Welcome back! In the last iteration of how to train your python, we covered error detection and handling. Today we'll be diverging from this and discussing functions. More specifically, we'll be creating our own functions. First we'll need to understand exactly what a function is, then we'll get on to making our own! So, let's get started!

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.
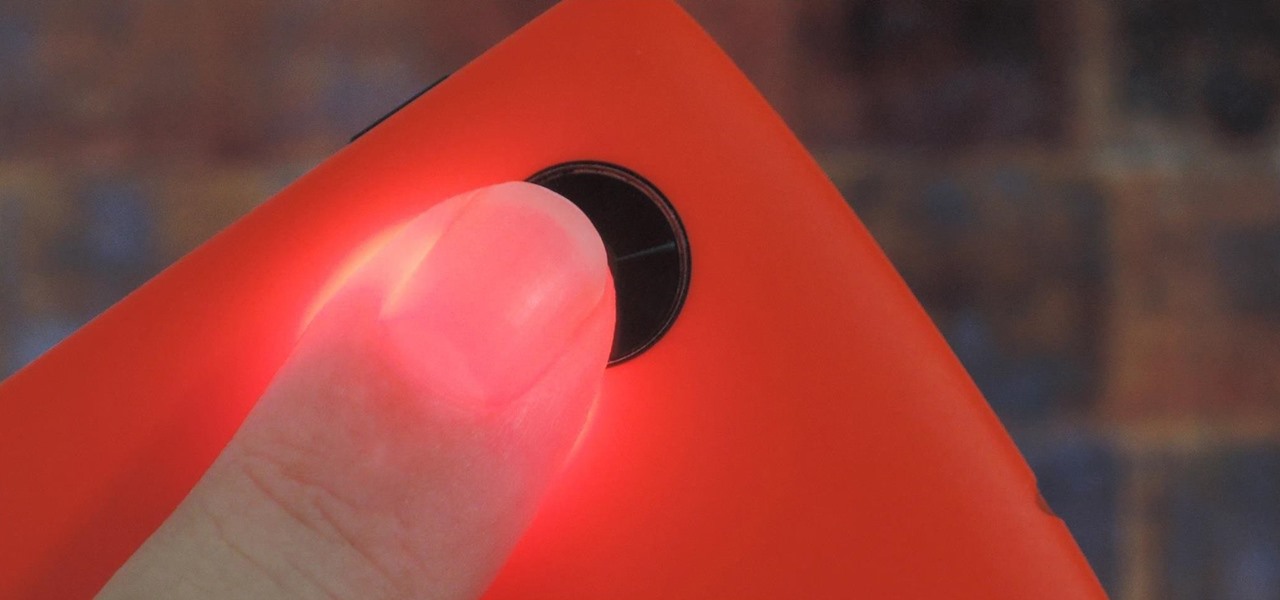
Samsung created quite a buzz when it debuted a built-in heart rate sensor on the Galaxy S5 back in 2014, but amazingly, not many other manufacturers decided to follow suit. It's really a shame, too, since data from a heart rate sensor would go perfectly hand in hand with the increasing fitness- and activity-tracking features that most smartphones sport these days.

Your average Android phone or tablet comes with quite a few apps already installed—even before you turn the device on for the first time. These pre-installed apps are certainly helpful when it comes to getting your feet wet with Android, but in many cases, they're not always the best apps available for accomplishing the tasks that they perform. Additionally, many third-party apps can add lots of cool functionality to your device, so you might say that sticking with only the pre-installed apps...

From day to day, it can be difficult to remember everything that's required of you. I tend to forget exactly where it is I'm supposed to be during my busiest moments, and it's even easier to delete each day's events out of your brain when there's so much else that dominates your mind. Yet taking the time to remember exactly what it is that happens during each of our days can be a vital part of our memory—and with nothing more than 15 minutes, we can strengthen our brains and remember more tha...

No matter how fresh, sharp, or clean a razor is, it can still create an itchy, inflamed trail of razor burn bumps. When razor burn appears, it's unpleasant, and can even affect your next shave.

Apple's latest round of devices—including the MacBook Pro, Apple Watch, and the iPhone 6S—use a new touch input method that can detect when you've applied a bit more force than usual. Dubbed "Force Touch" ("3D Touch" on the new iPhones), this gesture simulates a long-press or right-click, but it usually requires special hardware to detect the amount of pressure you've applied.

For every contact photo you add, Android keeps two copies. The first is stored at a 720p resolution, and this is used for high-definition imagery when you're looking at a full-sized contact card. But the second image is only 96 pixels by 96 pixels, and this is used for all thumbnails throughout the operating system.

Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

The Google Now gesture included in the Google Now Launcher and on Nexus devices isn't something I regularly utilize, and you might not either. There is a way to disable it, which is a good idea if you were executing it accidentally, but what's even better than disabling it? Repurposing it!

Looking back at my childhood in the '90s, I can't help but feel like I was deceived. Movies that took place in the "future," like in the year 2015, would showcase awesome technology. You know, self-driving or flying cars, hoverboards, and virtual displays controlled with hand gestures—so where are they?!

Are you a lawyer who's married to a computer programmer? Chances are you might not have even dated if you first met online.

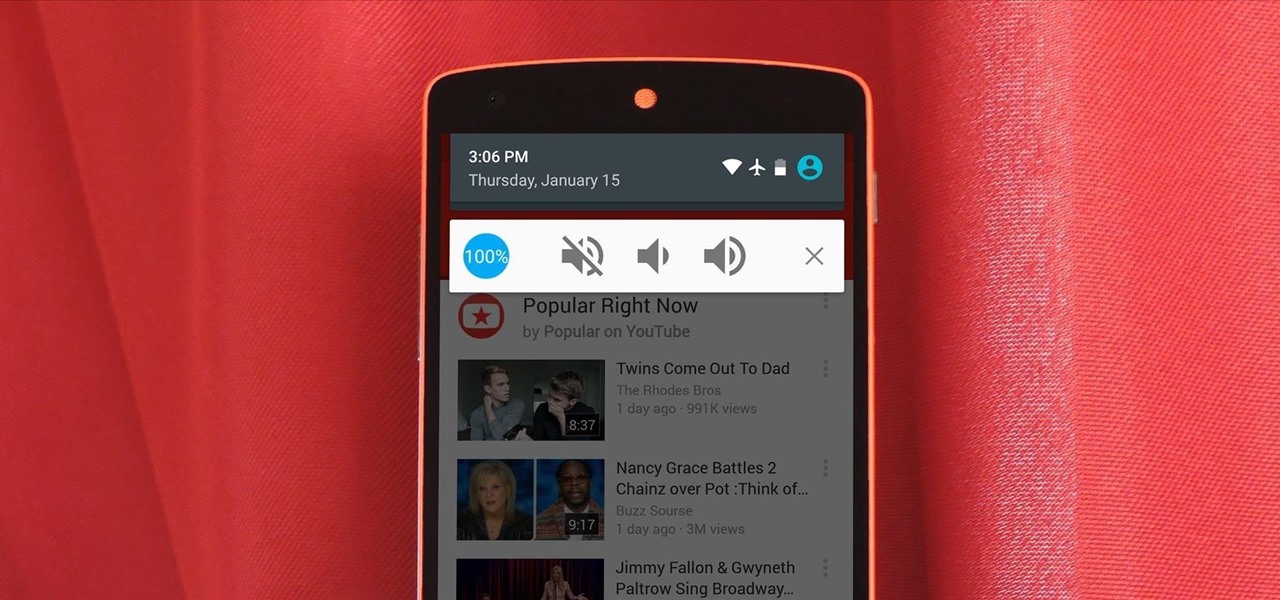
If there's one gripe I have with Android Lollipop, it's the new volume menu. When Priority mode was introduced, the stock volume panel was revamped to accommodate it, and somewhere along the way a bit of functionality was lost.

Meat tenderizers are absolutely necessary when dealing with leaner, tougher cuts like flank or skirt steaks. And while fruit like papaya, kiwi, and pineapple contain enzymes that can tenderize meat, the results can be hit-or-miss, and impart a fruity flavor that you may not always want.

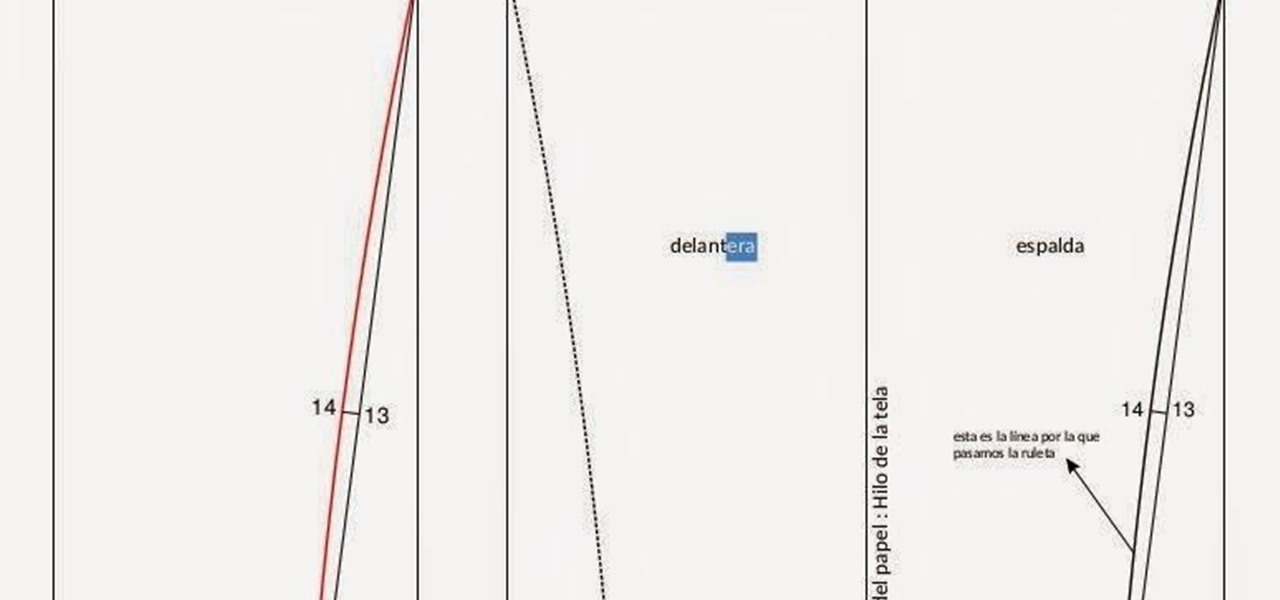
A well designed sleeve is very important to creating a top or jacket that fits comfortably. Get your correct measurements before you begin. Please view the following step-by-step instructions and accompanying video and diagram to create the basic sleeve.

The interwebs is a great source of information, but sometimes said information is not always legit. That can be frustrating when it comes to making fun food, costumes, and arts and crafts for Halloween, like this bowl of "bloody" gummy worms.

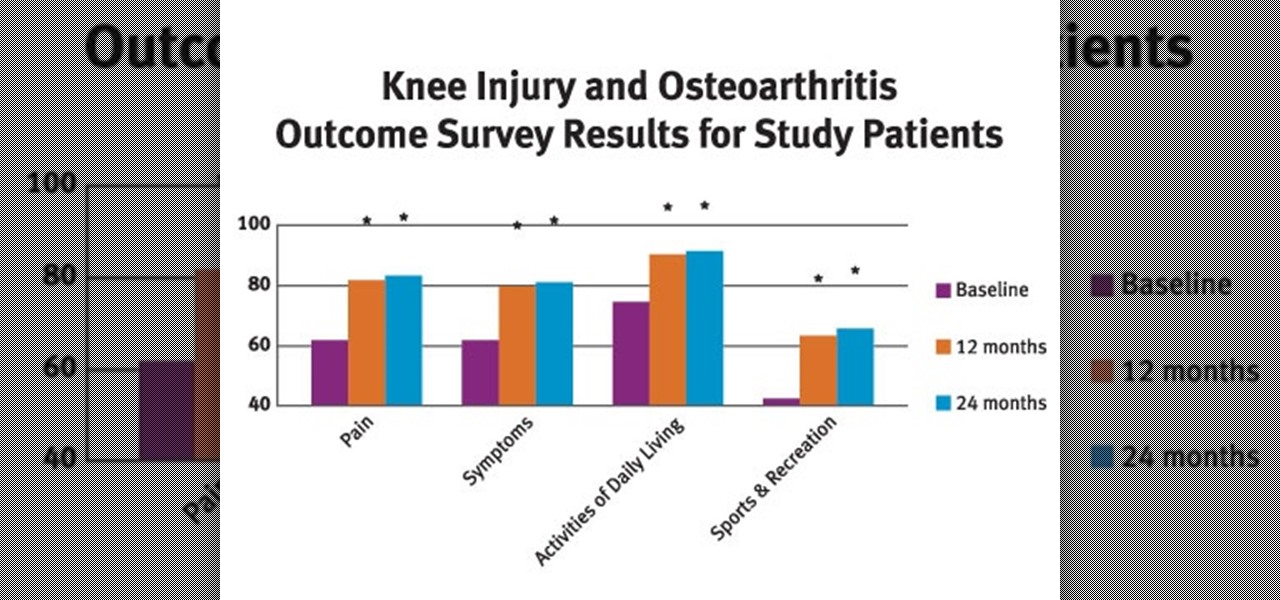
Osteoarthritis can affect every gender and at any age but it commonly occurs in women than in men. In America there are approximately 27 million Americans aged over 25 who live with osteoarthritis.

If you notice any issues with your LG G3, pinpointing the culprit can be an arduous task. It could be a hardware issue, a resource-heavy app, or a bloatware-infested operating system.

Can you cook a steak or salmon filet that's straight out of the freezer and get good results? Ordinarily, I would say no. Usually your steak ends up a sad grey mass fit only for the family dog and the fish is burned on the outside with an icy, undercooked center.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

The Galaxy S5's screen is truly a feat of modern technology. It uses what is known as an AMOLED display—an acronym for Active-Matrix Organic Light-Emmitting Diode. In short, this technology means that every individual pixel on your phone's screen emits its own light. This is a break from the traditional LCD technology that requires a backlight for any pixels to be visible.

When theming Android, it's the little touches that complete the look, making your device yours. If you're rooted, you probably know by now that there's virtually nothing you can't change the look of on Android.

These days, our smartphones carry some very sensitive data. From banking app passwords to personal photos, there are many things on your Nexus 5 that you might not want other people to have access to.

As I begin my move across the country, I find myself dodging all kinds of Craigslist scams, particularly in the apartments and housing classifieds. Fortunately, I've discovered a little trick that will tip me off to a scam before I lose $1,000 in a fake security deposit.

One of the hardest tradeoffs when installing a non-Sense-based custom ROM on an HTC One is the loss of Beats Audio. Due to a patent restrictions from Beats and compatibility issues, it's currently impossible to port it to a non-Sense ROM, but with ViPER4Android you can get almost identical results, bringing life back to the BoomSound speakers on your device.

Usain Bolt ran 100 meters in 9.58 seconds, an insane record-breaking time that might not ever get beat. As fast as that is, wouldn't it feel like a travesty if your Samsung Galaxy S3 took that long to open up Wikipedia?

There is nothing more refreshing than an ice cream in a hot summer day. And even though, here in Australia, summer is "just" a couple of months away, I still like to have a scoop or two every now and then. However, I like to make the ice cream on my own. In this way, you can make whatever flavour you want, plus you know what type of products you have used and it usually tastes better than a commercial one.

One of the very first Photoshop skills we learned in my tenth grade photojournalism class was cropping the background out of images. I hated it. It was extremely time consuming, and the magnetic lasso tool never seemed to want to cooperate with me.

Keeping your operating system up to date is essential to keeping it bug-free and running properly. Windows regularly pushes out patches and security fixes through Windows Update, so making sure to turn on Automatic Updates or checking at least once a week is strongly advised.

Welcome! Today I would like to share a few hints about picking the right color. So, if you do not know what color your today's outfit should be or your or which color you should choose for your room walls, please follow my suggestions.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

Add antibiotics to the possible list of culprits responsible for honeybee decline around the world. While it may come as a surprise, antibiotics are commonly mixed into feed used by commercial beekeepers to maintain their hives. In a recent study published in PLOS Biology, researchers from the University of Texas at Austin found antibiotics used to treat honeybees may be a contributing factor in individual bee death and colony collapse.

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!