Check out this guide to Battlefield Bad Company 2, the mission entitled Zero Dark Thirty. Find the M-Com Stations and destroy them, but stay alert for all enemies. Watch this video walkthrough to learn how to complete the Zero Dark Thirty mission in Bad Company 2 on the PS3.

Things are really heating up now with that the Russians are putting on the pressure in Battlefield Bad Company 2. This time your helicopter gets hit by an RPG and you need to put it down and make your way through the clearing in the jungle. Destroy all the M-Com Stations, and nobody can die. Watch this video walkthrough to learn how to complete the No One Gets Left Behind mission in Bad Company 2 on the PS3.

The first thing you need to do in this mission on Battlefield Bad Company 2 is to hop out of the copter and get in the sand buggy and head to your marked location. You'll need to locate and head to each station on the map: Bravo Base Station, Charlie Base Station, and Alpha Base Station. After that, complete the Triangulation Point. Watch this video walkthrough to learn how to complete the Sangre Del Toro mission in Bad Company 2 on the PS3.

Make your way to the crash site in this mission on Battlefield Bad Company 2. You'll need to protect the crashes satellite from RPGs and enemy fire. Then you need to destroy yet another M-COM Station, so make sure you're ready. Watch this video walkthrough to learn how to complete the Snowblind mission in Bad Company 2 on the PS3.

Crack the Sky in this mission on Battlefield Bad Company 2. Use the minions on the helicopter to to take care of your enemies below, and once you kill them all, the copter will drop you off where your real mission starts. Make sure to destroy the M-Com Station. Watch this video walkthrough to learn how to complete the Crack the Sky mission in Bad Company 2 on the PS3.

In Mission 4 (Chapter 3) of Battlefield Bad Company 2, you need to first take care of the sniper. You can only fire the sniper rifle during the thunder, or you'll automatically lose the mission. So make sure you have sniper sensibility in this mission. Watch this video walkthrough to learn how to complete the Upriver mission in Bad Company 2 on the PS3.

This is the third mission in Battlefield Bad Company 2 called the Heart of Darkness, where you need to follow your unit through the ruined village. But first you have to survive the helicopter ride with the hippy pilot. You need to destroy the M-COM stations to succeed in this mission. Watch this video walkthrough to learn how to complete the Heart of Darkness mission in Bad Company 2 on the PS3.

At the very beginning of Battlefield: Bad Company 2, you and your squadron are floating down a river behind enemy lines. At first, you're just watching and learning, then you finally gain some control and learn how to use your weapons and make your way around the battlefield. Watch this video walkthrough to learn how to complete the prologue Operation Aurora in Bad Company 2 on the PS3.

Chess is a strategy and logical deduction game between two players that is enjoyed by children and adults alike, from park benches to convention halls across the world. Though the game of chess has taken many variations over its long history, today's form involves black and white teams orchestrated by players and has even entered the digital age, as games and tournaments are played online and via email. Using a square board composed of grids and smaller squares, the game pits a queen's army a...

In this tutorial, we learn how to overcome driving anxiety. Remember that you aren't alone, a lot of people have anxiety while they drive. First, take a step back and think about the root cause of your anxiety, whether it's from a car accident or someone else who has been in one that was close to you. Next, you will need to set a goal to get better and not run away from your fear. You will also need to develop tactics to overcome your panic and learn things that can help you, like breathing d...

This video give you a step by step in how to cut your mango cheeks, and owszat shows you how to do it. Using careful tactics on the mango, you can see a slight edge. Where you distinguish your mango's center point is where you will be cutting from. Tear off your stem to have a flat relying surface. Cutting about five millimeters from the center point on each side, making one slice that releases your cheek, and doing the same for the other side leaves you with two mango cheeks and the center p...

This video tutorial is from Grandmaster Alexandra Kosteniuk, who shows you how to play a game of chess, like the masters play.

Enfilade is a concept in military tactics used to describe a military formation's exposure to enemy fire. Well, the same concept applies in a game of chess. Check out this video tutorial from Grandmaster Alexandra Kosteniuk that shows you how to use the technique called enfilade. This chess position was taken from a 1737 chess book. White plays and wins by playing the rook and sacrificing it. See how the endgame of chess is really played.

Burglary is common, but is also quite preventable with these tactics. You Will Need

Pinochle is a card game with complex rules, strategies, and tactics. Here’s a game overview for new players.

Women can use a variety of basic self-defense techniques and tactics to defend themselves against attackers. Learn basic self-defense moves and techniques in this free video on women's self-defense.

While there's an art to surviving the all-nighter, there's also an art to staying awake throughout the day when you're operating on little to no sleep. In 1964, the record for sleep deprivation was set by 17-year-old Randy Gardner, who stayed awake for an incredible 264 hours and 12 minutes. Now while we're not out to challenge Randy for his title, we can certainly look to him for inspiration in beating back our own fatigue.

Russian cyber disinformation campaigns have many missions, but one of particular interest is using technology to monitor, influence, and disrupt online communications surrounding culturally sensitive topics or protests. The ability to watch these events, and even filter positive or negative tweets to amplify, gives rise to the ability to execute a number of disinformation campaigns.

The Pinchin Pirate is, of course, a giant crab with an eyepatch and a pirate hat. He's the second boss you'll have to defeat when playing Donkey Kong Country Returns. This guide shows you the best strategies and tactics to vanquish him!

This is not a tutorial for juggling six balls. watch to learn basic grip and release tactics. Check out this video to understand the hand parallel to the floor approach.

Video: . Nobody likes an RV or camper toilet that smells, this video will show you how to prevent your RV toilet from smelling.

Hiddenstuff.com has great tips and tricks for the massive, multiplayer, online, role-playing game, World of Warcraft. Their guides and strategies for WoW are bound to help you out, outlining some of the most important tactics in the video game. This video tutorial will show you how to play on level 80 in World of Warcraft.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

In this how to video, you will learn how to use the Nerf Gun Long Shot. First, you will need to know about the magazine. These can hold 8 shots and are spring loaded. Do not load 8 shots, as it will jam. Instead, load 6 shots to prevent this. The shots can be used in other guns, but the Long Shot magazine can only use this shots. The holes in the shots make a whistling sound. If you get shot, you will feel it regardless of distance. The gun has a trigger, a mount, a quick grab design, a hidde...

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

Null Byte readers are no strangers to the powers and benefits that come from learning how to code. By knowing only a handful of programming languages and platforms, an intrepid developer can create everything from best-selling apps to spyware in the comfort of his or her own home.

The overarching and expanding field of data science and analysis has become virtually inseparable from areas such as programming and development.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

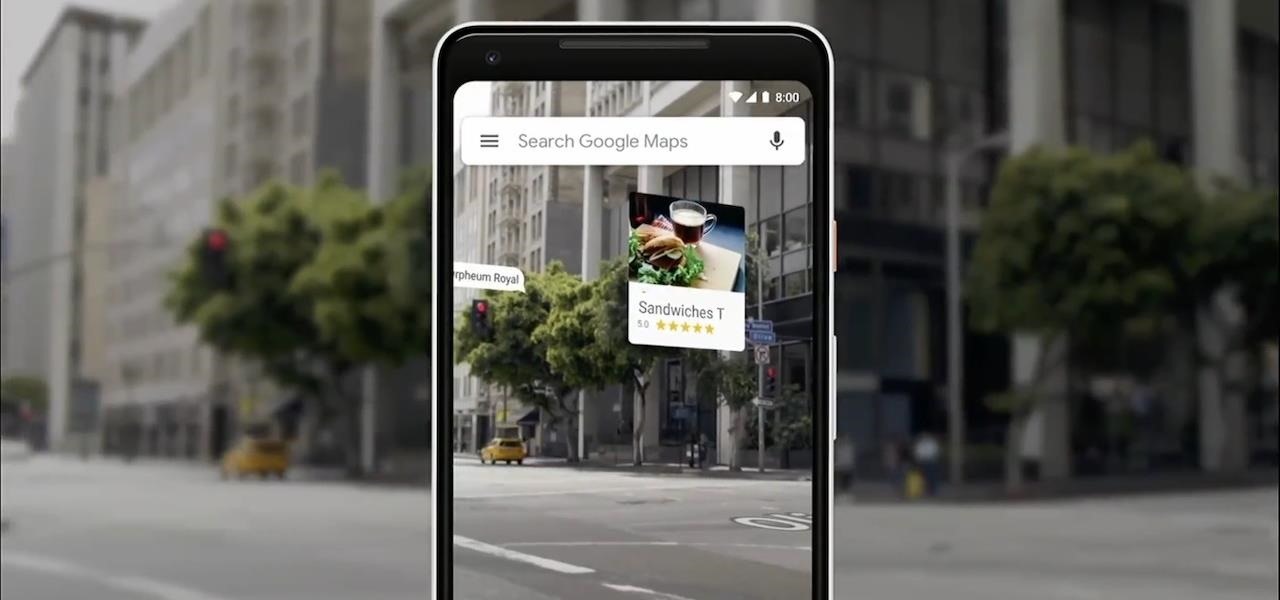
The augmented reality walking navigation mode for Google Maps appears to be closer to an upcoming release for the general public.

Despite the wide availability of markerless augmented reality experiences for mobile devices, there is still a market for scanned triggers for content, as evidenced by the new image recognition capabilities on Facebook's Camera AR platform.

When it comes to marketing, sexy sells, a point that has been lost on most augmented reality hardware makers focused mostly on the geek space. But a new promotional spot from AR-in-the-car accessory maker WayRay indicates that AR companies are beginning to see the virtual sizzle reel light.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

How to fight multiple attackers with 5 simple Wing Chun techniques that will help survive a attack by a gang of multiple attackers. These are some of the best tactics on how to fight a group of people while staying safe.

By Zech Browning Shihan of Gyodokan Martial Arts. Step 1: "Storm Within the Calm - Putting It All Together - Part 1"

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

Dark mode themes for mobile apps are all the rage these days, but YouTube is taking that a bit literally with its latest augmented reality experience.

Following in the steps of Snapchat, Instagram, and YouCam, another popular photo app has gotten into the virtual try-on augmented reality game.

The hype for HBO's Game of Thrones reached proportions as epic as the series itself this week with the latest release of the final season's official trailer, but it's a Snapchat promotion that will truly make fans at SXSW bend the knee.