Welcome back, my budding hackers! In my continuing series on Linux basics for aspiring hackers, I now want to address Loadable kernel modules (LKMs), which are key to the Linux administrator because they provide us the capability to add functionality to the kernel without having to recompile the kernel. Things like video and other device drivers can now be added to the kernel without shutting down the system, recompiling, and rebooting.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...
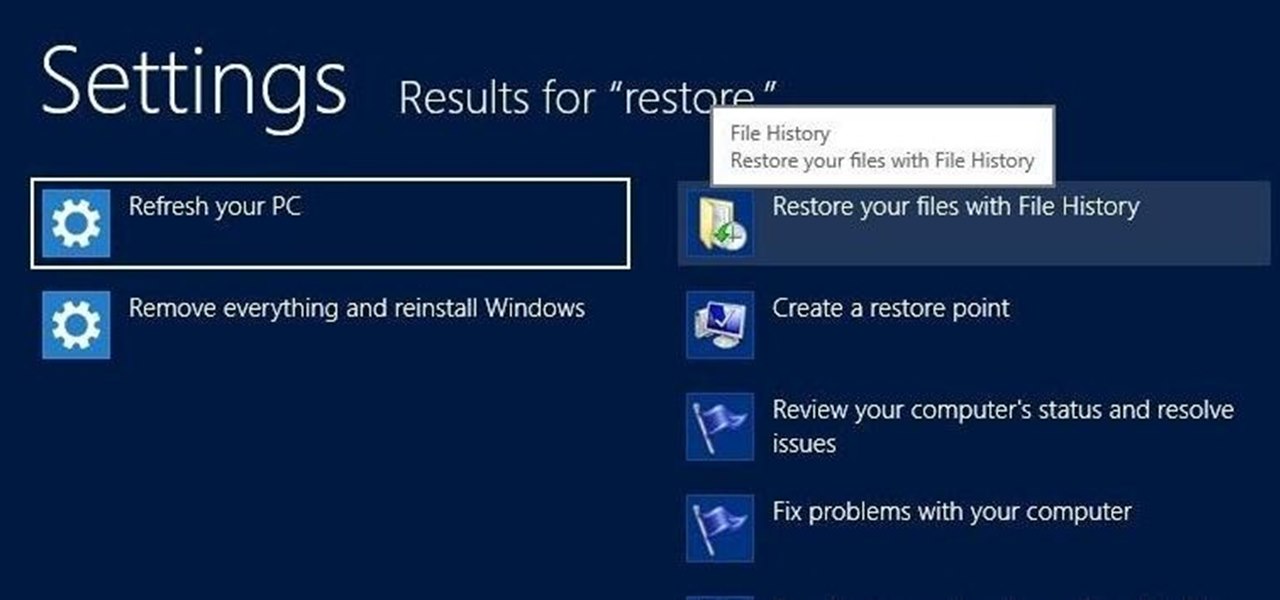
There is nothing worse than losing valuable information or programs on your computer. And if you've ever accidentally deleted a file or document, you know how agonizing that entire process can be.

I get advice from my friends on a lot of things in life—cool video games, movie reviews, and feedback on my choices in women. Friends can be very helpful in filtering out some of the excess noise and are more likely to give you suggestions you can relate to.

Self-restraint is one of the hardest thing to do. I'm a world-class procrastinator, and one of the biggest causes for my procrastination is my iPhone. Temple Run 2 was probably the best and worst thing that could have happened to me.

The Rubik's Cube is probably one of the most well-known puzzles, but if the number of articles about how to solve them is any indication, it's also one of the least understood. How many people do you know who actually know how to solve one?

Religion is one of the most-ignored topics when it comes to Steampunk, which is surprising given how important religion was in Victorian England. Even the hot-button issues of race and gender are confronted with a greater awareness than religion.

Fingers are very useful for many things in life—but fingers get dirty. With most smartphone and tablets using touchscreen technology, our fingers have become our greatest technological asset. But if you want to keep your phone or tablet from looking like this: Then you can try some of these awesome and easy DIY styluses.

While becoming the next Mark Zuckerberg may be out of reach for someone just getting introduced to code, the skill has never been more valuable. Just understanding basic programming language is a great thing to put on your resume, and if you know how to code, you’re golden. Software developers and programmers have been the most resistant to the recession, as jobs in the tech industry continue to grow.

When the time comes to move home, the logistics of moving your belongings can easily become tiresome, tricky and even disastrous. However, with a little careful planning and foresight, the act of packing can be a simple process. The key to getting the most from your move is in efficiency, planning and care. Here, we take a look at the best ways to pack in order to ensure a safe and simple move.

Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, the hints are displayed as a code that looks encrypted, but Claudius noticed a pattern of zeroes that could be easily translated back to plain text with a decoder he made in Ruby. He added this functionality to the Meta...

Hello, today I will tell you about how you can create a page through wordpress. this is a performance for those who have scarcely been touched wordpress. This guide will put you through basis and create a user and a website among millions of people.

Get a crash course on HScript Expressions, Variables, and Attributes in Houdini 10. If you don't even know what this means, then you probably need to check this video tutorial series out. Understanding how to massage data in Houdini is key to giving yourself the creative edge and allowing you to unleash mind-blowing visual effects. This 18-part video series covers a variety of simple yet essential weapons in your arsenal including Global, Standard and Custom Variables to Math and String Modif...

In this tutorial, we learn how to play the Dungeons and Dragons role playing game. To get started, you will most likely join an existing group, which is the easiest way to get started. You will be part of a story and have different adventures, depending on how your group is ran. You will need to have a full set of dice to play this, then go through the different adventures on the game. You will also need a character sheet to play and your player's handbook. Make your character, and pick all o...

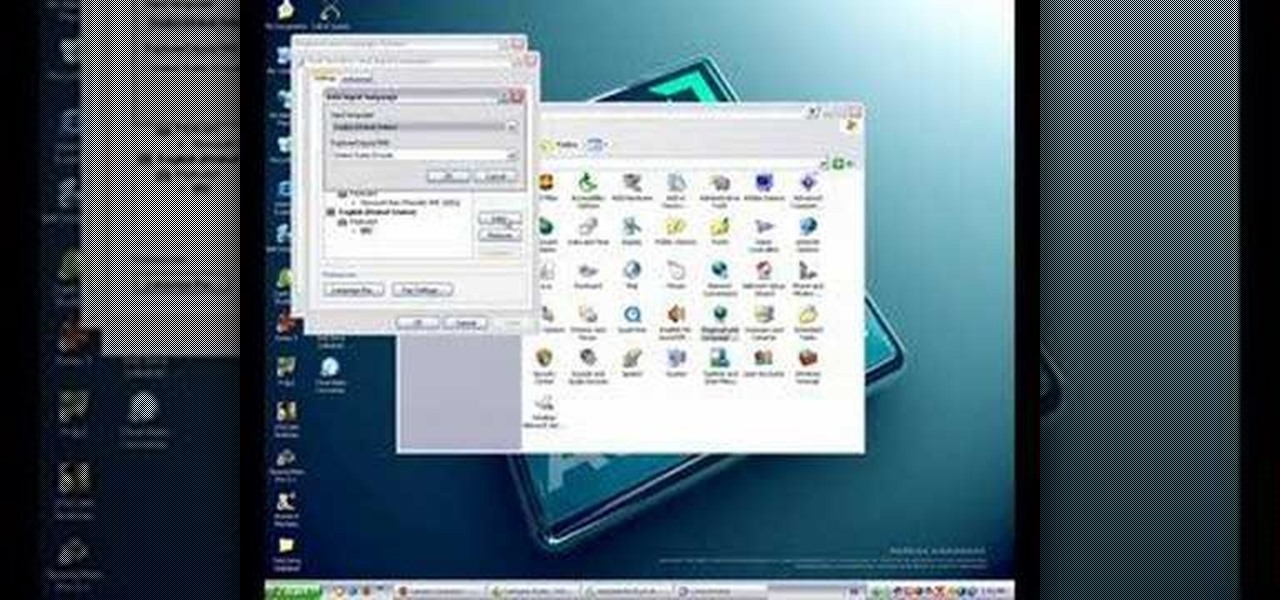
In this video tutorial, viewers learn how to set the language on a Microsoft Windows XP computer. This process is very fast, simple and easy to do. Begin by clicking on the Start menu and select Control Panel. Now double-click on the Regional and Language Options. Go to the Languages tab and click on Details. In the Settings tab, click on Add and select the language that you would like to add. Then click OK. This video will benefit those viewers who use a Microsoft Windows XP computer, and wo...

In this instructional video you will learn how the WWE choke slam is performed. Be sure to understand the stunts performed should not be done by just anybody but by professionals. Now, whoever the attacker is they want to place their right hand on the very top of the defenders chest, and once that happens the defender will take his left arm and hold the attackers arm like he's actually being choked. Next, the attacker will put the defenders right arm over his right shoulder and the attacker d...

Awakening the female energy that resides in the base of your spine is not a process that can be done in an afternoon but is something you work towards though lots of work in kundalini yoga and work toward an enlightened state of being.

It takes more than a kicky costume to become a professional wrestler. Start young to build up your basic wrestling skills and athleticism. To turn pro you’re going to need some acting flare, love for performing and a little luck.

Need to graph a line but aren't sure quite where to begin? It's simple once you understand the whys and wherefores of solving for Y. In this eight-part mathematical video series, instructor Kent Murdic will teach you everything you need to ace your next alegbra test.

The mother's body can be the source of delivery complications like placenta previa or uterine rupture. If delivery problems do occur, your doctor can usually help you manage these childbirth complications with medication or an emergency cesarean section.

Want to learn how to improvise and play jazz piano? Well first you have to learn from the jazz greats of yesteryear. This lesson teaches you how to play "The Man I Love"by George & Ira Gershwin on piano. With some practice and basic understanding of music theory and harmony you will soon be able to improvise jazz solos over basic chords. Soon you will be able to play along with any tune with this jazz piano lesson. Check out this jazz piano how to video and you will be on your way to playing ...

You seem to have the Rubik's Cube down, you can solve it like no other, but you're not fast. This video tutorial will help you become a faster Rubik's Cube speedcuber with a few tricks and techniques.

Understand the way accordions function in this free video series that will help you play your accordion with ease and comfort.

Learn what common time or 4/4 time is and how you can use it with this how to video. This music theory tutorial will help you understand the concept of time signatures and counting rhythm.

Understanding the different types of horse racing is crucial to your betting success. Researching a horses background will help you pick the winning horse. Making sense of the numbers is very important. Watch this video tutorial for all you need to know to wager correclty on the right horse at the tracks.

Learn how to use the ProSear Burner on your Lynx Grill. The Lynx grill has many innovative features and understanding how to use each grill feature can make you more proficient user of the grill.

Learn how to use the main grill burners on your Lynx Grill. The Lynx grill has many innovative features and understanding how to use each grill feature can make you more proficient user of the grill.

Learn how to use the rotisserie feature on your Lynx Grill. The Lynx grill has many innovative features and understanding how to use each grill feature can make you more proficient user of the grill.

Learn how to light a Lynx grill. The Lynx grill has many innovative features and understanding how to use each grill feature can make you more proficient user of the grill.

Bored with crosswords and sudoku puzzles? Well, try your hands at a new type of puzzle: KenKen logic puzzles.

It's finally here. After years of rumors and speculation, Apple unveiled the new iPhone SE on April 15. While it doesn't have a 4-inch display like the original SE, it's the smallest new iPhone you can buy today, with the chipset of the iPhone 11, 11 Pro, and 11 Pro Max. So, when can you get your hands on it?

My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

By using almost any packet-crafting tool, a hacker can perform denial-of-service (DoS) attacks. With the power to create just about any packet with any characteristics, a hacker can easily find one that will take down a host or network. Nmap and Hping are effective packet manipulation tools, but there's also Scapy, which is almost infinitely customizable.

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

Thanks to its intuitive interface that makes sending and receiving money a breeze, Venmo has become the go-to app for millions in the US. In fact, you've probably heard the term "Venmo you" being tossed around between friends. But before you take the plunge and sign up, it's always a good idea to read the fine print and know what you're getting into. Money is involved, after all.

After delaying its launch by four months, LG revealed its 2018 entry to the flagship market on Wednesday, May 2. After years of an underperforming mobile division, the LG G7 ThinQ is the first product since a shakeup within the division to get things back on track, and it brings a number of upgrades over its G6 predecessor.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.