One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.
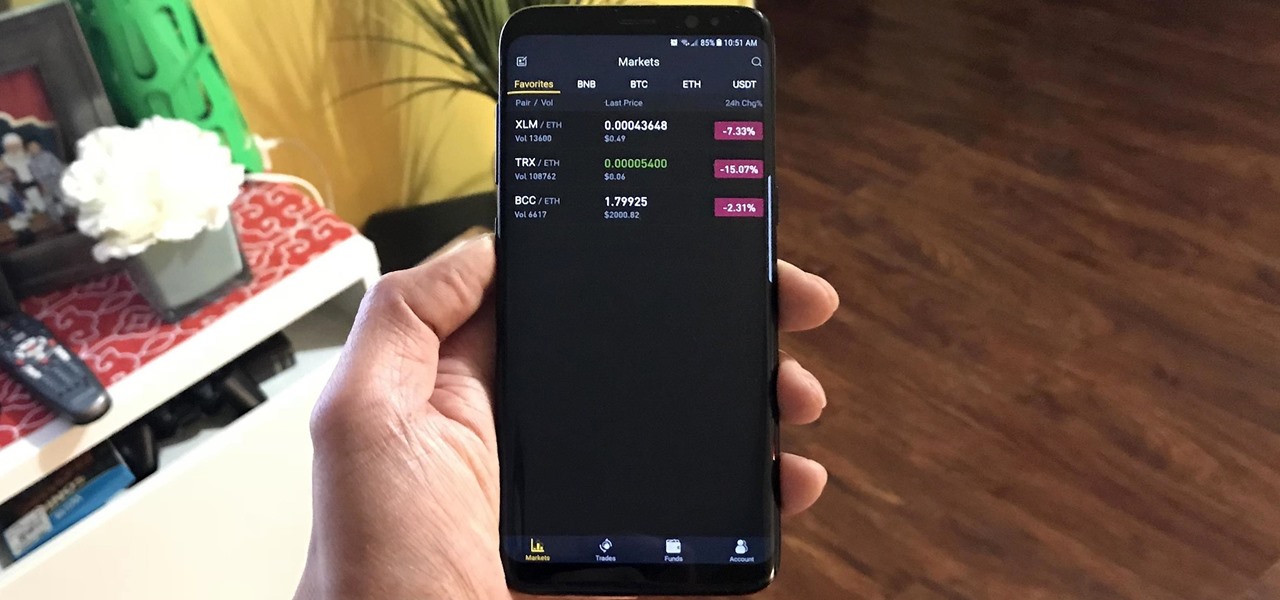
With the sheer number of alt-coins that you can buy and sell on Binance — Ripple (XRP), Stellar (XLM), and NEO to name a few — keeping track of coins you're interested in is a hassle. But with the tap of a button, you can mark trades and alt-coins that are on your radar for quick access on your Binance account.

Samsung's Galaxy S8 and S8+ are excellent smartphones that wowed critics and consumers alike. So, it's only natural that Samsung's followup, the Galaxy S9 and S9+, would garner significant anticipation. While we don't know everything about these devices quite yet, we do have guesses to some key points of interest, including when the device will be announced and even released.

Snapchat has broken new ground in its augmented reality advertising efforts, as BMW has opted to show off its new X2 model in AR with the Augmented Trial Lens.

Smartwatches are an excellent way to keep track of our smartphone's notifications as well as our own fitness. However, these devices are not usually cheap. If you'd rather not pay a premium for a piece of wearable technology, check out all the Black Friday deals on smartwatches — we've got all the best ones listed right here.

Our smartphones have outlived the Walkman, iPod, and even stereo systems, to some degree. So it makes sense to treat your iPhone or Android device to a quality pair of headphones, whether you're a hardcore audiophile or just an everyday music lover. This doesn't come cheap, of course, so why not buy them on Black Friday?

Speakers today are a marvel for their portability and sound quality. No longer do we need giant boxes to bring down the house — a speaker that can fit in your hand can fill a room with your favorite music. This is even more important when you pair it with your smartphone, and there are lots of smartphone-friendly speakers on sale this Black Friday.

There's a good chance that an iPhone is on one of your Christmas shopping lists, but these things are uber-expensive now, making it hard to justify as a holiday gift — even for yourself. That's what Black Friday is for, though, which can help you save a little bit of cash on an iPhone purchase — or at least, give you something in return to help you get even more holiday presents.

The advent of ARKit and ARCore has strengthened the demand for development tools to build augmented reality experiences for compatible iPhones, iPads, and Android devices.

Modern warfare takes on a more literal translation with the advent of new augmented reality displays revealed recently by the US Army to improve soldiers' situational awareness on the battlefield.

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.

Tim Cook claimed 85% of new iPhone buyers are switchers from Android back in 2015. Now, after financial analysts noted a drop in the company's stock prices, Apple has unleashed a series of ad campaigns directly targeting the users it needs to win over. That's you, Android lovers.

When Facebook purchased WhatsApp for $19.3 billion back in 2014, we all knew this was coming—it just took longer than we thought. But starting today, the data mining became official, and now, information from your favorite messaging app is no longer out of reach for the world's biggest social media site.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Greetings my fellow hackers.

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

Sometimes, it helps to be prepared before jumping into a new relationship; look before you leap! To have a healthy relationship with someone who has an STI, it is advisable that you enter the relationship knowledgeable about sexually transmitted infections and what your risks might be.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

When it's most important for me to browse the web incognito, I always seem to forget to enable private browsing. If that sounds like you, it's time you stop making that mistake for good. Manually deleting the cache and browser history is a thing of the past, and as it turns out, so is manually switching to incognito mode.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

The best way to show your parents that you are ready to date is by being responsible. Document just how responsible you are and present them with possible, mind-easing dating options and you’ll be dating in no time.

Acne sucks - or, more correctly, acne oozes. Which is why it's so important to take care of your skin with oil-reducing, calming products. Most anti-acne medications you can buy are severely drying and irritating, meaning they can cause the adverse effect of making your skin compensate by producing even more oil.

Is your Christmas tree looking a little too "I got everything from Target" generic? Then it's time you learn some decorating tips from interior designer Rebecca Robeson.

Do you play an intensive sport, like soccer or football, that requires you to be able to not only run quickly towards a target area far away, but also to be able to catch a flying ball with precision that far away? Then you'll benefit from the speed and quickness training methods presented in this video.

Imagine… your friend is drinking an ice-cold soda out of his/her styrofaom cup, and everything's fine, until… it's starts leaking everywhere! It could be utterly hilarious, or disastrously evil, depending on who your target is.

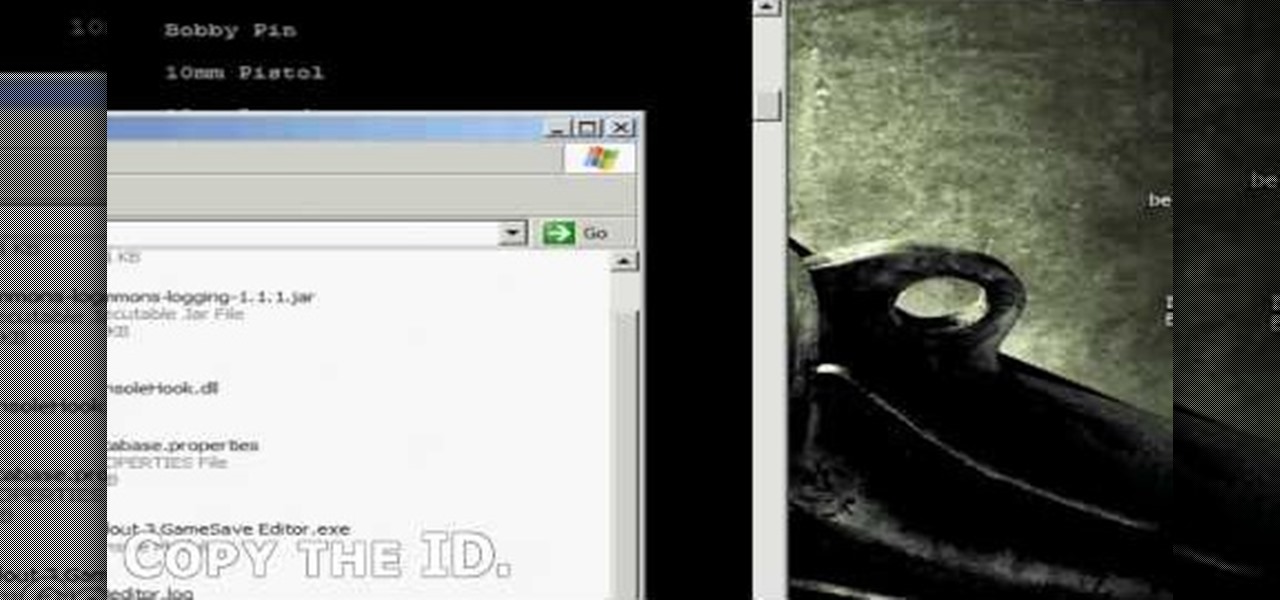
Fallout 3 is one of the most popular and biggest (content-wise) games on the XBox 360, and has thus become a popular target for hackers to mod. This video will show you how to mod your Fallout 3 saved game from the XBox 360 version using some FREE software. This does not include Modio, the popular for-money save game editor that many hackers use. Here are the files:

Four time abs is an excellent exercise for working the lower abdominals and abs workout. Try this out to tone your lower abs, which typical crunches can't get to.

Learn how to create a character rig when animating 3D models in Blender. Specifically, this clip addresses the following topics: Bone creation, splitting and re-parenting. Weighting with bone heat, mirrored weight painting and posed weight painting. IK setup, bone roll, and pole targets. Advanced foot rig with control to pivot off of the heel, toe, ankle or ball and control to lift the toes. Whether you're new to the Blender Foundation's popular open-source 3D computer graphics application or...

Despite what the name may imply, triceps kickbacks don't involve kicking of any sort. Rather, this tricep-sculpting exercise move involves getting down to a near squat position and bringing a dumbbell forward and back, keeping the shoulders stead and down.

Lock and load! In this Xbox 360 tutorial, you're taken for a nifty little ride by the guys at Achievement Hunter. The main target: an easter egg. And not just any cool easter egg, it's one that puts you, somewhat, in contact with another zombie basher from a different game, Dead Rising. Yes, in this Left 4 Dead 2: The Passing, easter egg hunt, you'll be reading a little message left to you from the man himself, Frank West. So sit back and prepare for the worst. Enjoy!

You must have a certain attitude to appreciate practical jokes and pranks. Your friends (or targets) may not appreciate pranks as much as you, especially messy ones. The messy pranks are the ones that are less likely to provide a laugh from your victims, at least not right away. This ketchup prank is one of those.

Brooke Burke and Autumn Calabrese walk the viewer through a super-effective, targeted butt workout, doable in your living room in only 5 minutes. The first exercise, a "Heel Press", is done from your hands and knees. Keeping your head in line with your spine and your belly button tucked in, press one heel toward the ceiling, then bring it all the way into your chest. Brooke recommends 15-20 reps on each leg. The next exercise, "Crossovers", builds on the Heel Press. After pressing your heel t...

This is footage from B.F. Skinner's psychological tests on shaping behavior.