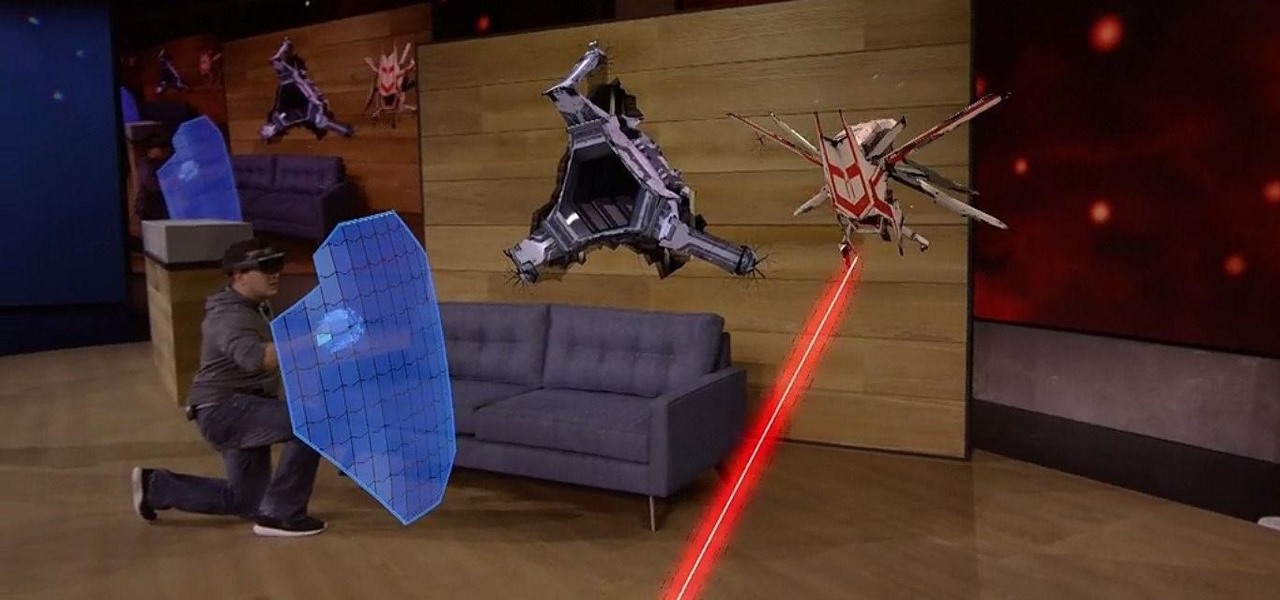
In an early morning blog post, Microsoft announced the expansion of the Microsoft HoloLens Agency Readiness Partner Program. This announcement comes on the tail of an expanded HoloLens release over the last few months to many countries outside the initial US and Canada.

New research suggests the bacteria that causes listeriosis may be a bigger threat in early pregnancy than previously thought. Usually considered a danger to late pregnancy, scientists suggest early undiagnosed miscarriages could be caused, in some cases, by infection with Listeria.

We live in a marvelous age, a time where technology is driving us forward as a species at a rapid pace, and tech-driven miracles are becoming more and more commonplace. While the human race may not be focused on building the largest wonders of the world, as it once was in history, the current order of wonders are much smaller in scale—even internal.
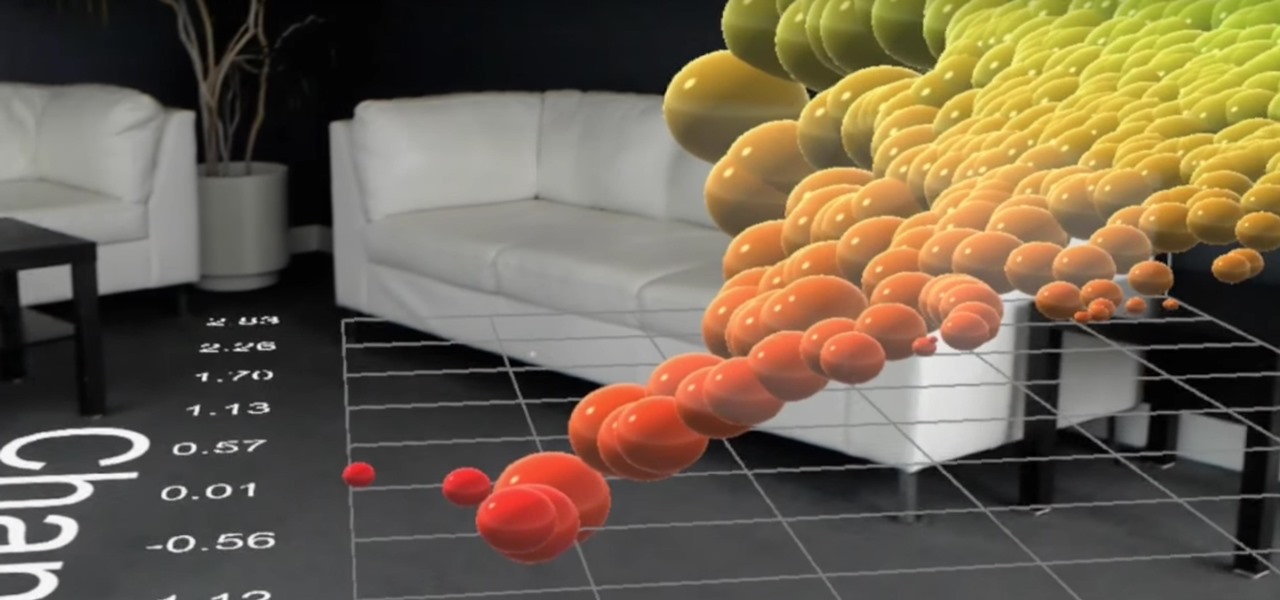
HoloLens developer Michael Peters of In-Vizible has released quite a few videos since receiving his HoloLens last year. Many of his experiments are odd and funny, but some include serious potential approaches to data visualization. In the videos embedded below, you'll specifically see stock market information beautifully rendered in different ways to help understand the data.

Transmitted by a sandfly one-third the size of a mosquito, parasitic Leishmania protozoa are responsible for a flesh-destroying disease that kills an estimated 20,000 people per year. Two new studies offer understanding of how the parasite provides immunity through persistence and why some people suffer more virulent forms of the disease.

Where in the world did it come from? All of a sudden, one day, someone had an infection with flesh-eating bacteria. It captured headlines and worldwide attention because it was such a severe, strange, uncontrollable, and really disgusting condition.

The largest and arguably most widely known event of its type, especially in the US, the Sundance Film Festival is an annual celebration of independent film—ones made outside the Hollywood system. This year, a new type of experience appeared at the Sundance Film Festival in an installation called "The Journey to the Center of the Natural Machine." This mixed reality presentation offered the user the newest type of storytelling in a long and important line—continuation of the species kind of im...

Lighthouses and signal fires may have been the first social media. Without the ability to share language, a distant light meant "humans here." A new study from the University of California, San Diego, finds that bacteria can also send out a universal sign to attract the attention of their own, and other bacterial species.

One thousand feet under the ground, extremophile microbes that have not seen the light of day for four million years are giving up some fascinating facts to scientists who go the distance.

Here at NextReality, we talk a lot about the many different ways of controlling holograms in the HoloLens and other augmented and mixed reality devices; New and creative ways are coming more and more every day. Most recently is something called the HoloSuit. In the 25-second clip below, you can see a woman moving the arm of a jacket which in turn moves a 3D model of Darth Vader on the screen. It's a simple idea with big potential.

Findings from a mouse study suggest that the Zika virus infection may have serious reproductive consequences for men.

Today, December 7, it was officially announced that Magic Leap has found their replacement for the recently departed Brian Wallace. Magic Leap CEO Rony Abovitz has tapped Brenda Freeman, former EVP and Chief Marketing Officer of National Geographic Channel, as their new Chief Marketing Officer.

People have been transforming mud into art, aka pottery, for thousands of years. This is not a new phenomenon, but often the finished product has a certain utilitarian aesthetic, such as a bowl or vase.

Visualization is one of the obvious commercial applications for technology such as Microsoft's HoloLens. The ability to see the assets of a project in different scales—from micro to larger-than-life—with a quick air tap will play a large part in the coming augmented reality revolution. Whether the assets are art for a game, interior design, raw financial data, or architecture, data visualization will play an important role in the future. This is due, in part, to our ability to absorb informat...

In recent weeks, Unity has made a few great leaps forward for HoloLens development. These new features will increase iteration speed inside Unity and quickly increase the output of applications in the mixed reality space. Of these new features, let's take some time to talk about Holographic Emulation and why this will do so much for the development community.

Snapchat has already found a compelling way to create advertisements in augmented reality with their branded filters, but they continue to experiment with new ways to monetize the bridging of the real and digital worlds. Their latest idea, which requires users to "snap" an image to unlock content, could succeed where QR codes haven't.

In Pokémon GO, having an in-depth understanding of your Pokémon's stats and abilities is crucially important to becoming a better player. Not all Pokémon are created equal; as such, it's critical that you look at each of your Pokémon—even duplicates—with a keen eye.

The internet, as I understand it, is a wonderful, magical place where people congregate to share memes and viral videos. Well, okay... there's a lot more to it than that, but let's just focus in on the good stuff.

Microsoft's HoloLens has many applications in the business world, both large and small, but what about gaming? Initial demos gave the impression that we could expect amazing first person shooters, platformers, and even Minecraft. Yet, as Newsweek noticed, the HoloLens was nowhere to be found at E3 this year.

Even for an avid egg enthusiast, a popular dish like scrambled eggs can get tiresome if it's on repeat in your breakfast rotation. For an unusual way to add some oomph to your œufs, consider adding a squeeze of lemon to your scramble. Read on to understand why this seemingly odd suggestion will boost your eggs' flavor.

We're already glimpsing the future when we look at mixed reality through a headset, but is the real evolution of this technology something that will exist as part of our bodies? As intense as that may sound, TechCrunch's Jay Donovan offers compelling reasons why it's not such a crazy idea:

Microsoft's HoloLens is certainly a leap into the future of mixed reality interfaces, but it's not without drawbacks.
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.

We've all been there—you're away from home, your phone's battery is quickly nearing zero, and you forgot to bring your charger. "Hey, does anybody have an iPhone charger?" you ask. Crickets. If you could understand cricket-speak, you'd know that they too were saying "Sorry, bud. We're all on Android."

Hello ladies and gentlemen, welcome back to the Part 2 of our UDP & Wireshark adventure as I promised. Last time we discussed about what DNS is and how it uses UDP as its transport protocol but we left some unexplained parts behind and I'm about to investigate those with you. I would advice you to go back to Part 1 so you can have a clear understanding in case you don't feel comfortable with the topic. So our computer made its request to the DNS server and asked "Hey, I want to find out what ...

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

Right, So i've been asking alot of questions here on Null-Byte and everyone has been really helpful to me.

This is not essentially the next part in the series, but an expansion of previous part about why should you not use cryptocurrencies.

Apple's once flawless mobile operating system has seen its fair share of bugs recently. From Messages and Wi-Fi settings crashing to having your photos and contacts exposed, iOS has been standing on shaky ground for a while now.

I've been doing tutorials on Rasberry Pi and I would like to thank everyone that have both read the tutorials and gave me feedback on how well I'm doing. But now I've decided to take a small break and start a mini series that I'm hoping to be at least five tutorials. This doesn't mean I'm gonna stop posting Raspberry Pi tutorials, but since I'm learning so much at the same time I've decided to share some of that knowledge. Hence this tutorial. Please sit back, relax and read on.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

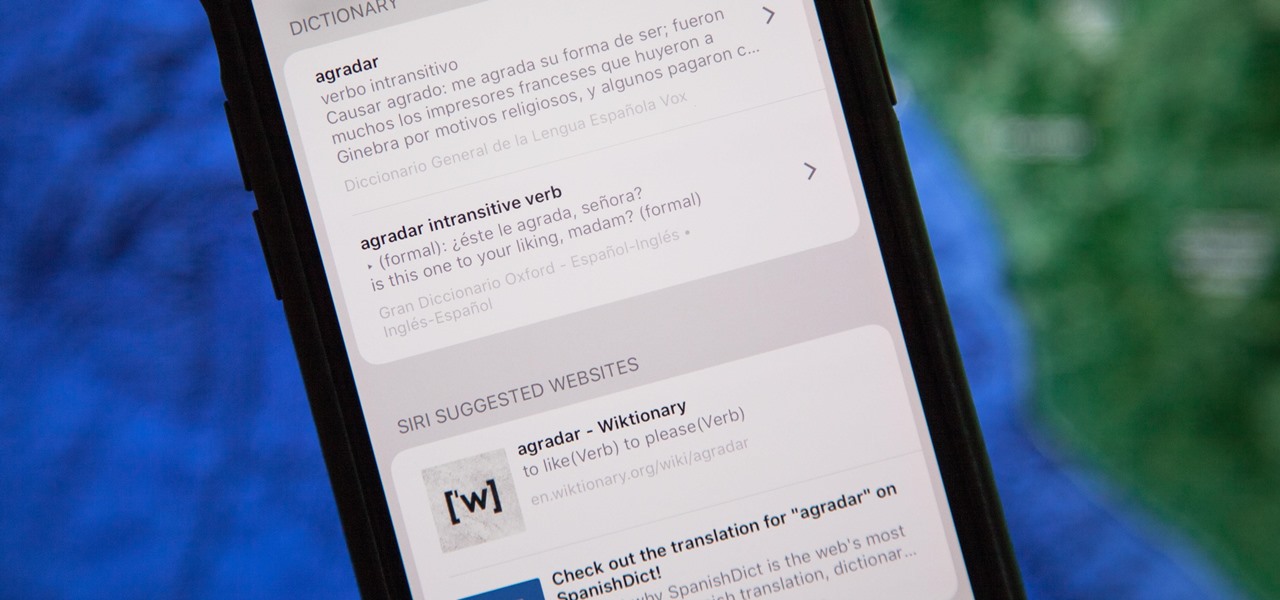
The native dictionaries in iOS, which have been around since 2011, let you define words on your iPhone on the fly in Safari, News, Notes, and other apps. But if you read or write in more than just English, you won't be able to see accurate definitions unless you add those other languages to your list of dictionaries manually.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

In previous tutorials we have encountered these things called pointers and addresses but we still don't know what they really are. Let's learn a bit more to clear things up.

Just last month, Microsoft announced plans to take away a huge chunk of storage from the free tier of their OneDrive cloud service, and users are understandably quite upset. At the same time, they reneged on an offer to give Office365 users unlimited OneDrive storage, and instead, will only be offering 1 TB of storage.

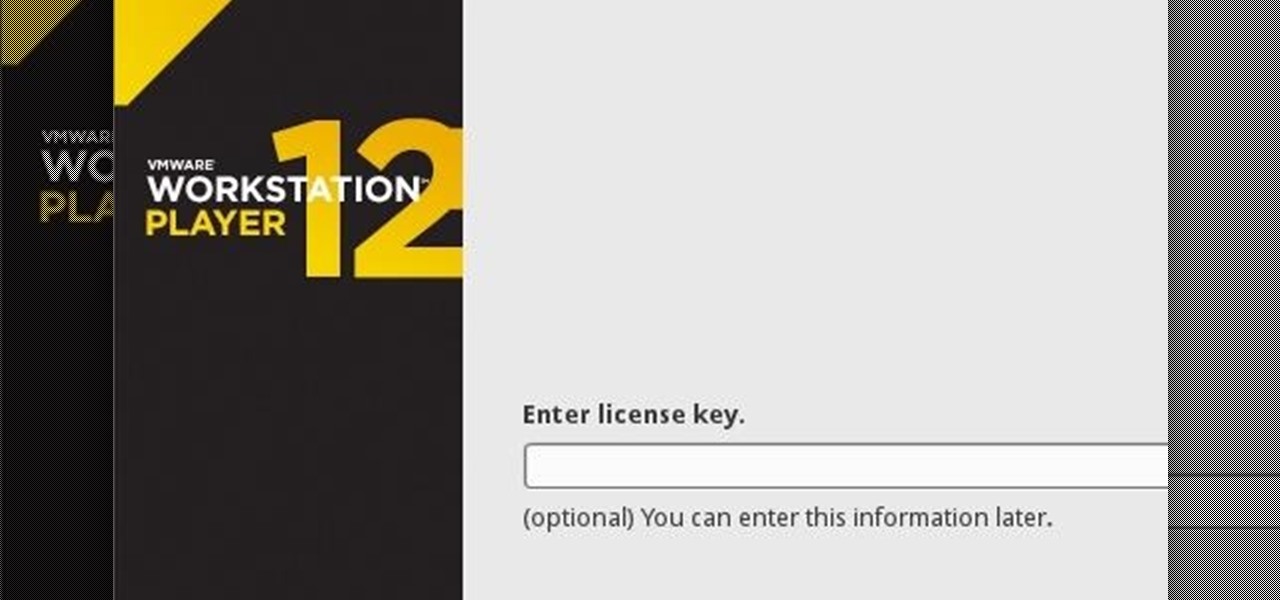
If you have never heard of a Virtual Machine (VM) before you might think it to be some new kind of gamers virtual reality system, and that would be incorrect. A virtual machine is a Virtually a real computer that exists inside of your own computer. You can run Kali inside of a Windows environment via your VM. Not quite the same as an actor portraying an actor on TV. A virtual machine will have it's own IP address and you have the ability to network to it from your Real (Host) computer and bac...