Over the past three years, Epic Games has raised billions of dollars in funding on the success of Fortnite as well as Unreal Engine, one of the top 3D engines available for developing games and AR experiences.

Microsoft believes its Mesh platform can help developers build immersive AR apps more easily. We spoke with a member of the Microsoft team to learn more about the platform.

After piloting the Nreal Light in South Korea and Japan via carrier partnerships and securing another round of funding, Nreal is now ready to begin selling the consumer edition of the smartglasses to the western world as well as introduce a version for enterprise customers.

Let's say you're hanging a picture frame, and it doesn't look quite right. Sure, you could grab a spirit or bubble level, but maybe it's in another room or buried in a toolbox somewhere. Maybe you're away from home, away from your tools. As it turns out, you almost always have a level with you, and it's likely sitting in your pocket right now or resting in your hand as you read this article.

A lot of digital ink has been spilled heaping scorn on Magic Leap. Much of that media schadenfreude was due to what some believed were unmet promises versus some of the early hype around the product. Others just seemed to be rubbed the wrong way by the startup's Apple-esque secrecy and penchant for attempting to coin new terms and frameworks for things that were, mostly, already in play.

Back when I worked in the music industry, I never imagined there would be a day that I'd be able to sit in a room surrounded by virtual album covers while listening to beats, but that day is really here.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Starting Sept. 13, you can preorder the iPhone 11, 11 Pro, or 11 Pro Max from Apple, wireless carriers, and various e-commerce websites. However, unlike with Android smartphones, there is only one set of iOS phones that come out each year, so they're pretty hot items. That means being the first to get your hands on one could be a challenge, but we're here to help you out.

When it comes to platform games on mobile, endless runners are some of the hardest to play since they can go on seemingly forever. There's always room for improvement since your goal is to beat your previous score (or someone else's high score). But which endless running games are worth your time?

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

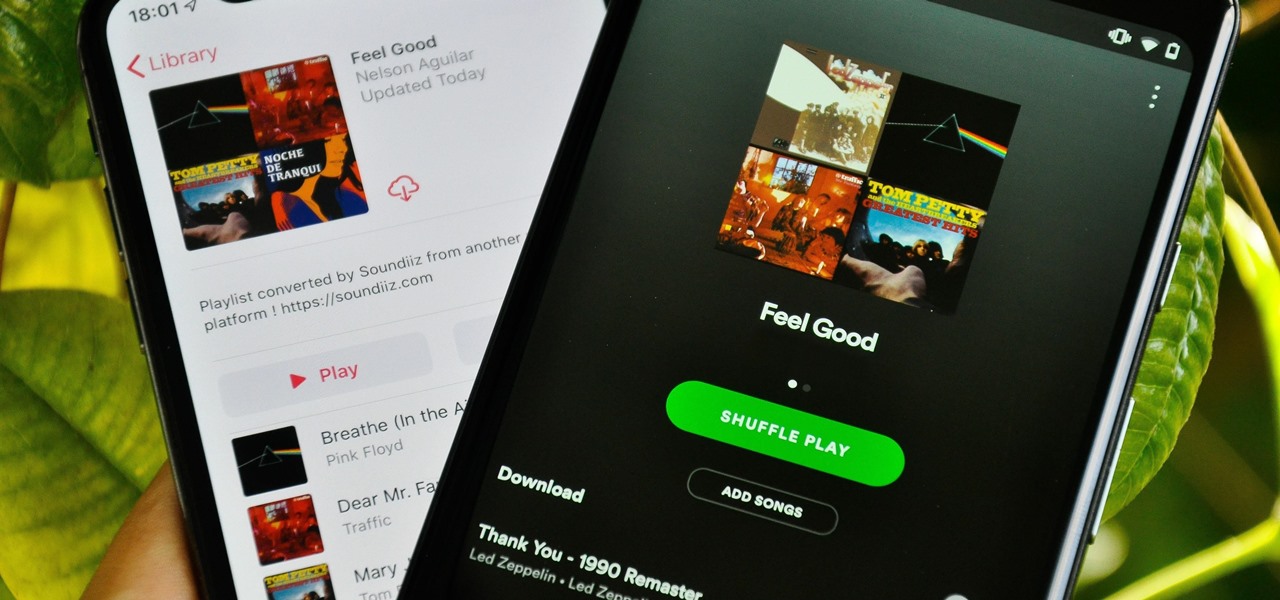
Music streaming services make it difficult to transfer your favorite songs and artists from one service to another and for a valid reason: they don't want you to leave. But when it comes to switching, playlists are a big concern, because who wants to do it all over again? Luckily, if you're moving from Spotify to Apple Music, you can use a third-party app to take playlists with you.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Once again, LG is mixing up its launch. Instead of the announcing the latest entry in G series later in the year, the LG G8 ThinQ was announced at Mobile World Congress 2019, shortly after Samsung's Galaxy S10 event. And instead of trying to match what other OEMs are doing, LG is once again trying to be different.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

So, you've lost your Apple TV remote. Maybe it's busted. What are you supposed to do now? You could go out and buy a new one, but they're expensive if you have a newer Apple TV with a Siri Remote, and wouldn't you rather spend that money on a movie? You might be without a working dedicated remote, but you likely have the next best thing already in your pocket.

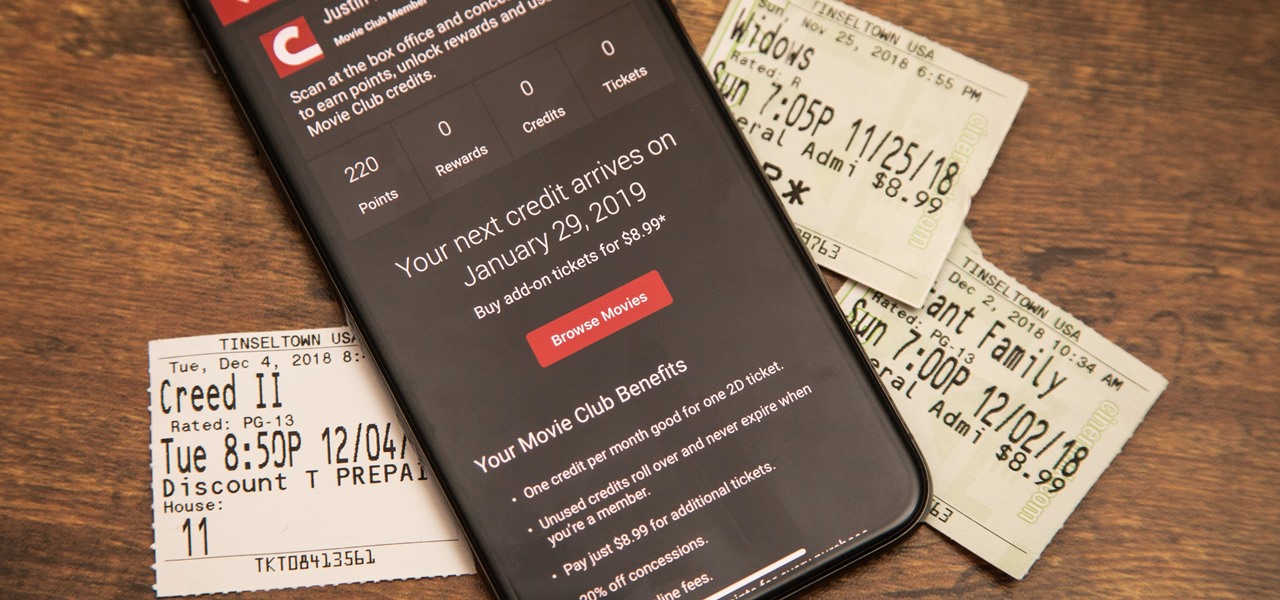
Cinemark may not be as big as AMC Theatres, but it also has a subscription if you want cheaper access to movie tickets. There aren't as many theaters, but if there's no AMC around you, there will likely be a Cinemark to save the day. But is the price of its Movie Club plan worth it?

Streaming movies and TV shows on phones is more popular today than ever, but what about when you're on a plane, have a limited data plan, or will be in a no-service area? You'll want to download your movies and TV shows instead. While Netflix is excellent, you can't rent or download most of the latest movies and TV series. What you need is an app that lets you do just that.

In a previous tutorial, we were able to place the Mona Lisa on vertical surfaces such as walls, books, and monitors using ARKit 1.5. By combining the power of Scene Kit and Sprite Kit (Apple's 2D graphics engine), we can play a video on a flat surface in ARKit.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Apple's new iPhone XR, XS, and XS Max are sure to be hits this year. Of course, that means plenty of hungry customers are looking to sign up for a model once preorders begin on Friday, Sept. 14, for the XS models, and Oct. 19 for the XR. Luckily, there are preemptive actions you can take right now to avoid waiting outside an Apple Store overnight or getting kicked out of the preorder queue online.

Since getting our hands on the Magic Leap One last week, we've been methodically delving into each feature and reporting our findings step-by-step. Earlier this week, we took a look at the Screens app (a video viewer) and the Helio app (an AR web browser). This time around, we'll be digging into the Create app, the experience that allows you to fill the real world with objects that transform the nature of your local reality.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

We've shown you the best augmented reality headsets, and now it's time to show you the rest. These are the AR headsets you've probably never heard of or even seen. The AR headsets that, in some cases, have a shot at the big time, and may one day reach widespread adoption, and, in other cases, are unwieldily contraptions that look like something out of a weird science fiction movie.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

2017 was a down year for HTC. First, the U11 and U Ultra were widely criticized. Later, Google purchased a large chunk of HTC's manufacturing division, leaving the Taiwanese company running with a skeleton crew after losing 2,000 key employees. But that's not stopping HTC — their flagship U12+ was just announced, and it's quite impressive.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

Connecting to your headless Raspberry Pi on the go typically requires a network connection or carrying around bulky peripheral hardware like a screen and keyboard. With the help of an old-school connecting standard, though, you can log into your Pi from any computer using a simple cable. If you don't have a power source, you can also power your Linux distro over the cable at the same time.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.

Cruise Automation, the driverless car startup General Motors (GM) bought for $1 billion in 2016, is readying a formidable fleet of robo-taxis for rollout in cities throughout the US. But when it comes to details about how the company plans to realize these lofty goals, it's been fairly tight-lipped.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

You may not have heard of visceral leishmaniasis, onchocerciasis, or lymphatic filariasis, and there is a reason for that. These diseases, part of a group of infections called neglected tropical diseases (NTDs), impact more than a billion people on the planet in countries other than ours. Despite the consolation that these often grotesque illnesses are "out of sight, out of mind," some of these infections are quietly taking their toll in some southern communities of the US.

In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envision it in real life.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!