Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

Regardless of where you happen to live in the United States, you can always count on Caesar salad being on a menu nearby. The restaurant may be top dollar or a humble diner, but this ubiquitous salad prevails in every region and at every price point.

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.

If you've ever spent any serious time examining the Chinese tech startup world, you know that it moves fast — very fast. The tech startups hailing from Beijing and Shenzhen are moving so fast that they're now in serious competition with Silicon Valley.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Hey, all you Instagram lovers, haters, or people who have no choice but to submissively bow down to the social app giant for other reasons, you've come to the right place. Today, I'm going to walk you through a very simple marketing trick to start boosting traffic to your IG account.

Hi everyone. Recently I've been studying some topics about Assembly, memory and exploitation, and thought I could write something nice, easy and fast about it, just because I like to share what I learn, and probably sharing what you learn and trying to explain it to a stranger is the best way to learn it better. It worked for me, and I hope it will be useful for you too.

For 2019, Sony is trying to shake its failures of the past and start fresh. Following the unsuccessful Xperia XZ series, Sony is changing the name of their flagship to a single number: Xperia 1. With the name change comes a few upgrades, one of which is its new look. Secondly, its new display is unmatched in the mobile space.

It's that time of year again. No, not Thanksgiving. Black Friday. There are a lot deals available this holiday weekend, many of which include flagship Android devices. Whether you are thinking of buying a phone for yourself or looking for a gift for someone else, you can find a little savings to shop smart during the holidays.

After delaying its launch by four months, LG revealed its 2018 entry to the flagship market on Wednesday, May 2. After years of an underperforming mobile division, the LG G7 ThinQ is the first product since a shakeup within the division to get things back on track, and it brings a number of upgrades over its G6 predecessor.

So now that we know what the iPhone 13 and iPhone 13 Pro and their respective mini and Max versions are all about, you've probably made your decision on whether or not to upgrade (or swap over from Android) during this cycle.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

I don't know how many of you had this experience in your youth, but when I was a kid, I used to actively think about what would happen if I suddenly woke up in a fantasy land, or were to pass through a portal into another space and time. I knew it wouldn't really happen, but when you're a kid, these can be important issues to you. So I slept with my glasses on every night, just in case. Photo from George Pal's The Time Machine.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

There are a lot of Android phones out there, and chances are that someone in your life is looking for one this holiday season. Well, there also happens to be a lot of Black Friday deals on Android phones this year. So we've rounded up the best deals taking place on Black Friday weekend to help you save big.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

Traveling abroad can be a hassle. Between the flight, hotels, food, and the languages barriers, it can be a lot to manage. There's one tool you have that can help with all of this — your smartphone. Fortunately, nowadays, you don't have to change your carrier to continue using your phone.

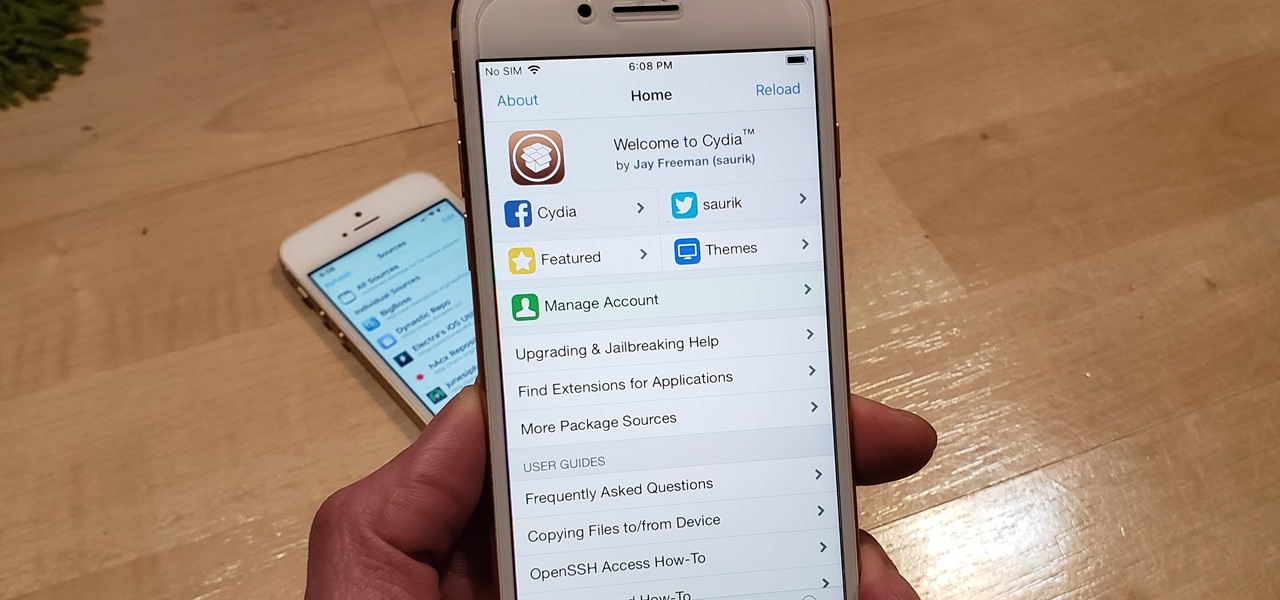
With Unc0ver, Pwn20wnd was the first to jailbreak an iPhone and iPad running iOS 12 versions. While it initially couldn't work on all devices, it's an entirely different story now. Unc0ver currently works up to iOS 13.5 for most A7 to A13-powered devices. Plus, Chimera, another jailbreak tool, supports a similar range of models on iOS 12 to 12.3 and iOS 12.4.

You can feel it in your bones. You may die if you don't get this phone. There's just one problem — the price. Suddenly, you come across what seems like manna from heaven. That very device, at a deeply discounted rate, can be yours.

I hesitate to even post screengrabs from this piece. The storytelling by this creative team (dir. David Altobelli & DP Larkin Seiple) is so perfect that taking stills out of context doesn't do it justice. At first, I was disappointed that the automatic thumbnail Vimeo chose was so nondescript but ultimately it's for the best. Here's just a tease:

In this video tutorial we will see how Stuart Little "lights up" a lighthouse inside a photo. You will learn how to use the lighting filter command within Photoshop to do the trick. After learning it, don't hesitate to experiment on "lighting" other buildings! Click on the screenshot of the video and it will generate a larger pop-up of the actual video. Light up a lighthouse in a photo using Photoshop.
My name is Elvis. I'm from Film & Theatre Arts charter high school. I'm in this world to help people become better poets/writers. I'm going to help Serigo make this world better, adding different things, and giving advice on how to express yourselves better. I'm also going to be putting up some of my own stuff wether it's poetry or music, I've made myself. I'm heard to help so if anything is need don't hesitate to ask.

As a follow up to my article 10 Time Saving Menu Bar Applications for the Mac, this video covers Butler, one of my favorite menu bar applications. Produced by ManyTricks.com, Butler can help you quickly launch applications, websites, and other items on your Mac. It also includes a web search feature, a clipboard manager, a hot key launcher, and much more.

Curious about the newest obscure zines to hit the streets? Words and Stuff is a great website full of reviews on zines (mostly in the punk, politics, eroticism, and art arena) that either give the thumbs up or the thumbs down on what's worth purchasing.

What's a football game without a touchdown? And what's a cheer without the right touchdown move? Learn 3 moves that will have you bringing the crowds to their feet! Follow along and learn how-to do t's, touchdowns, and diagonals for cheerleading.

Hi everyone This is something that I should've done the first day but hey...better later than never right?

One of the many reasons Circuit City should go out of business is their sale of ridiculously expensive cables, wire and cords. The secret to the industry of Monster Cables is that it is unnecessary and ineffective. Gold-plated or otherwise, Monster's $100 cables are not intrinsically better than the cheaper versions they're stocked next to. Don't believe us?

Map Tutorial for Ninja Saga Kage Room

What do you expect Israel do say when a suicide bomber from Sweden kills travelers on a bus at such a high point in tension between the US, Israel and Iran?

This how-to video discusses various modes of window management in Windows Vista. Learn how to use the hesitate, alt-tab and flip features. Never again will you need to engage in the laborious process of cycling through each minimized application window by mouse click. Switch, or flip, between windows in Windows Vista.