Grandmaster Henrik Danielsen explains the different lines in his F4-System, the Polar Bear System. If you need a new way to play chess, then this is just right for you. See what he has developed in this two-part video.

This video series explains how to charge and evacuate the air conditioning system in a vehicle. Lots of machines are involved so you won't be able to do this at home.

Covers installation of BMW X5 Subwoofer system for X5 00-06 (E53). Part 1 shows removal of original subwoofer (if present). Part 2 shows accessing the OEM amplifier and battery. Part 3 and 4 show amplifier connections. Part 5 shows amplifier power and ground for the subwoofer system. Part 6 shows fuse install, first amp sound test and amp mounting. Part 7, the final part, shows rear hatch assembly and final amplifier tuning.

The business world is currently figuring out how to deal with the coronavirus crisis, with many offices opting to work remotely for at least the next few weeks as a safety precaution. Predictably, this has thrown remote meeting software back into the spotlight, especially augmented reality solutions.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Another piece of Magic Leap's mysterious story has been uncovered thanks to a new patent application revealed on Thursday, March 15.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

Google is reportedly working on an iOS keyboard that brings key features to the iPhone, including Google's image and text search functions. (GIFs, yay!) According to The Verge, the keyboard has been in development and testing for months, and will act much like the Android version.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Hello again, and welcome back to another tutorial on functions, this time, covering recursion. What Is Recursion?

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

In general, smartphones and cars don't mix—but this is mainly because you have to take your eyes off the road to poke around on your handheld gadget. In reality, the only difference between your smartphone and your car's FHWA-approved infotainment system is that the latter is mounted in a fixed position and has an oversized interface that makes it easy to use without looking away from the road.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Welcome back, my hacker novitiates!

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

With the release of the Samsung Galaxy S5 right around the corner, the first full system dump has been released by Sammobile. As the inevitable ports of functioning apps slowly begin to leak, today we've got a non-app aspect of the system and the one that tends to leak first—ringtones.

Once you've updated your Nintendo 3DS to a recent version of the software, you'll be able to connect your 3DS and any of the older DS handhelds (such as a DSi). You can transfer content between the two devices using the System Transfer tool, as described in this tutorial.

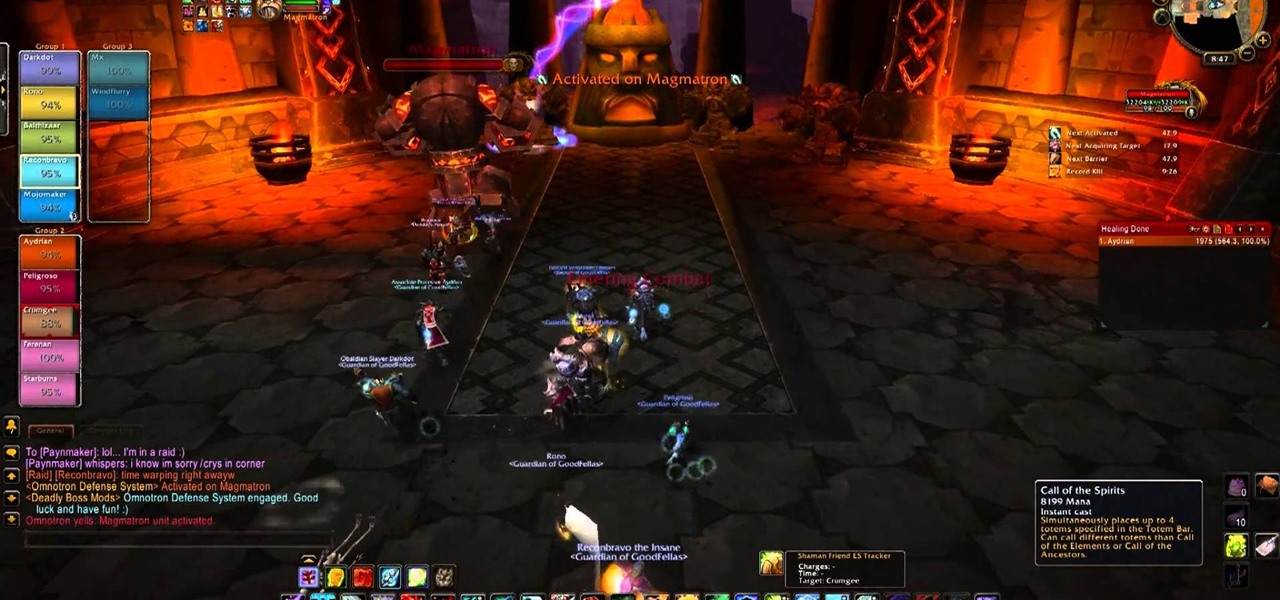
Blackwing Descent is one of the awesome new raids in World of Warcraft: Cataclysm, and one of the first gigantic bosses you'll find there is the Omnotron Defense System. Watch this video for a guide to killing it's big robot-spawning butt quickly and easily.

One of the coolest parts of DC Universe Online is it's tremendously complex super hero character creation system. The system i pretty daunting at first, but this video will guide you through making an awesome character that will be the envy of your guildmates online.

The CAGED system is an amazing way of organizing the fretboard to allow you to find any chord on any place of the neck and instantly have a shape to play on, a scale, a triad and even an arpeggio. In this video you learn how to apply the method with minor chords as opposed to major chords.

Have you ever wondered how all of the blood and dust that flies from wounds and bullet holes in Hollywood films gets shot through the air so convincingly? The answer is a pneumatic dust system. This video will show you how to make one yourself for almost no money, allowing you to achieve all sorts of cool special effects without any expensive digital technology.

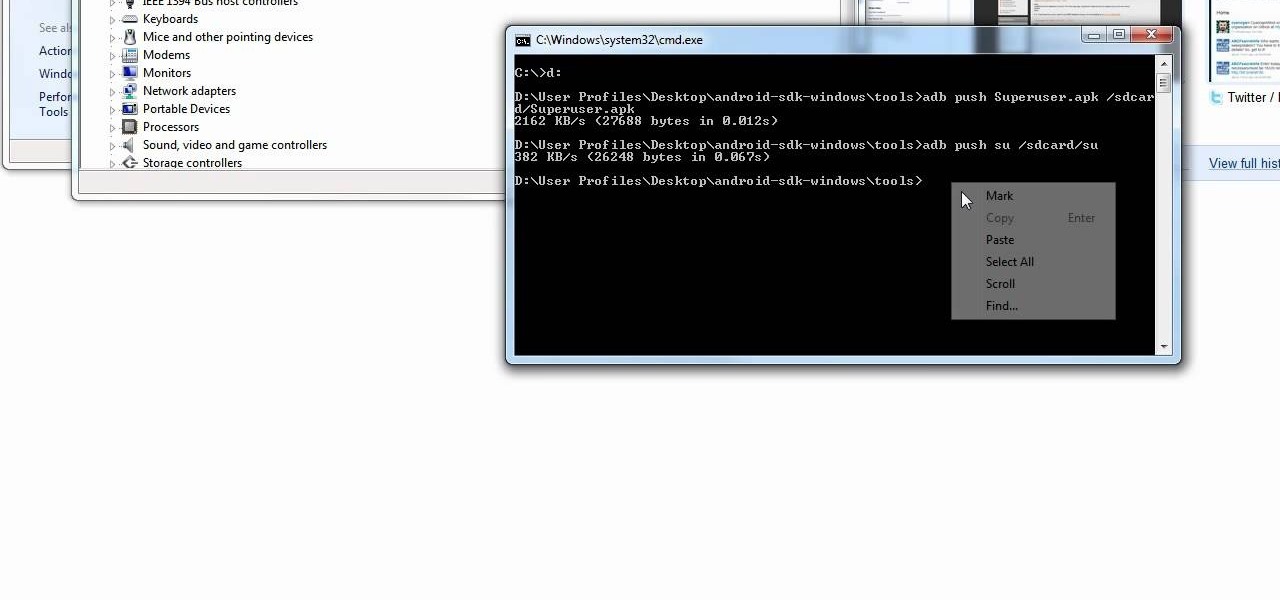
So, a lot of people seem to be having trouble rooting their Motorola Droid X smartphone from Verizon Wireless using ADB (Android Debug Bridge). Well, there is an alternative for those having problems with the ADB version. You will need to have a Wi-Fi or Bluetooth widget handy for this hack. If you follow the instructions in the video, you'll have a completely rooted Motorola Droid X cell phone. Try it out.

Yes, the Droid X from Motorola can be rooted, and yes, you can do it at home. Just make sure you follow the directions precisely. If you succeed, you'll have a completely rooted smartphone. eFuse doesn't matter. If you want to expand your options on Verizon Wireless's Droid X, then you just have to take a chance… use this video in conjunction with the links and description below.

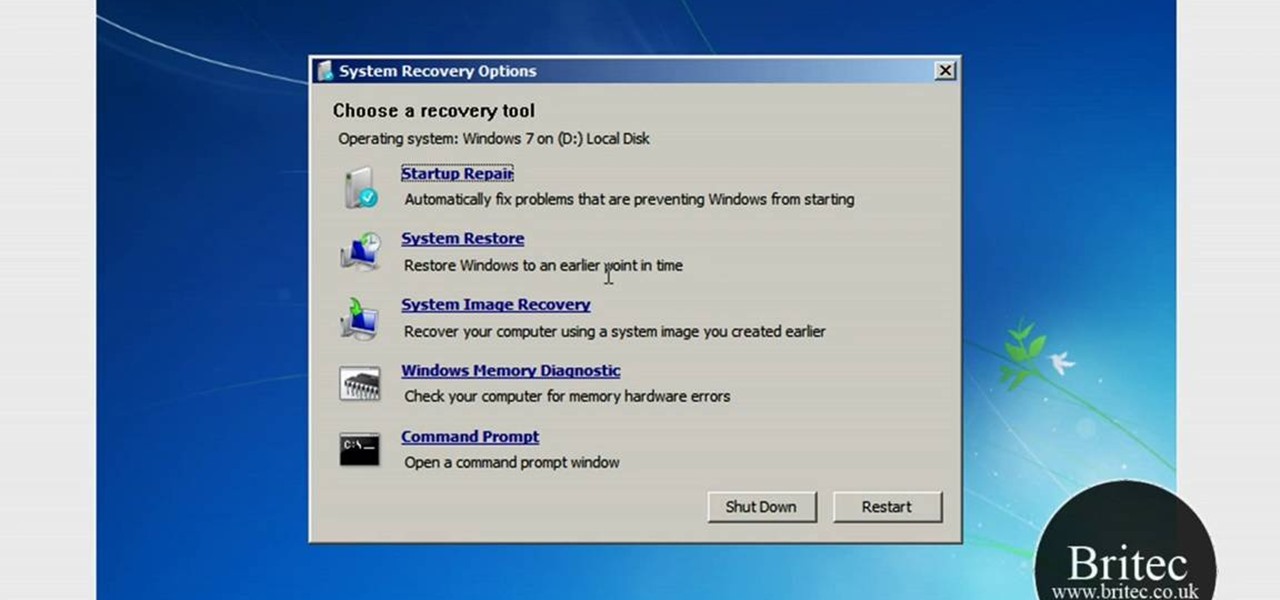
This video tutorial from Britec09 presents how to backup and restore Window 7 registry.First, press Start button and enter regedit command into Start Search area.Registry editor window will open, click File-Export.This option works on all Windows operating systems.Type file name - registrybackup and click Save. You can save it wherever you want, but in this video it was saved to Desktop.Next step is to reboot to Windows DVD. Insert you Windows DVD and reboot computer.Press any key to boot fro...

Mark Wallace shows how to set up a pocket wizard system and use mixed lighting for photography.

From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier than ever to follow in their footsteps (or just finish your homework or study for that next big test). With this installment from Internet pedagogical superstar Salman Khan's series of free math tutorials, you'll learn how to solve non-linear systems of equations in algebra.

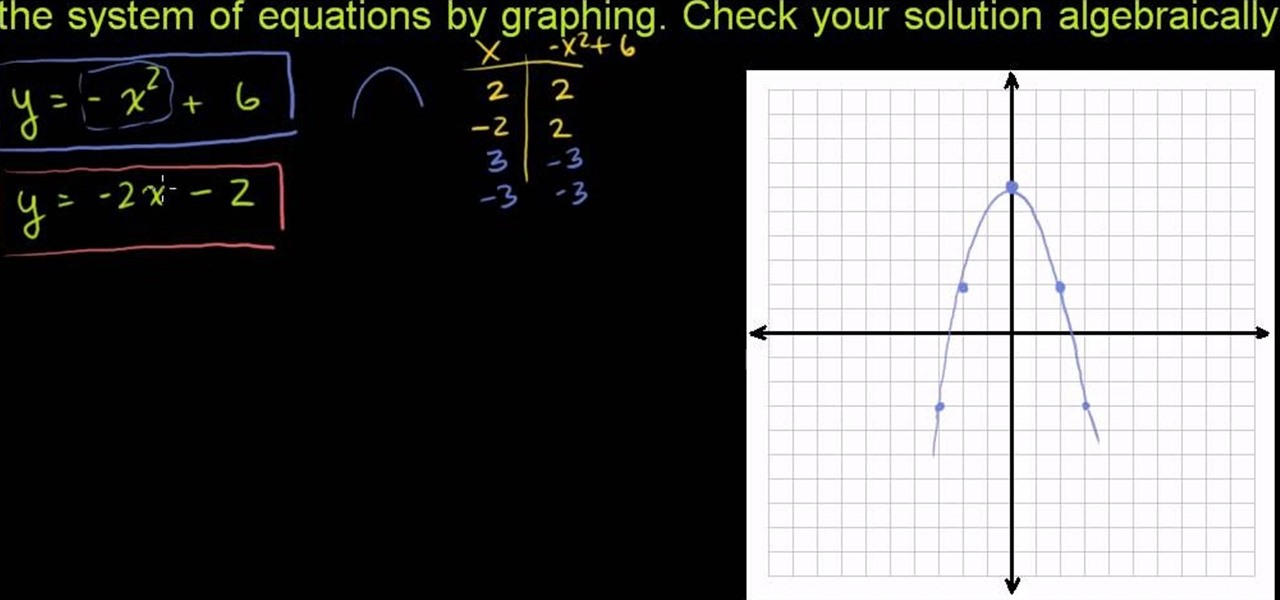
System of equations is nothing but a system which contains more than one linear equations. This system of equations can be solved to arrive at the solution of the system. A simple system of the linear equations can be a pair of equations. To solve this kind of system you can employ the substitution method. So take the two equation of the system. Solve for the value of y in the first equation in terms of x. Now take this value of y and substitute in the second equation y value. Now the second ...

Driving around and notice an accident the road keeping you from getting where you need to go? Well, you're in need of a GPS navigation system. Check out this video tutorial on how to Use media functions on a TomTom Go 930 Traffic navigator device. You'll see how to use the GPS system in details and see all of the key features of the Go 930 TomTom, like playing music, listening to audiobooks, and watching videos.

In this video tutorial, viewers learn how to reformat an Acer computer hard drive. Begin by clicking on the "Empowering Technology" logo on the top of the screen and select Recovery Management. Then click on the Restore button and click on Restore system to factory default. Enter the password if you have one and click on Yes in the next process confirmation window. The system will begin to shut down. Now just wait for the computer to finish loading up and input all the system information. Thi...

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

Now that we're feeling the full force of Jack Frost's chill, scarves are the perfect fashion accessory, balancing that fine line between function (keeping our necks warm and toasty) and form (since they're oh so cute). Check out this fashion styling video by Michelle Phan to learn seven different ways to work your neck wrap.

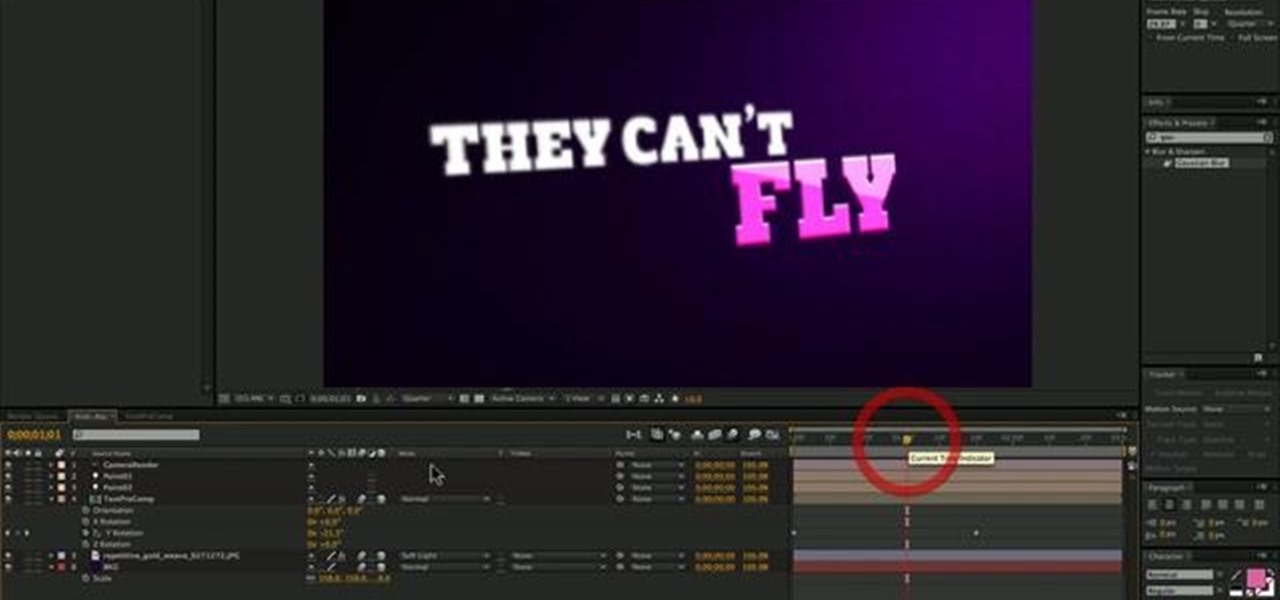
This tutorial uses a title screen from the Kick Ass trailer as its inspiration. Learn how many of the tools, functions and processes work within Adobe After Effects by completing this tutorial. You'll be an AE master by the time you're done.

Wait, a query within a query? This function is possible within the framework of MySQL. Learn how to correctly implement a subquery or sub select in your next database project and avoid a couple perils that will make your program unstable.

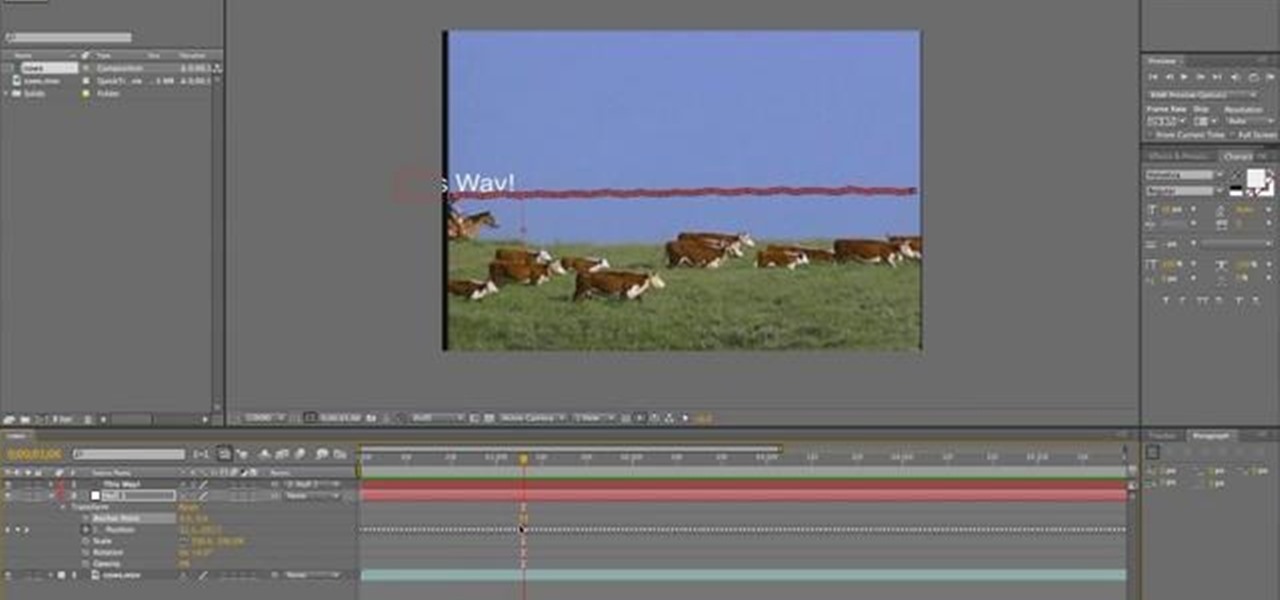
Learn the fundamentals of position tracking in After Effects in this informative 5 minute tutorial from Patrick Carter. This video lesson involves attaching a text object to a moving cowboy on screen to demonstrate the basic transform tracking function.

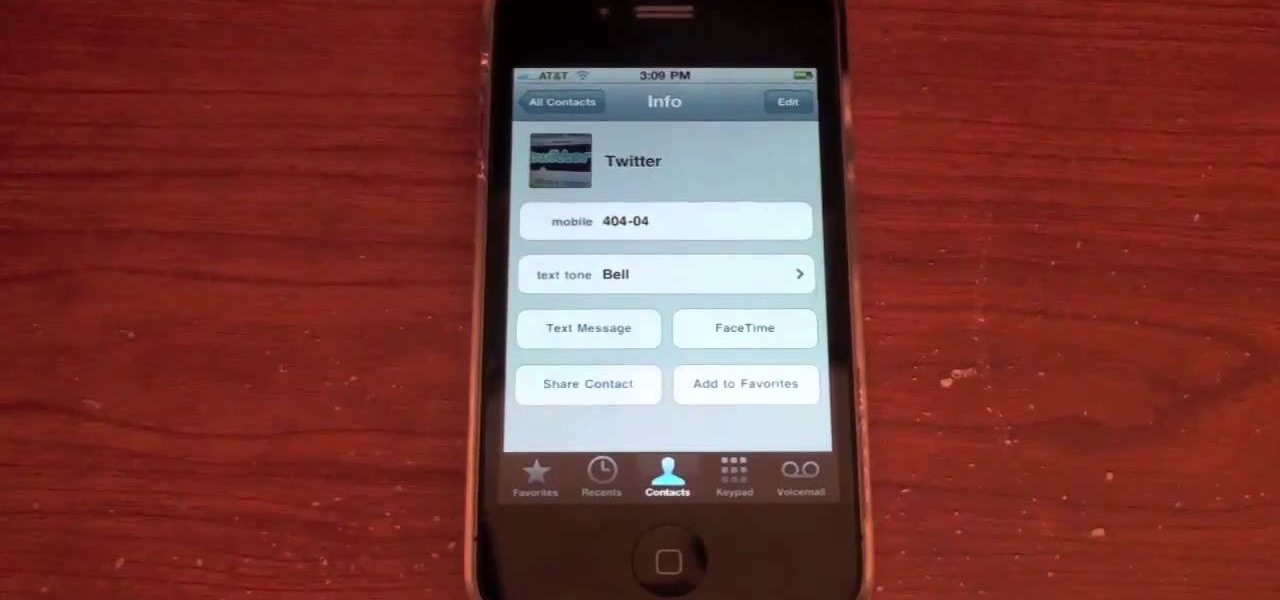
It took all the way until firmware version 4.2 for Apple to add a function to the iPhone that's been present on other phones for years: the ability to set custom ringtones / sounds for text messages from different contacts. This video will show you how quick and easy it is to set this up on the new firmware.

A remote control for a camera? Why not! You won't have to worry about racing the timer function any more! Build a remote control for your digital camera that will take the picture whenever you want. The range is as far as two miles!