Vanae goes over some tips on how to successfully ask a girl out in this video tutorial. The first tip offered in this tutorial is building a connection between yourself and the girl. This means talking and getting to know the girl before asking her out. The next tip is figuring out what she likes as far as restaurants and movies. The third step is to decide where you want to take her. For example, if there is a new restaurant that just opened up, Vanae suggests asking the girl if she wants to...

This a simple drawing video targeted for and taught by a young girl. The instructor demonstrates how she sketches out female figures, either little girls or women, on her drawing board. She makes additional remarks about hoe to modify and personalize these renderings. So gather up some pens or pencils and paper, and check out this cute little video. You'll learn how to sketch people in no time!

Aerobics are targeted by total physical fitness: strength, flexibility and cardiovascular fitness. Aerobics can be taken in classes and are usually done with music. To practice aerobics you should follow an instructor, stay in motion, use arms to lower or raise intensity, and strengthen heart rate. With this how to video soon you will be able to practice aerobics.
MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

This three part how to video shows you a butt workout that will help you tone and tighten your glutes with three of the best butt sculpting exercises to target your butt, hips and thighs. Do these exercises and you will be able to get in great shape.

This tutorial demonstrates a weight training workout for your triceps. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your triceps and the rest of your arms.

This tutorial demonstrates a weight training workout that develops your deltoids. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your shoulders.

This tutorial demonstrates a weight training workout for the chest. This how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your pecs.

This tutorial demonstrates a weight training workout for your biceps. The how to video provides different exercises to target specific muscle groups so you can gain lean muscle mass and increase strength levels in your biceps.

Learn to play the board game "Plunder" with tips from this how-to video. To play Plunder, you need six players at the most. It is targeted mostly toward adults but even kids as young as eight like to plunder.

This is my updated video of eyeshadows brushes that I use when I do my eye makeup. I tried to be as detailed as possible.

The oblique muscles targeted by this bend-and-twist exercise will help you pick up everything from envious stares to spare change on the sidewalk.

In this tutorial, Bert will show you quickly how to use a bunch of different layers to create a ray gun shooting and exploding it's target. It will help if you already have some Photoshop knowledge for this one.

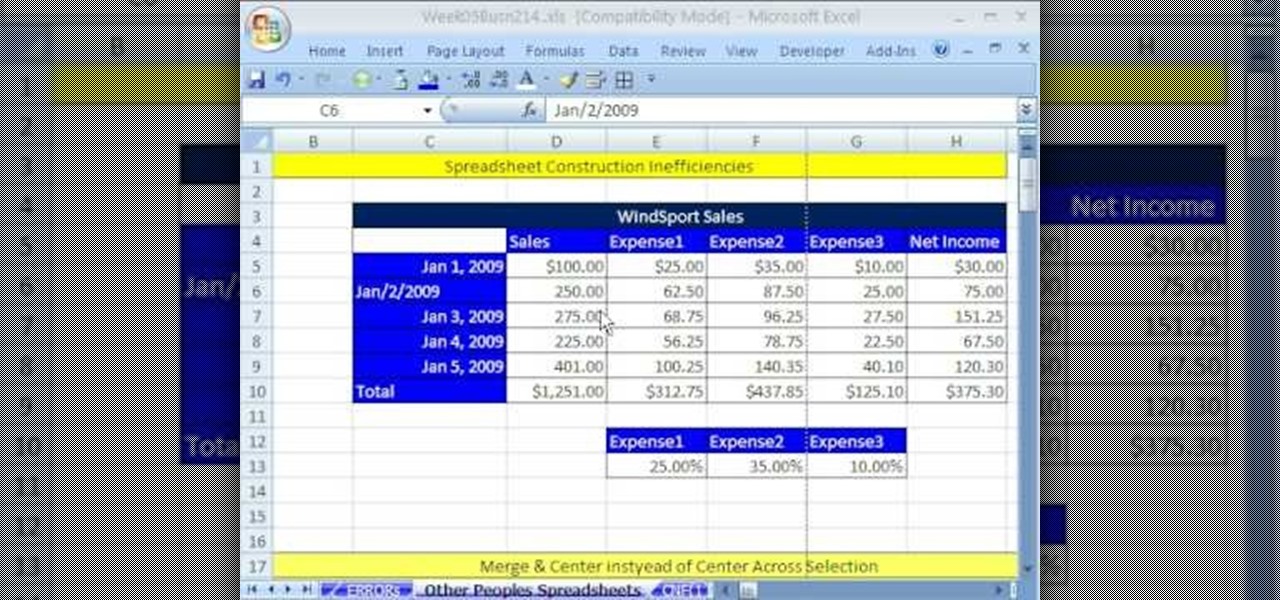
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you're in the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the 26th installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to use spreadsheet construction guidelines to fix common problems:

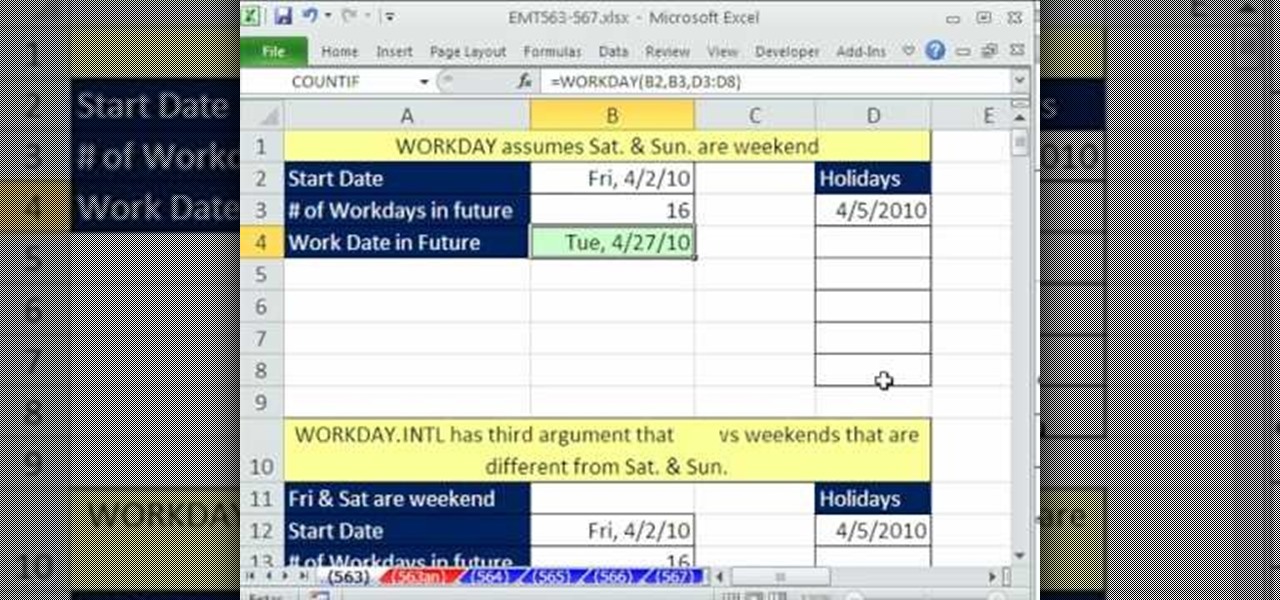
This video tells us the method to use the WORKDAY & WORKDAY.INTL functions in Excel. These functions are used to find a workday after a finite number of workdays in the future. WORKDAY uses Saturday and Sunday as off days. Its syntax is WORKDAY(start date, days, [holidays]). 'days' refers to the number of days in the future and holidays is the list of holidays written below each other in the same column. If Saturday and Sundays are not your off days, use WORKDAY.INTL. Its syntax is WORKDAY.IN...

Celebrity Chef Phil Vickery teaches in this video how to make a British favorite dish: sticky tofee pudding. This tradition dish is served warm and in often during the winter. Phil soaks the dates in boiling water and baking soda to bring out more of their flavor for the dish. While the dates are soaking, he starts creating the sponge part of the cake. With basic ingredients combined, he creates his sponge cake in a way more like a batter than your tradition method of making a sponge cake. Ne...

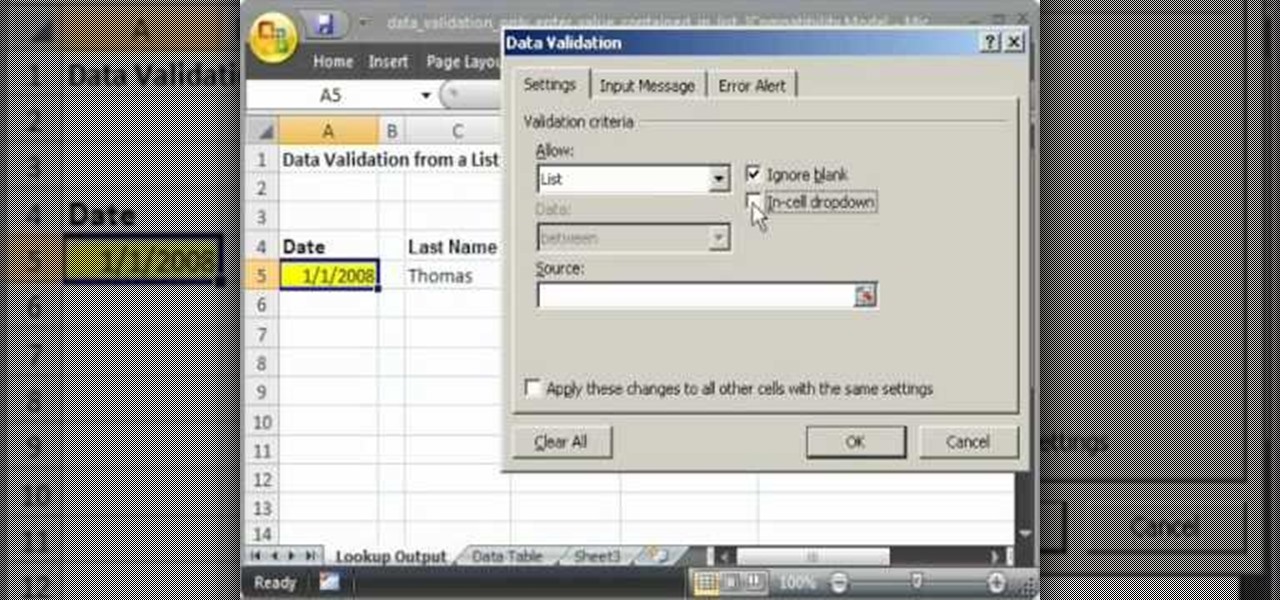
This video shows you how to idiot-proof a data set in Excel pretty much. It demonstrates how to enable data validation in a cell, so that when you type something in it must be in a predetermined list or will not work. Start by typing in your data table in a second tab. His example is a date, then information about certain employees based on that day. To enter the data validation menu, click the cell you want to use and then hit ALT+D+L to bring it up. Go to settings, then under the Allow menu...

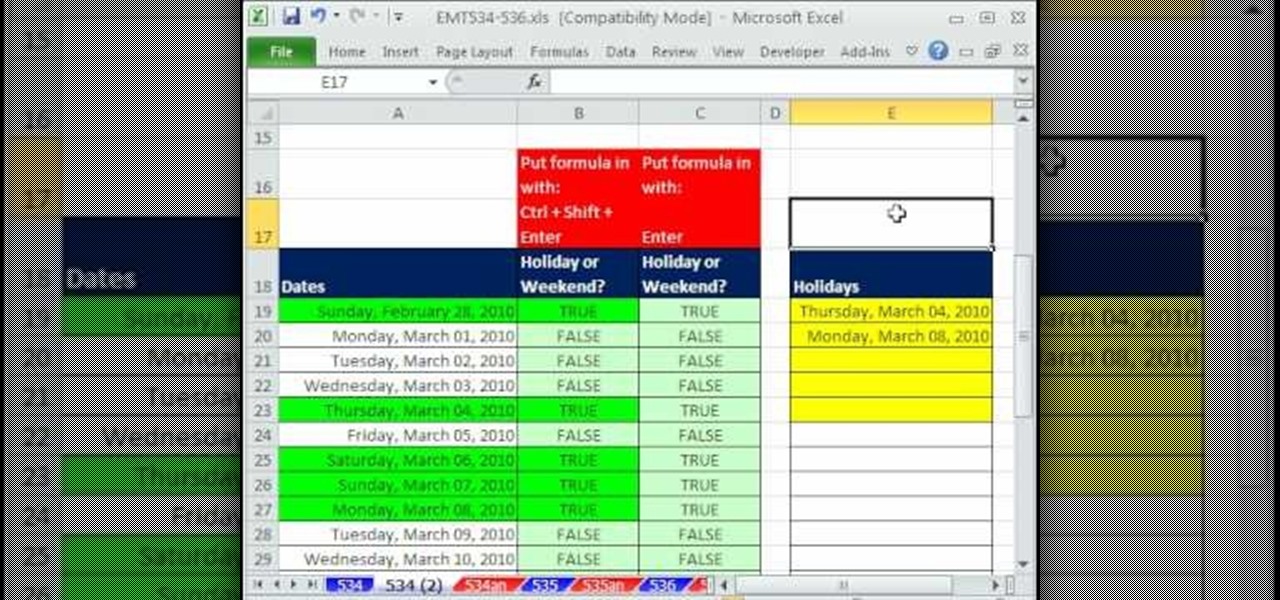
New to Excel? Looking for a tip? How about a tip so mind-blowingly advanced as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 534th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the OR and WEEKDAY functions to create a logical true/false formula that will automatically apply formatting to dates that are either weekends or holidays.

Video demonstrates how to synchronize two folders on windows without doing much of copy pasting and does the job easily. This is a free wear, “FlagSync”.

Chaya Ryvka from Raw living foods teaches to make raw chocolate-pecan crust. You will need: pecans, raw cocoa nuts and powder, dates, vanilla, salt and food processor. First put the pecans into the food processor. Later add the raw cocoa nuts (make sure its raw ) and raw cocoa powder. At last add some fresh organic dates and a pinch of salt in the food processor. Now process all the ingredients until the crust starts to rise and repeat the process until all the nuts are broken down. Now add t...

Get ready for the boss fight of your lifetime in the Xbox 360 game Darksiders. In the boss fight in Twilight Cathedral, spar against Tiamat. When you reach the bat queen Tiamat she will take offf into the air immediately. Quickly dash to the Inert Bomb Growth around the edge of the arena closest to the flying and then throw it at Tiamat. Now you need to use your Crossblade and target a flaming urn then the bomb you stuck onto Tiamat to light the bomb on fire. Once you detonate the bomb on her...

Keep your crossblade near for this level of the Xbox 360 game Darksiders, In the sub-boss fight in Twilight Cathedral - The Jailor, make sure to target the sores. This grotesque monstrosity towers over War. It is almost as wide as it is tall. You'll want to keep your distance from the Jailer as it has a powerful attack in which it slams the cage it carries onto the ground. You'll want to spend most of you time here with the monster targeted while you backpedal away from it. The biggest annoya...

Caged Fighter: Make your way across town and you'll find an injured soldier on the rooftops that gives you some new information on finding Bartolomeo, who should in turn help you with Silvio. You get a large green area added to your map, but note that it's overlapped by a restricted area. Expect trouble.

Knowledge Is Power: But can power be knowledge, too? Pay a visit to Leonardo and he'll cook up a new weapon for you based on a mystery codex. After the cut scene, move out to the yellow map marker and you'll get some directions on how to use your new pistol. Lock onto the three dummies across the river and shoot 'em. Holding down the fire button builds up your accuracy, making it possible to hit the distant targets. When all three targets are shot, return to Leonardo to complete the mission. ...

Infrequent Flier: Fly through this episodic mission and take control. As you take flight, immediately pause the game and check out your map. You can see the locations of all of the fires in the city, as well as the target to the far, far southeast. If you make a simple beeline for the target, the Palazzo Ducale, you won't get the updrafts you need to maintain your height and infiltrate the fortress. Instead, you need follow the trail of fires that lead you east and then north before finally t...

Have you tried working out with a swiss ball? A swiss ball and outer thigh lifts are an essential part of toning your legs and strength training. This fitness how-to video demonstrates how to target the outside of your thighs with outside thigh lifts. Learn about muscle training and exercises in this video workout.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Encrypting payloads and encoding stagers are more effective against macOS than one might think. It's very easy to evade VirusTotal and macOS antivirus software using a few simple tricks.

OnePlus has officially given us a date for when the OnePlus 5T will be announced. We've known about most of the specs for a while, and we just found out about the potential pricing, so a release date is the final piece of the puzzle. Consider this puzzle solved.

After exploiting a vulnerable target, scooping up a victim's credentials is a high priority for hackers, since most people reuse passwords. Those credentials can get hackers deeper into a network or other accounts, but digging through the system by hand to find them is difficult. A missed stored password could mean missing a big opportunity. But the process can largely be automated with LaZagne.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

This is just a heads up that thieves are now using GPS fitness apps to target people. Thieves are using popular GPS fitness apps such as Strava to find out where you live where they will then come and steal your bikes.

In this how to video, I discuss three different exercises that have really helped me to tone my waistline. Although you cannot specifically target different fat deposits while dieting, it is still important to perform these exercises to give your core and waist that aesthetic look. These exercises have given me great results, but a solid diet and a good training program is also extremely important to sculpting your body. Enjoy!

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

Make a great online dating profile with this tutorial! Having a good profile is very important because when it comes to catching someone's eye and getting them to contact you. You have maybe a few seconds so your profile has to stand out, be interesting, and personable. Photos are also very important. You need 3-5 nice solo photos to put on your profile. Photos will help a person decide if they are interested in you. Posting good head and shoulder and full body photos is important. Do not use...