The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

While self-driving cars appear to be as inevitable as augmented reality headsets, the auto industry and its technology partners likely have years of testing to complete and regulatory loopholes to jump through before self-driving cars hit most highways.
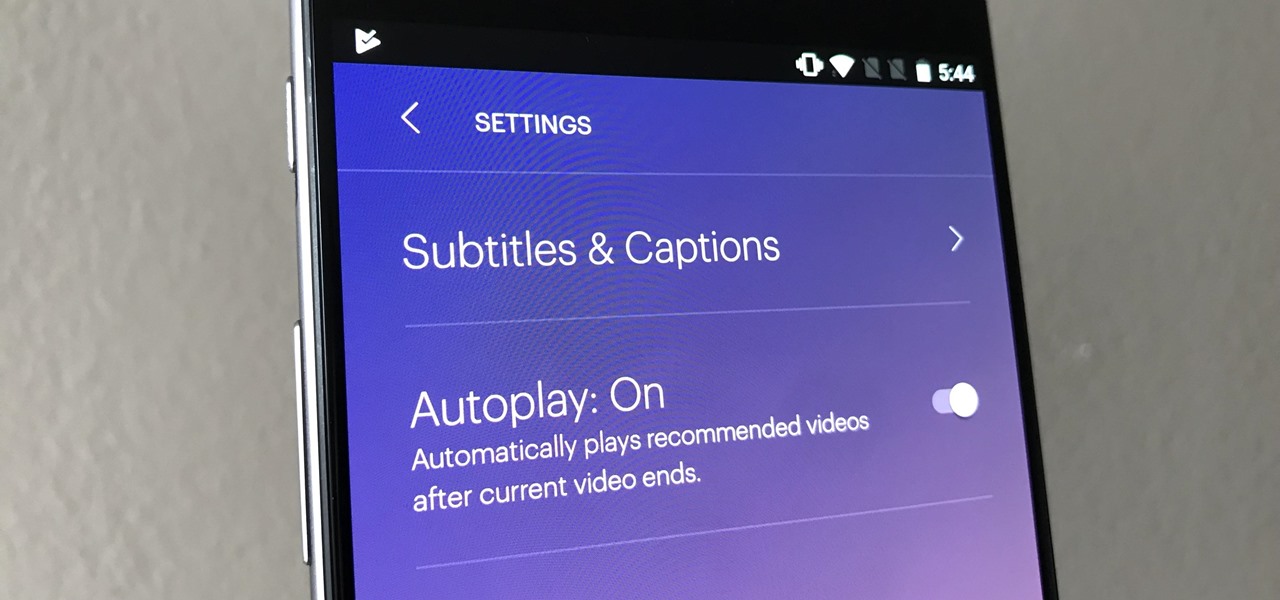
We use subtitles when we can't understand what's being spoken on screen, but most of the time it seems like those subtitles are out of our control. Maybe we find them too small, or even too large. Maybe the color is too faint, or the background too distracting. If only we could change the subtitles to reflect our own needs and styles ...
In the first part of this series, we looked at the surface detection that is provided by the ARKit. We looked at how it worked and covered some of the tools that could help us determine what is not working; when it doesn't. Now let's take this to the next step.

At Apple's yearly event, the World Wide Developers Conference, the tech giant finally announced their decision to enter the augmented reality space. Through adding basic AR functionality to the beta release of Xcode 9, the development environment for Mac computers, as well as their line of iOS devices, the company has said they understand the importance of the tech.
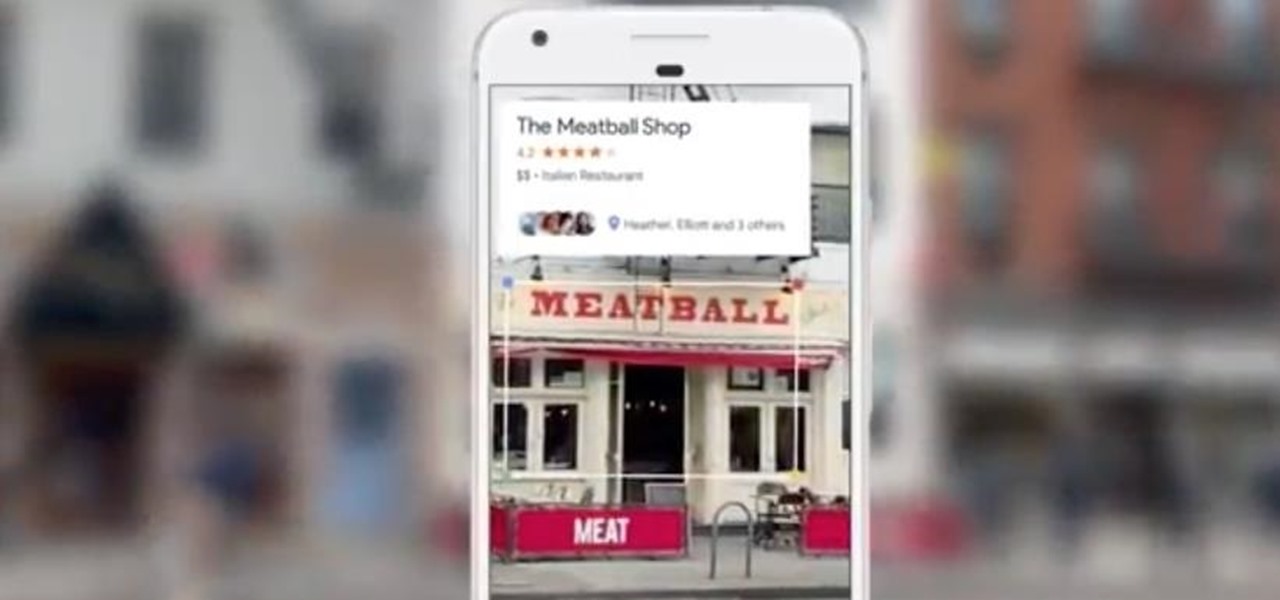
Google Assistant will be getting an AI makeover with the addition of Google Lens. This new feature is basically a set of vision-based computing capabilities within the Assistant.

Onshore, or on a boat, have you ever wondered what swims below in the dark water? Using standard equipment and a new process, marine scientists can now get a good look at what is swimming by—just by analyzing the water.

There's now more reasons to make sick workers stay home—a new game theory study suggests adequate hand washing and other illness-aversion tactics aren't as useful as we thought to keep you from getting infected when a virus or bacteria is circulating.

To shine light on the future of the relationship between humans and viruses, a team of researchers from the University of Oxford looked into the dim and distant past.

We've explained the differences between mixed, virtual, and augmented reality through old-fashioned text and infographics, but in a rapidly-changing environment that leads to even more terms, it's best to think of all these realities in one simple way—as a continuum.

When you wear a holographic computer on your face, you gain some things and lose others. That's certainly the case when using Skype in Microsoft's HoloLens. Some video chats will work better because your caller can see what you see, rather than your face—but others just feel weird.

Google I/O is right around the corner, and everyone's expecting new virtual and augmented reality news. Here's what to expect from this week's announcements.

So you dropped your smartphone and the screen cracked. Again. Just the thought of sending it out for repair or buying a new phone is driving you mad.

Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PHP instead of C#).

Before I continue with a topic on strings, we first require some fundamental understanding of how memory works, i.e. what it is, how data looks in memory, etc. as this is crucial when we are analyzing vulnerabilities and exploitation. I highly suggest that your mind is clear and focused when reading the following article because it may prove to be confusing. Also, if you do not understand something, please verify all of your doubts, otherwise you may not completely understand when we touch on...

Hello again! In this tutorial, we are going to go over something called "operators" which will help us build upon conditions of control structures and also some variable manipulation. Without further ado, let's dive in!

Samy Kamkar, the security researcher known for the MySpace Worm and his combination lock cracking skills (using an online calculator), is back—and this time, he's after your credit cards!

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

Hi everyone! In the previous part of this series, I introduced one way to hijack a program's execution flaw, though I only showed you how to crash the program and left you with a little mystery to solve. Today we are giving the solution of that and then introducing shellcode usage and remote command execution.

Hi everyone! Last time we explained what roles Ebp and Esp registers have. We first introduced function's stack frame building, return address and calling conventions, but left some of the concepts floating without a full stop.

Hello readers, and welcome to Null Byte. Before we start, for those of you who may not know me, my name is ghost_; I'm a relatively active member of our community and have been around for a while.

From parents and other family members to friends and peers, personalities are built by environment. Though people are important in the development of our own individual personality, there are other, different influences, including what you choose to read. The books you take the time to enjoy can make you nicer and more understanding, or leave you overall unchanged.

While CNN, FOX News, and MSNBC are valuable sources of information for what's going on in the world today, they may not be the best news stations to watch if you actually want to learn something. They, along with local news stations, are great at grabbing your attention, but if you truly want to learn something about recent events, you're tuning into the wrong channel.

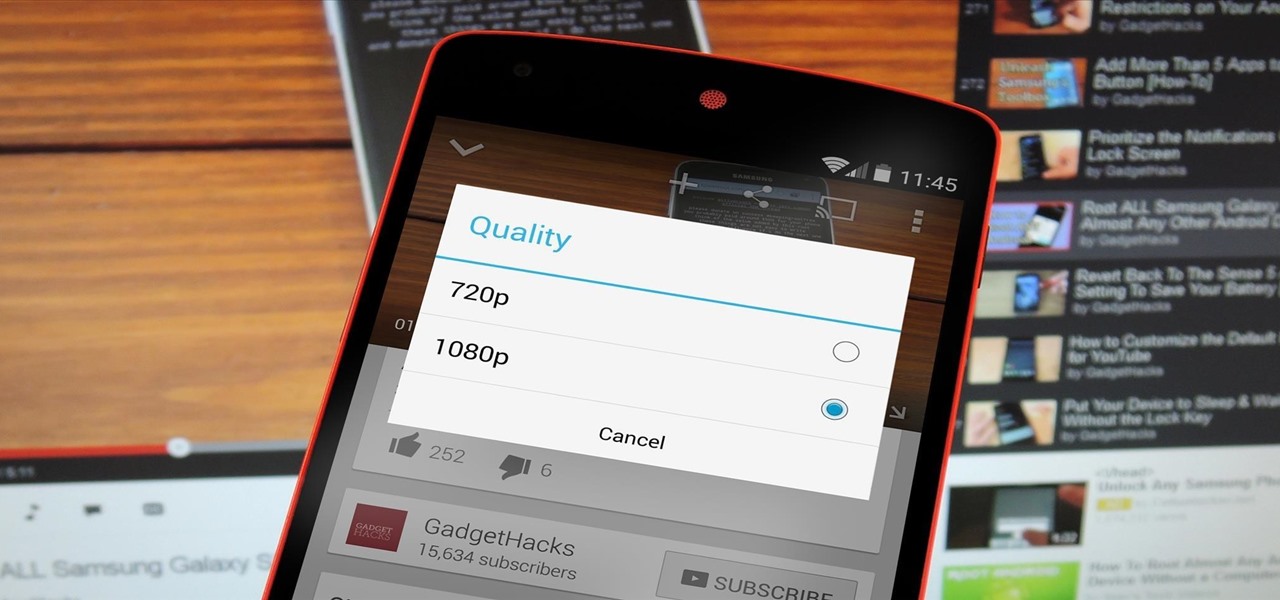
The Nexus 5 and Nexus 7 (2013 edition) boast beautiful 1080p screens that are capable of displaying images and videos in ultra-sharp high definition. But for some strange reason, the YouTube app only allows for streaming of 720p content on these devices. It's not a limitation of YouTube for Android, since other devices support 1080p playback out of the box, and some, like the LG G3, even support higher resolutions.

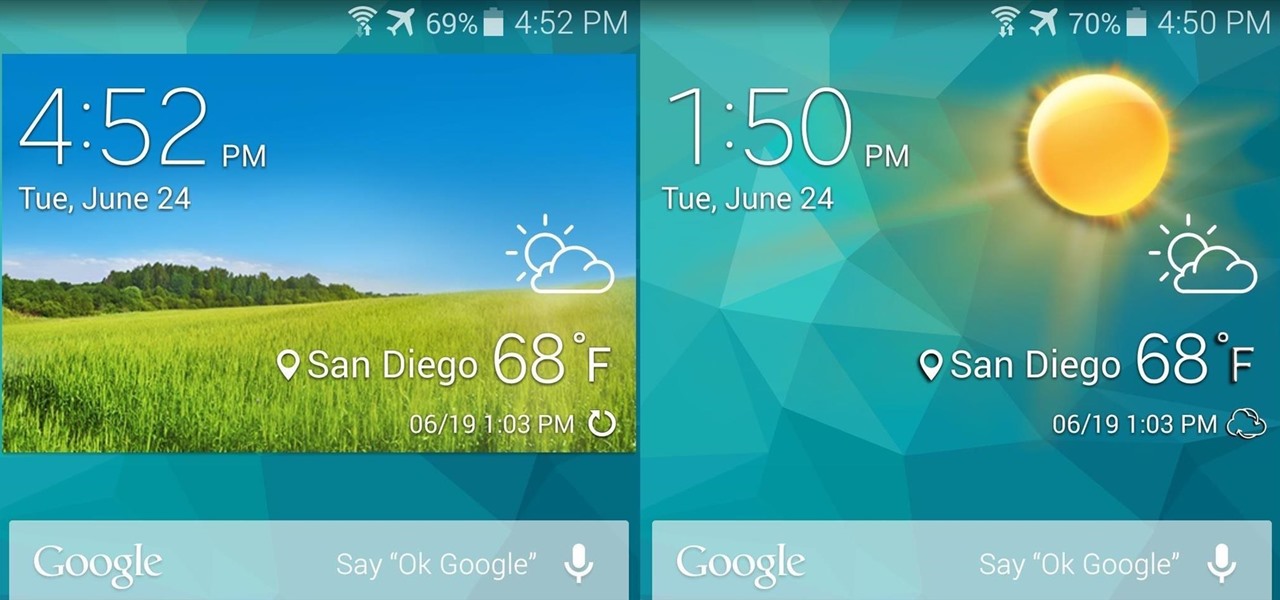
The weather widget on the main home screen of a fresh-out-of-the-box Galaxy S5 is meant to show off the screen. Super-high contrast and crisp definition on the individual blades of grass in the background let you know that the phone you're holding has one helluva display.

As this generation continues to evolve, we become more involved with social media. For example, you may have a Facebook, Twitter, and a Google+ account, and be heavily involved in using all three, but the constant switching between sites, logins, and conversations can get very tedious.

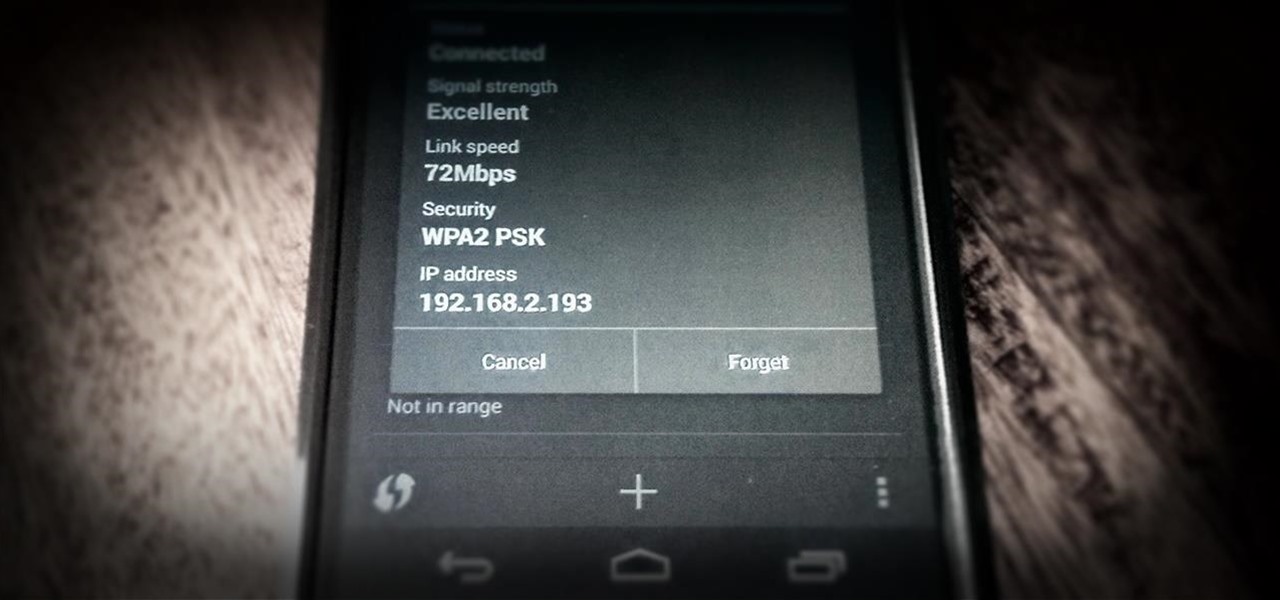
One of the most common complaints that people have about the Nexus 4 would have to be its intermittently poor Wi-Fi performance, a problem that for many, persists through the installation of updates and even custom ROMs.

Think eating food is as easy as putting it in your mouth? It's considerably more complicated than that. Your brain plays a big role in determining what and how you eat. Understanding how your brain interprets food choices is key to managing your eating habits.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

The vast majority of people involved in Steampunk are interested in history but, like with science, there's something about history that we don't talk about very often: The holes.

Steampunk is a tremendously interesting phenomenon because of its reliance on science fiction, and fiction in general. Steampunk can arguably be broken down into two categories: the fiction, and the aesthetic. Sometimes these categories cross over, but they're often more distinct than most people suspect; that said, the aesthetic is firmly based in works of fiction.

Conflict is a part of life but how you deal with that conflict is up to you. You may find yourself in an argument and instead of making it a shouting match, employ some techniques that will be sure to keep this conversation civil.

Merrill never fails to amaze. In this video, he instructs you to "come as you are— but bring a pencil." And you don't have to be a diehard Nirvana fan to understand what this tutorial's about— Kurt Cobain. Watch and learn how to draw Kurt Cobain in a portrait, step by step, using pencils and a few art tricks.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

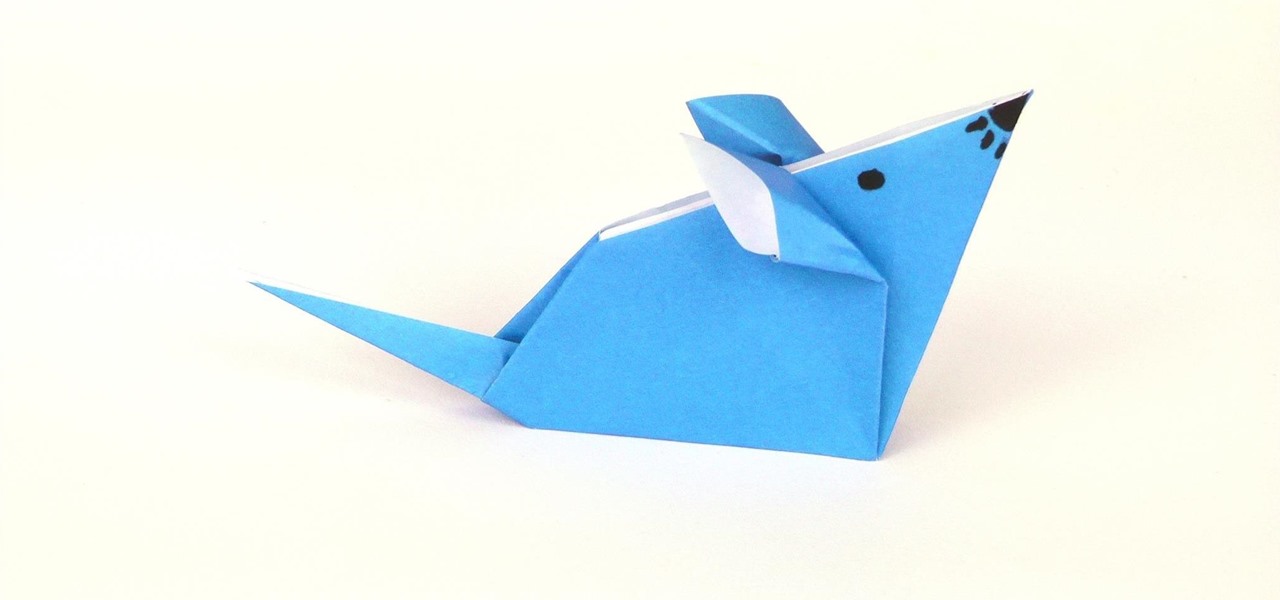
This tutorial teaches you how to fold an origami mouse with an ordinary sheet of paper. This model is suitable for beginners and children. Origami is great for small kids as the only material needed is paper, no scissors or glue that could do harm!

In this detailed, creepy, video series you learn and understand the fundamentals of having an Out of Body Experience (OBE) or Lucid Dreaming. Everything from a clear explanation fo "The Phase", getting started, deepening of the experience, and much more.

Math is one of those subjects in school where you either love it or hate it or just don't get it. But math is nothing to fear, because it's a part of our everyday lives, and ifs something everyone should know the basics of. Don’t let math intimidate you. Whether you’re multiplying two fractions or a fraction and a whole number, solve the problem without a calculator in just a few steps.

She thinks just because you're related that your closet is her closet; and if she ever gives your things back, they're never washed. If it's time to stop your sister from being a closet bandit, check out this video. This tutorial is full of tips for gettinf rid of that pesky sibling and keeping your clothes all to yourself.

The name of your business will leave an impression on people as this is probably the first information they will receive. Make sure to express yourself and give the impression you intend by choosing the best name for your business.