A tiny louse is responsible for decimating the citrus industry. Diaphorina citri, the louse in question, better known as the Asian citrus psyllid, harbors and spreads the "Candidatus Liberibacter asiaticus" bacteria that causes citrus greening disease.

The pathogen referred to as a "nightmare bacteria" is quietly adapting and spreading faster than anticipated.

Disengagement report numbers for self-driving car testing in 2016 on public roads in California were just released, and the biggest point we can make about them is that Waymo is very far ahead of their competitors in almost every metric.

Specialized cells in the lining of the gut may provide a key to preventing an infectious brain disease caused by misfolded proteins.

A gold-medal winning entry into the iGEM synthetic biology competition could change the way we look at Esherichia coli, the bacteria better known as E. coli.
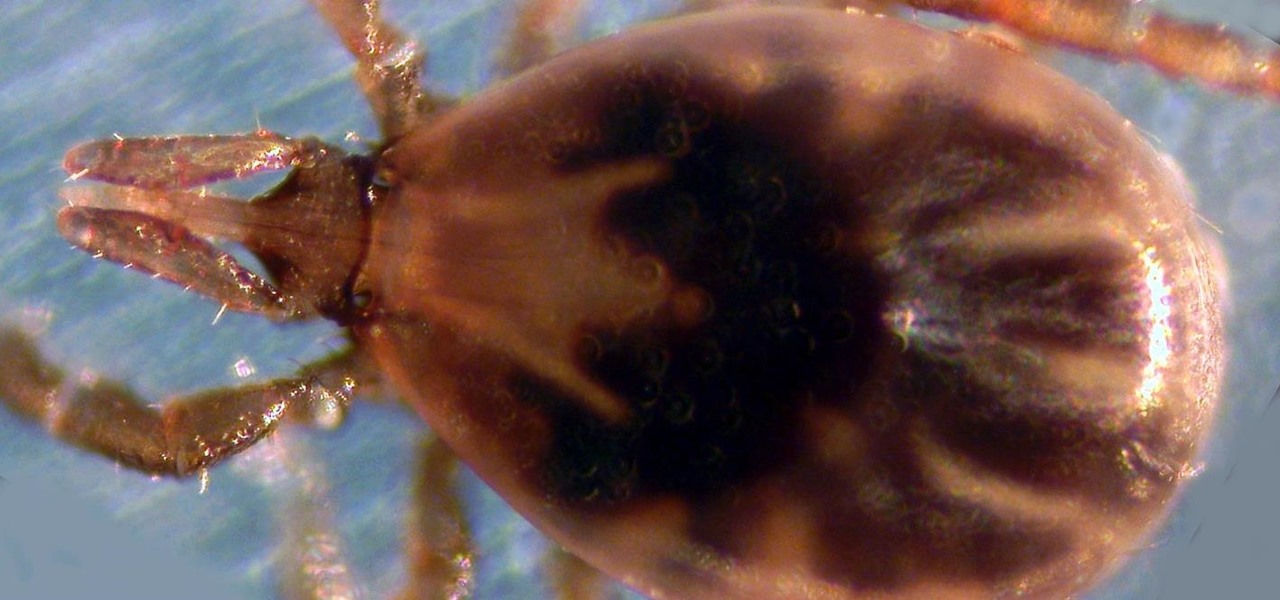
Transmitted by ticks, Lyme disease is a serious infection that is probably headed your way. A recent study confirms the pathogen that causes Lyme disease is now established in nine national parks in the East, including Acadia and Shenandoah National Parks.

The Snapdragon 820 and 821 were met with praise last year, receiving almost no complaints compared to their overheating predecessor, the Snapdragon 810. But now, all eyes are on Qualcomm to see what goodies they have in store for us this year, as their new SoC, the Snapdragon 835, will be revealed this week at CES 2017.

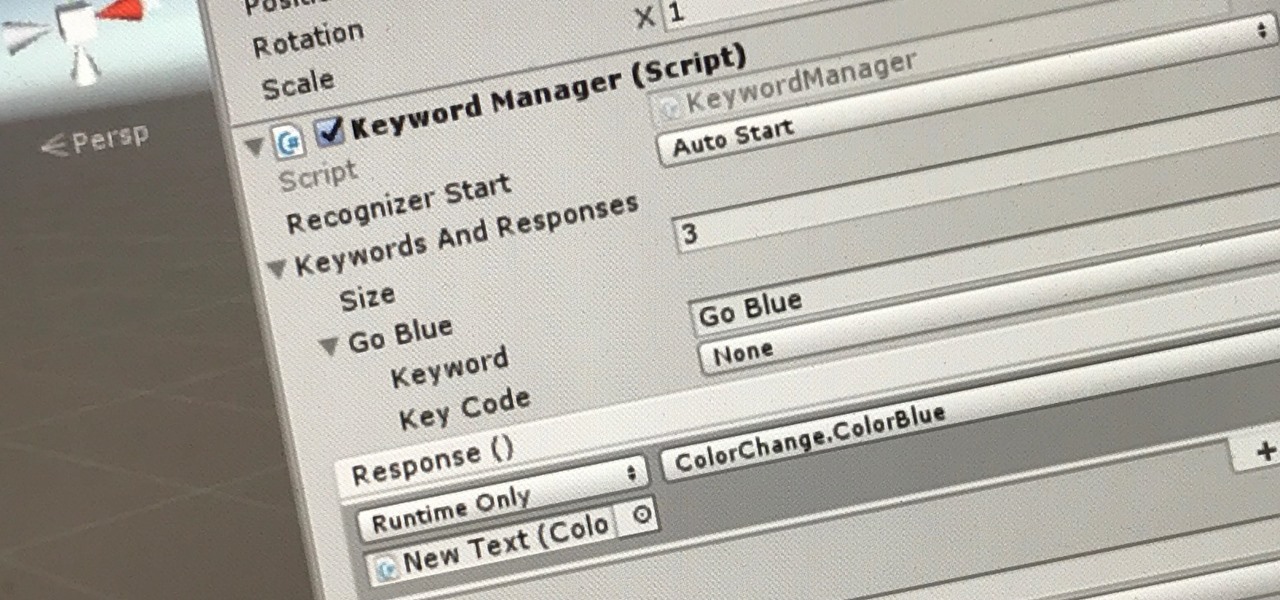
The HoloToolkit offers a great many, simple ways to add what seems like extremely complex features of the HoloLens, but it can be a bit tricky if you're new to Windows Holographic. So this will be the first in an ongoing series designed to help new developers understand what exactly we can do with the HoloLens, and we'll start with voice commands.

There were some new hurdles to clear, and then there were a few more, but legendary root developer Chainfire has created a fully-functional root method for Google's Pixel and Pixel XL flagships. Like past devices, this method relies on the SuperSU ZIP, but now, there's an additional file that needs to be flashed in order to bypass issues with Android Verified Boot (AVB).

For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

At an event in Mountain View, CA, and watched by fans via live stream on YouTube, Google announced a slew of new products today. Over the last few weeks, there was no shortage of rumors and leaks about what might be unveiled, but now the secrets are out.

While you can't turn art into a formula, the film industry has managed to come stupidly close. While many storytelling principles still stand across mediums, successfully crafting a compelling, immersive narrative in virtual reality requires a brand new rulebook. Through trial, error, and success, writer/director/editor Adam Cosco figured out the right rules to follow (and break) in "KNIVES"—his latest 360-degree short film. The film tells an old-fashioned tale of a woman, Kelsey Frye, strugg...

I'll admit it: I ignore expiration dates. No matter if it's a sell-by date, "best if used before" date, or even a use-by date, I don't care. I just check for signs of food decay and keep on eating.

Caramel is delicious, but it can be a tricky flavor to incorporate into baking. Traditionally, caramel is a liquid, and that doesn't always suit dessert preparation since adding extra liquid to baked goods can ruin them. So how do you get that buttery, toffee-like flavor?

Hummus seems like it should be easy to make, but creating that ideal creamy consistency can be pretty difficult. Often it comes out too chunky, which means your hummus won't be good for dipping into. Luckily, there is one trick that will help you create the creamiest consistency and make you never want to go near store-bought hummus again: add baking soda.

For those of you that prefer a soft-baked cookie that is fluffy in the middle, using cake flour instead of regular all-purpose (AP) flour is your secret baking weapon. "But I don't have cake flour," you protest. Fear not: if your kitchen is sans cake flour, you can easily whip some up by mixing together AP flour and a little bit of cornstarch for the same results.

Android's stock battery menu is pretty decent. You can see which apps have been using the most power, and you can tell when your CPU was awake or asleep, among other things. But a lot of times, battery-sucking services will get lumped under the generic "Android System" header, and even though you can see when your CPU was awake, you can't exactly see why.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

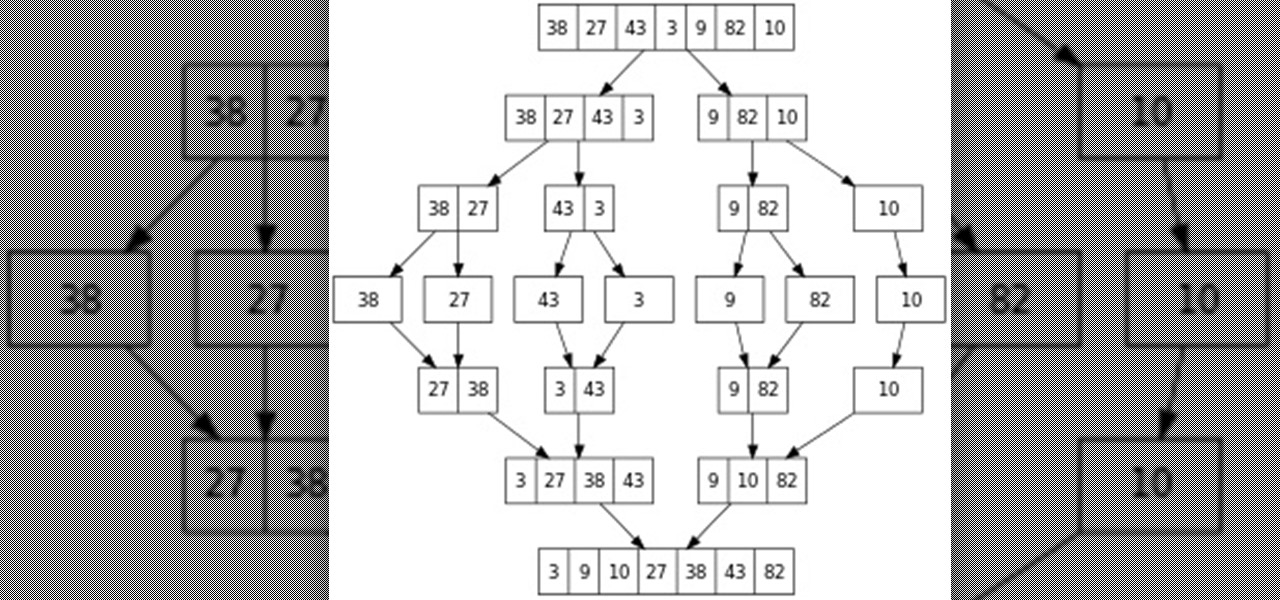
Hello everyone! This is part 7.0 of my Sorting series. I know, I said last time that there would be a 6.1, but not just yet!

Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.
If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the following instructions and recommendations that can lend you a hand in making a sequel for your game.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

The Google Now on Tap feature puts the power of Google Search inside each and every application on your Marshmallow-powered device, allowing you to retrieve contextual results based on the content on your screen.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

Welcome to a tutorial on XOR encryption. We'll be looking at what XOR is and how we can use it to encrypt or decrypt data.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Welcome back! Sorry I've been gone for so long, but if anyone has been keeping up with these articles, you'll know that when I get quiet, something is cooking under the surface. In other words, I've been working on a project lately, so I haven't had much time!

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Greetings fellow hackers. This tutorial is about creating "safe" passwords. This is different from strong passwords. Safe passwords is just creating a password that is not used by someone else or colleague, my definition. But how do you prevent something like this from happening? Of course you won't ask your friend if s|he is using the password you are about to create. Before I show you some of my tele-psychic powers like Professor Xavier, you might want to read this for advice on creating "s...

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

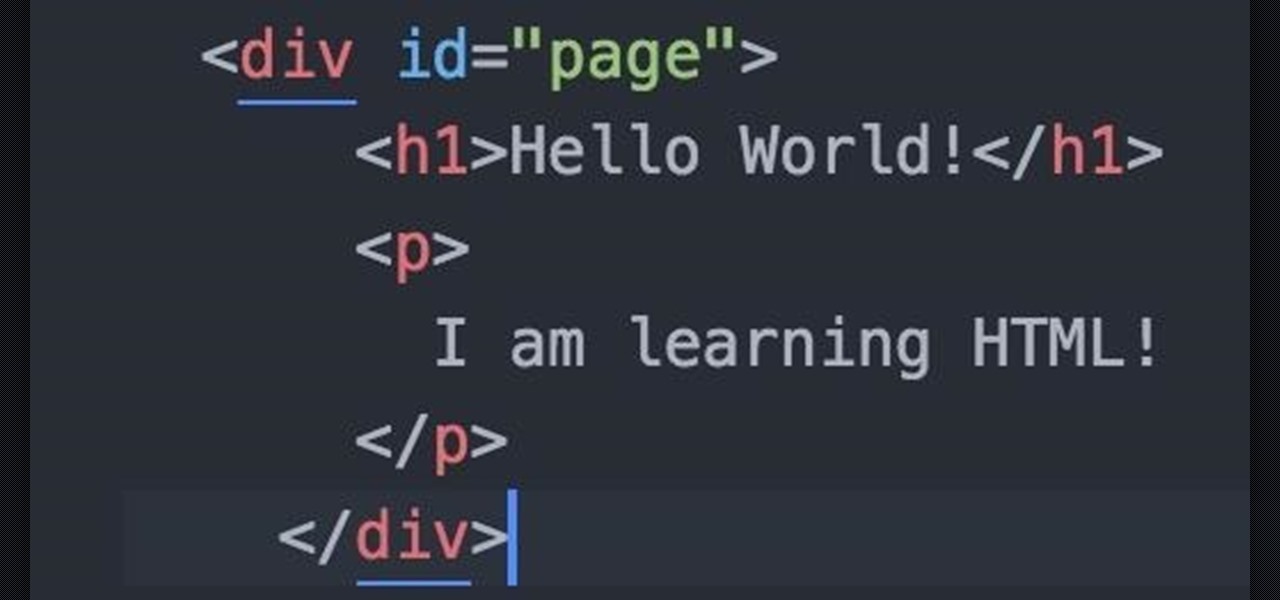
Welcome fellow Null-Byters! Sorry for the delay, this time of the year can be hectic for all of us. Hopefully this will not happen again. In this "tutorial" we will go over more styling and make our page look even better!

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Welcome back to another tutorial on functions. Last time, we looked inside memory to see what functions looked like in the flesh and all that Assembly was pretty nasty. At least you have some exposure to it. This time, we will be examining how functions work with the stack.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.