In this series of video clips, you’ll learn tips and techniques for using various types of metal shears, including how to use hand-held and foot-operated types of metal shears, and how to use a metal press and metal hole punch. Expert Jon Olson offers advice on cutting procedures, the proper clothing and precautions, and advice on maintaining and cleaning metal shears. Jon also covers the electrical requirements for operating an electric shear, the various points of danger when operating the ...

Learn how to make a fused pendant from sheet glass. This video shows the visual procedure of creating fused glass pendants with a torch and a kiln. You can fuse pieces of glass together with a torch and then bake the designs to perfection. While there are certainly more laborious details involved in the process, this video provides a helpful visual overview.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

With the nation facing a shortage of ventilators for COVID-19 patients and no apparent ramp-up in the production of new ones, engineers, medical resistents, and do-it-yourselfers are sharing plans for homemade versions.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.
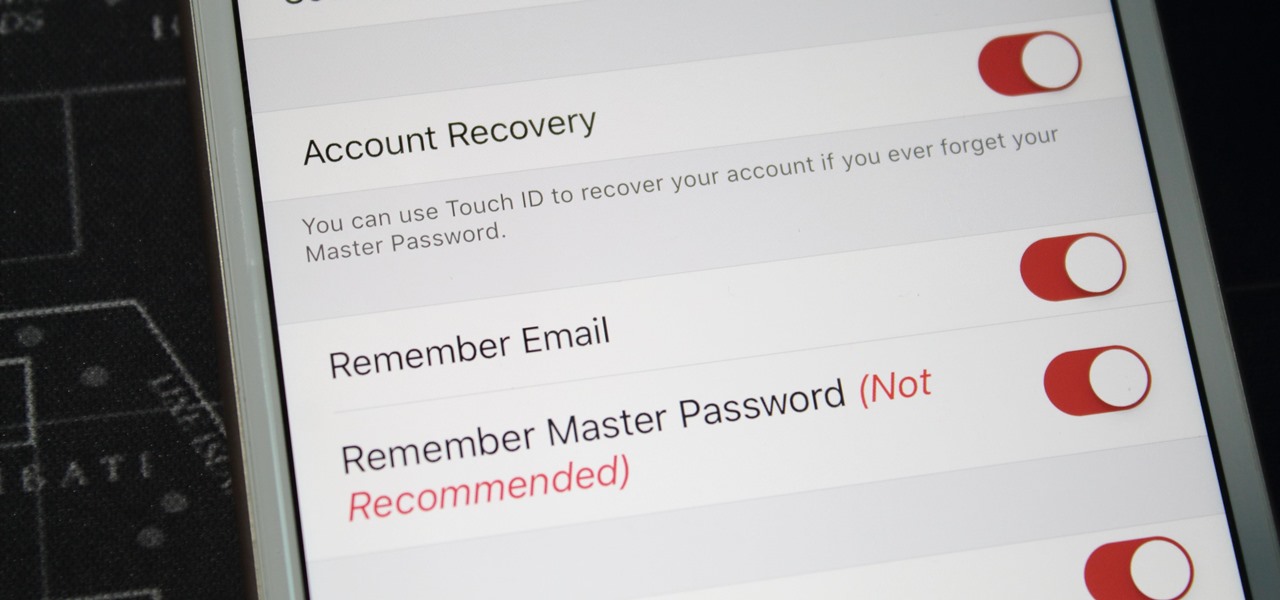
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

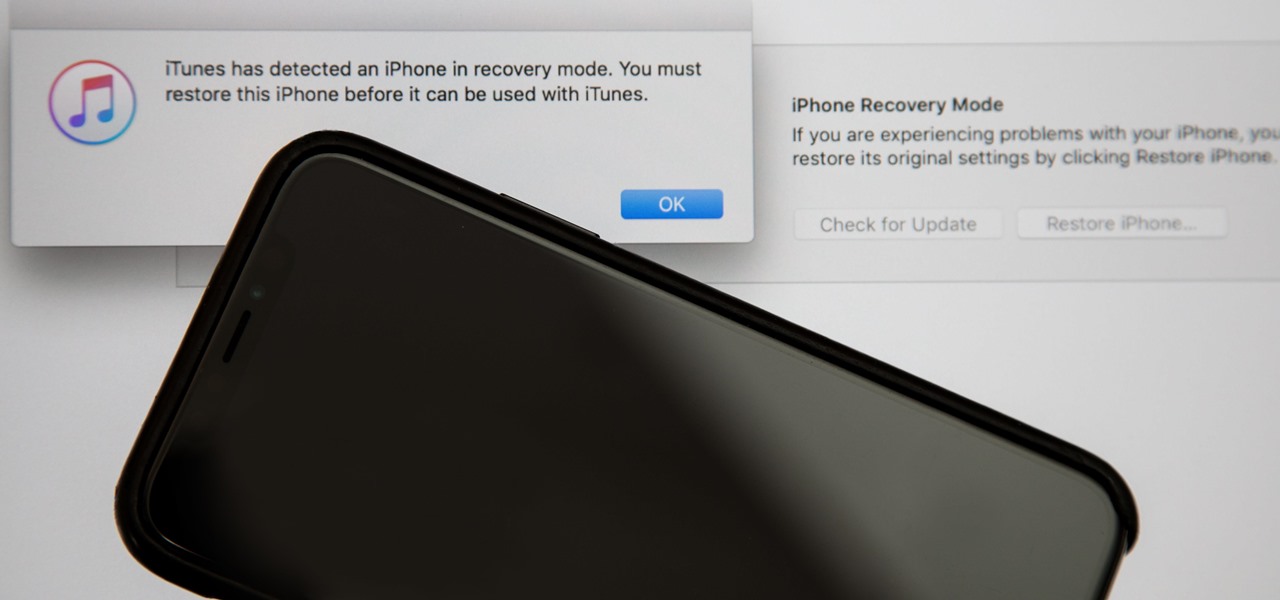
Following in the iPhone X's footsteps, the iPhone XS and XS Max, as well as the iPhone XR, have all ditched the iconic Home button last seen on the iPhone 8 and 8 Plus, which is one giant leap toward Jony Ive's ultimate vision of an iPhone that's a clean slab of glass. However, without the Home button, a lot of tasks have changed, most notably, entering and exiting DFU mode in iTunes.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

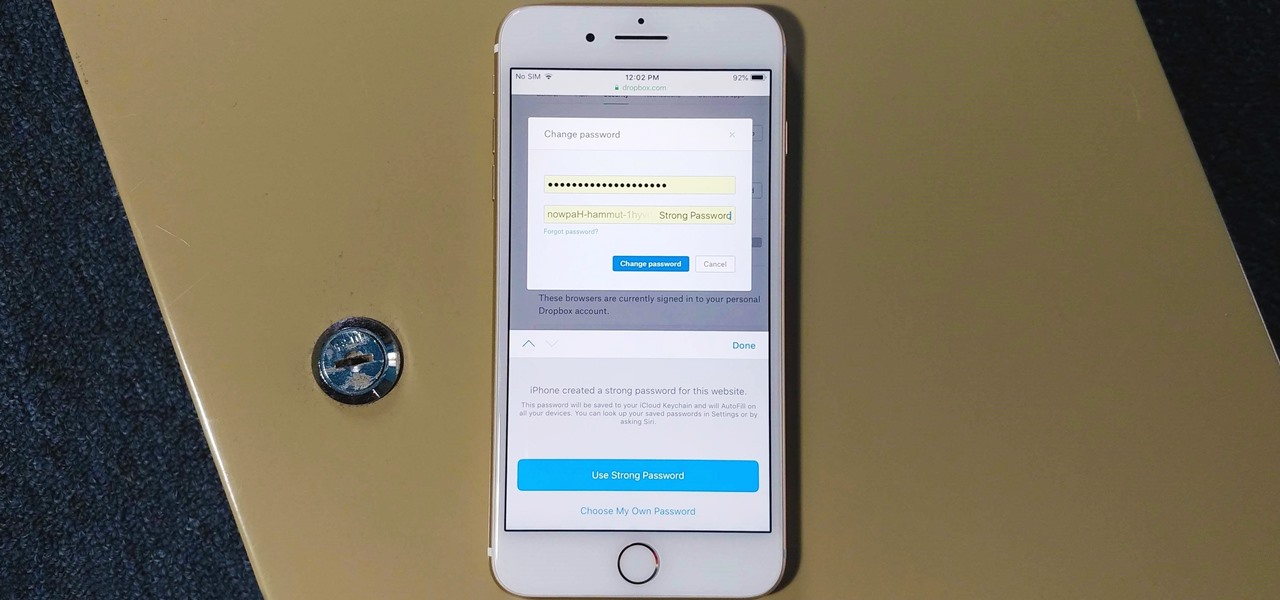
The option to auto-fill passwords on your iPhone has been around a while now, but iOS 12 improves on it by suggesting strong passwords when first creating an account online in Safari or within apps. Apple has also added "password reuse auditing" for your iCloud Keychain, where all your logins are housed, which will find and change your weak passwords to strong ones.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

Getting an insider view of the goings-on at Magic Leap is hard to come by, but occasionally, the company lets one of its leaders offer a peek at what's happening at the famously secretive augmented reality startup. One of those opportunities came up a few days ago when Magic Leap's chief futurist and science fiction novelist, Neal Stephenson, sat for an extended interview at the MIT Media Lab.

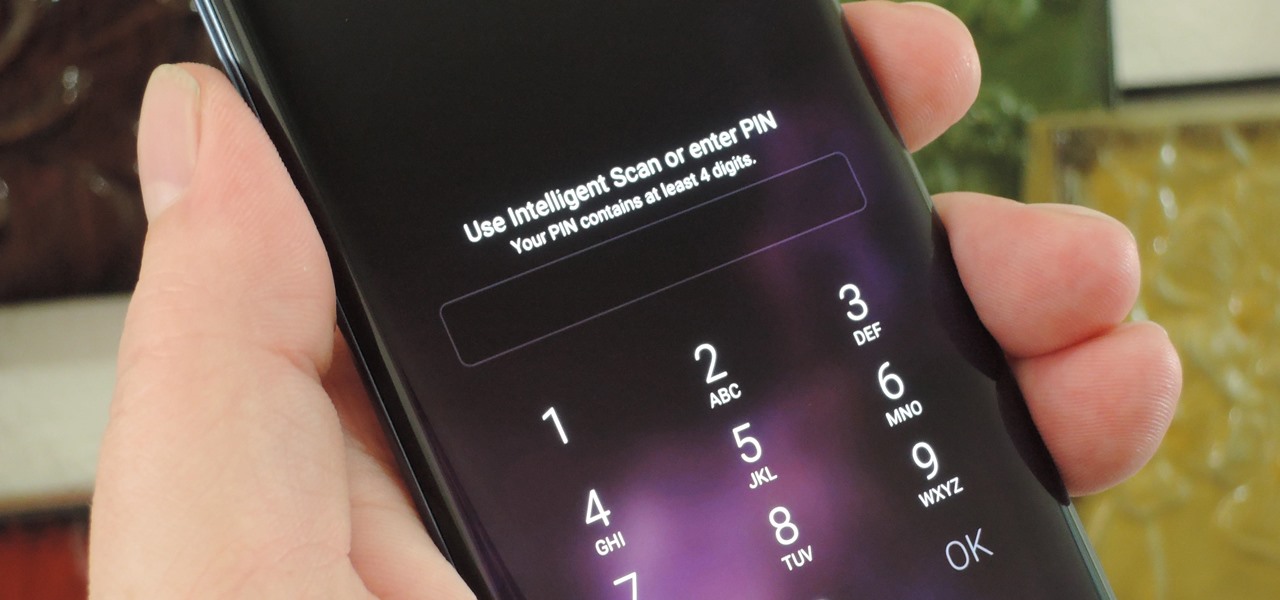
The Galaxy S9 is full of minor improvements and revisions that come together to make it a worthy upgrade over the Galaxy S8. One such improvement is facial recognition, which Samsung has fortified with machine learning and the inclusion of another sensor. The result of these efforts is called Intelligent Scan.

When it comes to applying augmented reality to various business functions, as the saying goes, there's more than one way to skin a cat.

Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes.

Dengue fever is a danger to anyone living or visiting tropical or subtropical regions. It can be hard to detect the infection in its earliest and most treatable phase, especially in children. Luckily, new research highlights better techniques for triaging the disease in infected children with more severe symptoms, potentially saving lives.

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.

If you ever imagined turning the surface of your desk into one large augmented computer, well the future might not be far off, my friends. Lampix, the company that transforms any surface into a smart surface, is currently working on a portable and quite fashionable lamp to project an augmented computer onto any surface that you can interact with using your hands.

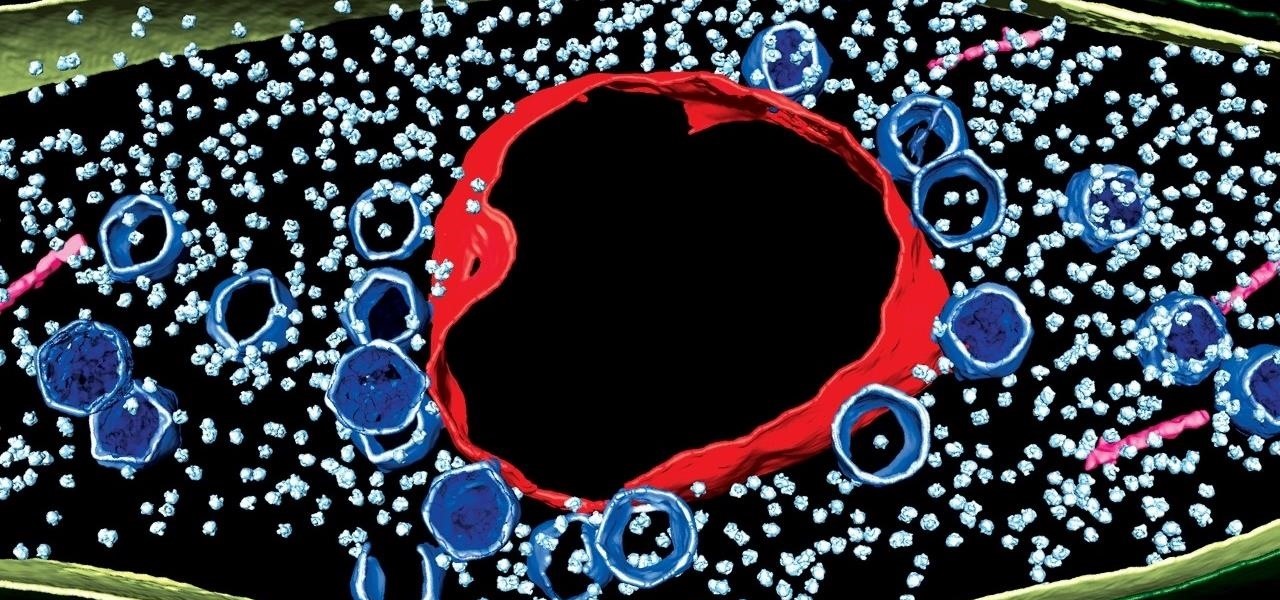
A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Using extreme time-lapse microscopy, scientists watched a virus take over a bacteria to create a cell that looked and functioned more like a plant or animal cell. True story.

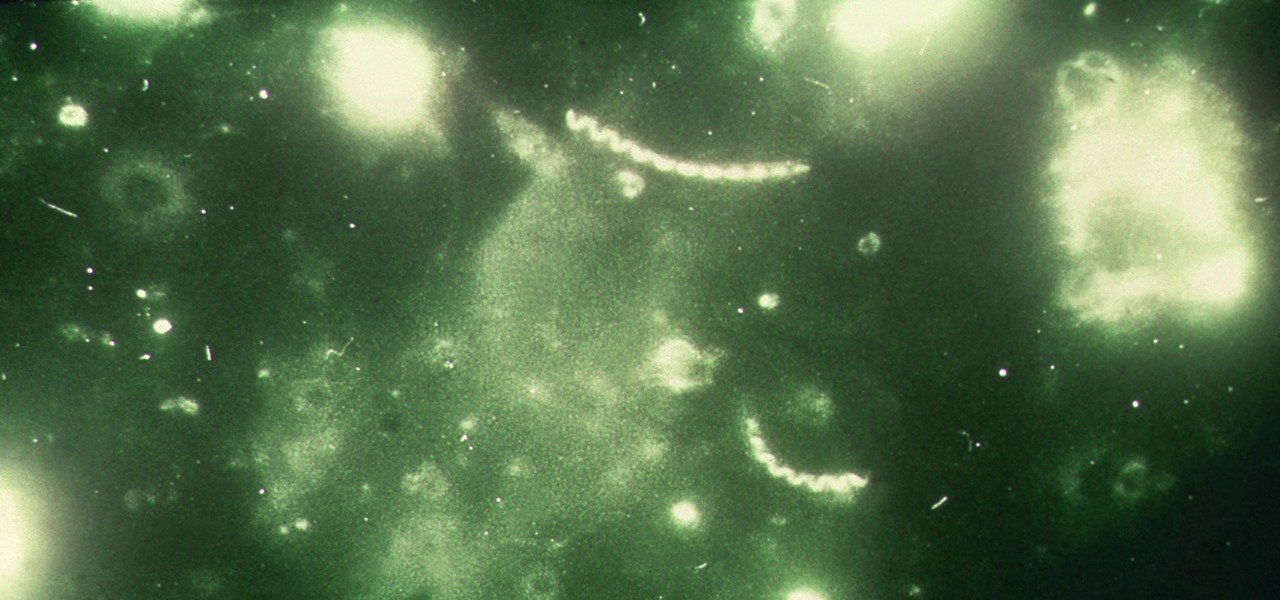
What do Leo Tolstoy (writer), Beethoven (composer), Paul Gaugin (artist), and Adolf Hitler (politician) have in common? They are all considered to have suffered from the sexually transmitted disease syphilis.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Chris' Outrageous Cheesecake, a decedent combination of chocolate cake, brownies, cheesecake, and coconut-pecan frosting, is easily one of The Cheesecake Factory's most popular desserts. But, the price of fulfilling your cravings for this addictive treat can get up there (at about $8 a slice), and when you eat it at the restaurant you likely are limited to only one small piece.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

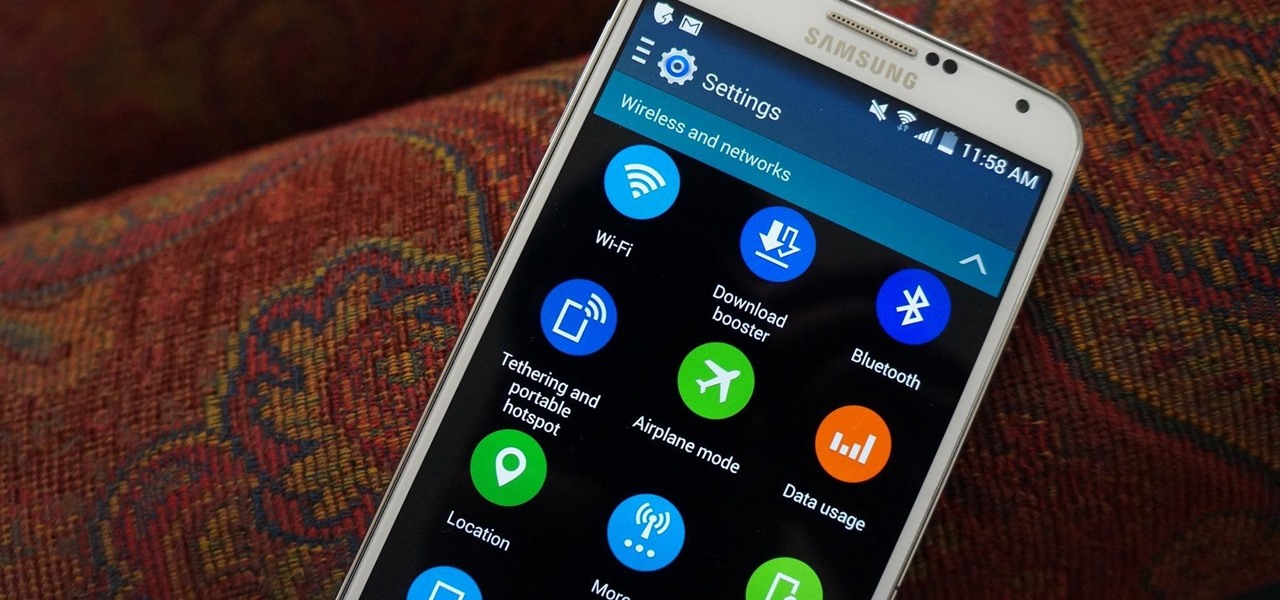
Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

The menu bar is a great place to perform quick searches, track battery life, and switch Wi-Fi networks on your Mac, but it can do way more than that if you let it. I've rounded up some menu apps below that not only have features that will boost your productivity, but are lightweight enough to run entirely from the menu bar.

The gag reflex: it can interfere while in the dentist's chair, upon seeing another person throw up, or even just getting a whiff of a disgusting, stomach-twisting scent. Every time this reflex kicks in, it stops us immediately, inducing a choking, gagging, coughing fit.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Summer is the season to enjoy stone fruit: peaches, plums, nectarines, and apricots are all kissed by the sun and bursting with juicy flavor—which is all well and good when you're eating them as is.

When the Samsung Galaxy S5 launched a few months ago, I was pretty envious of the new UI elements Samsung included on it, as I'm sure you were. The flatter interface provided for a more polished and less cartoony feel, bringing the device more in line with Google's design elements.

Having a dust- and water-resistant phone is truly useful, but it comes with a price. In order to achieve this functionality, Samsung had to literally plug up any holes in the Galaxy S5, and this included the charging port.

Whether you have the original Nexus 7, or the 2013 Nexus 7 tablet, rooting it will give you access to tomorrow's features, today.

Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

WhatsApp is one of the most well-known and most utilized cross-platform chat applications available today. It's free for one year, and only $0.99 a year after, which is chump change when you realize there are no hidden costs like international charges. Basically, it creates an easy to use forum for you and your friends to chat, regardless if they're an Android or iPhone user.

If you save scraps of yarn, and have a dog, this is an easy project for you. The Mobius scarf has the advantage of not having any ends to come untied, or dangle down for your dog to trip over, or get tangled in branches and stuff. I made this one for Pepper, my 16lb rat terrier. Step 1: Choose Your Yarn: I had very little yarn to work with. I had one more ball, but it had just a little more on it than the largest shown here.

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

The video describes the procedure of fixing the wiring harness on a Ninja 250R motorcycle. The person who owns the bike presents this video. He says that he got his bike back after getting the wire harness newly fitted. His signal blinker lights were not working. The next morning he wanted to make sure that it was fine. He plugged the wire and tried to switch it on, but it did not work. He also found that the horn was also not working. It was actually not working for a long time now. Then, he...

In this video clip series our welfare expert will show you exactly how to apply for it in the state of Florida. Many states are similar to Florida int his regard but some will have a few subtle differences in their application procedure so review more for that.

In this series of video clips you’ll get simple step-by-step instructions on how to replace a damaged lug nut stud on the wheel of your vehicle. Expert mechanic Nathan McCullough demonstrates the procedure in easy to follow steps, starting with breaking loose the lug nuts and removing the tire, parking brake cable, caliper and finally the broken stud. He also demonstrates how to clean and install the rotors and wheel assembly, and most importantly, how to check your work for safety.