Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.
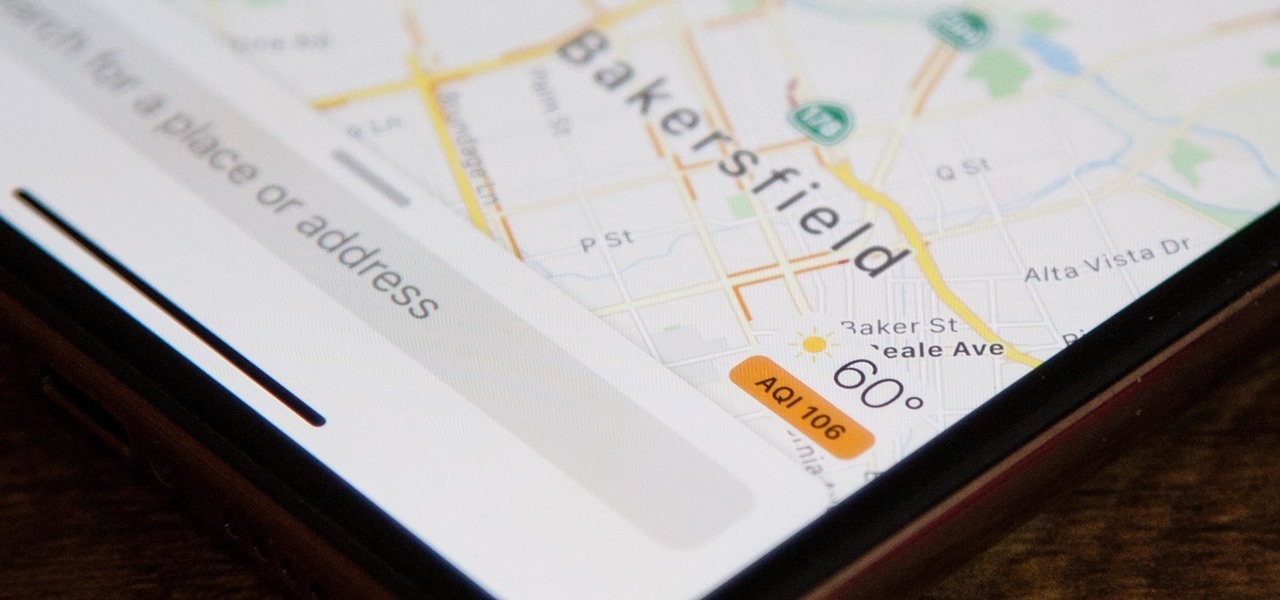
While the United States, in general, doesn't have the worst overall pollution, the air quality can drastically change from one day to the next. If you're particularly sensitive to pollutants in the air, there are apps that show how clean or polluted the air is in your area, as well as in cities you plan on traveling to, but Apple's making those apps less relevant with a new feature in Apple Maps.

Many popular IoT devices have terrible security. For instance, a hacker who's on the same Wi-Fi network as a Sonos speaker can assume direct control over the device's behavior. If an IoT device doesn't secure the messages used to control it over a network, it's easy for somebody to write a few Python scripts to make it do whatever they want.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

| Updated Aug. 22, 2019 with new phones. When will my phone get Android Pie? For the first time since Android's inception, this question shouldn't have an answer that lets you down. That's because Android Oreo introduced Project Treble, a new low-level arrangement that makes updating a lot easier. So with Pie, it's not if your phone will get it, but when.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

One feature in iOS you're likely underutilizing is 3D Touch, a highly useful, unique tool for iPhones ever since it first appeared on the iPhone 6S. Apple's pressure-sensitive interactivity gives iOS an extra layer of functionality, which can be clearly seen across the entirety of your device. From the lock screen to the home screen to the apps in between, there are plenty of ways to use 3D Touch.

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

An attacker with shell access to a Linux server can manipulate, or perhaps even ruin, anything they have access to. While many more subtle attacks could provide significant value to a hacker, most attacks also leave traces. These traces, of course, can also be manipulated and avoided through methods such as shell scripting.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

The software released in the 2015 iterations of the Samsung Galaxy line of devices—the S6, S6 Active, S6 Edge, S6 Edge+, and Note 5—have some pretty neat camera features that give these devices arguably the best smartphone camera on the market today.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

The oven is arguably our most essential kitchen appliance (right alongside the fridge, freezer, and yes, even the microwave). But even though we've been using them for a few millennia, many of us know so little about our ovens that our cooking or baking can feel like a roll of the dice sometimes.

Running out of storage space on your iPhone is annoying, but trying to free some up is downright aggravating. Until they figure out a way to throw a terabyte of flash memory in there, you're going to have to do some spring cleaning every now and then, especially if you're trying to update to iOS 8.

Cryptography is the science of keeping secrets, or more specifically, the science of disguising them. As a point of fact, cryptography has progressed quite a bit farther and now encompasses file and message integrity, sender authentication, and pseudo-random number generators.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

In the first part of this two-part guide, I covered cutting, grooving, beveling, making holes, and stamping/tooling. I hope you enjoyed that part, because we're pushing the accelerator to the floor and moving ahead at full speed!

The biggest update to arrive since iOS 18 and iPadOS 18 just came out, and it's packed with new features and changes for your iPhone or iPad. From new Apple Intelligence capabilities to Game Center improvements and new calling tools, there's a lot going on in iOS 18.1 and iPadOS 18.1.

Apple's official feature list for the Music app on iOS 18 and iPadOS 18 may highlight only one update, but there's much more happening under the surface than that. Whether you subscribe to Apple Music, the latest version brings hidden gems that enhance your up-next queue, playlists, and overall experience.

Apple Maps keeps getting better and better for all the hikers in the world. The latest update gives you access to thousands of detailed trail maps within U.S. national parks and topographic views, but it also lets you create your own walking and hiking routes.

If you're an AirPods user, things are a lot better with iOS 18 and iPadOS 18. If you're not, it may finally be time to grab yourself a set of AirPods, especially if you're into privacy and gaming.

Apple might not be finished with iOS 17. While the iOS 18 update was already released, there may still be things for Apple to fine-tune on your iPhone. This brings us to iOS 17.8. Will it happen? And will there be a beta?

Apple has already released iPadOS 18, but there still may be work to complete on iPadOS 17. That brings us to iPadOS 17.8. Is there one, and can you test-drive it on your iPad?

In less than a month, WWDC, Apple's Worldwide Developers Conference, will reveal the company's plans for the upcoming iOS 18 and iPadOS 18 software updates. But we already know what accessibility features will be hitting iPhones and iPads later this year, and many of them will be helpful to everyone, not just users with accessibility issues.

When Steve Jobs introduced the first iPhone, he pointed out that the biggest problem with physical keyboards on mobile phones is that they're always there, whether you need them or not. Now, 17 years later, a new company is bringing us full circle, giving us the best of both worlds: a physical keyboard for iPhone that can disappear whenever you want.

Apple Notes started with humble beginnings as a scratchpad of sorts, a place for us to stash some simple text for later. It's received many upgrades over the years, but Apple's latest iPhone software update is a game-changer.

Your iPhone has a safety feature that makes it easier to call 911 in the U.S. and other emergency services abroad. Instead of fumbling with your iPhone's dialer, you can call someone for help in various ways — with or without your hands.

There's an iOS feature that benefits many users, but it's absolutely vital if you wear AirPods or other headphones models connected to your iPhone. A large number of iPhone users don't even know about it, especially since it's disabled by default and hidden deep in the system settings.

On the latest iOS software, your iPhone comes with significant privacy and security enhancements to protect your data even more than Apple did before. From safeguarding your iPhone to passcode-protecting files to making it easier to browse the web safely, there's a lot you need to know and start using.

The Calculator app is probably one of Apple's most-used iPhone apps, yet I always meet people who don't know all the little tricks there are to using it more efficiently. You may know most of them, but there's a chance you don't or at least forget about some of them.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

Some apps look great with Dark Mode, and some do not. So when you have system-wide Dark Mode enabled on your iPhone and are using an app that only looks good in Light Mode, you'd normally have to turn the dark appearance off manually, then switch it back on when you leave. But there's a workaround that can automate the process for you.

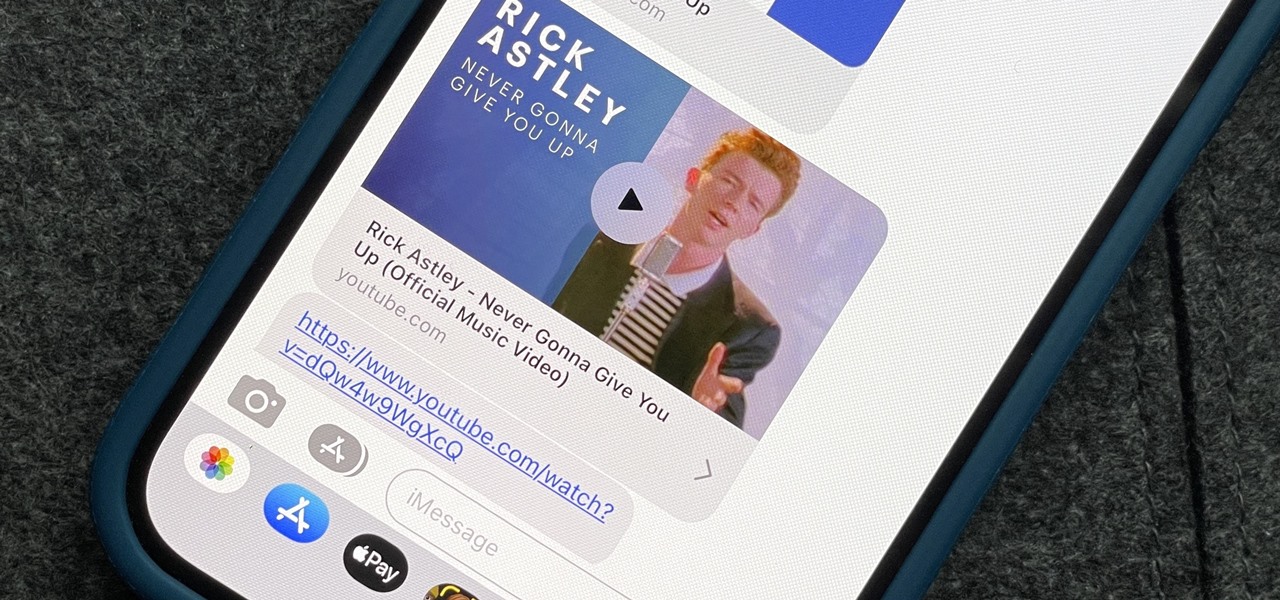
Apple automatically converts most URLs in the Messages app into rich link previews, but they aren't always pretty, and sometimes you just want to see the full URL instead. While there is no setting on iOS, iPadOS, or macOS that disables rich link previews in the Messages app, there is an easy way to show the URL complete with the scheme, domain name, and path.

You may be tempted to install the iOS 16 developer beta on your iPhone to try all the exciting new features it has to offer, but it may be a good idea to wait if you only have your personal iPhone that you use every day.