Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

You know that feeling when your cell phone gets stolen and you figure it is pretty much lost forever. You could've used one of the millions of device managers and trackers, but ya didn't. And the Good Samaritan is not coming to your rescue.

In this video series, our expert will teach you how to identify signs of depression. If you suspect you, a friend or family member is suffering from depression, let our expert explain the various symptoms of depression and when you may need to seek professional help.

This post has been brought to you by the letter S. With the Christmas season fast approaching, it's time to ask one of the most important questions of our lifetime:

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

It's a notoriously preconceived notion that a man has to ask the woman out. But why can it not work both ways? It does, and it's the best way to bag the man of your dreams, especially if he's the shy type. If you're tired of waiting for your prince to appear with a Manolo Blahnik in your size, then stop waiting, and start taking control.

If you know that ticks spread Lyme disease, you may already know you might also catch a bunch of other infections from them. One of the lesser-known diseases spread by ticks is infection with the bacterium Anaplasma phagocytophilium, called anaplasmosis.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

Apparently submerging a hand in liquid nitrogen isn't as painful as one might suspect (if you trust the Leidenfrost effect as much as Theodore of Gray Matter):

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Eight days ago, Apple pushed out iOS 12.3 public beta 4 for anyone who wants to try it out. Now, there's a new version, iOS 12.3 public beta 5, released May 7, less than an hour after the developer software update. Just like it's developer version, the fifth iOS 12.3 beta for the public is a simple update with seemingly under-the-hood changes only.

Trendy restaurants are fun, but waiting in line isn't. Too often, we arrive at a location to find a queue between us and our dinner. If only we could know when wait times were down so we could go out at the optimal time.

What a week for iPhone rumors. Monday saw an intriguing photo leak on Reddit of what could be the final designs for the iPhone 8, 7S, and 7S Plus (highly suspect, of course). Today continues the intrigue — iPhone assembler Wistron told reporters in Taipei that Apple's newest smartphones will be waterproof and feature wireless charging.

In mid-November, Vuforia officially released Vuforia 6.1, which has full support for the Microsoft HoloLens. They also released their AR Starter Kit to the Unity Asset Store, which contains scenes that show you how to use Vuforia features. While I have yet to find any confirmation, I believe it is safe to assume that the AR Starter Kit will work with the HoloLens. I already had a Vuforia tutorial planned for this week, so as soon as I know for sure, I will begin working on it.

Some people hate cold weather, but there are also plenty of things to look forward to in the wintertime. The holidays, building awesome snow sculptures (or igloos), and hot chocolate, to name a few. But with all the good also comes one gigantic downside—more people get sick during the winter than any other time of year.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

I love making my own printed circuit boards. It really gives a professional look to a finished project, and having all the design files means I can whip up another batch whenever I need to. However, when I need to make, say, three thousand swarmbots or fill an order for a dozen PCBs, the traditional etching process can slow down the operation to a crawl.

UPDATE: The OnePlus 8 Pro has been released! Check it out on the official OnePlus website or read through the rumored specs we've left below for posterity.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

As first reported by Next Reality last year, game developer Preloaded, in partnership with BBC Studios, has finally launched BBC Earth - Micro Kingdoms: Senses.

"Why do I keep getting popups on my phone when I'm not even doing anything?" I see this question asked all the time. The answer? You have a shady app on your phone and it started showing full screen ads. But people either don't know this (so they don't know they just need to find and uninstall the problematic app), or if they do know it's a bad app, they don't know which app is causing it.

You want whales? Ok, you'll get whales! That seems to be the unspoken message from Magic Leap via its latest update in the form of several new experiments posted inside its Helio app.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

The crime procedural show is the perhaps the most direct path to the average TV viewer's heart. Could the same hold true for augmented reality games?

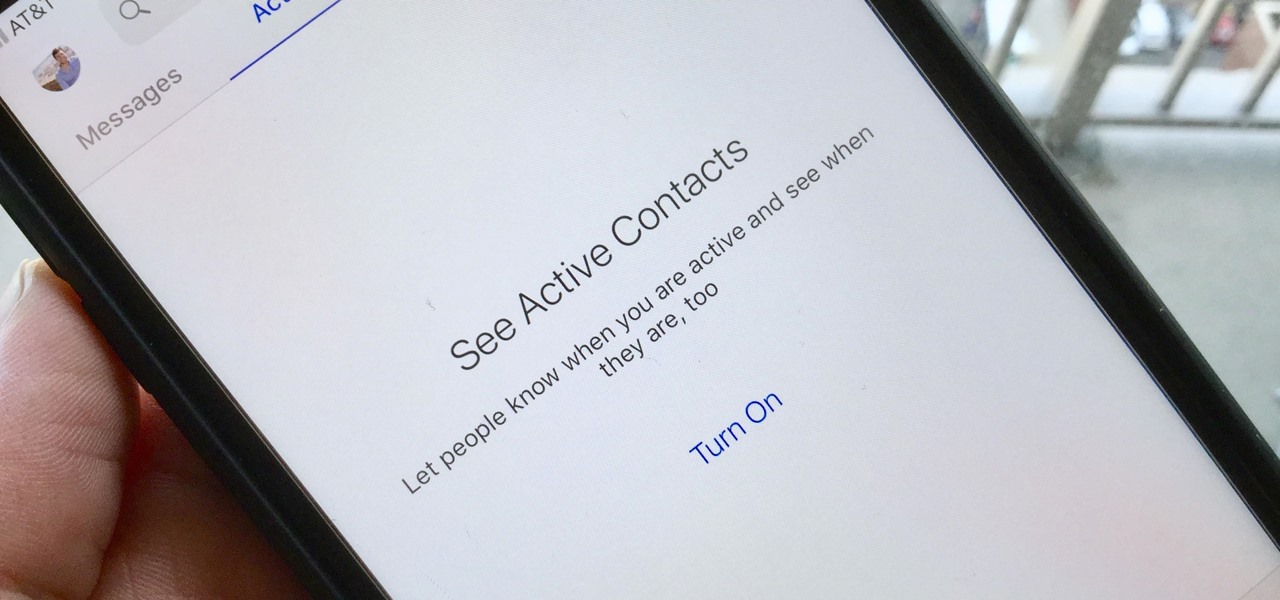
For all of its advantages, Facebook Messenger isn't the best for people who like their privacy. The popular app lets all your Facebook friends know when you're online by default, as well as how long you've been idle, making it impossible to check up with one person without leaving yourself vulnerable to your entire friends list. Luckily, this feature is one you can turn off.

With the hype surrounding the iPhone 8, Apple's announcement that it's developing driverless software, and the new iOS 11 beta out, it seems like the tech giant is constantly in the news. Today, Apple's continuing this streak with updates for its iWork app suite on iOS and macOS.

In Indianapolis, two-year-old Kenley Ratliff has passed away from what is suspected to be Rocky Mountain spotted fever (RMSF), a tick-borne illness. The young girl fell ill with a fever, and just a week later, passed away. Now her family and doctors are looking into the cause of her death and warning others to check themselves for ticks this summer.

Snapchat is attempting to take over the world via augmented reality technology. Well, it's more of a virtual makeover than a takeover, but still ...

Google's former driverless car boss Chris Urmson raised considerable funds to get his new startup company Aurora Innovation up and running. Axios initially reported that Urmson raised over $3 million to fund his brainchild in the wake of his Alphabet exit, according to an SEC filing.

T-Mobile just unveiled two new services—Scam ID and Scam Block—which specifically target those pestering robo-calls that reach out to 2.4 million Americans every month.

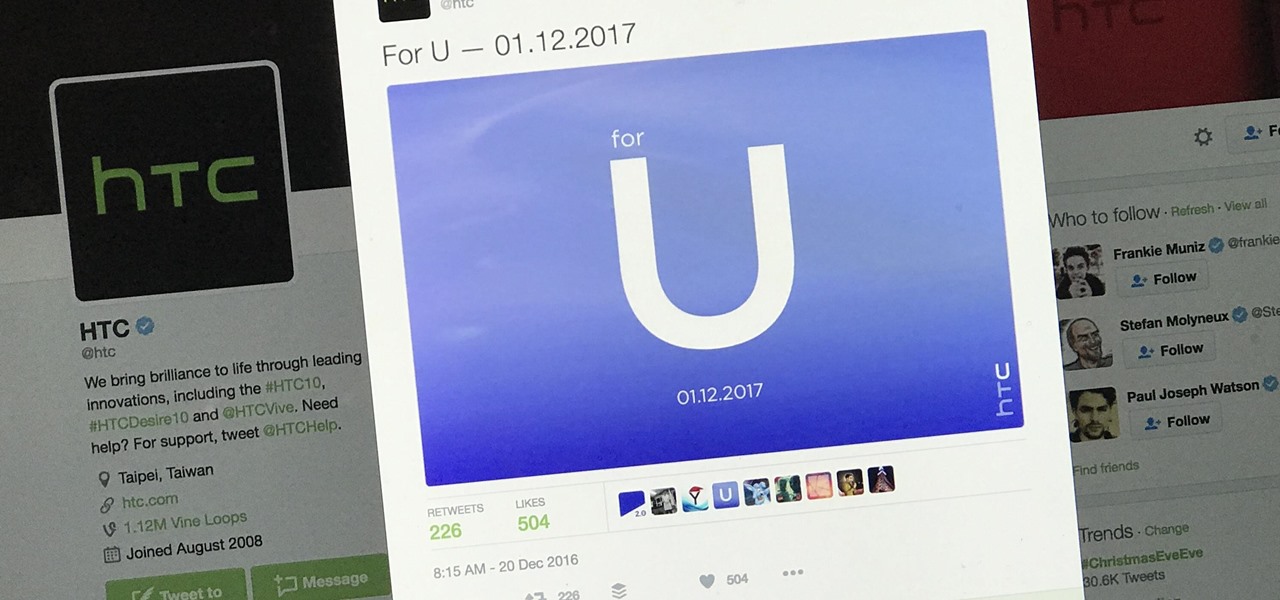
Earlier this week, a mysterious tweet appeared on the HTC Twitter account of a picture containing the letter "U" topped with a tiny "for" and the date "01.12.2017" at the bottom. It is a pretty solid teaser, but for a company that has had a solid year with their Vive virtual reality headset, and all of the other technological appendages they have, it seems a bit ominous for them.

Gender standards are entirely pervasive. We raise our sons to be masculine and our daughters to be feminine, which perpetuates the gender role formula when they grow up to be parents and raise their own children. Part of this whole equation is that boys are supposed to remain stoic and project an air of strength, and girls are expected to be amiable while being held to unrealistic standards of outward beauty.

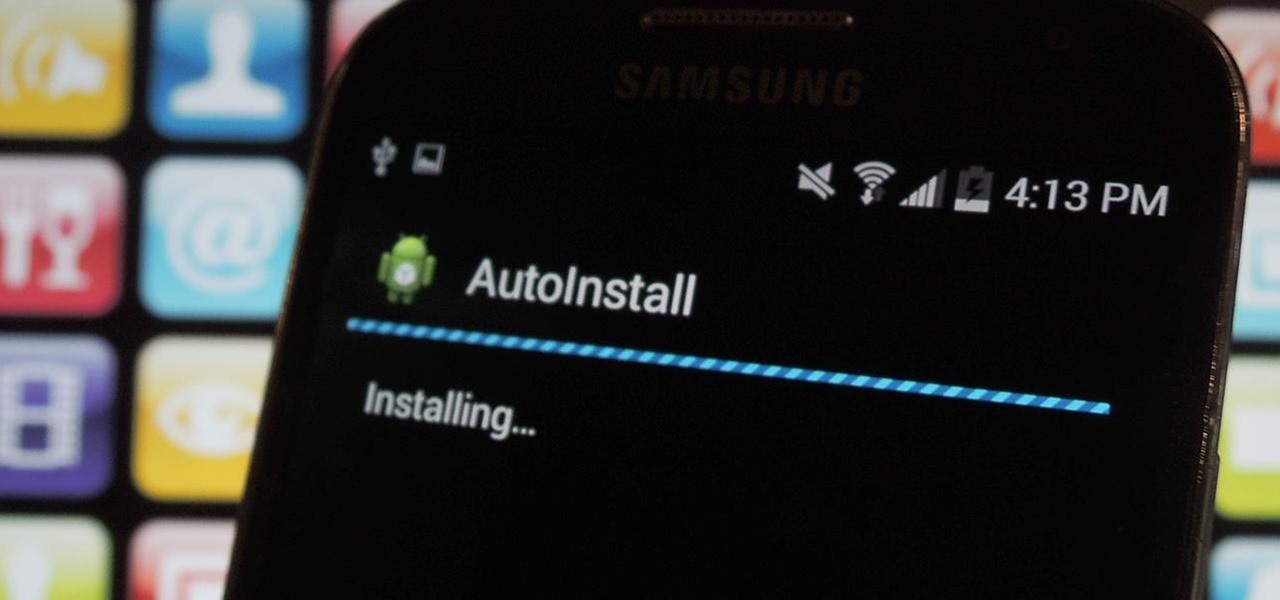
I'm always looking for the best apps and services for my Android, and that means sticking strictly to the Google Play Store is a no-go. If you're like me and tend to install a lot of APKs (application files), you're probably tired of seeing the "Install" confirmation that always pops up.

At last month's I/O event, Google demonstrated a set of cool new features that were said to be coming to the Chromecast soon. While we may not be able to set custom backgrounds or cast content without being on the same WiFi network just yet, the biggest feature of them all has started rolling out to devices today: Screen mirroring.

Applying for jobs can be a truly miserable experience. Sending out endless résumés, filling out those janky online applications, and creating cover letters can really wear a person down. So, any suggestions that make that process easier are always welcome.

While obvious, it's a lot more difficult to hack into a locked computer than an unlocked computer. As a white-hat hacker, pentester, cybersecurity specialist, or someone working in digital forensics, there's an easy solution — make it so that the computer won't fall asleep and lock automatically in the first place.