Freud once said that jealousy is both inevitable and universal. So why not work it to your advantage? While the end results of intentionally game playing are dubious, at least as far as building a healthy relationship, if you're hell bent on fostering a bit of jealousy in someone, this how-to video will do the trick. Follow along with the steps in this video and find out if flirting and acting unavailable help you out in the dating game.

You've met the perfect guy. You know he's the one. Now here's a surefire way to let your text-happy enthusiasm get the best of you both. Watch this video dating tutorial and learn how to lose a guy by sending crazy text messages.

This instructional dating video demonstrates how to improve your French kissing skills. Pay attention to these tips to formulate the perfect kiss. Keep your eyes closed, watch your hand movements, and pick a side of the face to aim for. Make sure to do a little lip locking and kiss that lovely person's face before moving in for a serious French kiss.

The Aries man or woman can be tough to figure out, but this video shows how to push all the right buttons. To trap an Aires you will need a love of athletics, a go with the flow attitude and a thick skin. Learn how to use astrology advice in dating, by watching this how-to video. Pick up astrology tips on making a relationship with an Aries work.

Aquariuses have high standards, but anyone with the right drive can meet them. Use your creativity, knowledge of art and music, and good social skills to trap that Aquarius. Learn how to use astrology advice in dating, by watching this how-to video. Pick up astrology tips on making a relationship with a Aquarius work.

Wanna be a smooth operator, but your dirty mind keeps tripping you up with your foot in your mouth? Listen to dating coach David Wygant dish out the goods! Start seducing girls instantly next time you go out.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

The Reminders app has always lacked the oomf that would make a person switch from a powerful third-party task manager. But Reminders has received quite the makeover in iOS 13, including a revamped UI and several new features, such as timed reminder alerts, which make the app a worthy to-do list option for the iPhone.

When it comes to web-based augmented reality, 8th Wall has emerged as one of the leading platform providers, and the company just cranked up its capabilities another notch for AR marketers.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

Razer took to the stage this month to unveil their new flagship phone, fittingly called the Razer Phone. The device is targeted at gamers, but has a list of specs that make it an intriguing daily driver for any user. Its headlining feature is an 120 Hz IGZO display, the first of its kind in a flagship smartphone released in the US. Tonight, Razer officially opened up orders for the new phone on their website.

Hitman Sniper topped our roundup for the best premium shooting games, and it's easy to see why. Straightforward yet intense story. Awesome visuals. Stealthy action. Strategic gameplay. Hitman Sniper is easily the best sniper game available for your smartphone, and it's currently free on Android for a limited time, as well as discounted for iPhone.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

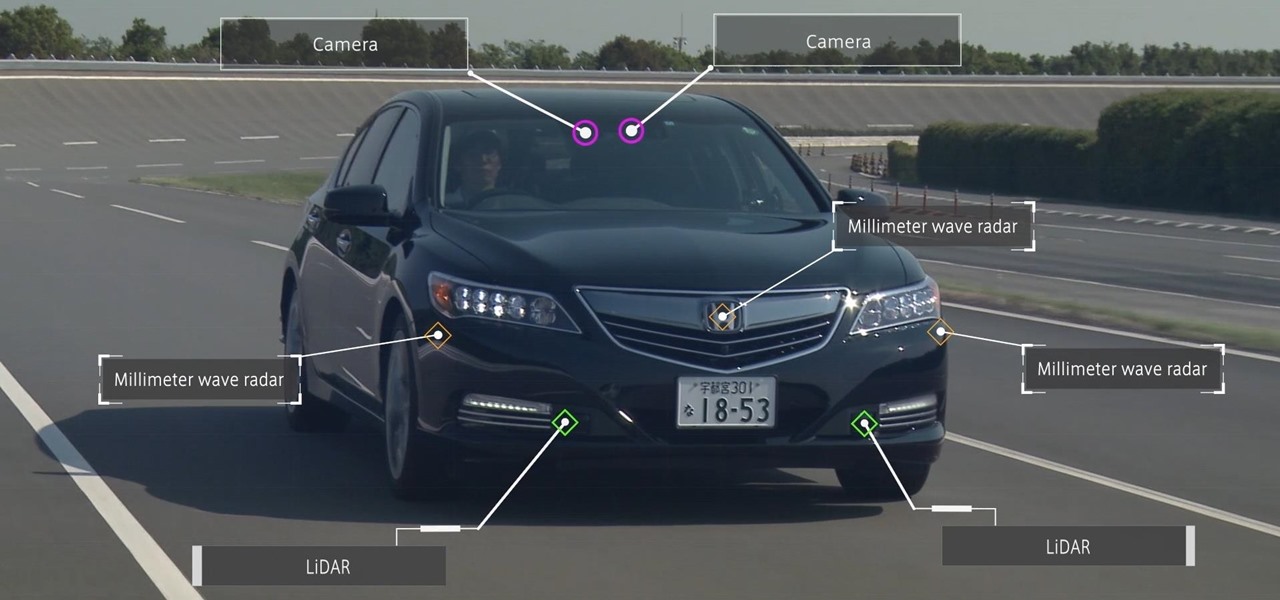
Honda president Takahiro Hachigo has just announced that Honda will complete development of fully self-driving cars by 2025. While the company aims to have level 3 — or conditionally autonomous cars requiring human intervention only in emergencies — on the road in time for the 2020 Tokyo Olympics, these level 4 cars would require no intervention in most environments and thus bring Honda one step closer to producing fully driverless cars.

Single and living in NYC? Forget bars, the female-empowered dating app, Bumble, has just opened a place where you can meet up with your online lovers.

Augmented reality (AR) generally exists through the lens of our smartphones as information layered on top of what the camera sees, but it doesn't have to. Developer Jon Cheng worked with an indoor climbing facility in Somerville, Massachussetts, called Brooklyn Boulders, to turn rock climbing into a real-world video game where participants compete in a time trial to hit virtual markers on the wall.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

Are you a lawyer who's married to a computer programmer? Chances are you might not have even dated if you first met online.

While I consider myself to be a pretty organized guy, there are often times where I just can't find a file I put on my phone. Most of the time, when I download a file it goes automatically into my Download folder, but when I use a third-party to download other files, like torrents, they could end up in a number of places. Filtering abilities on file explorers often fall short, so it was time to find an app that would automatically sort files in real time.

Don't throw away your dead light bulbs, they may come in handy one day. This video will show you how to start a fire using a dead lightbulb. And no electricity. The tricky part is emptying out the insides, but this can be done with sticks and stones, assuming you're in a survival situation and just happen to have a light bulb with you for whatever reason.

I can't begin to tell you how many times I've forgotten a special day or event. Once, I even showed up to class where everyone was turning in essays while I sat there empty-handed. Important dates sneak up on us. Especially one-time events we just can't wait for, like the release of a new movie when we count down the days, minutes, and hours.

Watch this video to learn how to make a Middle Easter favorite, a date and walnut cake. It goes great with rose tea or coffee.

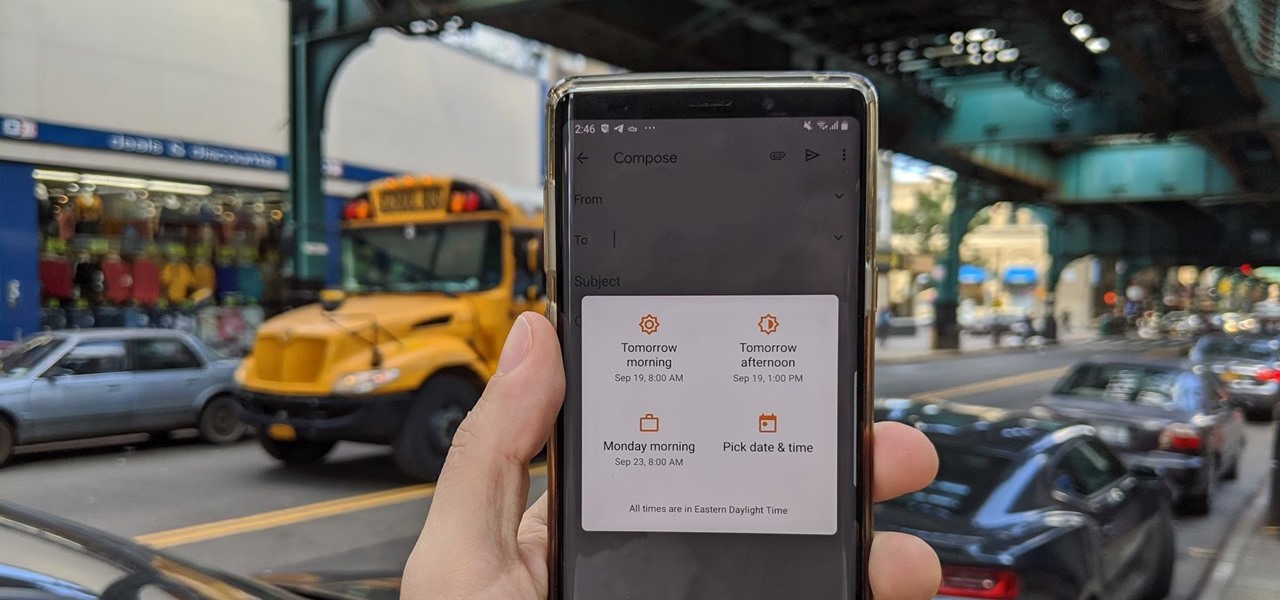
There is power in the detail. Sending an email at a specific time can give you an edge. Depending on what you are doing, it can help your email get read or it can put you at the top of someone's inbox. With the Gmail app for Android and iOS, you can now schedule your messages to maximize the efficiency of your email.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

Filmic Pro harnesses the full native power of your iPhone or Android phone — and then some. If your smartphone shoots in 4K resolution, Filmic Pro will let you choose that resolution. However, it's not all about the pixels — bit rate is an essential factor in determining the overall quality of your 720p, 1080p, or 4K video, something Filmic Pro gives you full control over.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

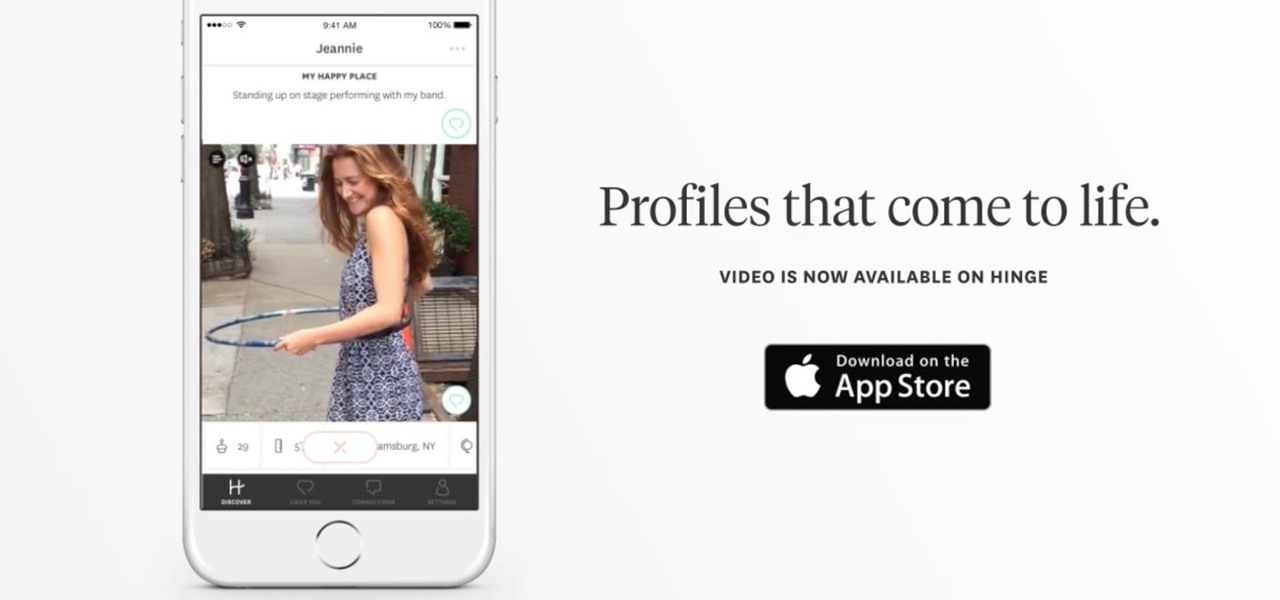
It seems we've come full circle in alternative dating routes. Just like a long time ago when people were able to go to matchmakers and watch videos of potential matches, the dating app 'Hinge' is now allowing you to add videos to your profile.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!