In this instructional video series, learn how to play a 6-2 defense. Understand how the game works, with an introduction to the basic rules and objectives, as well as a rundown of the offensive and defensive positions on the field. Lessons also include skills and techniques for beginner offensive and defensive players: how to carry the ball, throw a pass, block effectively, punt, and make a solid hand off.

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song. This series is a grea...

In these intermediate drawing lessons, learn how to transform simple shapes into an abstract creation. Our expert will help you understand how to use cubes and prisms, as well as bend the rules of perspective, to create a feeling of dynamic action in your drawings.

In this music recording software video tutorial, learn how to use one of the latest programs for bands and musicians: Apple Logic Pro. This software allows the user to record a song from beginning to end, bounce tracks, master, and do a final mix down to CD, mp3, and other desired formats. Our expert, Bill Macpherson, will walk you through the operations you need to understand to create audio tracks, lay down drums, keyboard, and a bass part, edit and master them, and mix to a final song. Thi...

With this video series you will be able to learn about the bass guitar and everything you need to know to start playing. Begin by learning the parts of the guitar. Our expert will break down the parts of the bass guitar so you understand what each part does.

In this video series, our expert will show you how to replace, repair and maintain your motorcycle brakes. You will get step-by-step instructions on disassembling your wheel, and brake components, cleaning the brake caliper and master cylinder, repairing broken parts, and finally, reassembling your motorcycle when you are finished. Our experts instruction will give you the knowledge to fix and maintain your own motorcycle brakes, as well as enhance the general understanding of your motorcycle...

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

Your childhood "social networking" may have been to go outdoors to the neighbor's — and outdoors is a great place for kids to be. But these days, the terms educational, digital media, entertainment, and toddlers don't have to be mutually exclusive. Like most things in life, it's about balance, and these apps can aid your child with social-emotional development when not playing with friends.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Around this time in 2016, the predictions for the next year had reached something of a consensus: 2017 would be the year of augmented reality. But a funny thing happened on the way to the future — nothing much, really. At least not for the first half of the year.

There are a lot of Android phones out there, and chances are that someone in your life is looking for one this holiday season. Well, there also happens to be a lot of Black Friday deals on Android phones this year. So we've rounded up the best deals taking place on Black Friday weekend to help you save big.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Learn how to bend circuits, disassemble toy cases, unscrew circuit boards and test a circuit bend in this free video series that will help you understand how and when to utilize this unique way of making music.

In this video series Rafael Mayans explains how to offshore fish. He goes over everything from the types of bait to use, trolling, tying knots and the laws of offshore fishing you'll need to understand.

If you are interested in learning how to fly a plane, this video series is perfect for you. While this is only an introduction to soaring the skies, it will help you understand more about the process of flying.

It's about that time again: Facebook has announced the dates for its annual Facebook Connect (formerly known as Oculus Connect until last year).

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

The enterprise applications powering the adoption of the HoloLens 2 are only just ramping up as developers continue to work with the still relatively new hardware.

If you do a lot of typing every day — writing reports, essays, emails, and whatnot — we can guarantee your day would be improved by taking less time to do it. Thankfully, we've found a super-smart AI-powered tool that will do just that, and right now, you can get an amazing 52% off a Lightkey Pro Text Prediction Software: Lifetime Subscription for the sale price of just $79.99 (regular price $169).

What does it mean when a software company obsessively focused on innovating the way we use our mobile devices to see and communicate with the world adds virtual voice agents? Possibly e-commerce magic, with a powerful layer of augmented reality.

The gold standard in any business is reaching the front page of Google. You need to get your brand in front of audiences. While it can seem daunting, it's not impossible when you master SEO best practices.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

As one of the world's largest and most powerful cloud computing platforms, Salesforce is used by countless companies to manage customer relations, deliver services, and innovate solutions to complex problems.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

Navigating a pandemic is new for everybody, which makes staying on top of your finances more important than ever. Fortunately, financial freedom is possible when you focus on budgeting and investing wisely.

The Internet of Things (IoT) is changing everything in our homes and at work, from security systems and lighting fixtures to smartphones and speakers. An estimated 50 billion devices are now hooked up to IoT.

AirPods are not only a great way to listen to music on your iPhone, but you can also use them as a headset for phone calls, videoconference, Siri, voice memos, audio messages, and more. While each 'Pod has a built-in microphone, they aren't used simultaneously, and your AirPods will automatically choose which to use. If you want to only use the mic from one 'Pod or the other, there's a way to do that.

If you're a tech-savvy coding pro, you have a virtually limitless number of great career choices to choose from. Whether you're interested in working at a small tech startup, freelancing as a cybersecurity specialist, or founding the next Google, having a solid understanding of development terminology and general programming will inevitably get you far.

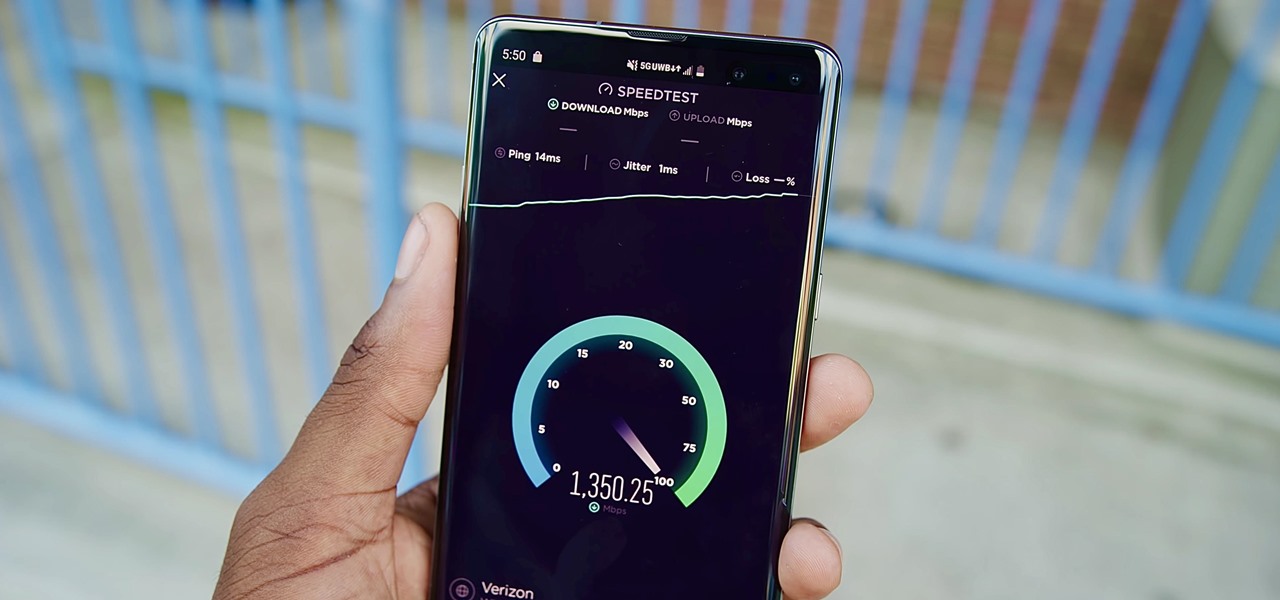
Not all 5G is equal. Even if you dropped the cash on a true 5G phone and you see it's connected to 5G in the status bar, that doesn't mean you're surfing the web, streaming Spotify, and binging Netflix faster than your friends with LTE phones.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

People fundamentally distrust magicians. And they should. The illusions they proffer are just that, illusions meant to astound rather than tangible interactions and results that have weight and meaning in our real world. Our lizard brains know this, and, no matter what the outstanding feat of "magic" presented, we nevertheless hold fast to our survival-based grip on the truth: we just saw simply "can't be real."

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.