hearing impairment. Deaf individuals are just as likely to save a life as anyone else, but they need to know how, just like everyone else. This video is signed to help those with hearing problems learn about strains and sprains treatments. Although strains and sprains are not a serious injury, they are still very painful for the sufferer, and the only way to make sure they heal properly is to make sure they get immediate atte...

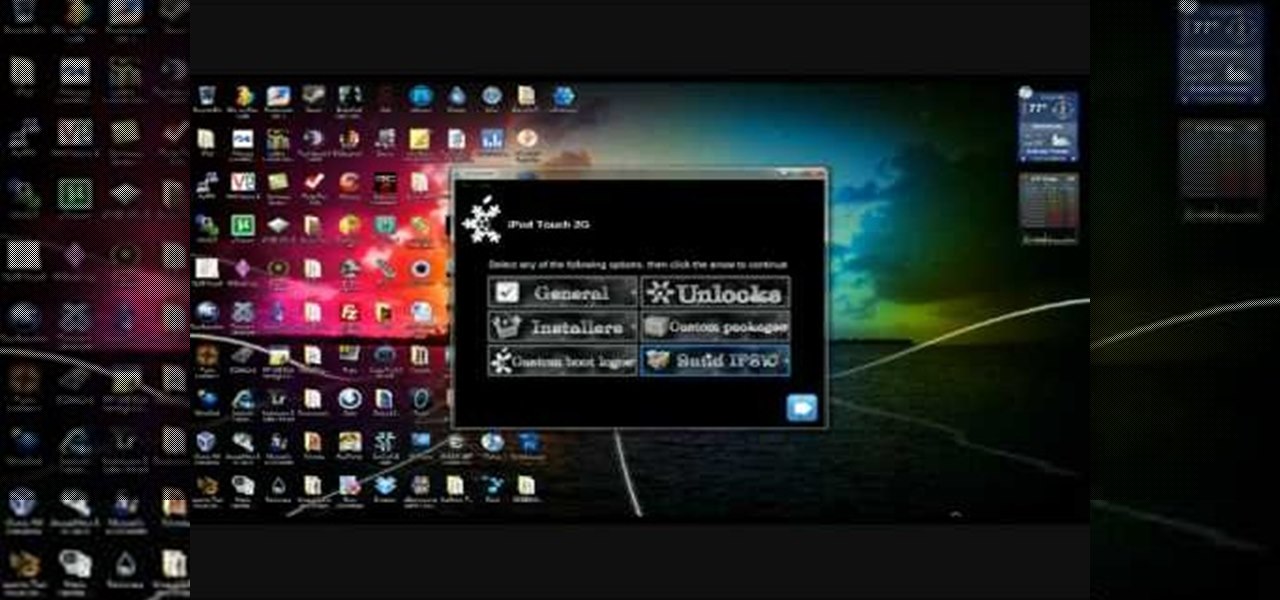
In this tutorial, learn how to jailbreak your new iOS 4 on your iPhone or iPod. This jailbreak will let you take advantage of cool new features including the huge app superstore: Cydia. Enjoy!

There is nothing like fresh vegetables from the garden. Dave Epstein shows us the secrets to planting peas.

In this how-to video, you will learn how to fertilize and deadhead roses. Late summer fertilization is okay for these roses. Make sure to water them in well, as this is key. Deadheading in late summer will give you a fall bloom cycle with the roses. Deadheading will mean cutting off dead blooms. Hips are dead blooms that have fertilized. These make seeds and some are either sterile or will actually grow. To properly deadhead, go down to the second or third five-leaf. Cut at a 45 degree angle ...

Doña Ana County Extension Agent John White and Master Gardener Benny Knudsen look at stone fruit trees on their tour of the "Garden of Weeden". The Mariposa Plum, the dwarf Stella Sweet Cherry, Elberta Peach, Tilton Apricot and the almond tree (which also belongs to the stone fruit family) are featured in this segment of Southwest Yard and Garden series. The suitability of these trees for a small garden is mentioned. Besides this, also discussed is the problem of late frost and its effect on ...

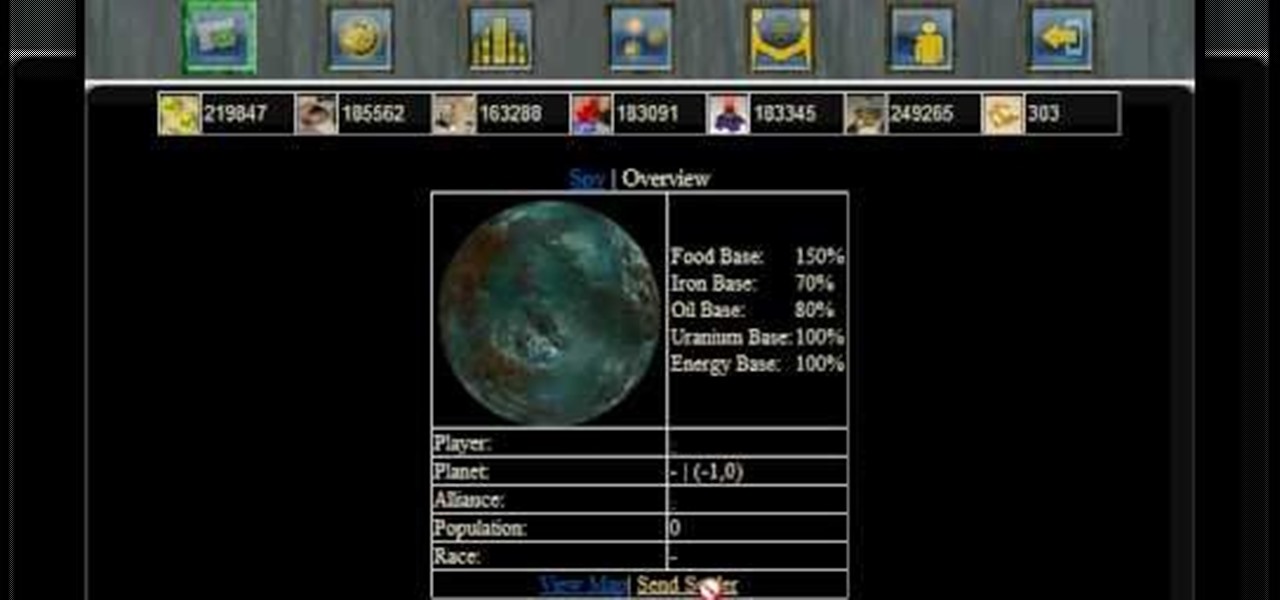
Settling a new planet will decrease your pride ratio, because your population will increase when you're settling a new planet. If you're not sure how to even settle planets...

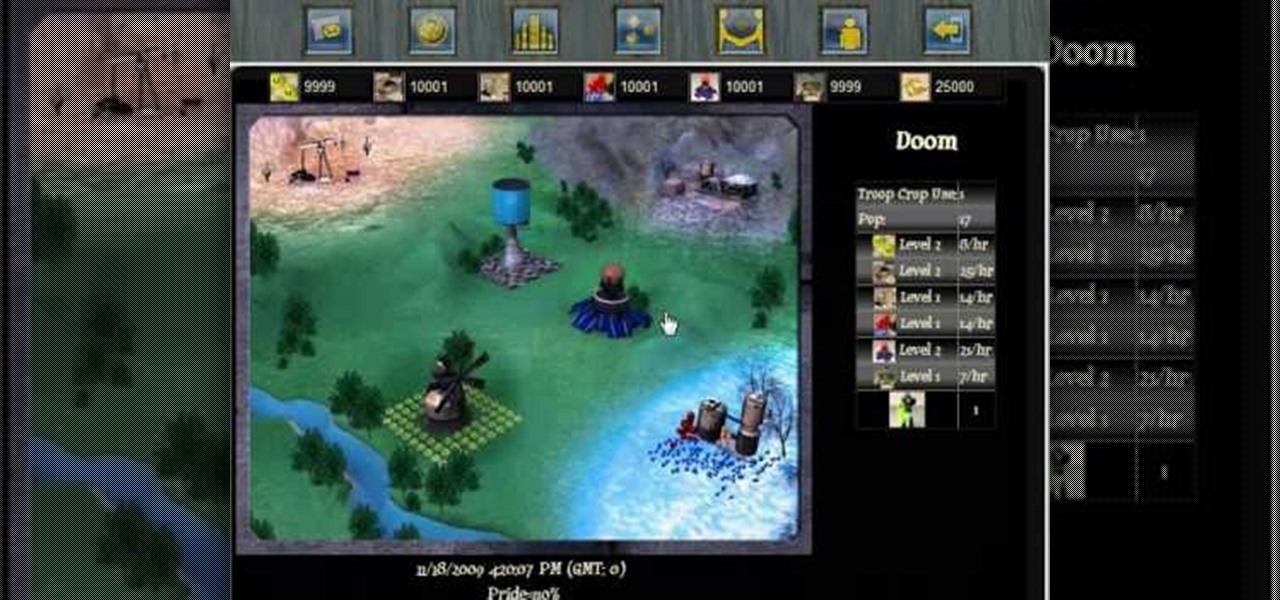
In order to spy and gain intelligence on your Conrohl enemies, you need to make an intelligence agency. Then you recruit your spies to perform simple espionage.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to dive into new features of Photoshop CS4.

Dave and Pat break down the basics of RFID technology and show you how to put it to use by building an RFID beer safe!

Since it's introduction, iPhone has become the standard for design and ease of use, redefining what's possible on a mobile phone. And now with iPhone 3G, this revolutionary device gets even better, offering even more advanced capabilities. iPhone 3G works with fast 3G cellular and wi-fi networks around the world to keep you connected wherever you go. With its integrated GPS technology iPhone 3G makes it even easier to find where you are and where you're going. iPhone 2.0 software includes sup...

Although strains and sprains are not a serious injury, they are still very painful for the sufferer, and the only way to make sure they heal properly is to make sure they get immediate attention.

CONTEST ENDED: WINNERS ANNOUNCED This contest has ended and winners have been announced. To see who won, check out our quick winners post. Thanks to everyone for submitting their ideas!

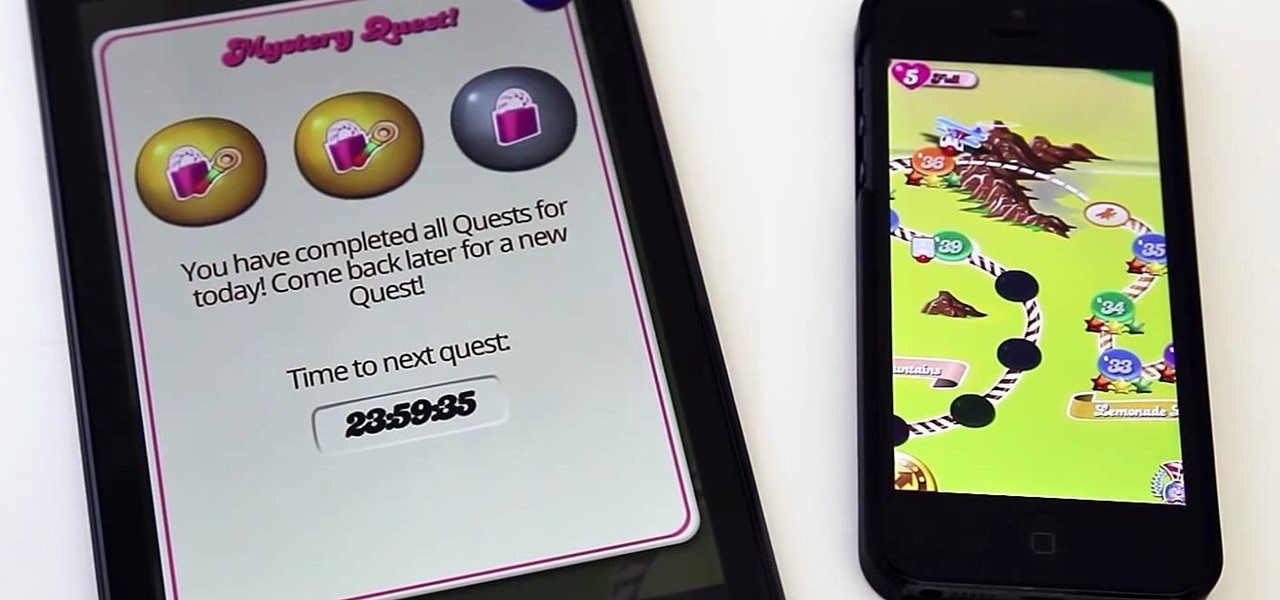
There's an easy time hack available for Candy Crush Saga that let's you bypass the time restrictions to you can play more games faster, and this video guide from KiboshGaming will walk you through it on both Android and iOS devices.

Video: . The author started with a written introduction of the importance of the executive summary as part of the business plan.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

Welcome to Minecraft World! Check out our full tutorials and make sure to post to the community forum if you have any questions or cool builds you want to share.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...

Strengthening your arms takes determination and effort, and one surefire way to get there is by working out your triceps. Triceps extensions are the perfect exercise for those of you with dumbbells at home. It's a great workout to get those dreamy arms and is a basic exercise that isolates the triceps. After doing a couple sets you may start to feel the burn! Lift safety!

If you want to tool around in the user interface of Star Trek Online and modify your client, this video shows you how. Do note that Cryptic doesn't support modding, and it could break your system. But if you want to alter the mouse pointer or your camera point of view, here's how!

Despite the perception that Zilean is only a support champion, if you build him properly, he can hold his own, even an 1v2 battle. Here are some good insights into how to use Zilean effectively on the Fields of Justice.

For roasted chicken, you would expect it to have a nice, brown crispy skin. You would expect it to be moist inside with great flavors throughout. By using the rotisserie function (very common in France) on the Cuisinart Brick Oven. Check out the recipe for this delicious herb-roasted chicken from Chef Hubert Keller.

In this How To Video Kurtis Elwell will walk you through how to do a fakie on a BMX. The best place to start learning how to roll a fakie is on a steep hill or incline. As soon as you start to lose momentum on the hill you will stop for a moment then start rolling backwards. If your BMX is equipped with a cassette wheel it will start to force you to pedal backwards. Then, when you are rolling backwards and want to turn around, turn your front wheel to a 45 degree angle. Lean back a bit so all...